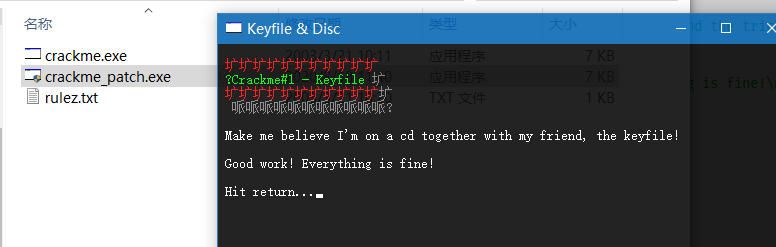
crackme1 Walkthrough
| reference | crackmes.de's crackme1 by midi |
Scan with die:
Execute the binary:

Load the binary to ghidra, and enumerate existed functions:
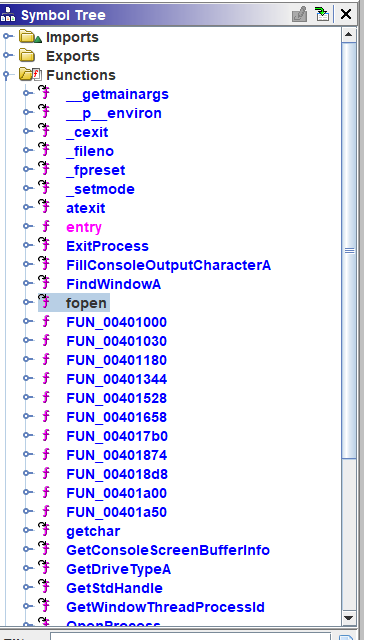
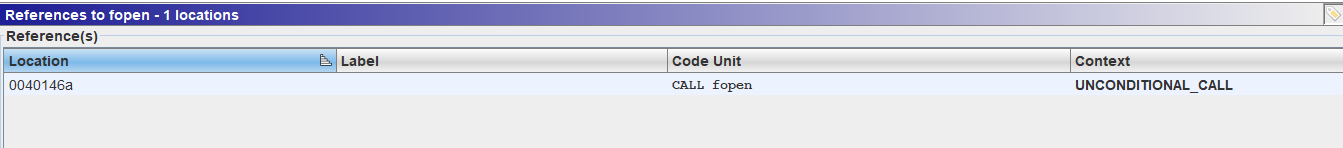
Show references to fopen keyfile:
FUN_00401344:
