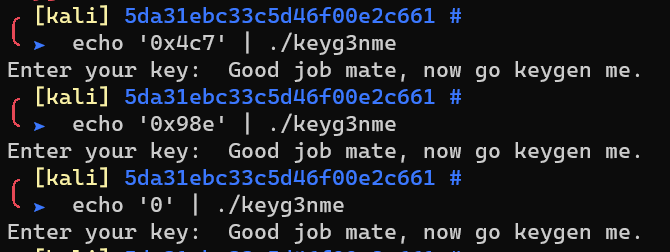
easy keyg3nme Walkthrough
| reference | ezman's easy keyg3nme |
Use horsicq/Detect-It-Easy to identify the binary first:
Here I use two methods:
radare2
pdf @ main to print disassemble function main:
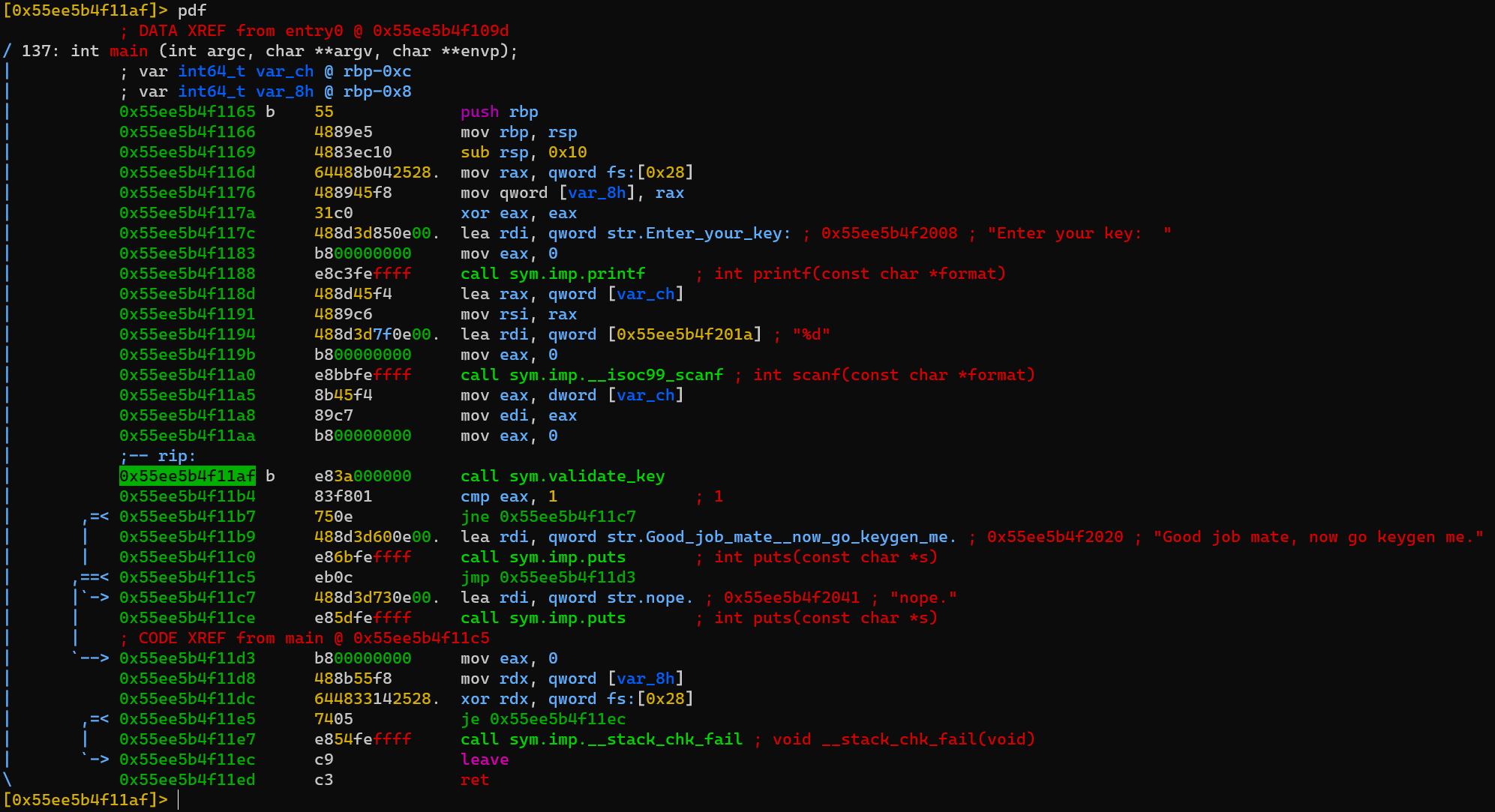
Address 0x55ee5b4f11b4 and 0x55ee5b4f11b4 need register eax to be 1 to go to address 0x55ee5b4f11b9.
pdf @ sym.validate_key:
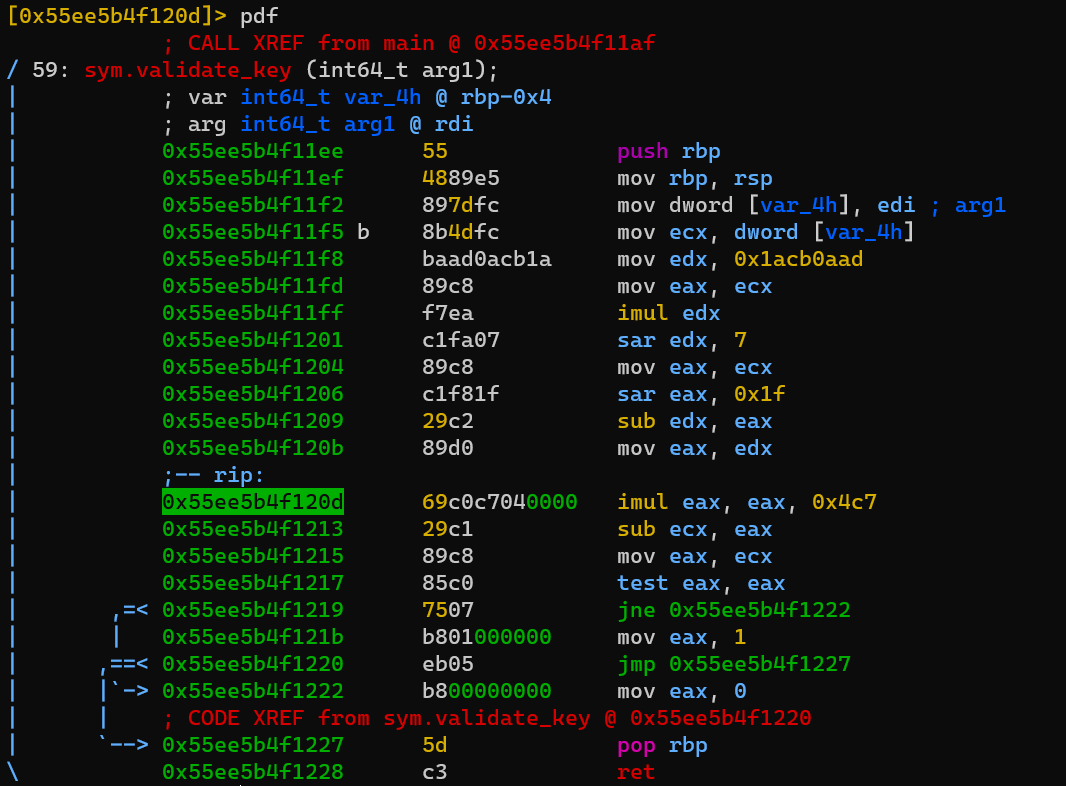
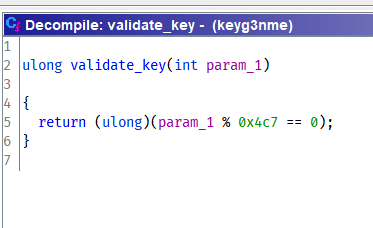
Function validate_key:
1 | mov ecx, dword [var_4h] ; ecx = arg1 |
I’ve not figured out what does it mean by edx_new * (2**32) + eax_new = arg1 * 449514157.
Try to set register edx to 1 after executing sar edx, 7, which leads register ecx to 0x4c7.
Verify imul edx:
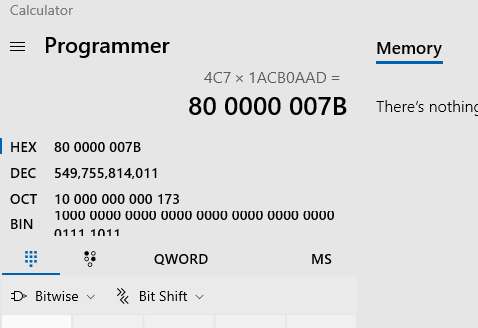
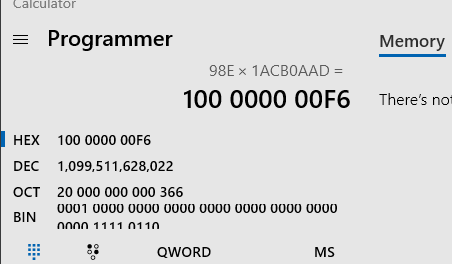
0x80 is just 128.
Also set register edx to 2, which leads register ecx to 0x98e.

ghidra
Use ghidra is quite easy, thanks to the build-in decompiler.
Load the binary to ghidra, and navigate to Symbol Tree to enumerate existed functions:
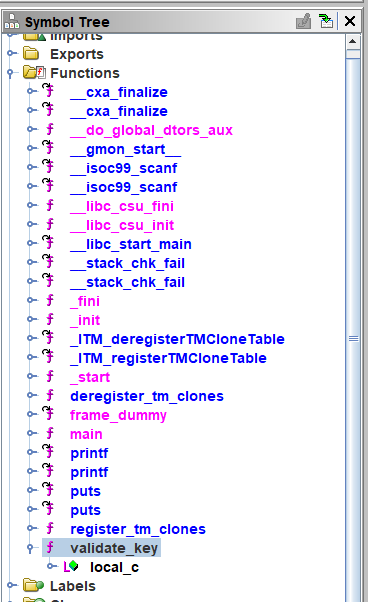
Navigate to function validate_key:
Navigate to function main:
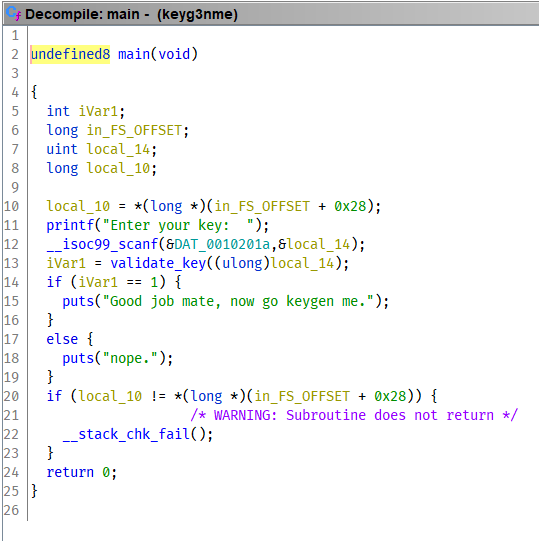
Function main:
- read variable
local_14from stdin - pass variable
local_14to functionvalidate_key, get result in variableiVal1 - check variable
iVal1
proof