Sectigo AddTrust External CA Root Expiring May 30, 2020 (for Ubuntu 14.04 Trusty)
This post is tested under Ubuntu 14.04.
It may also works under other legacy systems.
Sectigo at present offers the ability to cross-sign certificates with the AddTrust legacy root to increase support among very old systems and devices. This root is due to expire at the end of May, 2020.
If you’re still using Ubuntu 14.04 as a server and a client, you may be affected by this event today like me.
Some of your applications may complain if you don’t add “skip certificate check” option in your codes (shouldn’t be added by the way).
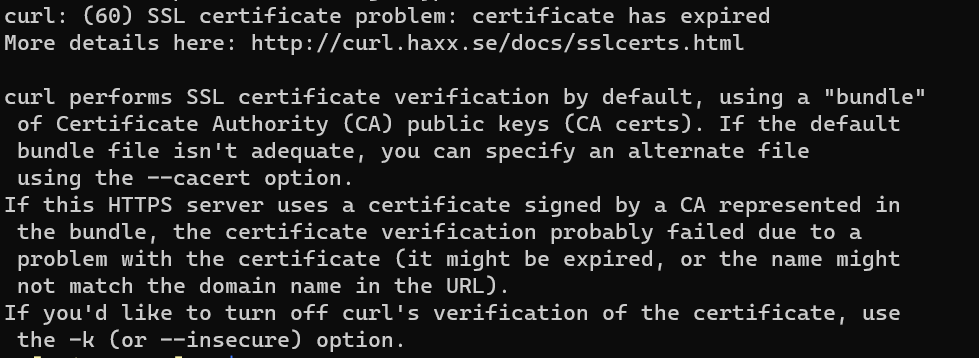
curl is just an example.
1 | curl -s https://foo.bar |
Check the certificate with ssllabs.
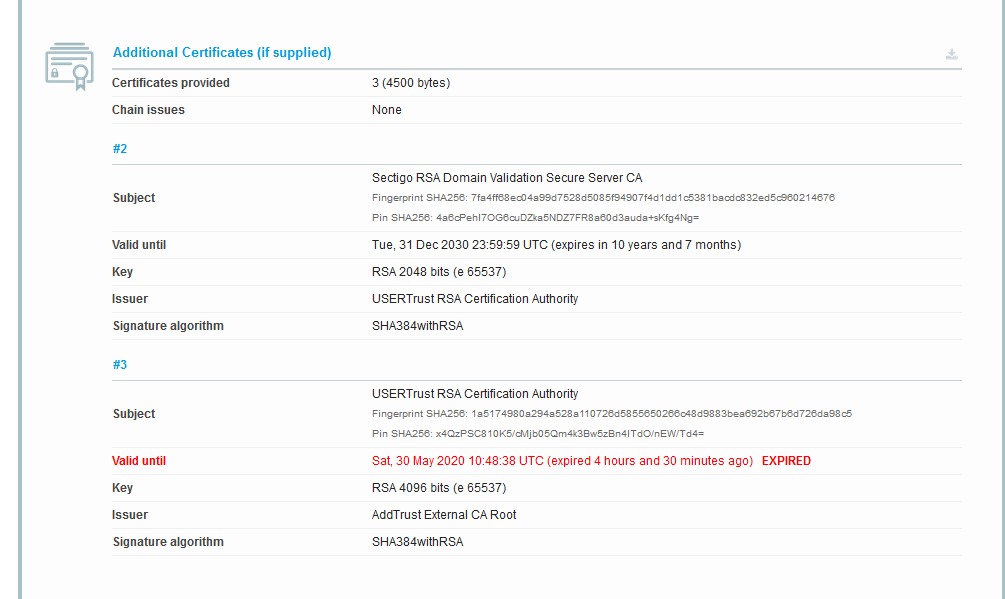
According to the knowledge base from Sectigo:
Note: Few legacy systems, that no longer receive any updates from their vendor, may not trust our SHA-2 Certificates. To enable them to trust our SHA-2 Certificates, we recommend our customers to include the Cross Signed Certificate into the Server Certificate chain. This will enable those legacy systems to trust our SHA-2 Certificates.
Replace the third part of the existed full crt file with USERTrust RSA Root xSigned using AAA CA [ Cross Signed ].
This link is just for DV type. Make sure what type of your certificate is.
Recheck with ssllabs.
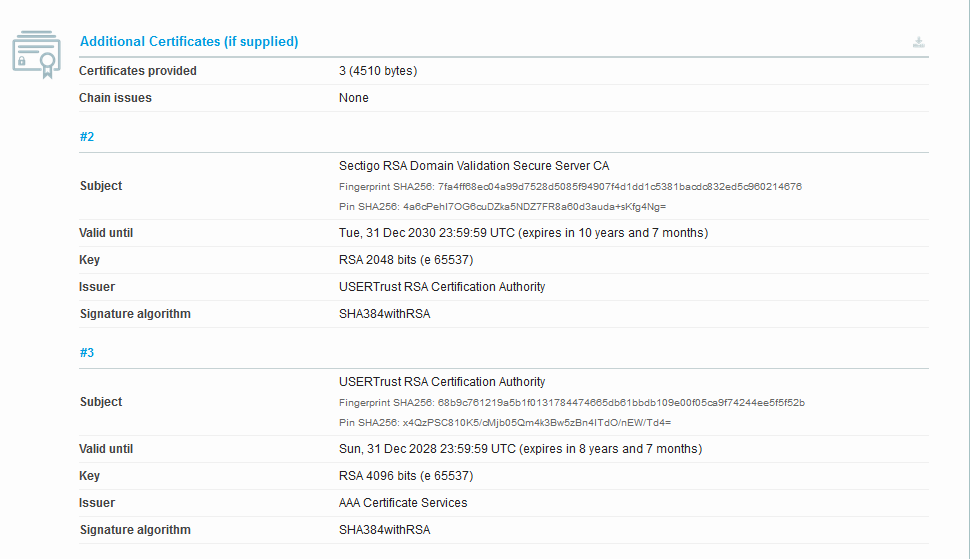
The valid date changes from ‘May 30, 2020’ to ‘Dec 31 2028’, and the issuer changes from ‘AddTrustExternal CA Root’ to ‘AAA Certificate Services’.
I also found a note from this page.
For unusual cases, Sectigo offers a new cross signing option with its AAA root, which does not expire until 2028.