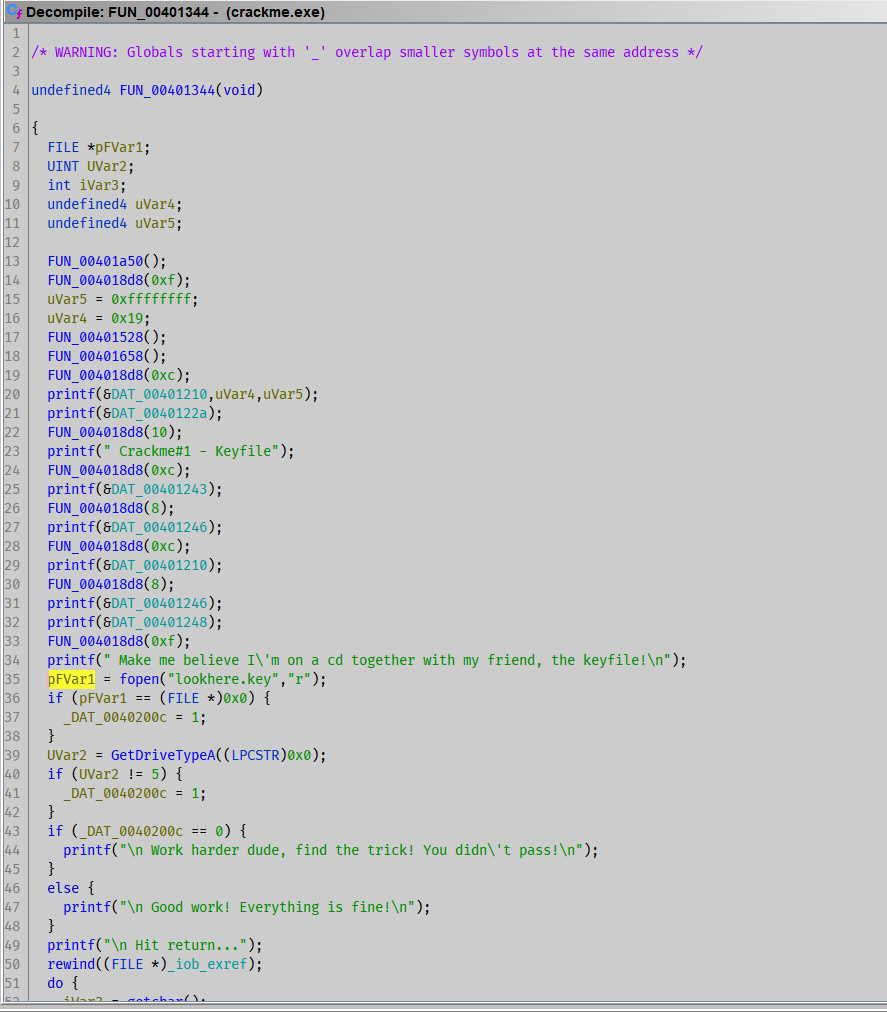
The program will:
fopenlookhere.keyGetDriveTypeA- check
_DAT_0040200c
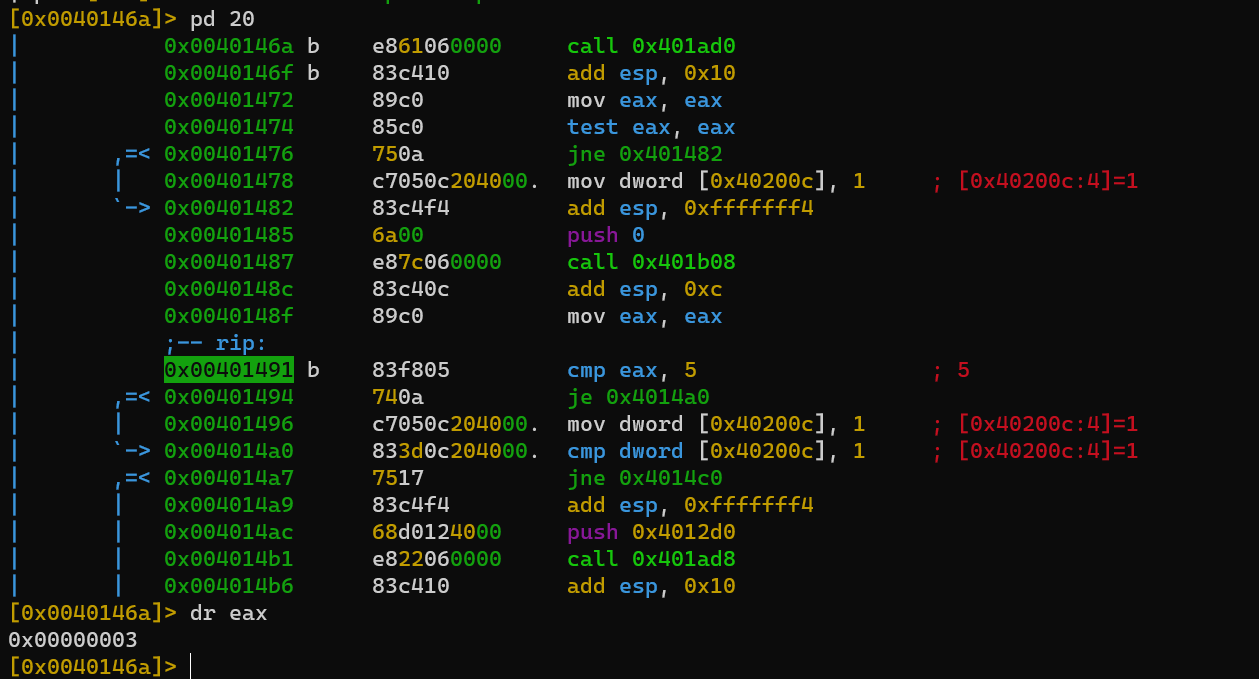
The fastest method is patching the step 3:
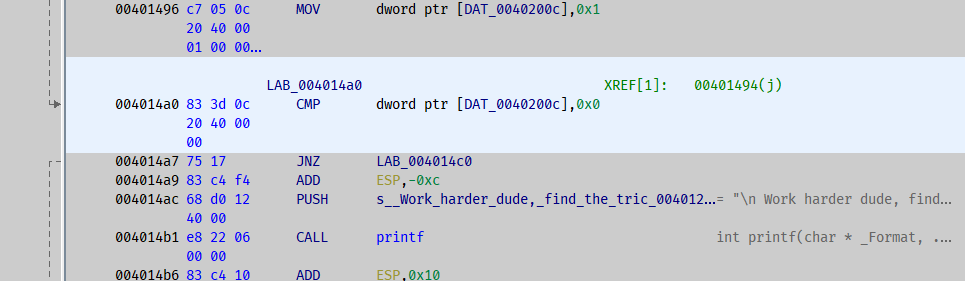
Decompilation of the function:
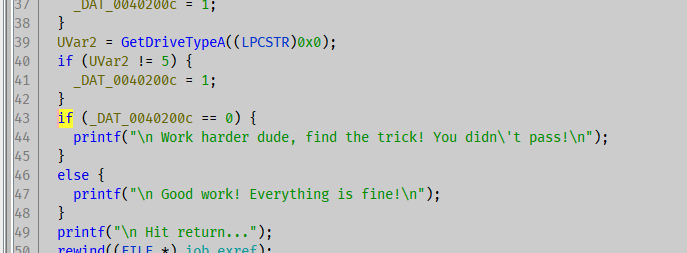
proof
Patch, save and export: