Simple crackme Walkthrough
| reference | kawaii-flesh's Simple crackme |
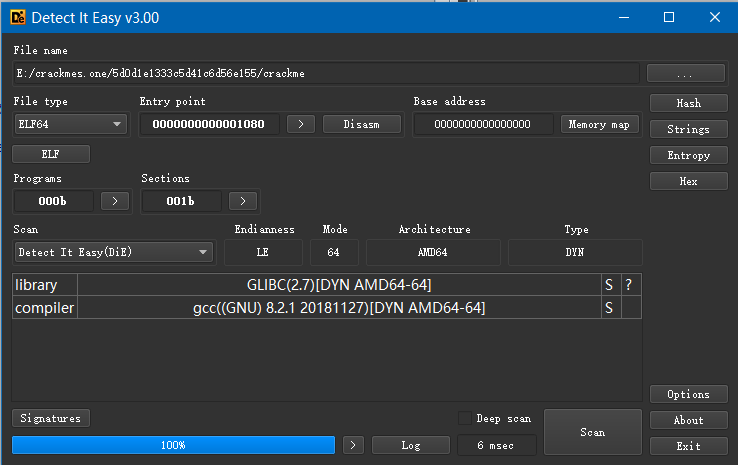
Scan with DIE:
pdf @ main:
1 | lea rax, qword [var_1a0h] ; rax = address of variable var_1a0h |
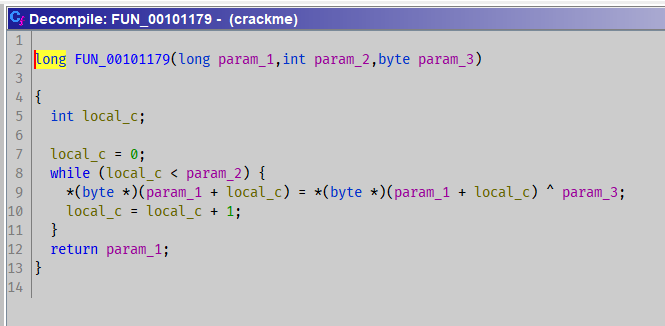
I don’t know why r2 doesn’t disassemble this function.
So I use cutter (still based on r2..) and ghidra.
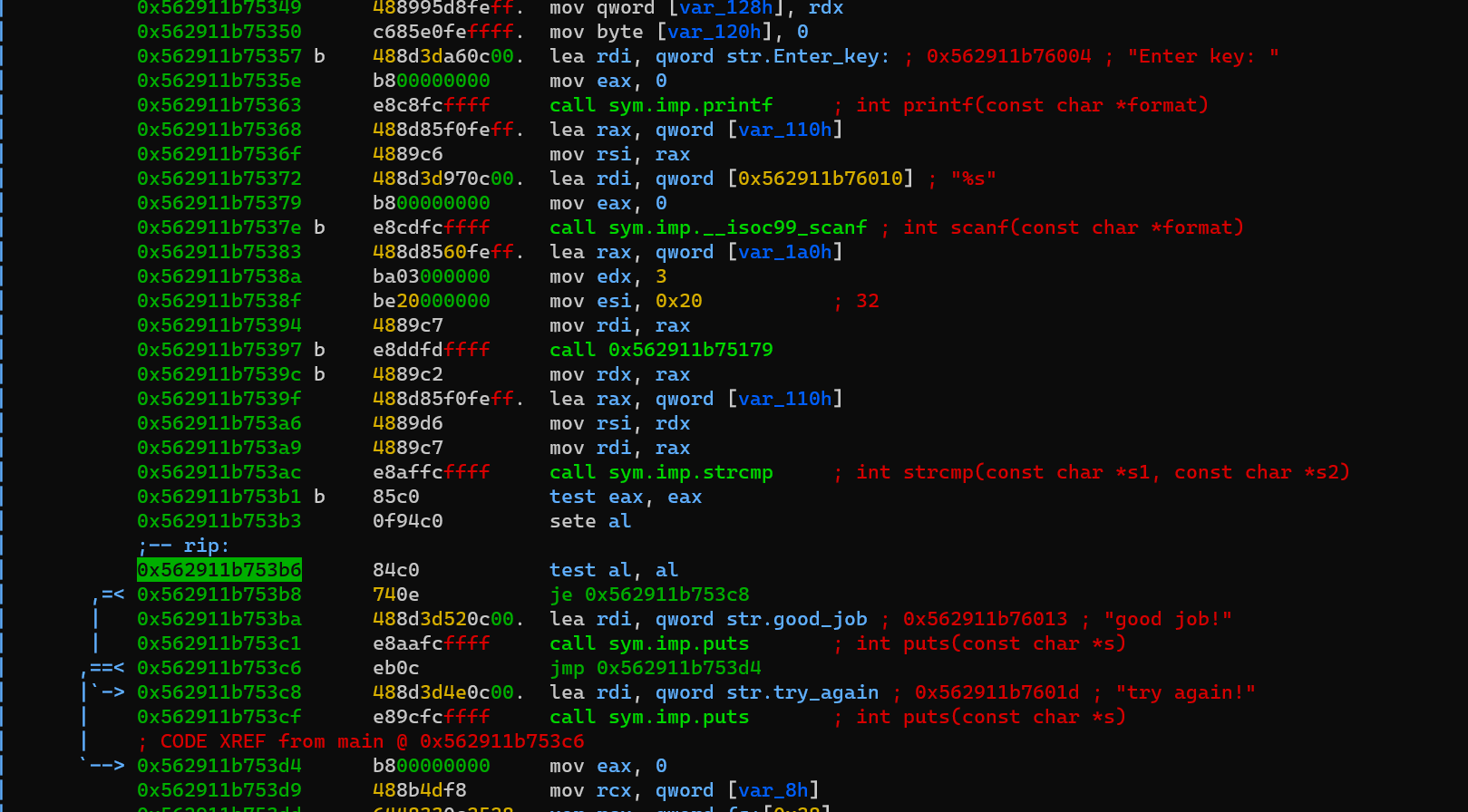
Add several breakpoints, dc to mov rdx, rax to finish executing function 0x562911b75179:
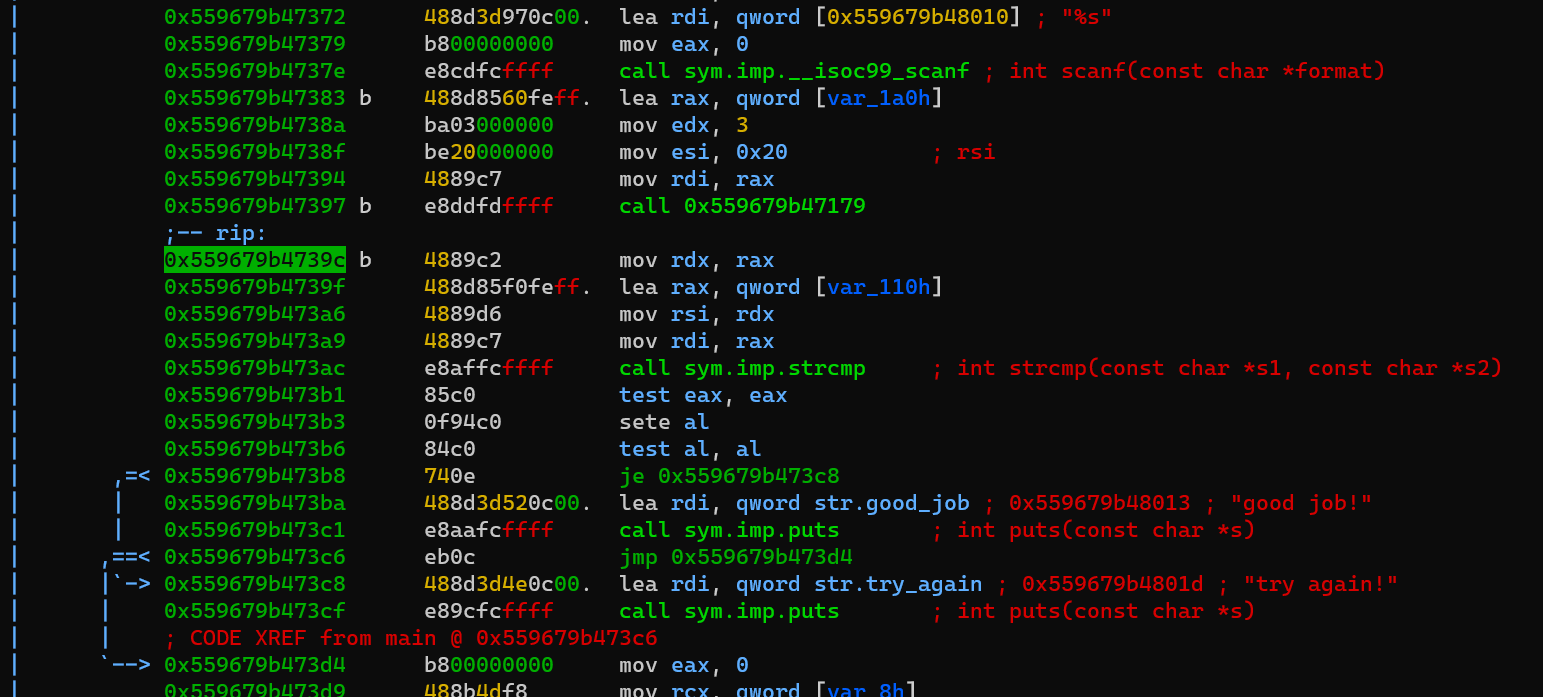
Now the program will compare the memory of rax and rdx as shown above in the comments:
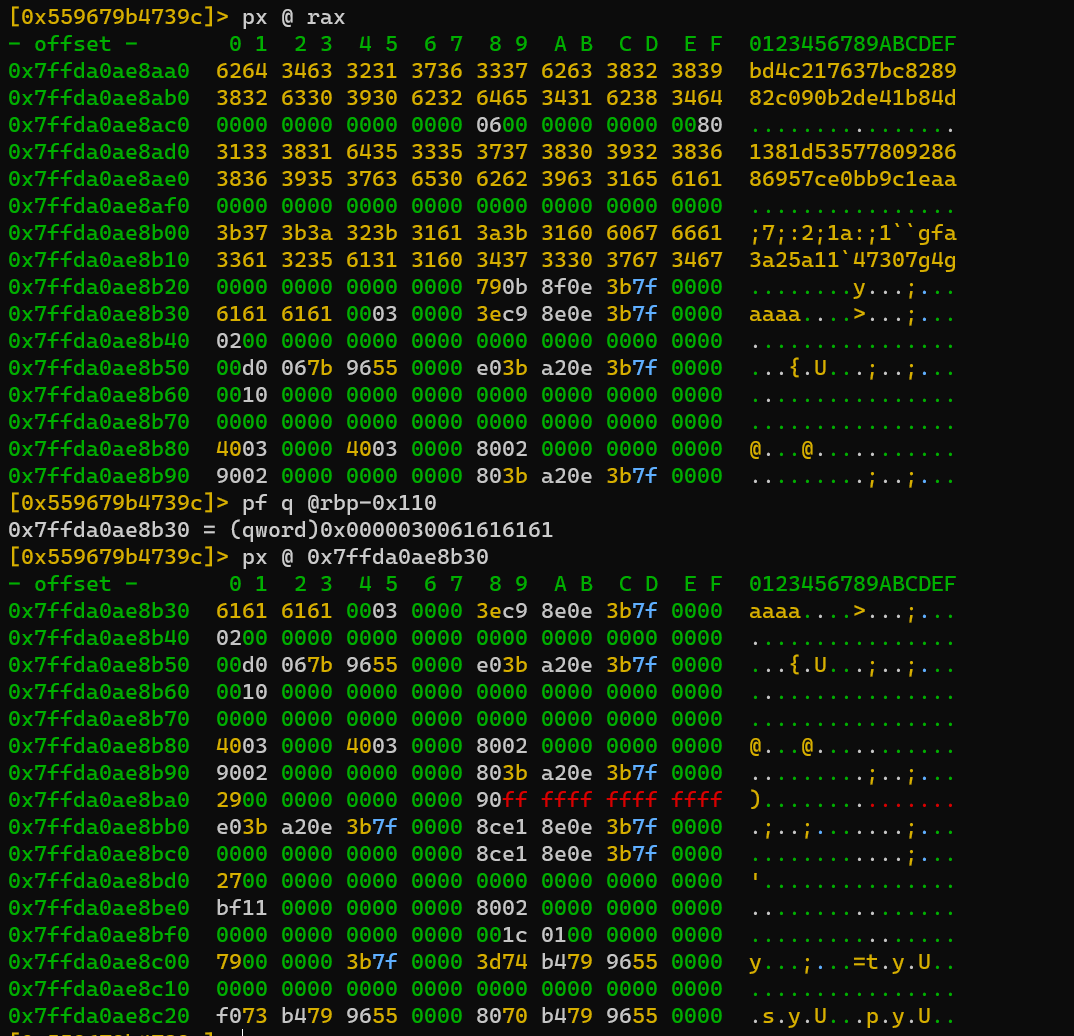
proof
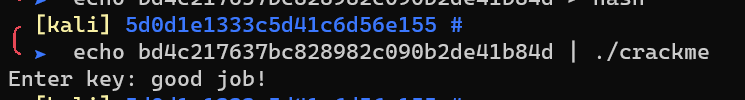
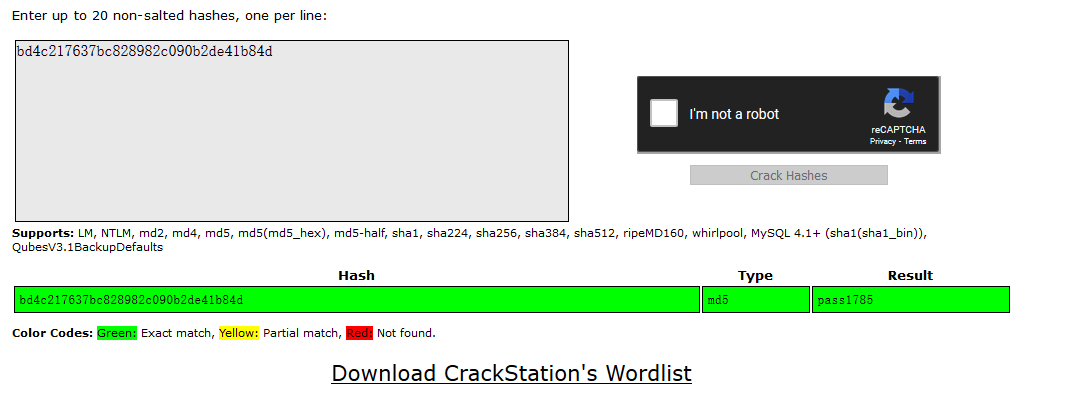
Crack the hash online:
- disassemble with
cutter:
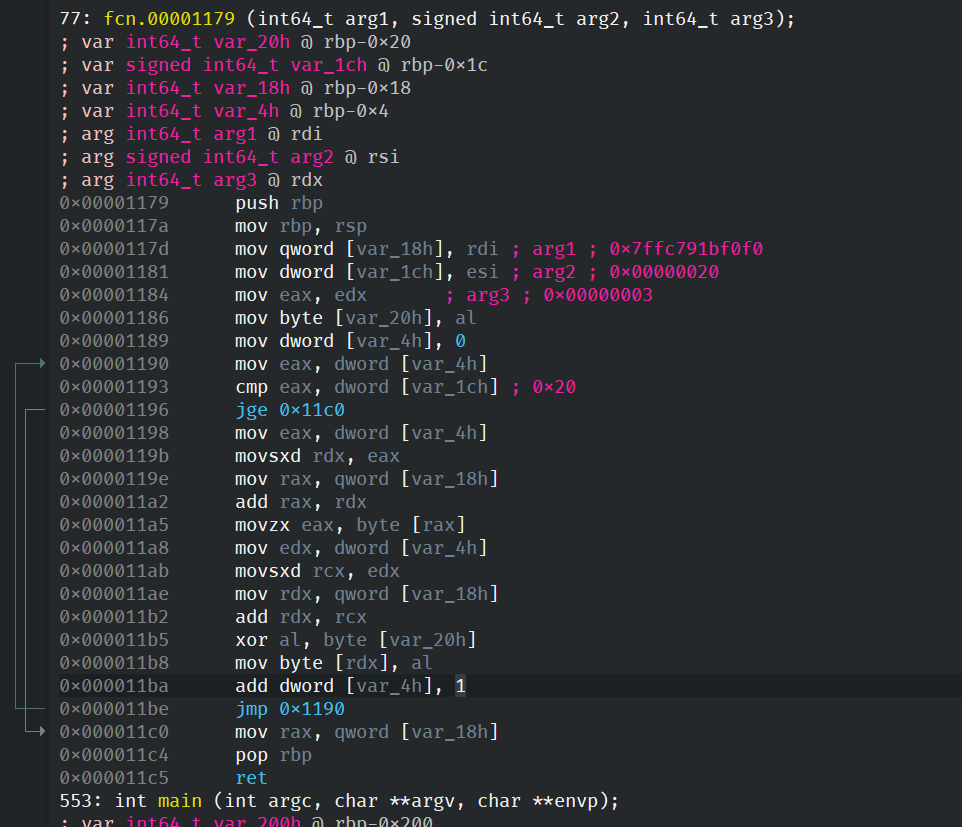
- decompile with
ghidra: